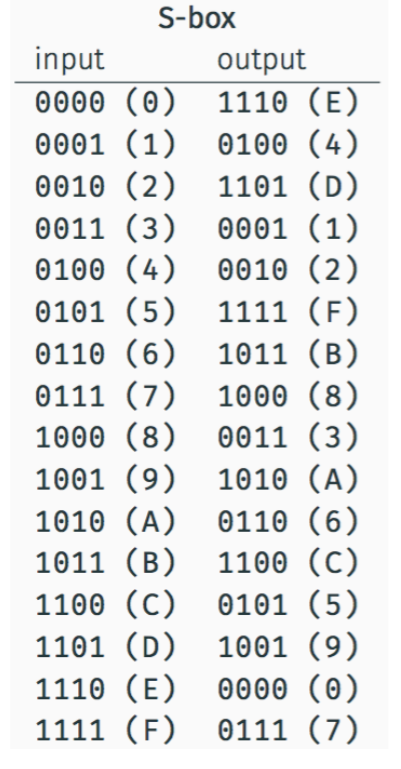
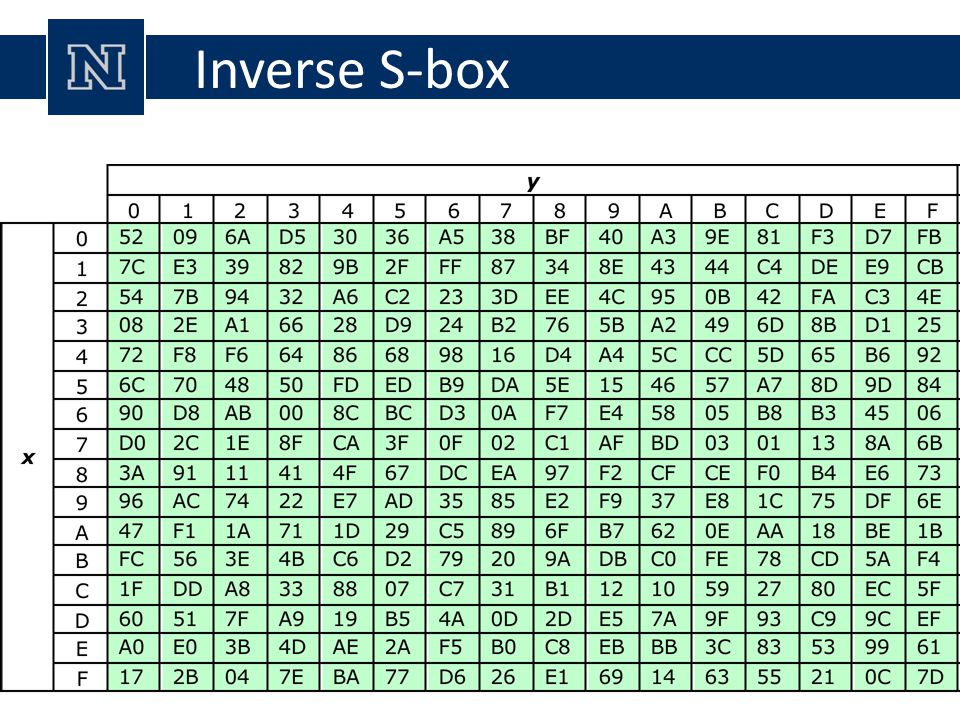
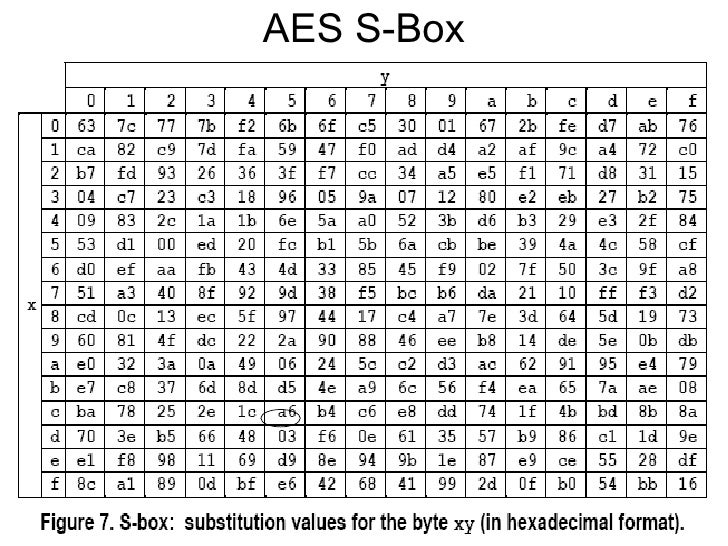
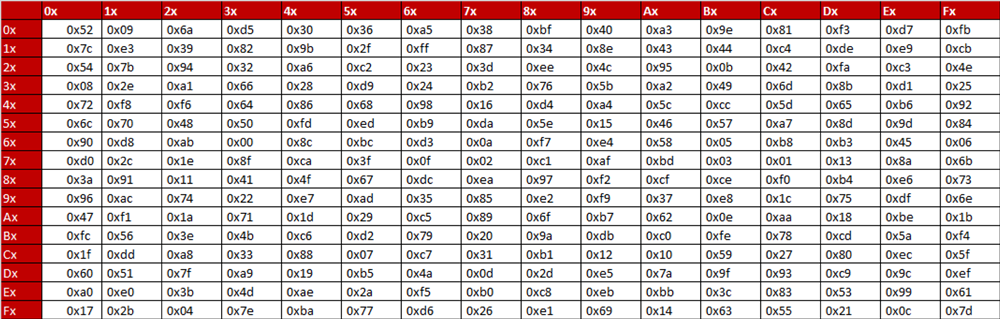
S Box Table
Pipeline Aes S Box Implementation Starting With Substitution Table

