Purpose Of S Boxes In Des
Referring To The Lecture Notes On Des There Are One Expansion Permutation Table1 Eight Substitution S Boxes And One Permutation P Box Table 2 Course Hero
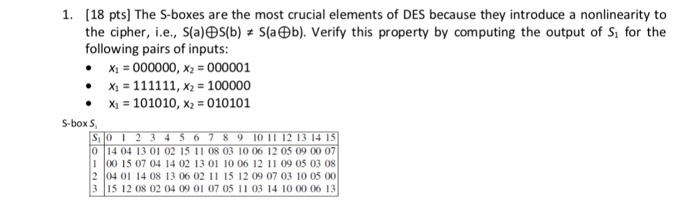
Solved 18 Pts The S Boxes Are The Most Crucial Elements Chegg Com
People Wou Edu Beaverc 440 W15 7 des and sdes Pdf

5 The Role Of The S Boxes In The Function F Of Des Is Illustrated In Figure 1 Course Hero
Www Sans Org Reading Room Whitepapers Vpns S Box Modifications Effect Des Like Encryption Systems 768
Entropy Free Full Text A Novel Construction Of Efficient Substitution Boxes Using Cubic Fractional Transformation Html
Sbox and pbox are the technologies that are used in cryptographic algorithms This is just small explanation about the Sbox used by the AES cryptographic algorithm The Sbox is generated by determining the multiplicative inverse for a given number in Rijndael's Galois Field The multiplicative inverse is then transformed using the following affine transformation matrix.
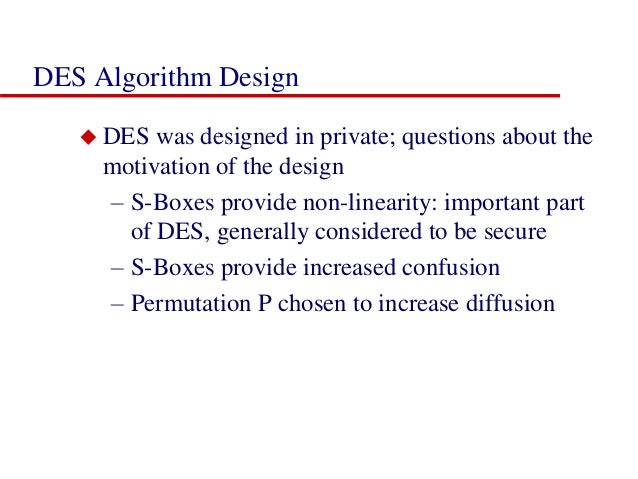
Purpose of s boxes in des. What is the purpose of the Sboxes in DES?. 4bit SBoxes have been analyzed in relation to linear equivalence 6,31, defined as follows Definition 5 Let M i and M o be two invertible matrices and c i and c o two vectors The SBox S0defined by two affine transformations S0(x) = M oS(M i(x c i)) c o belongs to the linear equivalence set of S;. The eight Sboxes of DES were the subject of intense study for many years out of a concern that a backdoor (a vulnerability known only to its designers) might have been planted in the cipher The Sbox design criteria were eventually published (in Coppersmith 1994 ) after the public rediscovery of differential cryptanalysis , showing that they had been carefully tuned to increase resistance against this specific attack.
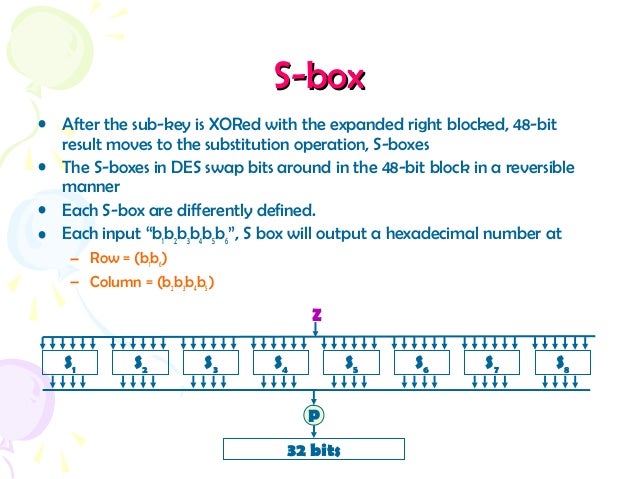
In a study of Sboxes of DES, it is possible to compare the Sboxes to random Sboxes of the same size This is not a bad idea in general, as random Sboxes are expected to result in a secure cipher if they are big enough However, in the design of DES the Sboxes are very small, designed to fit within the very basic IC technology of the early. The Sbox maps an 8bit input, c, to an 8bit output, s = S(c) Both the input and output are interpreted as polynomials over GF(2) First, the input is mapped to its multiplicative inverse in GF(2 8) = GF(2)x/(x 8 x 4 x 3 x 1), Rijndael's finite field Zero, as the identity, is mapped to itself. Each row of a Sbox defines a general reversible substitution It consists of a set of eight Sboxes, each of which accepts 6 bits as input and produces 4 bits as output What are the essential ingredients of a symmetric cipher?.
