S Box Aes Example
An Example Of The Aes S Box 4 3 Shift Rows Download Scientific Diagram
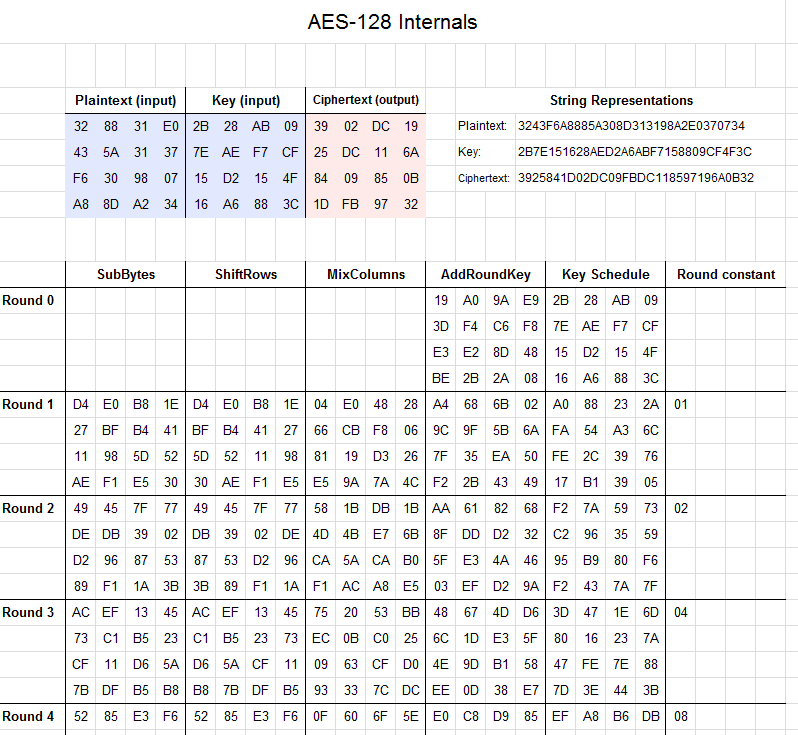
Aes Cipher Internals In Excel
A Novel Byte Substitution Architecture For The Aes Cryptosystem
Http Euler Ecs Umass Edu Ece597 Pdf Crypto Part4 Aes Pdf
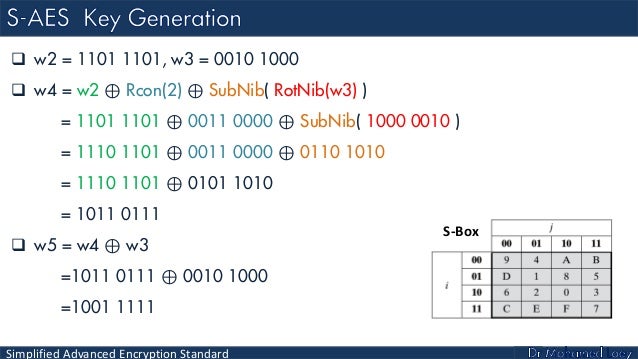
Computer Security Lecture 5 Simplified Advanced Encryption Standard
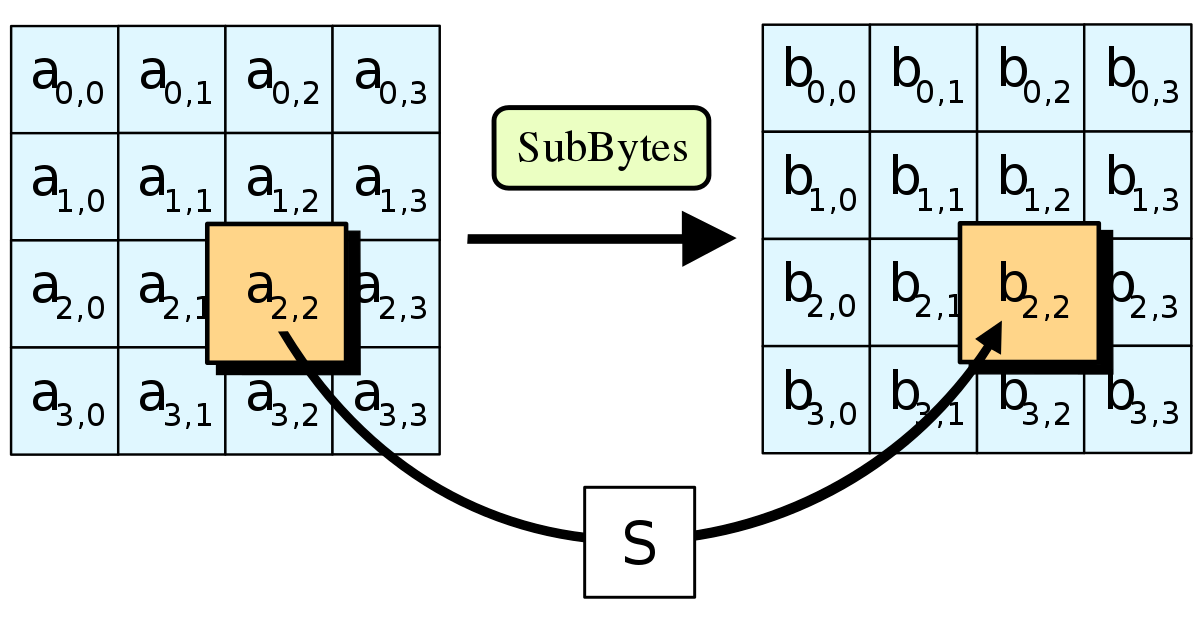
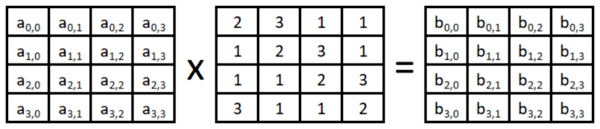
Advanced Encryption Standard Wikipedia
AES, for example, is 128 bits long Meaning, AES will operate on 128 bits of plaintext to produce 128 bits of ciphertext Like almost all modern encryption algorithms, AES requires the use of keys during the encryption and decryption processes AES supports three keys with different lengths 128bit, 192bit, and 256bit keys.