4 Bit Crypto S Box Download Table

Kerem Varici Cosic

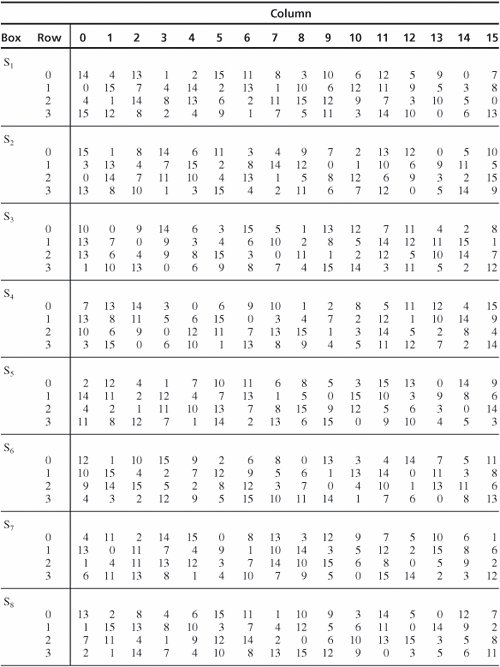
Function S Box S1 In The Des Algorithm Represented As A Table And Its Download Scientific Diagram

Rijndael S Box Wikipedia

Table 2 From An Algorithm For Key Dependent S Box Generation In Block Cipher System Semantic Scholar
I wanted to take the "Ultimate Las Vegas.

S box table. CSS Level 1 The definition of 'vertical-align' in that specification. This thing soaked up a 1/2 gallon of the mix, so it should be well protected from humidity and general shop abuse. Marlboro 100's, Box Box 1 carton = 10 packs 0 cigarettes.
Answer 1 of 7:. A computer program can be viewed as an elaborate algorithm. Welcome to Evuna, tapas bar, spanish restaurant and award winning wine merchant, a hidden gem in all sense of the word.
The Blowfish and the Twofish encryption algorithms). If the element has any border or padding, this is then added to the width and height to arrive at the size of the box that's rendered on the screen. By default in the CSS box model, the width and height you assign to an element is applied only to the element's content box.
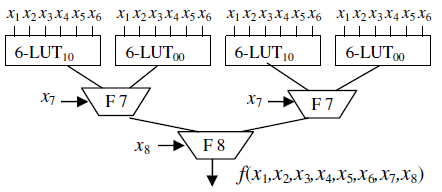
An m×n S-box can be implemented as a lookup table with 2 m words of n bits each. An algorithm (pronounced AL-go-rith-um) is a procedure or formula for solving a problem, based on conducting a sequence of specified actions. Adds the <length> value and allows it to be applied to elements with a display type of table-cell.
For finish I used a 50/50 mix of poly & mineral spirits. This means that when you set width and height, you have to adjust the value you give to allow for any border or padding. The suction is amazing and there is almost no dust left on the table or in the dust box.
This will be my first time in Vegas and I was trying to figure out where exactly Bally's Box Office Entrance Bus Ramp is, is it at Bally's Hotel and Resort on the strip or is it somewhere else. Applied some paste wax to the dados the drawers slide in and they operate very smoothly. In mathematics and computer science, an algorithm usually means a small procedure that solves a recurrent problem.
To vertically align an inline element's box inside its containing line box.
Section 12 2 Symmetric Encryption Security In Computing 4th Edition