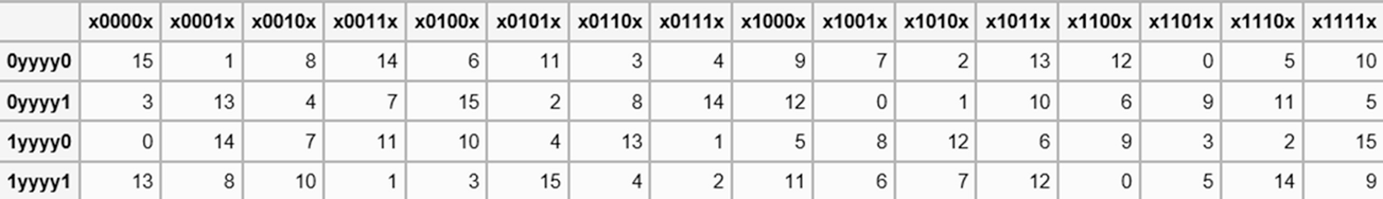
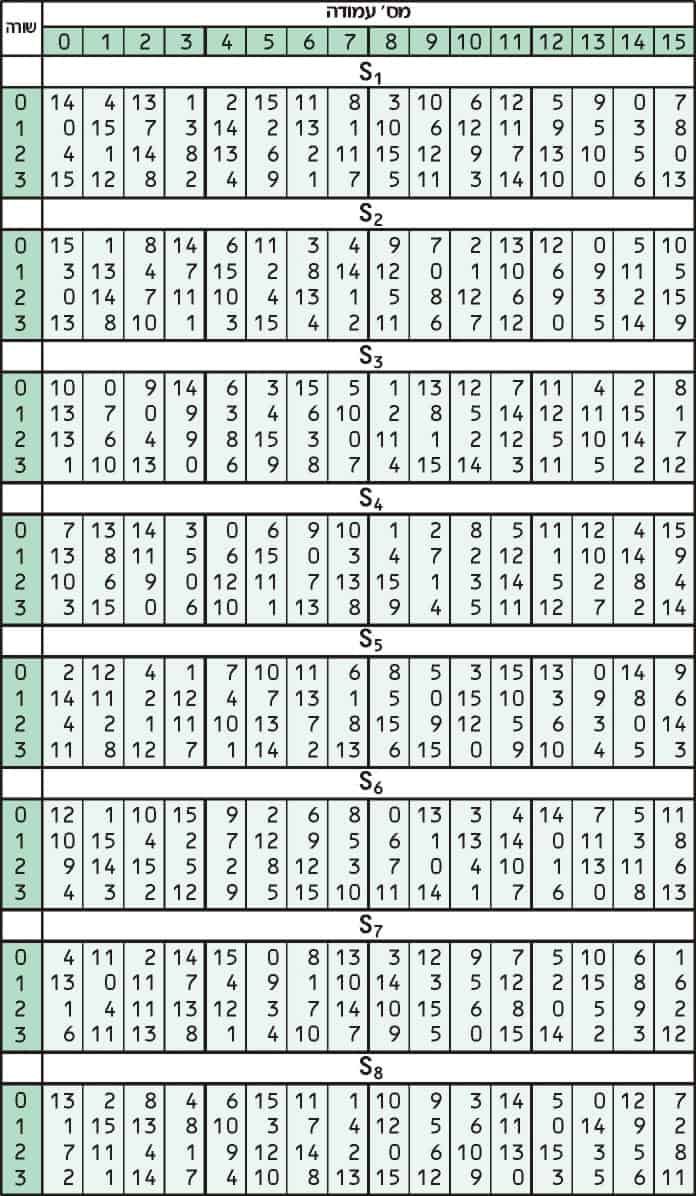
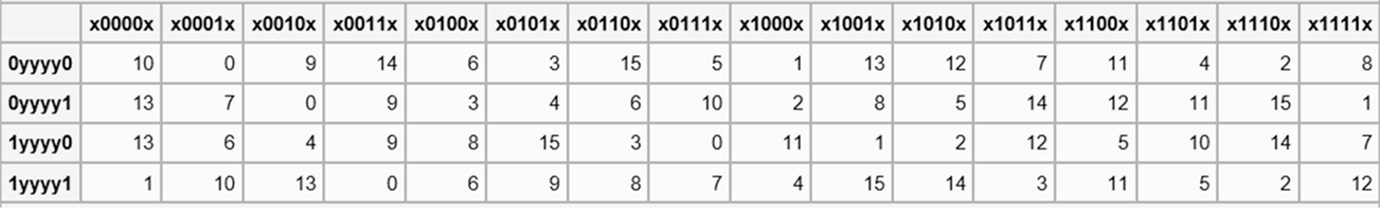
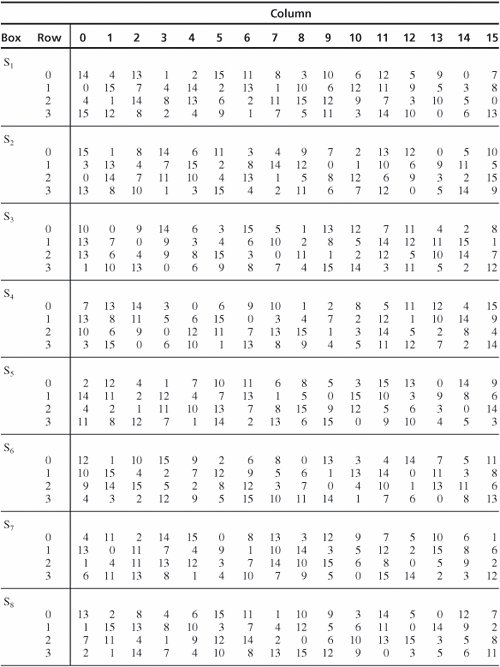
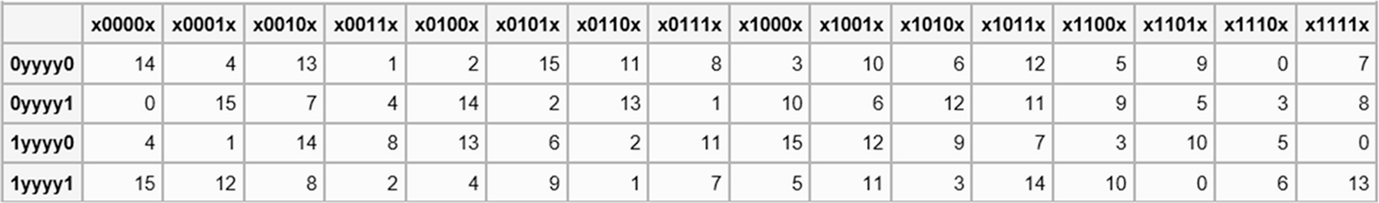
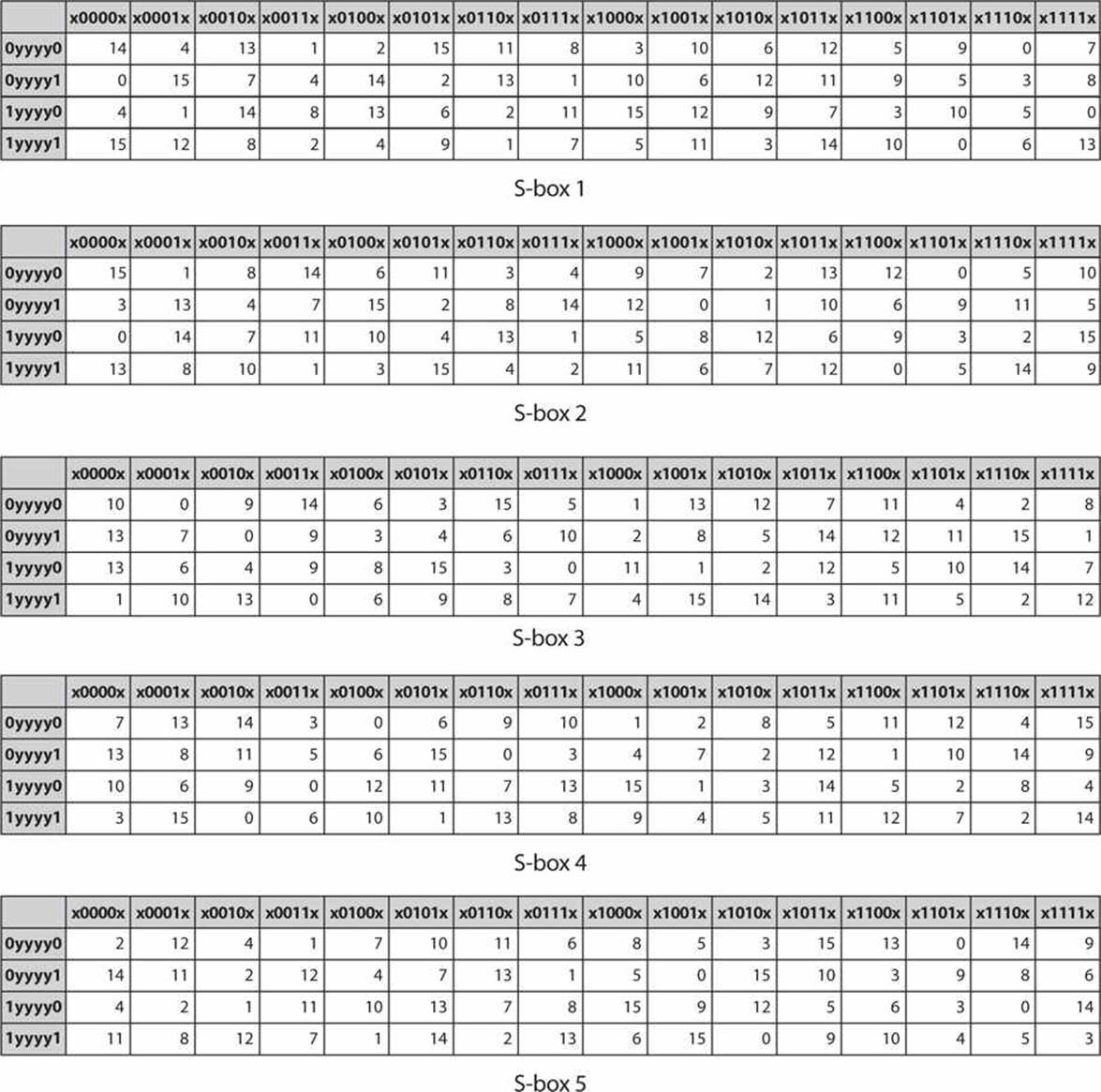
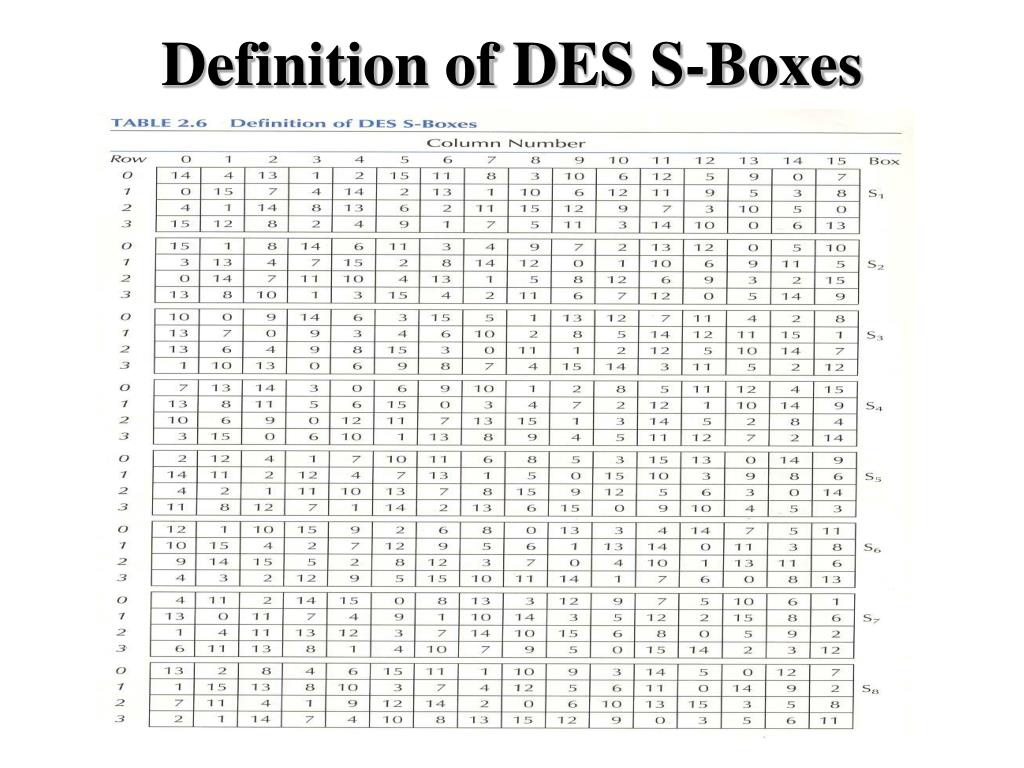
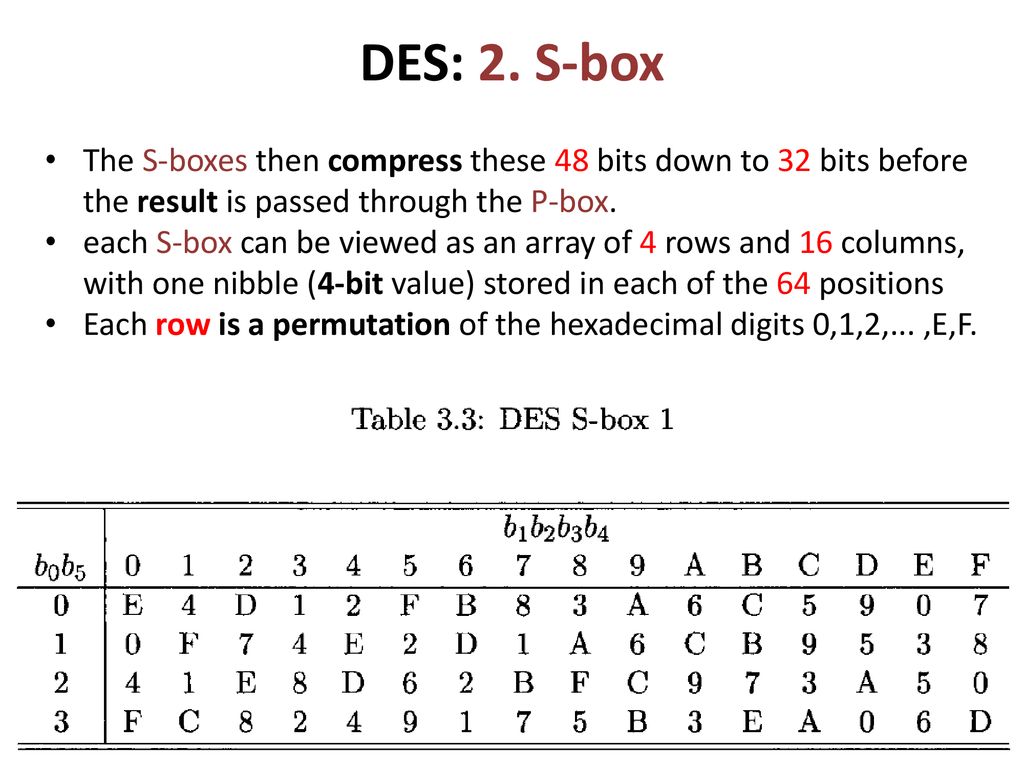
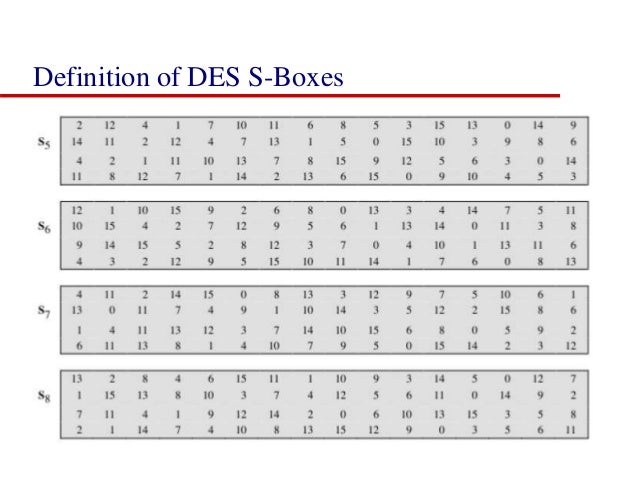
DES SBox(substitution box) 8 "SUbstitution boxes" or Sboxes;. MANCHESTER, NH – Last week NH’s Congressional Delegation sent off a letter to the USDA asking for them to investigate concerns brought to their attention by the NH Food Bank as part of the federal government’s Farmers to Families food box program Previously in Round 2 of the food distribution, boxes were supplied by Bostonbased Costa Fruit and Produce. 93 THE DES SBOXES, PBOX, AND INITIAL PERMUTATION (IP) Tables 94 to 911 specify the seven DES Sboxes, each with a 6bit input ( x0, x1, x2, x3, x4, x5, x6) and a 4bit output ( y0, y1, y2, y3 );.
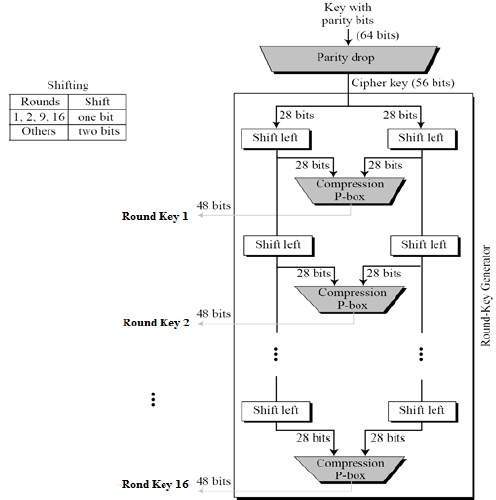
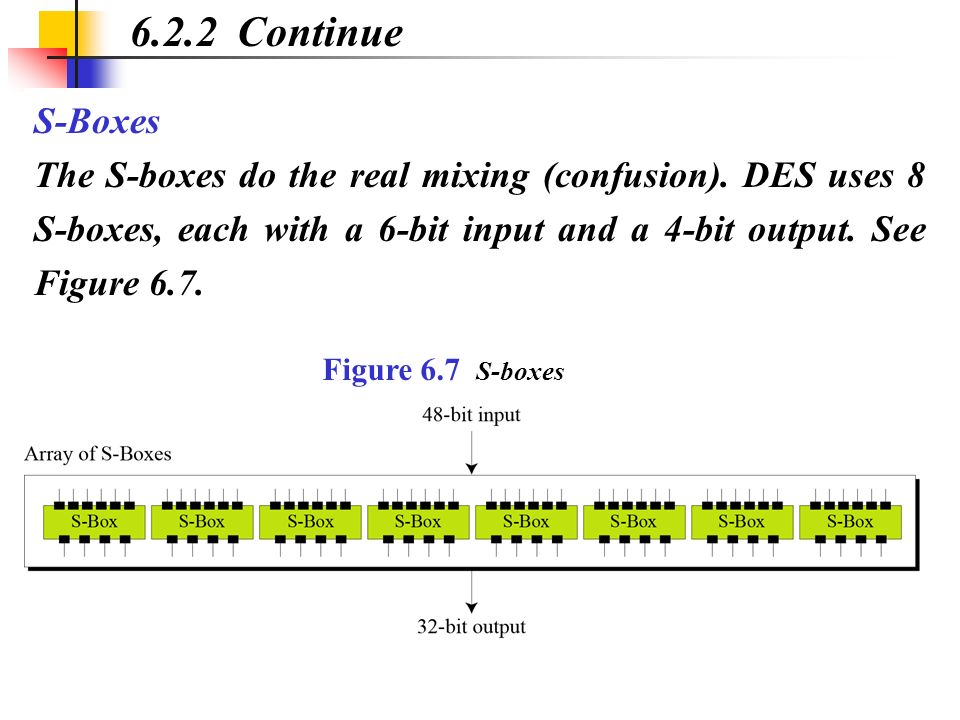
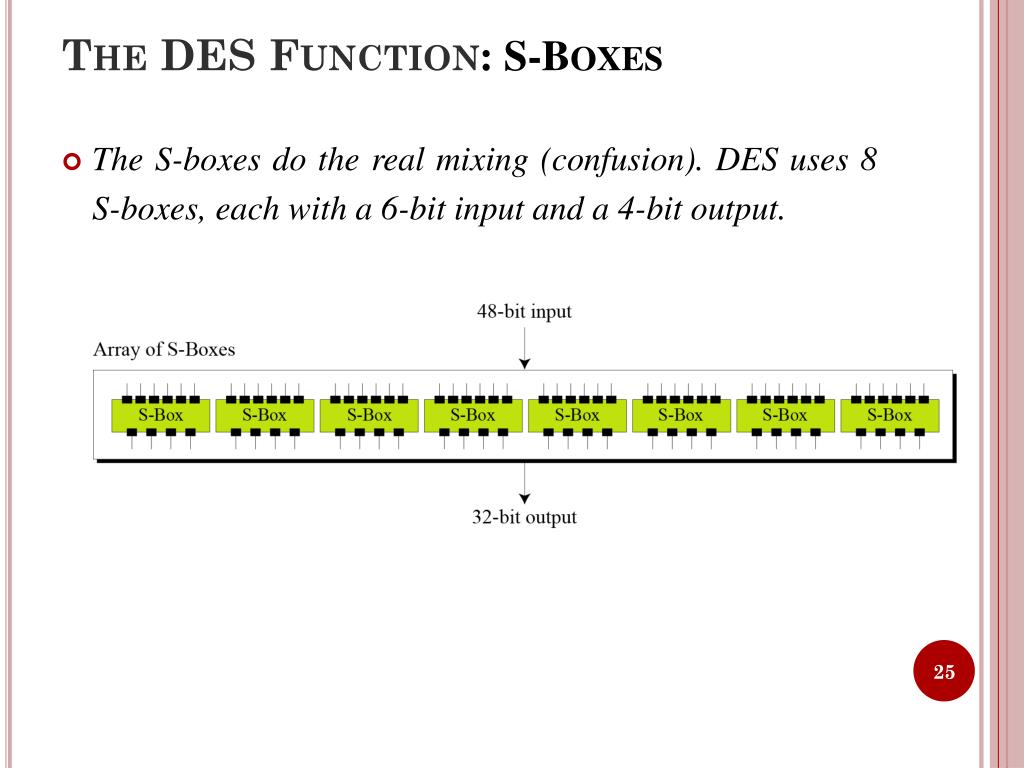
Data Encryption Standard (DES) 147 DES Function K I (48 bits) f ( R I–1, K I 48 bits) Out S S S S S S S S Straight Dbox Expansion Dbox SBoxes XOR 32 bits In 48 bits 32 bits 32 bits Fig 65 DES function The heart of DES is the DES function The DES function applies a 48bit key to the rightmost 32 bits (R I−1) to produce a 32bit output This function is. Substitution Boxes − The Sboxes carry out the real mixing (confusion) DES uses 8 Sboxes, each with a 6bit input and a 4bit output Refer the following illustration − The Sbox rule is illustrated below − There are a total of eight Sbox tables The output of all eight sboxes is then combined in to 32 bit section. • Good SBoxes from the cryptographic point of view when put in hardware are found to leak information, like power consumption etc • They thus lead to attacks called Side Channel Attacks, which can break ciphers in minutesafter all the hardwork • Then there are Algebraic Attacks • So, what to do?.