S box aes example. SBox Example using Java Sunday, June 09, 13 Posted by Bipin Rupadiya Write a programs to simulate encryption and decryption technique using SBox, algorithm development and Communication between client and server will be done using Java server socket programming. Table) is used to compute the Sbox that utilizes more memory, which increases area, power of AES and thus disadvantage of this is unbreakable delay and latency because of finite time of the architecture In memoryless method, implementation of SBox using LUT and SOP approach is fast but effective in cost. I found the Sage code for the AES Sbox online It is given below However, I do not know how to find the coefficients of a to h using Lagrange interpolation They seem to appear from nowhere, but I am told they are the result of Lagrange interpolation I only know how to apply Lagrange interpolation if I have a function and some given points.
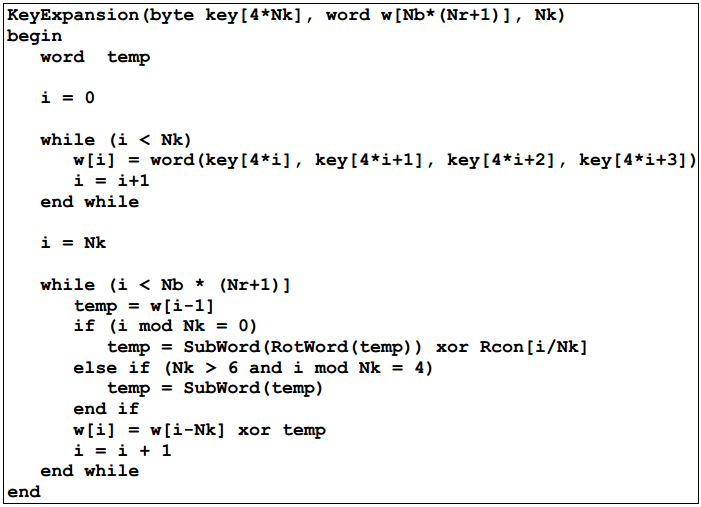
The standard concludes with several appendices that include stepbystep examples for Key Expansion and the Cipher, example vectors for the Cipher and Inverse Cipher, and a list of references 2 Definitions 21 Glossary of Terms and Acronyms The following definitions are used throughout this standard AES Advanced Encryption Standard. A more refined way of implementing the SBox is to use combinational logic Such examples of work that implements the SBox using this method were 1, 3 and 5 This SBox has the advantage of having small area occupancy, in addition to be capable of being pipelined for increased performance in clock frequency The SBox architecture. (C) Pass left 4 bits through S0 and right four bits through S1 0 1 1 1 (D) Apply P4.
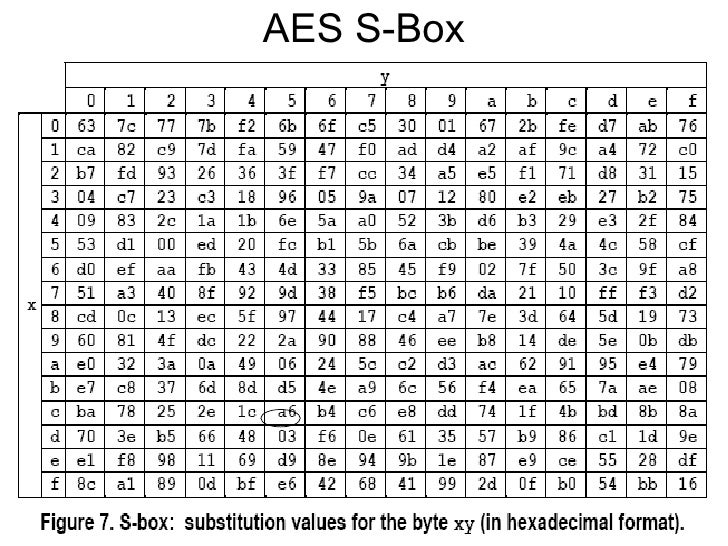
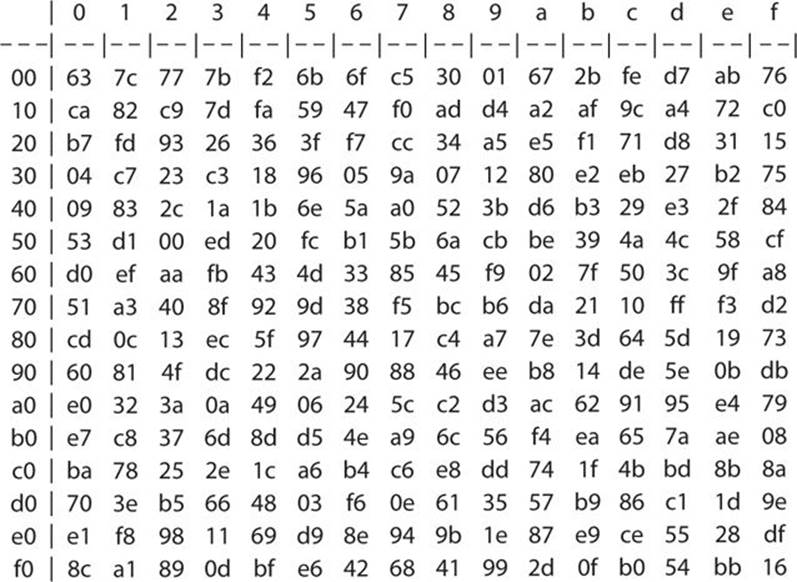
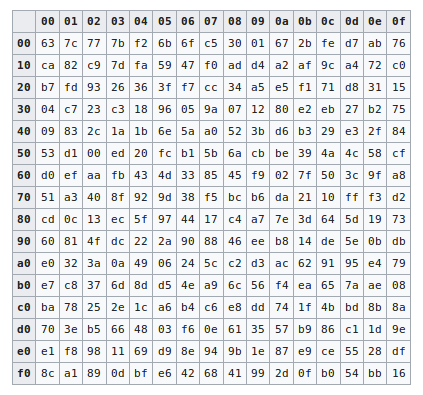
Now, the AES algorithm substitutes every byte with a code according to a preestablished table called the Rijndael Sbox It looks like this According to the table, an element like 19 becomes d4, e9 becomes 1a, and so on. If the value of s had a. Be aware that the following example is a simplification, but it gives you a general idea of how AES works Unfortunately, there isn’t enough coffee in the world to make most people want to get through the more complicated aspects of AES Normally, the process is performed in binary and there’s a lot more maths.
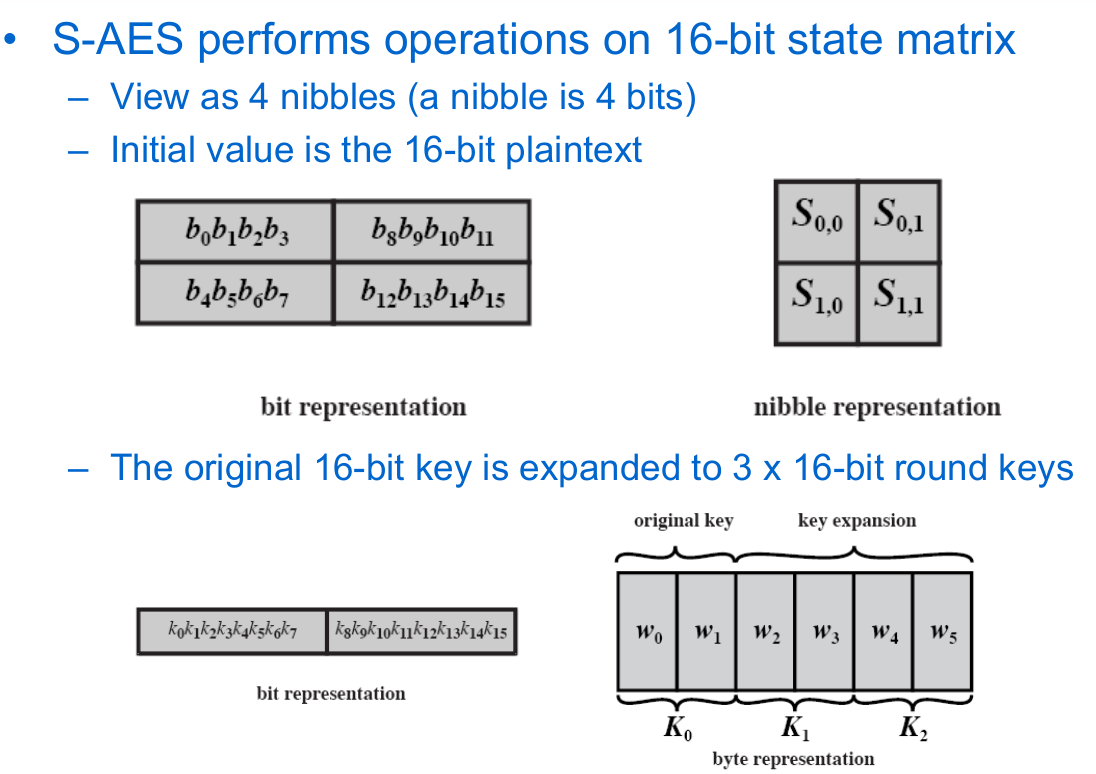
AES Example Round 1, Substitution Bytes current State Matrix is 0 B B @ 00 3C6E 47 1F 4E 22 74 0E 08 1B 31 54 59 0B1A 1 C C A substitute each entry (byte) of current state matrix by corresponding entry in AES SBox for instance byte 6E is substituted by entry of SBox in row 6 and column E, ie, by 9F this leads to new State Matrix 0 B B @ 63 EB 9F A0 C0 2F 93 92. They used the action of symmetric group 𝑆8 on AES Sbox and generated 403 𝑆8 Sboxes The Sbox have a vital role in AES, therefore most of the work is focused on its improvement In this paper, we proposed new 𝑆16 Sbox using the action of a 16 × 16 permutation matrix, from the symmetric group of order 16!, on AES Sbox. Advanced Encryption Standard (AES) Keywords Advanced Encryption Standard (AES), Basic Structure of AES, 1 Substitute Bytes, 2 Shift Rows, 3 Mix Columns, AES Arithmetic, 4 Add Round Key, AES Key Expansion, AES Example Key Expansion, AES Example Encryption, AES Example Avalanche, AES Decryption, Homework 5 Created Date 9/14/11 AM.
The corresponding output would be "1001". Suppose I have made changes in AES by removing the nonlinear Sbox and replacing it with a linear function I know that by removing the nonlinearity of the Sbox I'm making the AES vulnerable to. Sbox is a unique nonlinear operation in Rijndael, one encryption algorithm chosen as AES, and it determines the performance of AES In this paper, the weaknesses in complexity and security of AES.
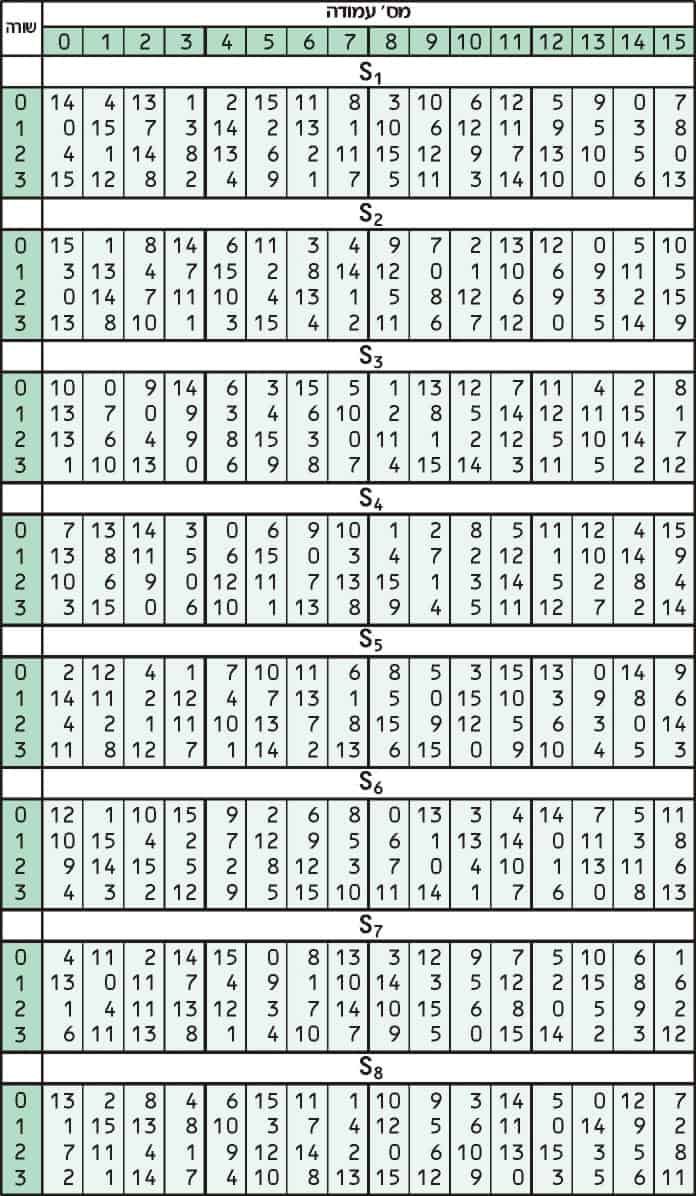
Return (AES Sbox b for b in word) def key_schedule (self) expanded = expanded extend (map (ord, self key)) for i in range (self nk, self nb * (self nr 1)) t = expanded (i1) * 4 i * 4 if i % self nk == 0 t = xor ( AES sub_word ( AES rot_word (t) ), (AES Rcon i // self nk, 0, 0, 0) ) elif self nk > 6 and i % self nk == 4 t = AES sub_word (t). Suppose I have made changes in AES by removing the nonlinear Sbox and replacing it with a linear function I know that by removing the nonlinearity of the Sbox I'm making the AES vulnerable to. One good example is this 6×4bit SBox from DES (S 5) Given a 6bit input, the 4bit output is found by selecting the row using the outer two bits (the first and last bits), and the column using the inner four bits For example, an input " 0 1101 1 " has outer bits " 01 " and inner bits "1101";.
Sbox The 48bit output obtained by Xor step is reduced to 32 bit again Pbox Here the 32bit result obtained from Sbox is again permuted, which result in 32bit permuted output Definition of AES (Advanced Encryption Standard) Advanced Encryption Standard (AES) is also a symmetric key block cipher. An example of a nonlinear transformation algorithm is Advanced Encryption Standard (AES) In this Rijndael algorithm, sbox is the most important part because of the encryption algorithm which means that it requires the key to be the same length as the message to be encoded. The SBox is computed from inverse of input to the original input The example of Affine Transformation is given by Consider an example, 4X4 matrix is a input text and s1 s2 s3 s4 is the inverse of the input the remaining one 0 1 1 0 is a cipher key The output is a z1 z2 z3 z4.
Sbox and pbox are the technologies that are used in cryptographic algorithms This is just small explanation about the Sbox used by the AES cryptographic algorithm The Sbox is generated by determining the multiplicative inverse for a given n. Small portable AES128/192/256 in C Contribute to kokke/tinyAESc development by creating an account on GitHub. Advanced Encryption Standard (AES) which works on a 128 bit data encrypting it with 128, 192 or 256 bits of keys for ensuring security In this paper, we compare AES encryption with two different SBoxes Sbox with 256 byte lookup table (Rijndael SBox) and AES with 16 byte SBox (Anubis SBox).