Advanced Encryption Standard Aes Transformation Functions

Parametric Comparison Of Emds Algorithm With Some Symmetric Cryptosystems Sciencedirect

Linux Security 15

On The S Box Of Streebog And Kuznyechik

9 3 The Des S Boxes P Box And Initial Permutation Ip Computer Security And Cryptography Book

Pdf Analysis Of Some Security Criteria For S Boxes In Blowfish Algorithm Semantic Scholar

Aes Advanced Encryption Standard Anu Vazhayil
I M Struggling With This Question Any Help Will B Chegg Com
Ieeexplore Ieee Org Iel7 Pdf

Lecture 4 Data Encryption Standard Des Dr Nermin Hamza Ppt Video Online Download

New S Box Calculation For Rijndael Aes Based On An Artificial Neural Network

Aes Advanced Encryption Standard Anu Vazhayil
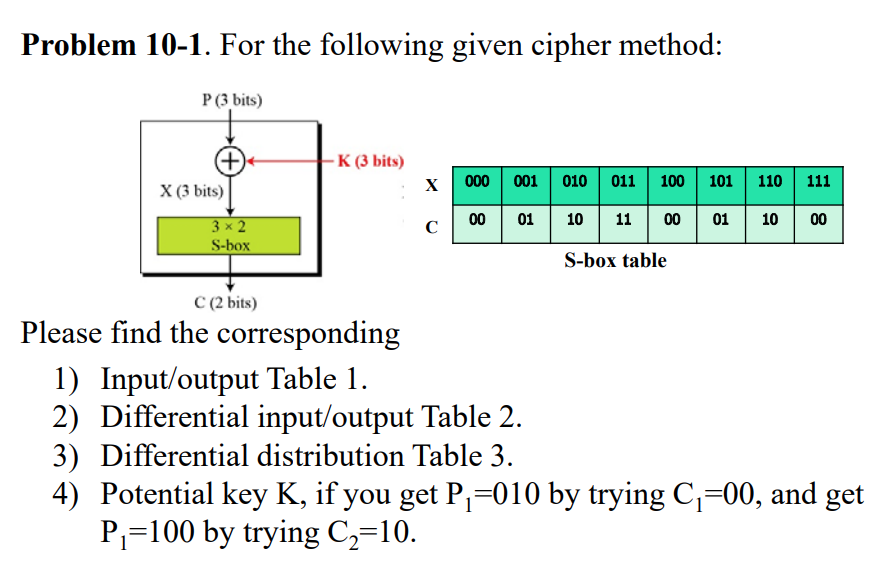
For The Following Given Cipher Method Please Find Chegg Com

Aes

Cryptography Data Encryption Standard Des
Ieeexplore Ieee Org Iel7 Pdf

Table 1 From Hardware Implementation Of The Data Encryption Standard Des Semantic Scholar

Generation And Optimization Of Rijndael S Box Equation System Scialert Responsive Version

What Is Data Encryption Standard Des Definition Working Advantages And Disadvantages Binary Terms
Lecture 23 Symmetric Encryption Ppt Download
Http People Scs Carleton Ca Maheshwa Courses 4109 Seminar11 Atttack on des Pdf

Robustness Of S Boxes Used By Des Download Table

Cryptography Data Encryption Standard Des
Dl Acm Org Doi Pdf 10 1145

Table Of Differential Cryptanalysis Of 1 St 4 Bit S Box Of 1 St S Box Download Table

Table 1 From An Algorithm For Key Dependent S Box Generation In Block Cipher System Semantic Scholar
Www Irjet Net Archives V2 I8 Irjet V2i811 Pdf

The Advanced Encryption Standard Aes Algorithm Commonlounge

What Is Aes Encryption And How Does It Work Cybernews

9 3 The Des S Boxes P Box And Initial Permutation Ip Computer Security And Cryptography Book