2 ways to show or hide check boxes to select items on Windows 10 Way 1 Show or hide check boxes to select items in the View menu Part 1 Show check boxes Open File Explorer (or This PC, Recycle Bin, etc), click View, tap Show/hide in the menu and choose Item check boxes in the submenu Part 2 Hide check boxes Access File Explorer, open View, click Show/hide in the menu and deselect. PO Box The Basics. What is the purpose of the S boxes in DES ANS Each row of a S box defines a from ROUTING AN network at Chisholm Institute of TAFE.
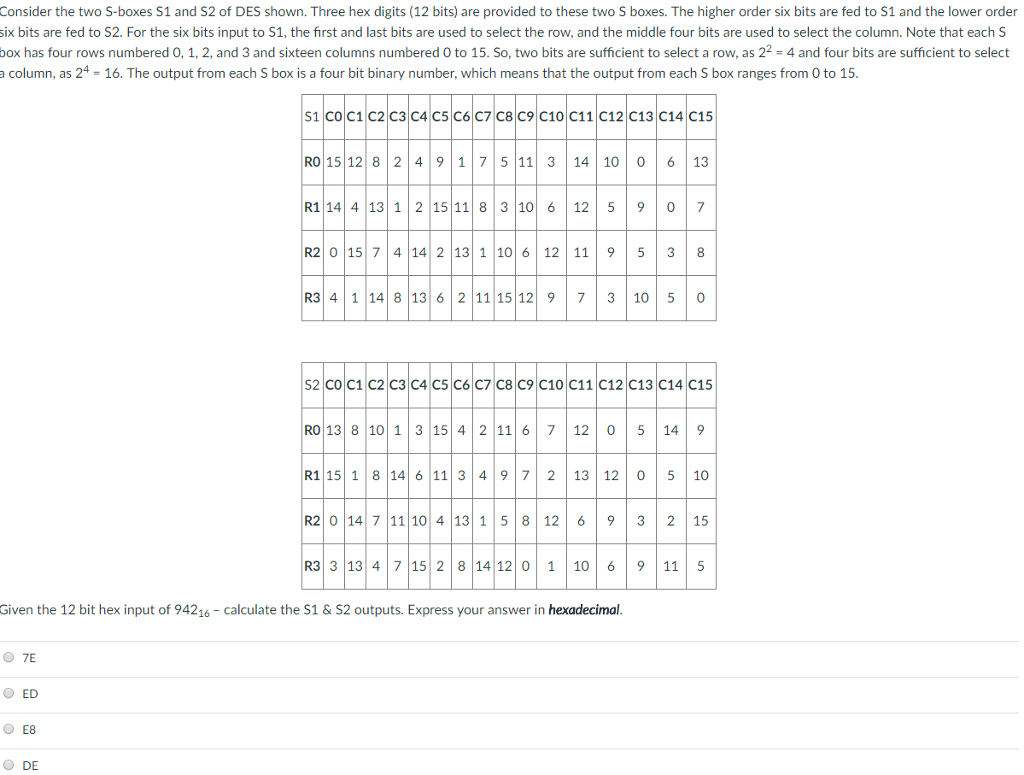
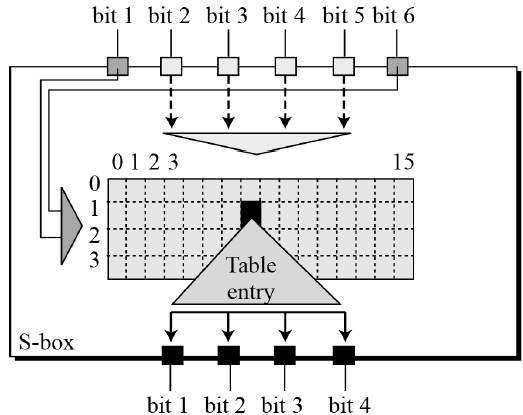
Open Research Problem(s) Criteria of Good SBox. (10 points) What is the purpose of the Sboxes in DES?. Column IndexRemaining 4 bits gives the column number;.
Every corner of the box is clean The color is an elegant, minimalist white Every part of the packaging is designed to be clean, simple and direct The design is simple in a world of clutter and constant sensory overstimulation Apple’s iconic sensory experience is the literal expression of the absence of eyegrabbing colors and images. IRA'S BOXES, Brno, Czech Republic 407 likes Trápí Vás přebytečná kila, cítíte se unaveni a nevíte si rady?. SBox(1) Row IndexThe combination of first and last bit gives the row number;.
What is the output if input is ?. Ticking the Plot Boxes in Andre Norton’s Yurth Burden Judith Tarr Mon Feb 15, 21 300pm 3 comments 2 Favorites I have said before that plotting was Andre Norton’s strength,. The Sboxes are the nonlinear part of DES that makes it difficult to break the algorithm and secure against linear and differential cryptanalysis the sboxes provide the "confusion" of data and.
In a study of Sboxes of DES, it is possible to compare the Sboxes to random Sboxes of the same size This is not a bad idea in general, as random Sboxes are expected to result in a secure cipher if they are big enough However, in the design of DES the Sboxes are very small, designed to fit within the very basic IC technology of the early. SDES or Simplified Data Encryption Standard The process of encrypting a plan text into an encrypted message with the use of SDES has been divided into multisteps which may help you to understand it as easily as possible Points should be remembered It is a block cipher. What is the purpose of SBox in DES?.
24F 0304, and repeal the rules cited as 04 NCAC 24D ;. Row = 10 = 2 ,Column = 0100 = 4. Note For a data set with an even number of values, the median is calculated as the average of the two middle values The data represented in box and whisker plot format can be seen in Figure 1 Figure 1 Box and Whisker Plot Example Left figure The center represents the middle 50%, or 50th percentile of the data set, and is derived using the lower and upper quartile values.