For example, an app that uses AES256 instead of AES128 might drain your phone battery a bit faster Luckily, current technology makes the resource difference so minuscule that there is simply no reason not to use 256bit AES encryption. AdvancedEncryptionStandardAlgorithm / src / AESjava / Jump to Code definitions AES Class main Method deepCopy2DArray Method subKey Method subBytes Method invSubBytes Method shiftRows Method leftrotate Method invShiftRows Method rightrotate Method mixColumns Method mcHelper Method mcCalc Method invMixColumns Method invMcHelper Method. SBox Example using Java Sunday, June 09, 13 Posted by Bipin Rupadiya Write a programs to simulate encryption and decryption technique using SBox, algorithm development and Communication between client and server will be done using Java server socket programming.
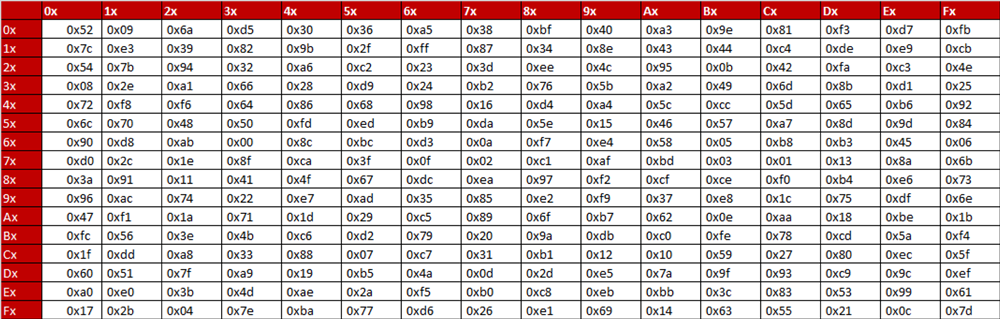
The AES SBox implements inverse multiplication in Galois Field 2 8 The AES SBox is shown in the Table below To read this Table, the byte input is broken into two 4bit halves The first half determines the row and the second half determines the column For example, the SBox transformation of 35 or 0x23 can be found in the cell at the intersection of the row labeled and the column labeled 03. Questions of SBox Design As previously noted, the basic principle of differential cryptanalysis is that the cipher being attacked has a characteristic if there exists a constant X such that given many pairs of plaintexts A, B, such that B = A xor X, if a certain statement is true about the key, E(B,k) = E(A,k) xor Y for some constant Y will be true with a probability somewhat above that. How does AES work?.
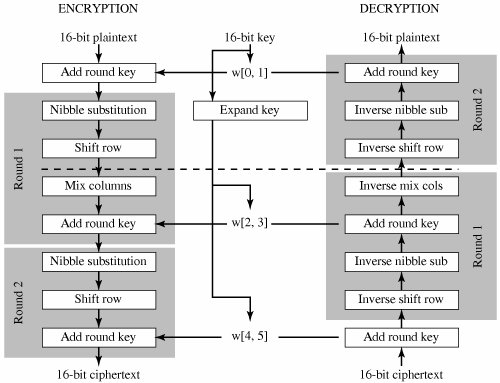
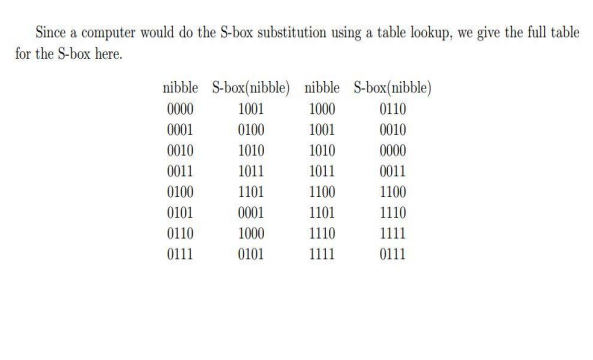
An example of a nonlinear transformation algorithm is Advanced Encryption Standard (AES) In this Rijndael algorithm, sbox is the most important part because of the encryption algorithm which means that it requires the key to be the same length as the message to be encoded. 93 THE DES SBOXES, PBOX, AND INITIAL PERMUTATION (IP) Tables 94 to 911 specify the seven DES Sboxes, each with a 6bit input (x0, x1, Selection from Computer Security and Cryptography Book. Simplified AES 16bit block 16bit key 4 x 4 Sbox Its Linear and Differential Cryptanalysis”Cryptologia 27(12), 148 – 177 Sbox Input nibble Output nibble 0000 1001 0001 0100 0010 1010 0011 1011 0100 1101 0101 0001 0110 1000 0111 0101 1000 0110 1001 0010 1010 0000 1011 0011 1100 1100 1101 1110 1110 1111 1111 0111.
If the value of s had a. The SBox is computed from inverse of input to the original input The example of Affine Transformation is given by Consider an example, 4X4 matrix is a input text and s1 s2 s3 s4 is the inverse of the input the remaining one 0 1 1 0 is a cipher key The output is a z1 z2 z3 z4. SBox Example using Java Sunday, June 09, 13 Posted by Bipin Rupadiya Write a programs to simulate encryption and decryption technique using SBox, algorithm development and Communication between client and server will be done using Java server socket programming.
Return (AES Sbox b for b in word) def key_schedule (self) expanded = expanded extend (map (ord, self key)) for i in range (self nk, self nb * (self nr 1)) t = expanded (i1) * 4 i * 4 if i % self nk == 0 t = xor ( AES sub_word ( AES rot_word (t) ), (AES Rcon i // self nk, 0, 0, 0) ) elif self nk > 6 and i % self nk == 4 t = AES sub_word (t). In cryptography, an Sbox (substitutionbox) is a basic component of symmetric key algorithms which performs substitution In block ciphers, they are typically used to obscure the relationship between the key and the ciphertext — Shannon's property of confusion In general, an Sbox takes some number of input bits, m, and transforms them into some number of output bits, n, where n is not. A Very Compact \Perfectly Masked" SBox for AES (corrected) D Canright1 and Lejla Batina2 1 Applied Math, Naval Postgraduate School, Monterey CA , USA, dcanright@npsedu 2 KU Leuven ESAT/COSIC, Kasteelpark Arenberg 10, 001 LeuvenHeverlee, Belgium Abstract Implementations of the Advanced Encryption Standard (AES),.
Small portable AES128/192/256 in C Contribute to kokke/tinyAESc development by creating an account on GitHub. For example, the value 9a 16 is converted into b8 16 The Sbox maps an 8bit input, c, to an 8bit output, s = S (c) Both the input and output are interpreted as polynomials over GF (2) First, the input is mapped to its multiplicative inverse in GF (28) = GF (2) x/ (x8 x4 x3 x 1), Rijndael's finite field. AES stands for “Advanced Encryption Standard” and is a specification that has selected the Rijndael cipher as its symmetric key ciphering algorithm Using AES, a message can be encrypted with a key (like a password) and no one except the key holder can decrypt the message This is useful for many reasons, but a good example is a password manager that encrypts all of the user’s passwords.
This article describes the Sbox used by the Rijndael (aka AES) cryptographic algorithm where x0, , x7 is the multiplicative inverse as a vector The matrix multiplication can be calculated by the following algorithm Store the multiplicative inverse of the input number in two 8bit unsigned temporary variables s and x Rotate the value s one bit to the left;. Rijndael sbox with an example in simple words Ask Question Asked 10 years ago All over google and wiki i'm not able to understand the rijndael sbox key scheduling Can anyone explain them in simple words and with an clear example????. This article describes the Sbox used by the Rijndael (aka AES) cryptographic algorithm where x0, , x7 is the multiplicative inverse as a vector The matrix multiplication can be calculated by the following algorithm Store the multiplicative inverse of the input number in two 8bit unsigned temporary variables s and x Rotate the value s one bit to the left;.
Sbox is a unique nonlinear operation in Rijndael, one encryption algorithm chosen as AES, and it determines the performance of AES In this paper, the weaknesses in complexity and security of AES. Advanced Encryption Standard (AES) which works on a 128 bit data encrypting it with 128, 192 or 256 bits of keys for ensuring security In this paper, we compare AES encryption with two different SBoxes Sbox with 256 byte lookup table (Rijndael SBox) and AES with 16 byte SBox (Anubis SBox). Advanced Encryption Standard (AES) is one of the most common symmetric encryption algorithms The hardware complexity in AES is dominated by AES substitution box (Sbox) which is considered as one.
Nonfeistel Ciphers, Example AES(Advanced Encryptin system) Feistel Cipher Feistel cipher An SBox(SUbstitution box) is an M*N susbtitution box where m and n are not necessarily same each output bit is a boolean function function of the inputs y1=f1.
A Very Basic Introduction To Aes 256 Cipher Hacker Noon