Secret Key Crypotography
Eprint Iacr Org 17 1161 Pdf
Network Security Lec4
Solved Q1 In A Des System A S Box Consists Of 8 Sub S B Chegg Com

What Is Data Encryption Standard Des Definition Working Advantages And Disadvantages Binary Terms
Http Cse Iitkgp Ac In Debdeep Courses Iitkgp Crypto Slides Dc Pdf
Aes Encryption
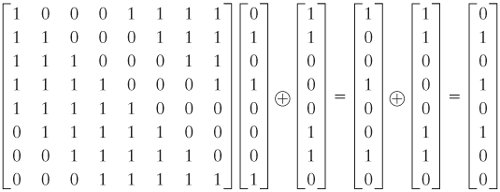
Next Generation Block Ciphers
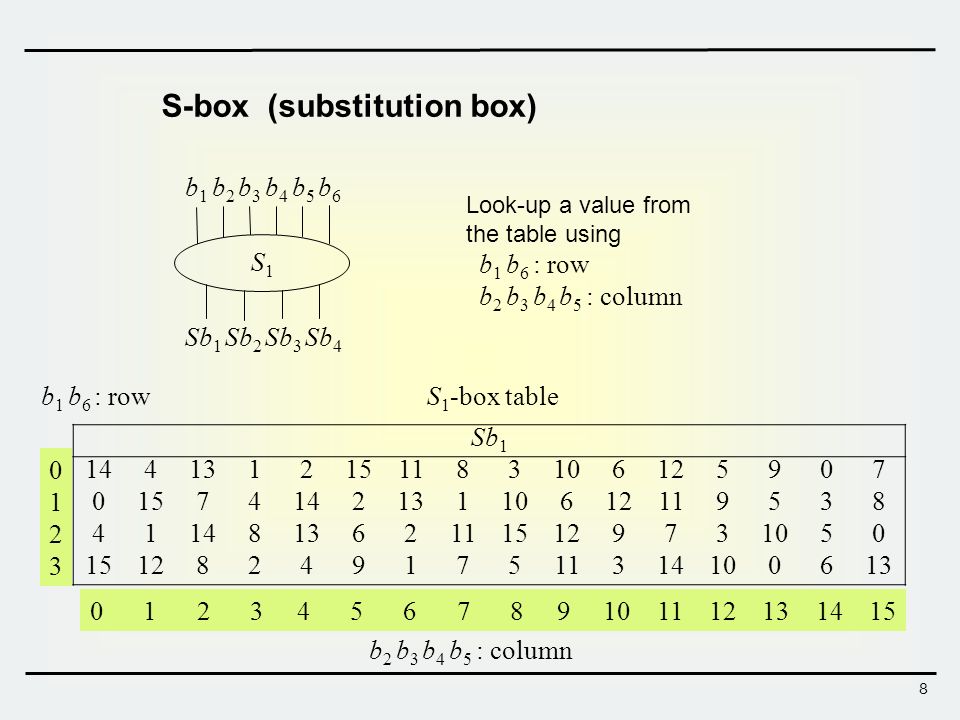
Section 5 2 The Aes Cipher Cryptography And Network Security 4th Edition
Acadpubl Eu Hub 18 118 22 Articles 22c 58 Pdf
Q Tbn And9gcq Raxfwj2ura1kadboki 0ic9uqbm48wdz6h9hhbtj3p64kk Usqp Cau

Pdf An Improved Aes S Box And Its Performance Analysis Semantic Scholar

Transformed S Box In The Form Of 16 16 Matrix Download Table

4 Bit Crypto S Box Download Table
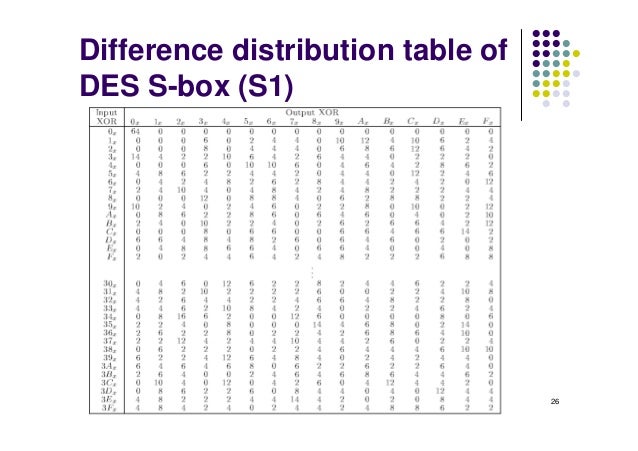
1 Lect 7 Data Encryption Standard 2 Data Encryption Standard Des Des History 1976 Adopted As A Federal Standard 1977 Official Publication Ppt Download