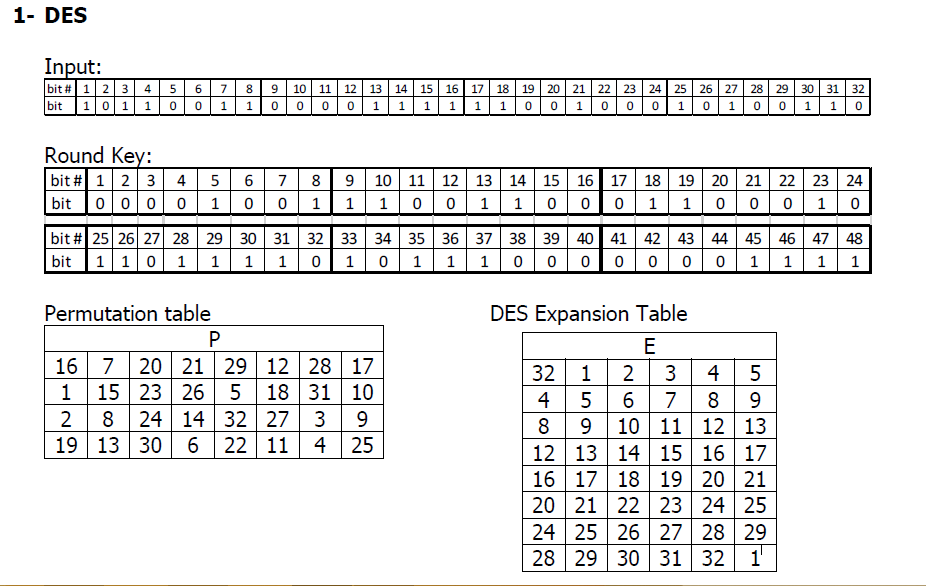
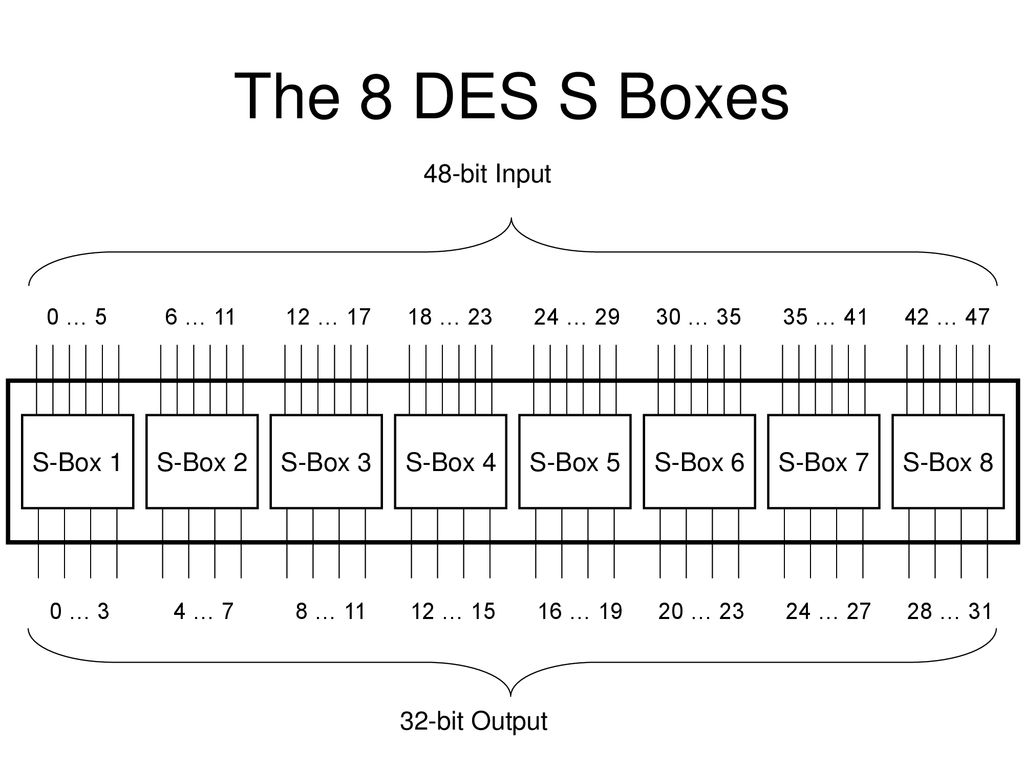
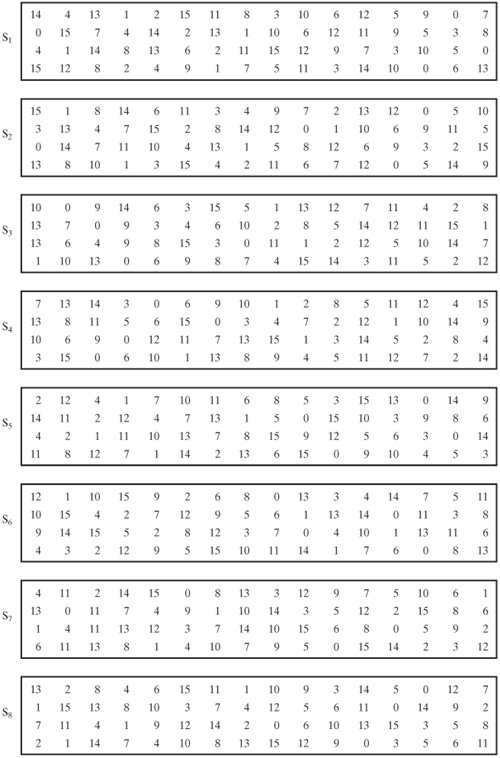
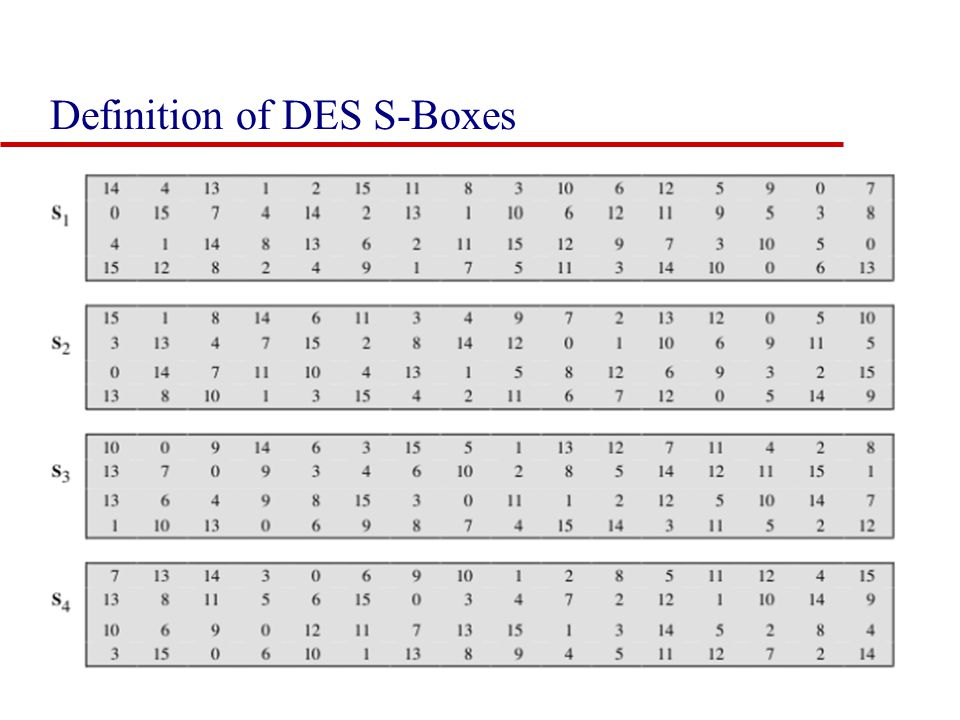
An S box takes as input 6 bits and gives 4 bits output that will replace the 6 bits input We have 8 groups of 6 bits B i, which will then be transformed in 8 groups of 4 bits, for a total of 32 bits K n ⊕E(R n1) = B 1 B 2 B 3 B 4 B 5 B 6 B 7 B 8, where each B i is a group of six bits We now compute S 1 (B 1)S 2 (B 2)S 3 (B 3)S 4 (B 4)S 5 (B 5)S 6 (B 6)S 7 (B 7)S 8 (B 8) The S 1 box works as follows. Answer this question 2 Mark question Asked in Cryptography 72 Our page and social groups College Note ourcollegenote Bsc CSIT Freshman Year (1st and 2nd semester) Bsc CSIT sophomore Year (3rd and 4th semester) Bsc CSIT Junior Year (5th and 6th semester). Versatile storage for All Sorts of Uses You can never have enough rugged storage Whether you’re storing tools, hauling game day gear, or coming up with literally hundreds of other uses Dee Zee’s universal poly plastic chest is like the Swiss Army Knife of utility chests.
Purpose, structure, relations, rewards, leadership and helpful mechanisms. The US Postal Service is removing mailboxes in several American cities as the threat of violence in state capitols surrounding Presidentelect Joe Biden’s Wednesday inauguration continues to. PO Boxes USPS.
The mail box that gives back!. Versatile storage for All Sorts of Uses You can never have enough rugged storage Whether you’re storing tools, hauling game day gear, or coming up with literally hundreds of other uses Dee Zee’s universal poly plastic chest is like the Swiss Army Knife of utility chests. Box 1 Ordinary Business Income (Loss) 12 Box 2 Net Rental Real Estate Income (Loss) 12 Box 3 Other Net Rental What s New General Instructions Purpose of Schedule K1 Inconsistent Treatment of Items Errors Decedent's Schedule K1 Sale of S Corporation Stock International Boycotts.
1 Solutions In general, an Sbox takes some number of input bits, m , and transforms them into some number of output bits, n , where n is not necessarily equal to m. The eight Sboxes of DES were the subject of intense study for many years out of a concern that a backdoor (a vulnerability known only to its designers) might have been planted in the cipher The Sbox design criteria were eventually published (in Coppersmith 1994 ) after the public rediscovery of differential cryptanalysis , showing that they had been carefully tuned to increase resistance against this specific attack. S02LE(S) We call M i(x c.