S Box Substitution Box Youtube
Network Security Lec4

S Box Youtube
S Box Design Symmetric Ciphers And Hashes Modern Cryptography Applied Mathematics For Encryption And Informanion Security 16
Appendix 5b Simplified Aes Cryptography And Network Security 4th Edition

How Are The Aes Inverse S Boxes Calculated Cryptography Stack Exchange

The Advanced Encryption Standard Aes Algorithm Commonlounge

Advanced Encryption Standard Aes Implementaion Using Java

High Speed Area Efficient Implementation Of Aes Algorithm On Reconfigurable Platform Intechopen
Eprint Iacr Org 17 1161 Pdf

S Box Implementation Of Aes Is Not Side Channel Resistant Springerlink

The Advanced Encryption Standard Aes Algorithm Commonlounge

How We Can Calculate Aes Inverse Sbox Cryptography Stack Exchange

Advanced Encryption Standard Comp

The Advanced Encryption Standard Aes Algorithm Commonlounge
Lirias Kuleuven Be Retrieve
Http Www Facweb Iitkgp Ac In Sourav Aes Pdf

Implementation Of 128 Bit Aes Algorithm In D Lohit Kumar Dr A R Reddy
Q Tbn And9gcrmq1uror0bzpl6mnp52butzzlkreaovkmephwit8vsl474qera Usqp Cau
Sect Ctf 17 Bad Aes

Building Aes 128 From The Ground Up With Python By Henrique Marcomini Wavy Product Engineering Medium
Www Mdpi Com 1099 4300 21 3 245 Pdf
Aes Encryption
A Novel Byte Substitution Architecture For The Aes Cryptosystem
Simplified Aes Example L Simplified Aes Example Le Chegg Com
Http Www Mathnet Ru Php Getft Phtml Jrnid Mvk Paperid 227 What Fullt
What Is 3des Encryption And How Does Des Work Comparitech

Achieving High Performance For Advanced Encryption Standard Aes Applications
9 Advanced Encryption Standard

Aes

Advanced Encryption Standard Aes Transformation Functions
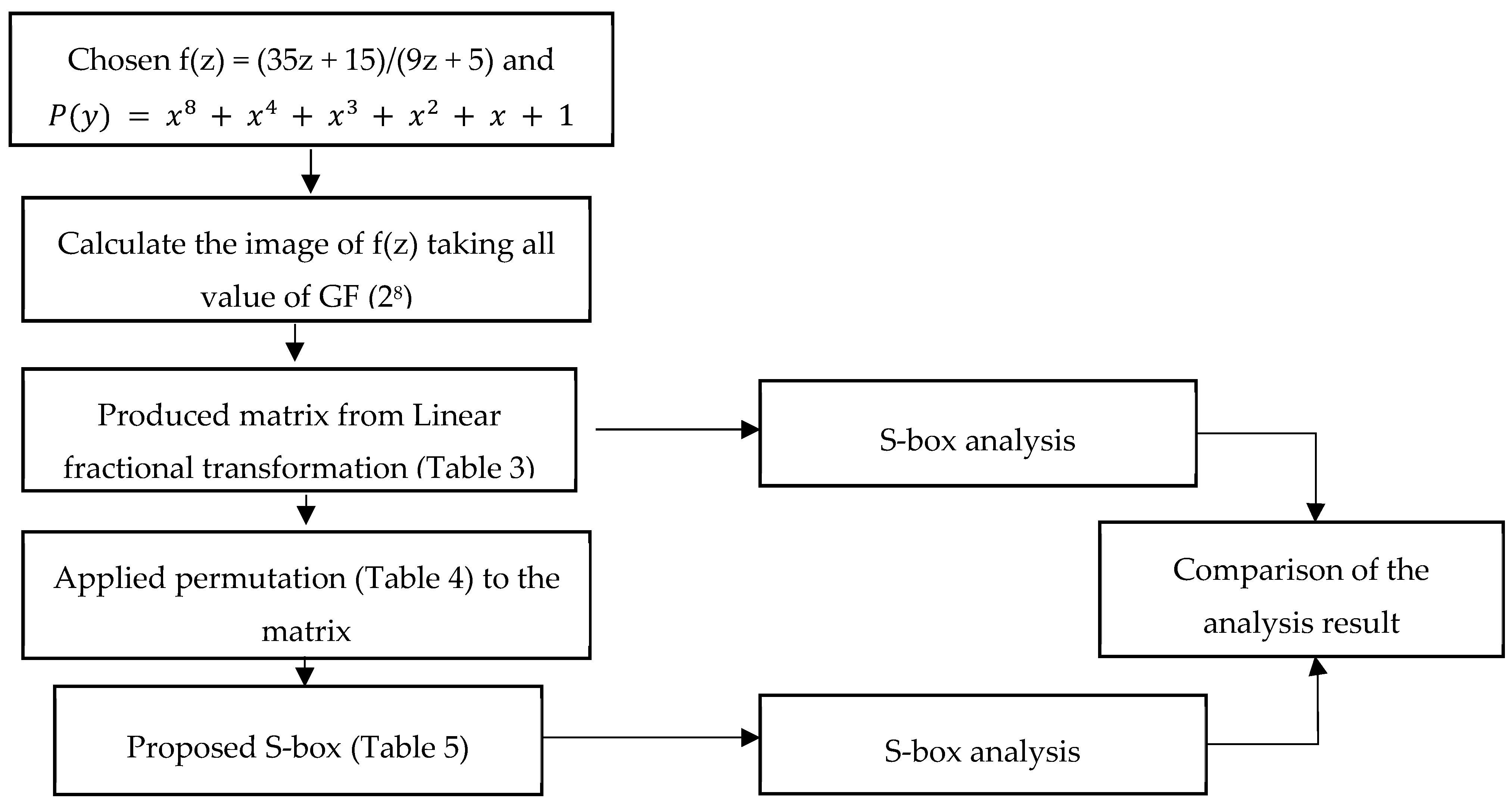
Symmetry Free Full Text S Box Construction Based On Linear Fractional Transformation And Permutation Function Html