DES Proposed Rules Notice is hereby given in accordance with GS 150B212 that the Department of Commerce Division of Employment Security intends to adopt the rules cited as 04 NCAC 24D 01, 06, amend the rules cited as 04 NCAC 24D 0102, 02, 03;. If the primary purpose of your job is to get a paycheck and there’s not much personal meaning in what you do — then you’re most likely not living your highest purpose If you’re counting the days until the next threeday weekend or sixday vacation — that’s probably a sign that you’re “off purpose”. Instructor We're taking the first big stepinto the structure of modern block ciphersNow we'll talk about Sboxes and PboxesSubstitution boxes and permutation boxesare key components of modern block ciphersSboxes are nonlinear transformationsof a few input bits that provide confusionand Pboxes simply shuffle the input bits aroundto provide diffusion as we've talked about beforeSo, the purpose of the Sbox, as I said,is to provide confusionThis is.
S 1 (b 1)s 2 (b 2)s 3 (b 3)s 4 (b 4)s 5 (b 5)s 6 (b 6)s 7 (b 7)s 8 (b 8) = 0101 1100 1000 0010 1011 0101 1001 0111 The final stage in the calculation of f is to do a permutation P of the S box output to obtain the final value of f. Boxesnet is the leader in providing quality custom cardboard boxes, corrugated boxes, shrink film, mailing tubes, carton sealing tape, stretch wrap, and stock packaging solutions. 1 Solutions In general, an Sbox takes some number of input bits, m , and transforms them into some number of output bits, n , where n is not necessarily equal to m.
Each Sbox maps 6 bits to 4 bits;. The boxes in this case may have reflected his feelings about the entirety of his life Example 3 A woman dreamed of pouring water into a empty box with a hose In waking life she was considering leaving her cheating husband The box in this case may have reflected her feelings about the entirety of her marriage as she considered ending it. There’s a “massive movement in wellness today,” and some retail boxes are being converted into this opportunity for health and wellness, says Anjee Solanki, national director for US retail.
Buxton's Boxes Self Storage, Ewing, NJ 759 likes · 5 talking about this · 53 were here Buxton's Boxes Self Storage is a Family Owned and Operated facility Offering storage in both climate and. Substitution boxes (Sboxes) This table lists the eight Sboxes used in DES Each Sbox replaces a 6bit input with a 4bit output Given a 6bit input, the 4bit output is found by selecting the row using the outer two bits, and the column using the inner four bits. Boxesnet is the leader in providing quality custom cardboard boxes, corrugated boxes, shrink film, mailing tubes, carton sealing tape, stretch wrap, and stock packaging solutions.
PO Boxes USPS. Utilizing Weisbord’s Six Box Model can help only if the provider acts upon the diagnosis Having used the six boxes pattern, the problems of the organization are identified and their quality improved The components of the six boxes pattern are namely;. The sbox is designed to be resistant to known cryptanalytic attacks Specifically, the Rijndael developers sought a design that has a low correlation between input bits and output bits, and the property that the output cannot be described as a simple mathematical function of the input In addition, the sbox has no fixed points (sbox(a) = a) and.
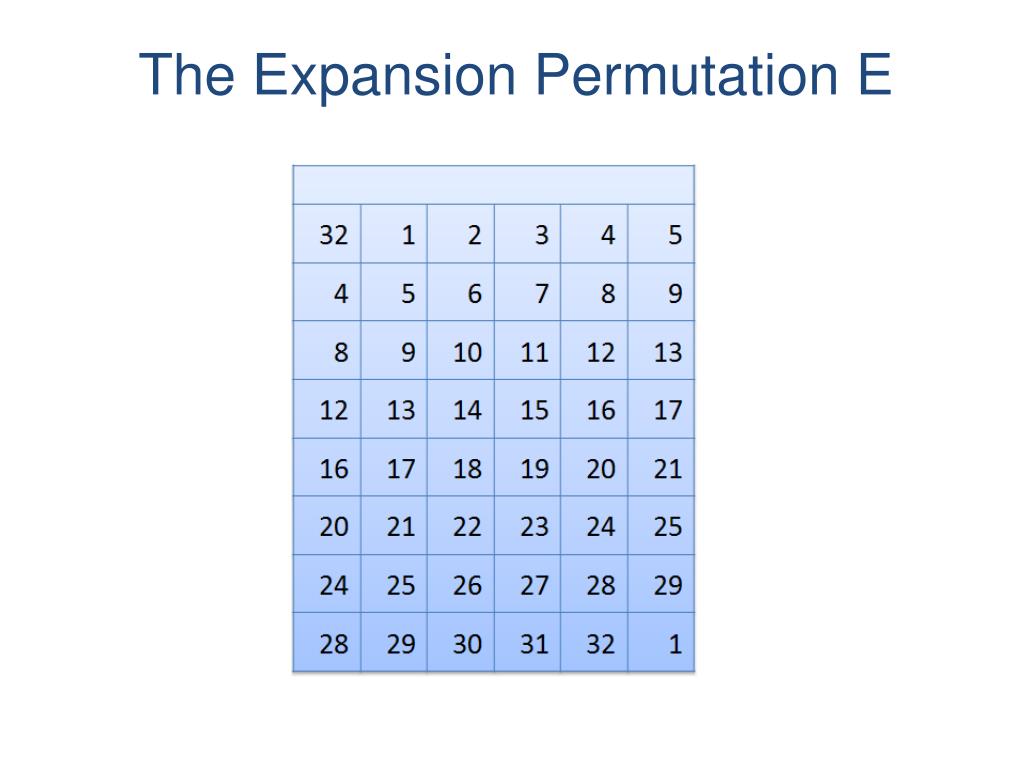
Each table contains 4 rows and 15 columns, where Bits ( x0, x6) identify a row in the table, and. In cryptography, an SBox (Substitutionbox) is a basic component of symmetric key algorithms which performs substitution In block ciphers, they are typically used to obscure the relationship. The Sboxes take 4 bits as input and produce 3bits of output The first bit of the input is used to select the row from the Sbox, 0 for the first row and 1 for the second row The last 3 bits are used to select the column Example Let the output from the expander function be So 1101 will be the input for the S1 box and 0010 will be the input for the S2 box.
Fruit, the fleshy or dry ripened ovary of a flowering plant, enclosing the seed or seeds The principal purpose of the fruit is the protection and dispersal of the seed, though some seedless fruits have been developed Learn more about the definition of fruit, fruit types, the importance of fruit, and seed dispersal. IRA´S BOXES je první a nejdéle působící firma v oblasti krabičkové diety v Brně!. The ends of most boxes of aluminum foil and plastic wrap come with tiny tabs with perforated edges Many consumers have likely seen this feature without thinking twice about it, but it's there for.
Block Ciphers
S Box Design Springerlink