An Algorithm For The Construction Of Substitution Box For Block Ciphers Based On Projective General Linear Group Aip Advances Vol 7 No 3
Arxiv Org Pdf 1908
Www Osti Gov Servlets Purl

Cs480 Cryptography And Information Security Ppt Download
Http Www Cs Haifa Ac Il Orrd Lc17 Paper60 Pdf

Figure 3 From Aes T Box Tampering Attack Semantic Scholar

Ch05 Testbank Crypto6e
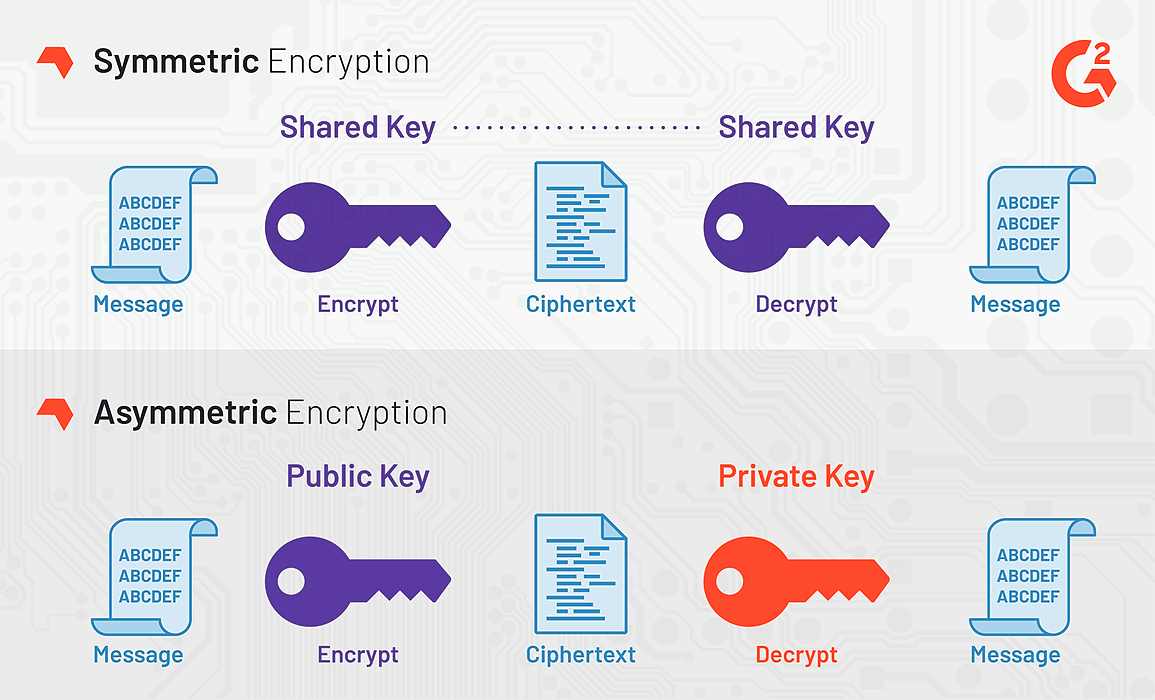
A Very Basic Introduction To Aes 256 Cipher Hacker Noon

Achieving High Performance For Advanced Encryption Standard Aes Applications

Aes S Box Input And Output Question Cryptography Stack Exchange

Advanced Encryption Standard Aes Transformation Functions

Rijndael S Box Wikipedia
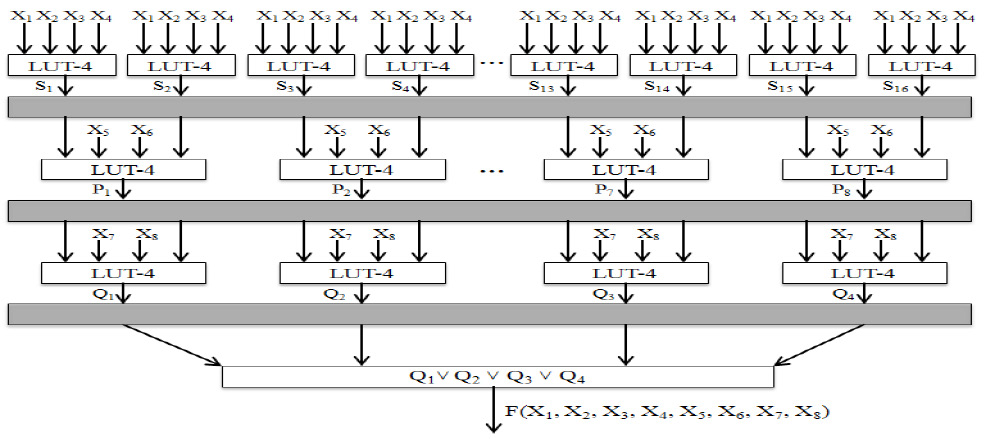
Performance Assessment Of An Efficient Search And Realization Technique Of The S Box In The Aes Cryptosystem Figure 8
Http Citeseerx Ist Psu Edu Viewdoc Download Doi 10 1 1 227 7609 Rep Rep1 Type Pdf
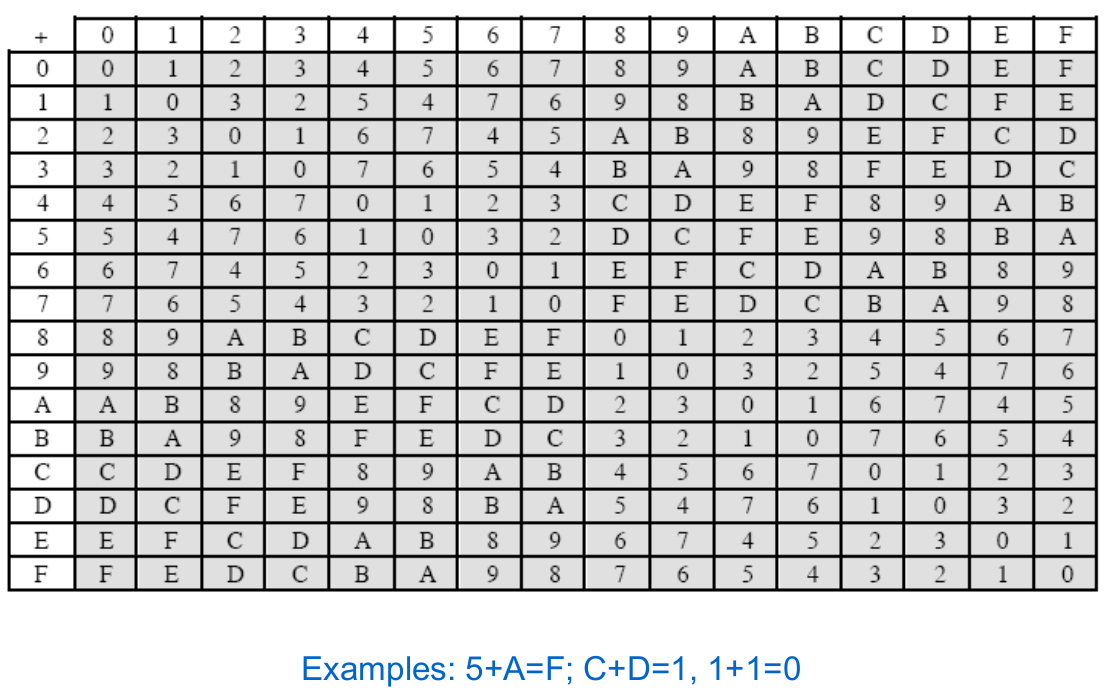
9 Advanced Encryption Standard