How Can Des Have 6x4 S Boxes And Still Be Reversible Theoretical Computer Science Stack Exchange

Lightweight Ciphers And Their Side Channel Resilience

Function S Box S1 In The Des Algorithm Represented As A Table And Its Download Scientific Diagram
What Is 3des Encryption And How Does Des Work Comparitech
S Box Design Springerlink

Lightweight Ciphers And Their Side Channel Resilience
Data Encryption Standard Tutorialspoint

2 Datapath Of The Serialized Des Asic With Original S Boxes Download Scientific Diagram

Discuss The Major Steps In S Box Design

1 Compute The 4bit Output Using The Given S Boxes Chegg Com
Data Encryption Standard Tutorialspoint
Information And Data Security Block Cipher And The Data Encryption St

9 3 The Des S Boxes P Box And Initial Permutation Ip Computer Security And Cryptography Book
Http Www Uobabylon Edu Iq Eprints Publication 2 6033 Pdf

Ch03 Testbank Crypto6e
Http Cse Iitkgp Ac In Debdeep Courses Iitkgp Crypto Slides Dc Pdf

A Complete Description Of Data Encryption Standard Des By Ahsan Barkati Medium
1 How Many Bits Of Output Are Produced After Subs Chegg Com
Schemes Of Block Cipher Exam Nights Live
Http Www Cs Man Ac Uk Banach Comp Info Courseslides Wk2 1 Des Pdf

Robustness Of S Boxes Used By Des Download Table
Cryptomeria Cipher Wikipedia
6 1 2 Overview Des Is A Block Cipher As Shown In Figure Ppt Video Online Download

Ppt On Des Powerpoint Slides
Link Springer Com Content Pdf 10 1007 0 387 0 56 Pdf

Ppt On Des Powerpoint Slides
Solved Consider The Two S Boxes S1 And S2 Of Des Shown T Chegg Com
Q Tbn And9gcqapowi2tt9xae7n8ibd3tbzbujci5pfuypknu9 Xztuxe9cuie Usqp Cau

If The First Key Bit Is Flipped Which Des S Boxes Are Affected Cryptography Stack Exchange
Q Tbn And9gcrkf7hktq2x0v Cofzbl Jg Hrfjci8qps8wyyhmjik1ssxscvm Usqp Cau

Solved This Set Of Homework Is For The Contents Covered I Chegg Com
Http Www Cs Man Ac Uk Banach Comp Info Courseslides Wk2 1 Des Pdf

Data Encryption Standard Wikipedia
A Extend The Input To 48 Bits Using Des Expansion Chegg Com

6 Data Encryption Standard Des Pdf Free Download

Simplified Data Encryption Standard S Des
Ppt Information Security Cryptography Part 2 Powerpoint Presentation Id

Lightweight Ciphers And Their Side Channel Resilience
Section 12 2 Symmetric Encryption Security In Computing 4th Edition

Pdf What Do Des S Boxes Say To Each Other Semantic Scholar

What Is S Meant By S Box Row And Column In Des Cryptography Stack Exchange
S Box Design Springerlink
S Box Design Symmetric Ciphers And Hashes Modern Cryptography Applied Mathematics For Encryption And Informanion Security 16
Ppt Data Encryption Standard Des Powerpoint Presentation Free Download Id

Cryptography And Network Security Chapter 3 Ppt Download
2
Q Tbn And9gct0abdt09pq1t3tk4maupgmxojjcotjx41l5h7t410 Usqp Cau

The Design Of Cryptographic S Boxes Using Csps Florida Institute
Chapter 3 Symmetric Key Crypto Ppt Download

Des Supplementary Material Wikipedia Cryptography Secure Communication
Data Encryption Standard
2
Feistel Cipher Des Ppt Download

Function S Box S1 In The Des Algorithm Represented As A Table And Its Download Scientific Diagram
A Novel Encryption Scheme For High Contrast Image Data In The Fresnelet Domain
Referring To The Lecture Notes On Des There Are One Expansion Permutation Table1 Eight Substitution S Boxes And One Permutation P Box Table 2 Course Hero

Data Encryption Standard Des Set 1 Geeksforgeeks

Table 2 5 From The Block Cipher Companion Semantic Scholar

Rijndael S Box Wikipedia

Scheme Presenting An Application Of S Boxes In The Des Algorithm On Download Scientific Diagram
Information And Data Security Block Cipher And The Data Encryption St

Pdf What Do Des S Boxes Say To Each Other Semantic Scholar
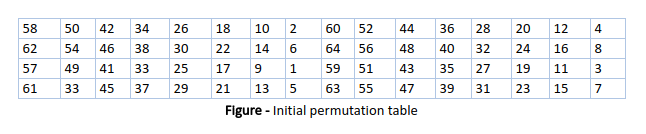
Data Encryption Standard Des Set 1 Geeksforgeeks

Data Encryption Standard Des Set 1 Geeksforgeeks

Pdf What Do Des S Boxes Say To Each Other Semantic Scholar
Ppt Modern Block Ciphers Powerpoint Presentation Free Download Id
Section 3 2 The Data Encryption Standard Cryptography And Network Security 4th Edition
Cryptography And Network Security Chapter 3 Ppt Download

Ppt On Des Powerpoint Slides
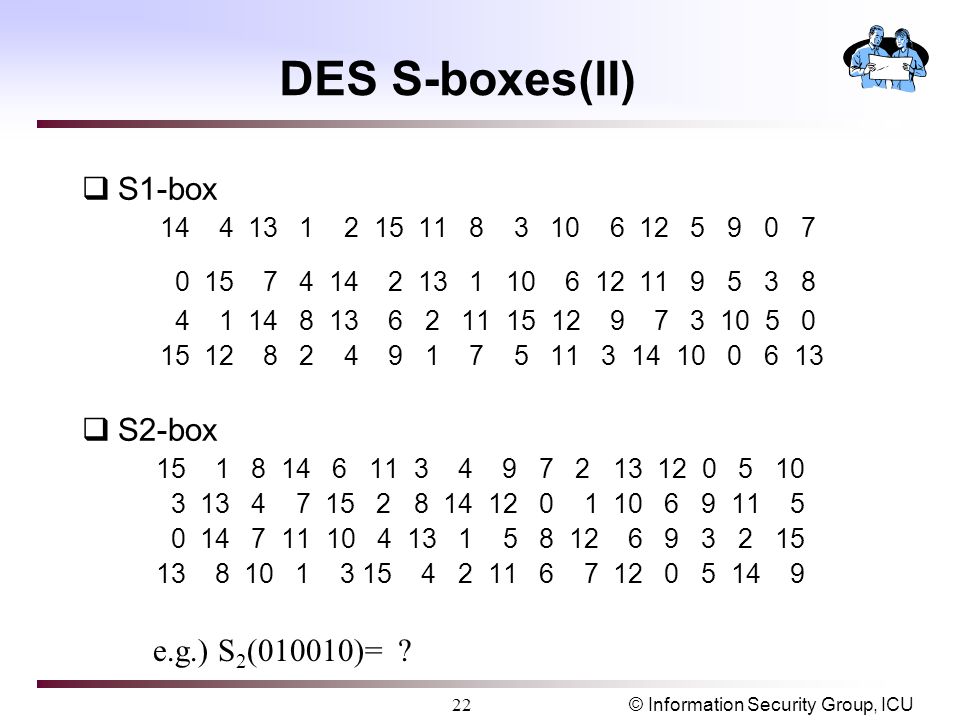
Information Security Group Icu1 Block Cipher Introduction Des Description Feistel S Box Exhaustive Search Dc And Lc Modes Of Operation Aes Description Ppt Download
Www Sans Org Reading Room Whitepapers Vpns S Box Modifications Effect Des Like Encryption Systems 768