Pdf Study Of S Box Properties In Block Cipher

What S Happens If We Use The Weakest S Box For Aes Cryptography Stack Exchange

Advanced Encryption Standard Aes Transformation Functions
Http Citeseerx Ist Psu Edu Viewdoc Download Doi 10 1 1 227 7609 Rep Rep1 Type Pdf
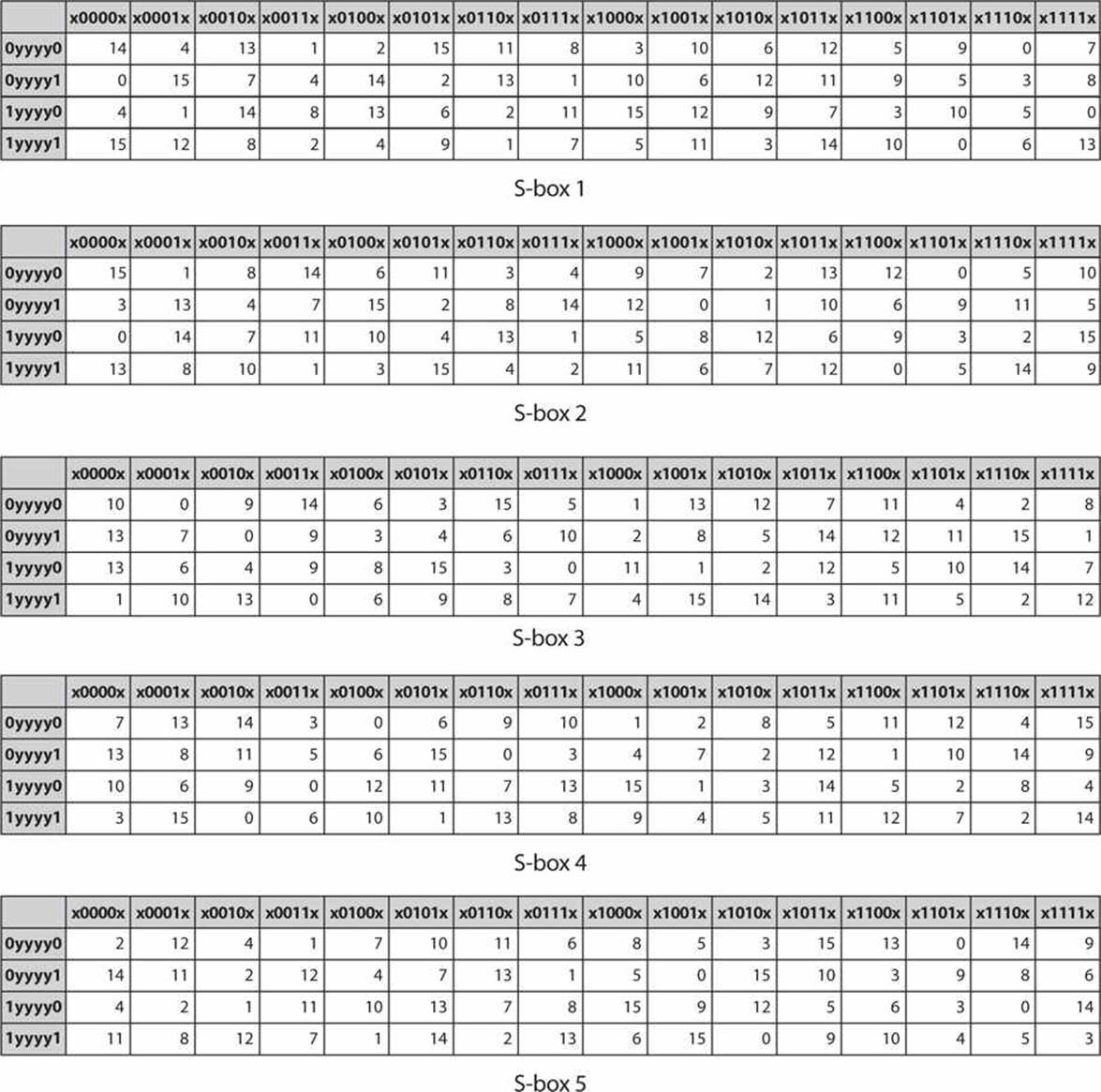
S Box Design Symmetric Ciphers And Hashes Modern Cryptography Applied Mathematics For Encryption And Informanion Security 16

How We Can Calculate Aes Inverse Sbox Cryptography Stack Exchange

An Example Of The Aes S Box 4 3 Shift Rows Download Scientific Diagram
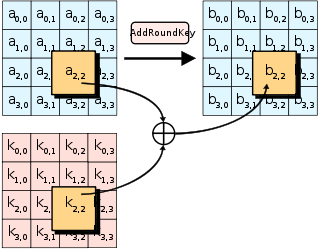
Advanced Encryption Standard Wikipedia

Css322y12s2h02 Simplified Aes Example Pdf Cryptography Key Cryptography

S Box Matrix With Explanation To Substitution Operation Download Scientific Diagram

A Very Compact Aes Spiht Selective Encryption Computer Architecture Design With Improved S Box
Http Eprint Iacr Org 11 332 Pdf
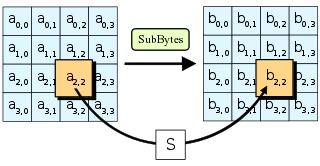
Advanced Encryption Standard Wikipedia
Http Www Cs Man Ac Uk Banach Comp Info Courseslides Wk2 3 Aes Pdf

Solved Simplified Aes 16 Bit Plaintext P Chegg Com
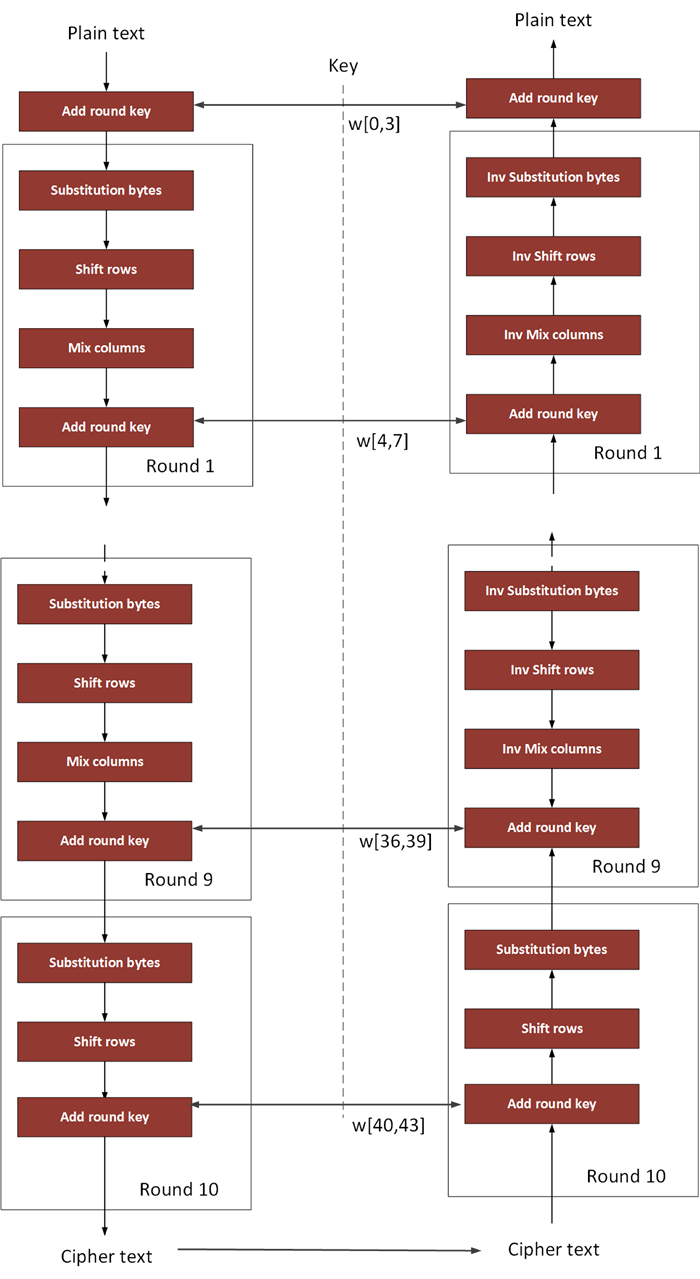
Aes Encryption
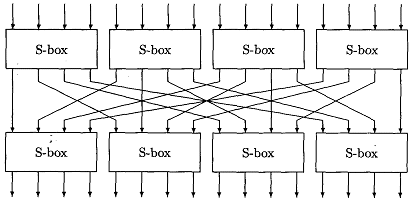
Sp Networks