What Is The Data Encryption Standard Des Encyclopedia
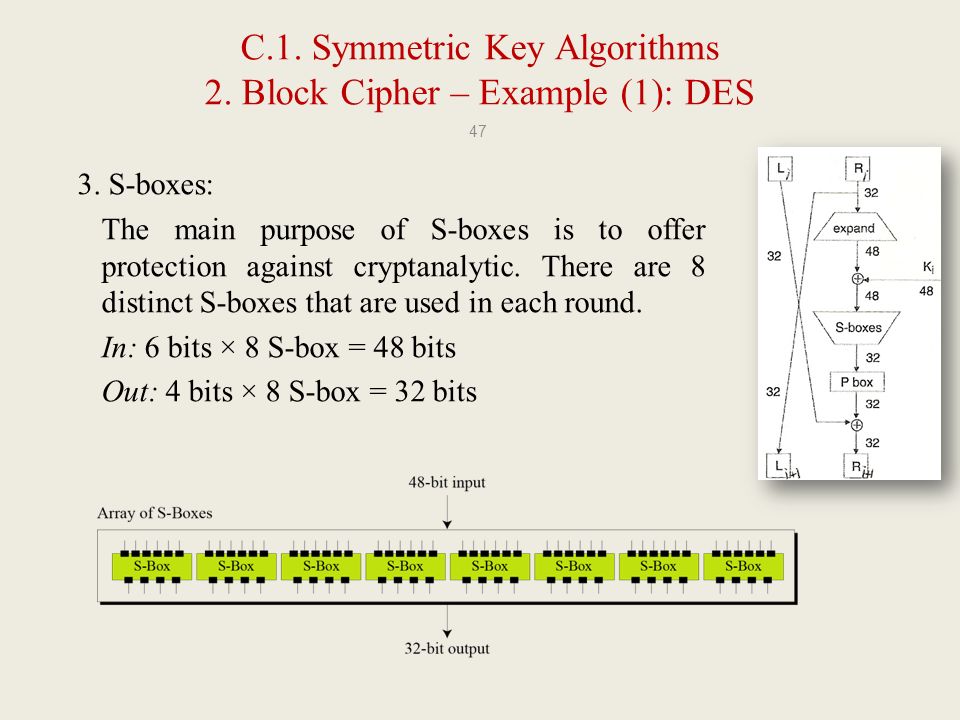
Cpit 425 Chapter Three Symmetric Key Cryptography Ppt Download

Des Cipher

6 Data Encryption Standard Des Pdf Free Download

File Des S Box Jpg Wikimedia Commons

How To Teach Des Using Python The Easy Way Part 2 Round Function F By Ajit Kumar Medium
Http Web Abo Fi Ipetre Crypto Lecture3 Pdf
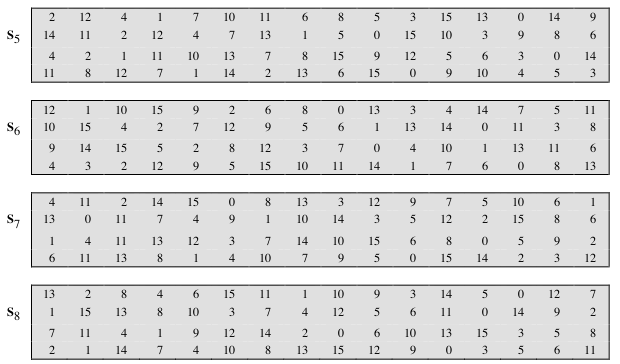
8 Data Encryption Standard
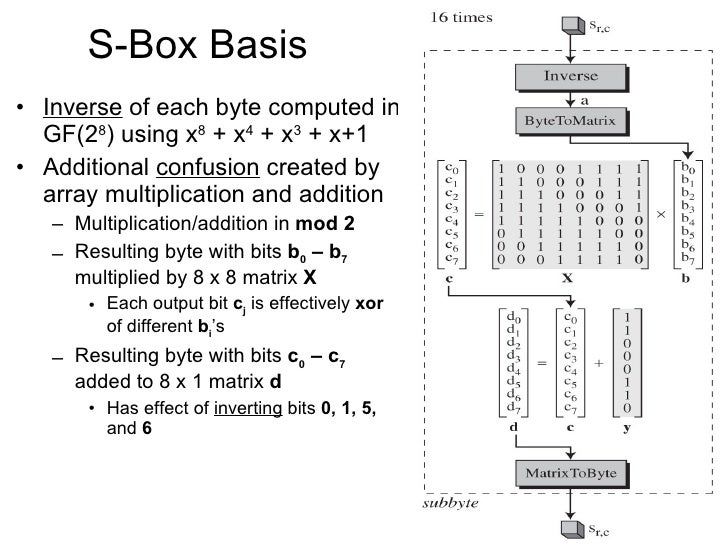
Network Security Lec4

Function S Box S1 In The Des Algorithm Represented As A Table And Its Download Scientific Diagram
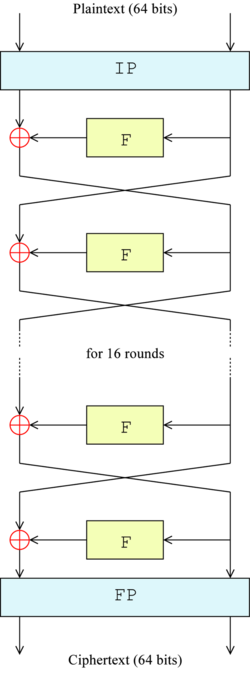
Data Encryption Standard Wikipedia

Data Encryption Standard Des Ppt Video Online Download
Performance Factor Of Des S Boxes Bitslice Des S Boxes Vs Download Scientific Diagram

Des Data Encryption Standard Anu Vazhayil

Pdf Plaintext Recovery In Des Like Cryptosystems Based On S Boxes With Embedded Parity Check Semantic Scholar
Www Sans Org Reading Room Whitepapers Vpns S Box Modifications Effect Des Like Encryption Systems 768

S Box Basic Question Cryptography Stack Exchange

Parametric Comparison Of Emds Algorithm With Some Symmetric Cryptosystems Sciencedirect
Q Tbn And9gcrkf7hktq2x0v Cofzbl Jg Hrfjci8qps8wyyhmjik1ssxscvm Usqp Cau
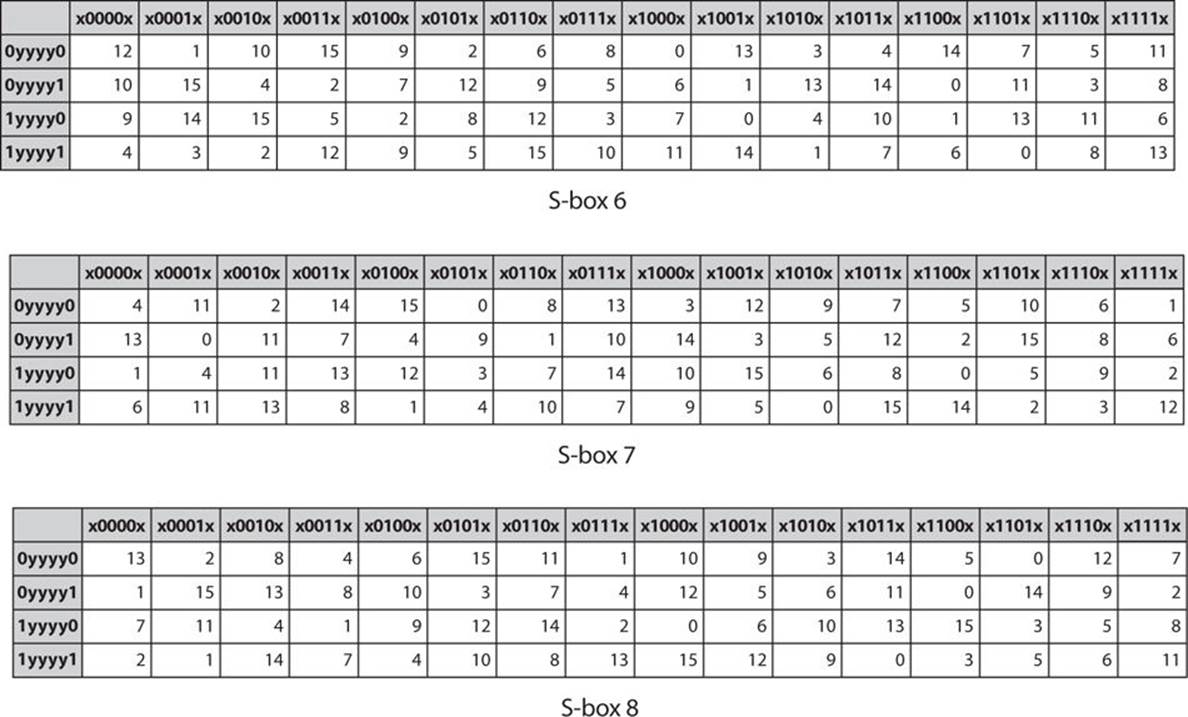
S Box Design Symmetric Ciphers And Hashes Modern Cryptography Applied Mathematics For Encryption And Informanion Security 16

Des Algorithm S Box Learning Programmer Sought

Schemes Of Block Cipher Exam Nights Live

Des Decryption And Weaknesses Of Des S Box Properties Youtube
Data Encryption Standard Wikipedia

9 3 The Des S Boxes P Box And Initial Permutation Ip Computer Security And Cryptography Book