How Are S Box Calculated In S Aes Cryptography Stack Exchange
Www2 Rivier Edu Journal Roaj Fall 10 J455 Selent Aes Pdf
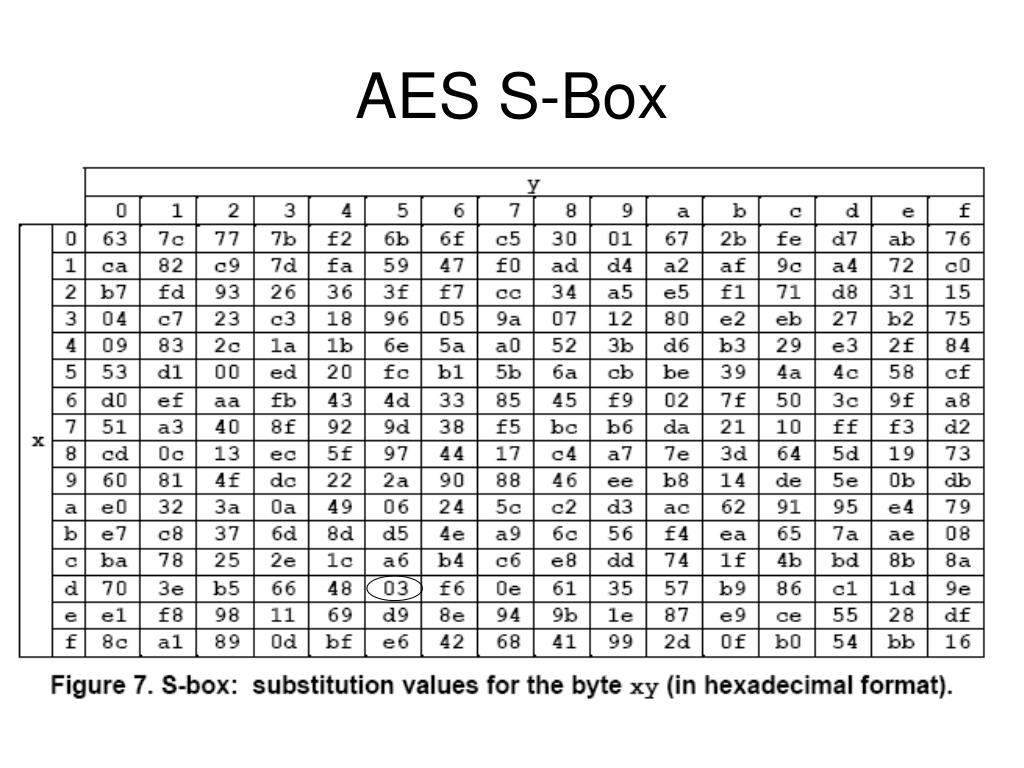
Ppt The Advanced Encryption Standard Powerpoint Presentation Free Download Id
Q Tbn And9gcqehpldz7psfjrs7pmbsxxysg 64ocgk26e2p94atioxorqy6m8 Usqp Cau
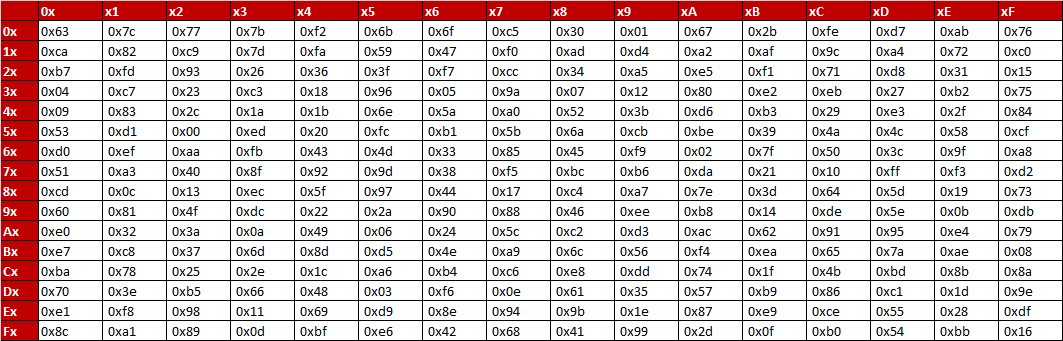
Aes Encryption

Symmetric Encryption And Message Confidentiality Ppt Download
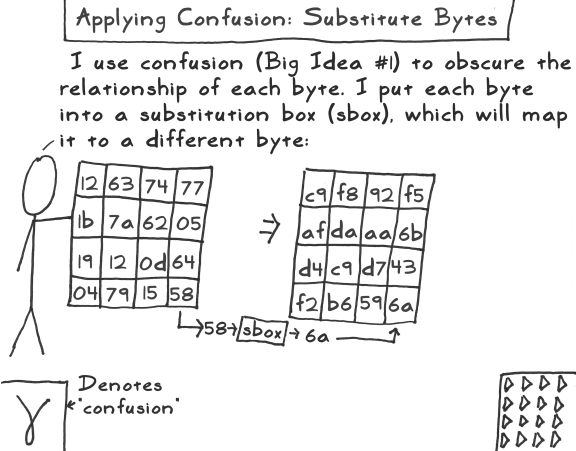
A Stick Figure Guide To The Advanced Encryption Standard Aes

Secret Key Crypotography
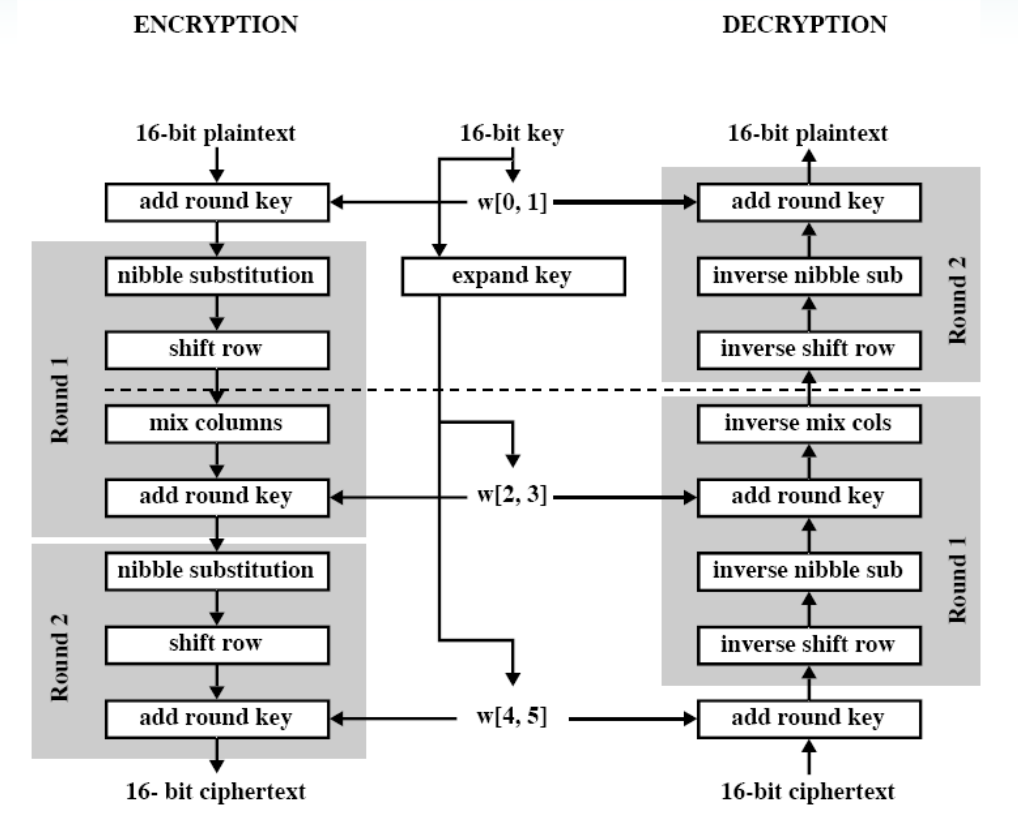
9 Advanced Encryption Standard
Aip Scitation Org Doi Pdf 10 1063 1

Simplified Aes Example
C Implementation Of Aes Encryption Algorithms
Q Tbn And9gcspmz4pvvldpmuymanx3og7knpoleyoqjbf050lmlijs2yhcok3 Usqp Cau
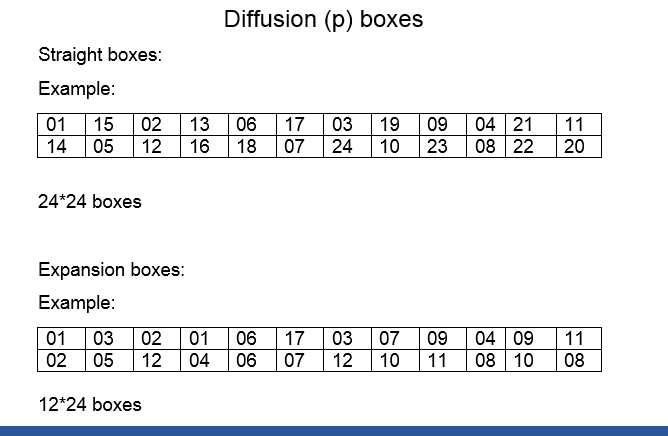
Data Encryption Standard
Www Lri Fr Fmartignon Documenti Systemesecurite 5 Aes Pdf

Table 3 From A New Algorithm To Construct Secure Keys For Aes Semantic Scholar
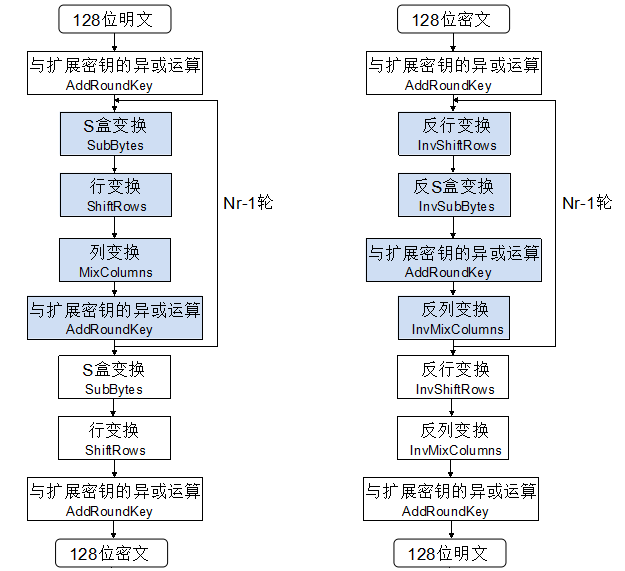
C Implementation Of Aes Encryption Algorithms

Finding Output Given An S Box Input Of 8 Bits Cryptography Stack Exchange

Construction Of S8 Liu J S Boxes And Their Applications Sciencedirect

Advanced Encryption Standard Aes Transformation Functions

Aes Advanced Encryption Standard Anu Vazhayil

Chapter 36 Aes Encryption And Decryption On The Gpu Nvidia Developer
Q Tbn And9gcqhgl8mhkczmcz8i10su9 Pui45goh Wz0xlqow41vfnqxnusck Usqp Cau

Achieving High Performance For Advanced Encryption Standard Aes Applications

The Aes Rijndael S Box

The Advanced Encryption Standard Aes Algorithm Commonlounge

Comparative Analysis Of Different Aes Implementation Techniques For Efficient Resource Usage And Better Performance Of An Fpga Sciencedirect
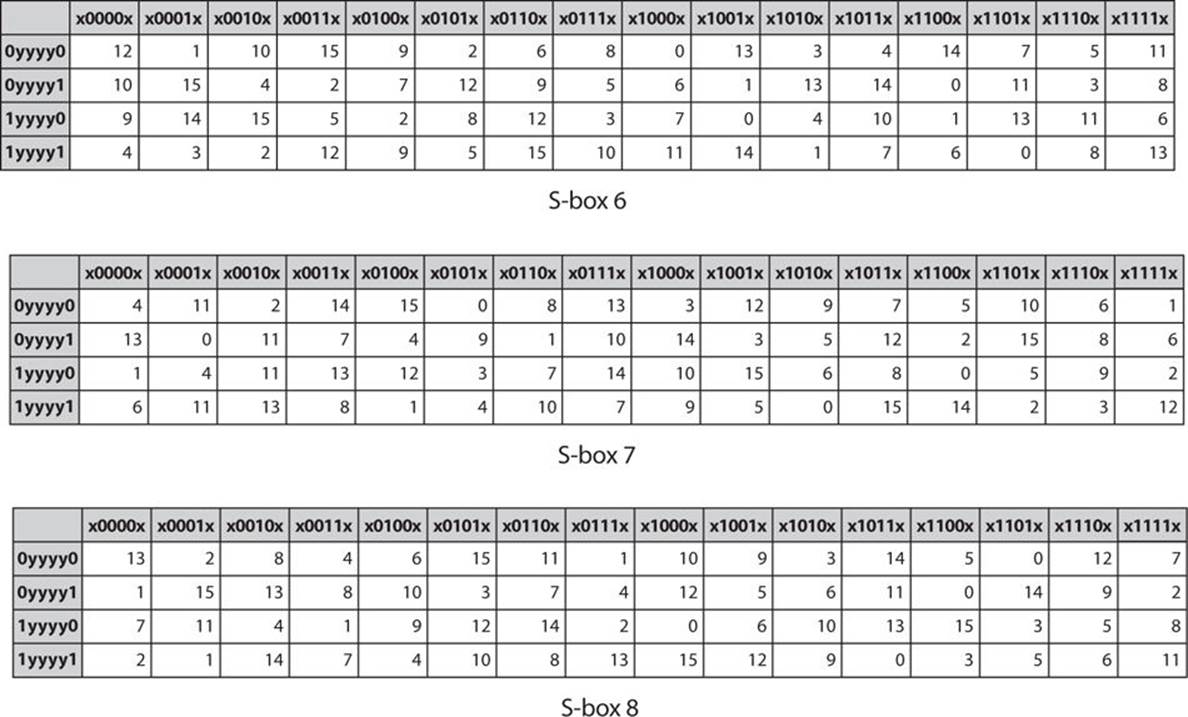
S Box Design Symmetric Ciphers And Hashes Modern Cryptography Applied Mathematics For Encryption And Informanion Security 16

The Advanced Encryption Standard Aes Algorithm Commonlounge

Overview On S Box Design Principles Youtube

Construction Of New S Box Using Action Of Quotient Of The Modular Group For Multimedia Security

High Speed Area Efficient Implementation Of Aes Algorithm On Reconfigurable Platform Intechopen
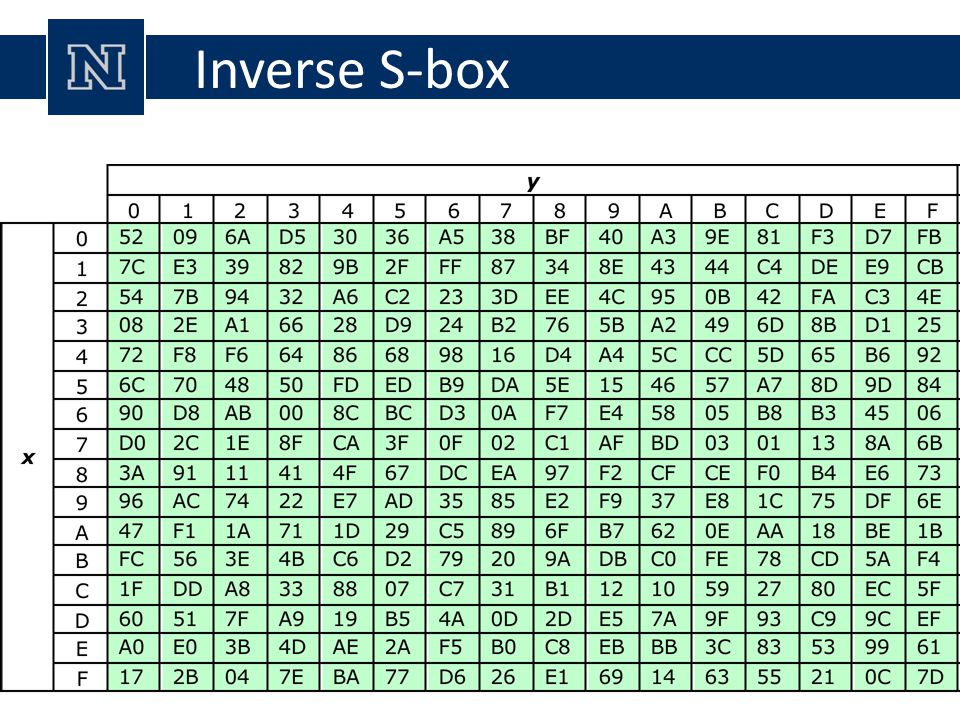
Lecture 23 Symmetric Encryption Ppt Download