Function S Box S1 In The Des Algorithm Represented As A Table And Its Download Scientific Diagram

Table 2 5 From The Block Cipher Companion Semantic Scholar

The S Box Table Alternatively To Implement The Sub Byte Algorithm Download Scientific Diagram
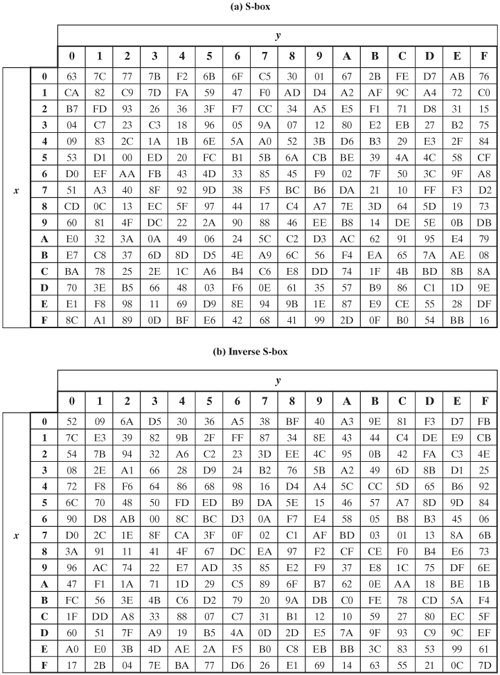
Section 5 2 The Aes Cipher Cryptography And Network Security 4th Edition
Http Www1 Spms Ntu Edu Sg Ask 17 File Slides Ask17 08 Yu sasaki Pdf

Anu An Ultra Lightweight Cipher Design For Security In Iot Bansod 16 Security And Communication Networks Wiley Online Library
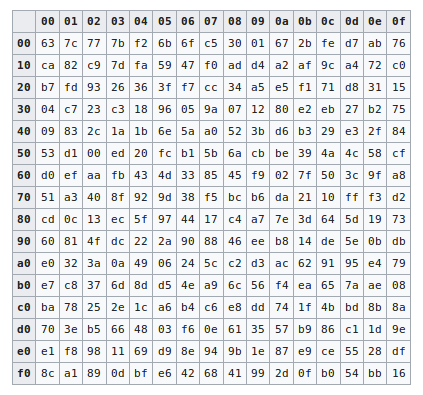
Sect Ctf 17 Bad Aes

Pdf An Improved Aes S Box And Its Performance Analysis Semantic Scholar

New S Box Calculation For Rijndael Aes Based On An Artificial Neural Network
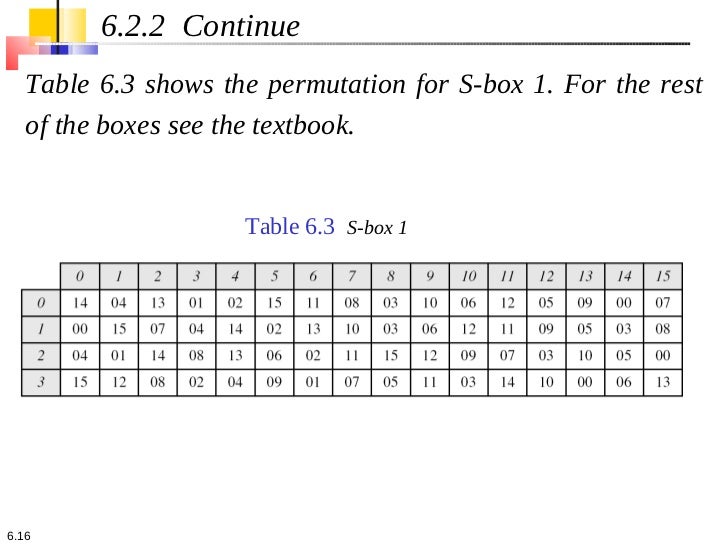
Des Cipher
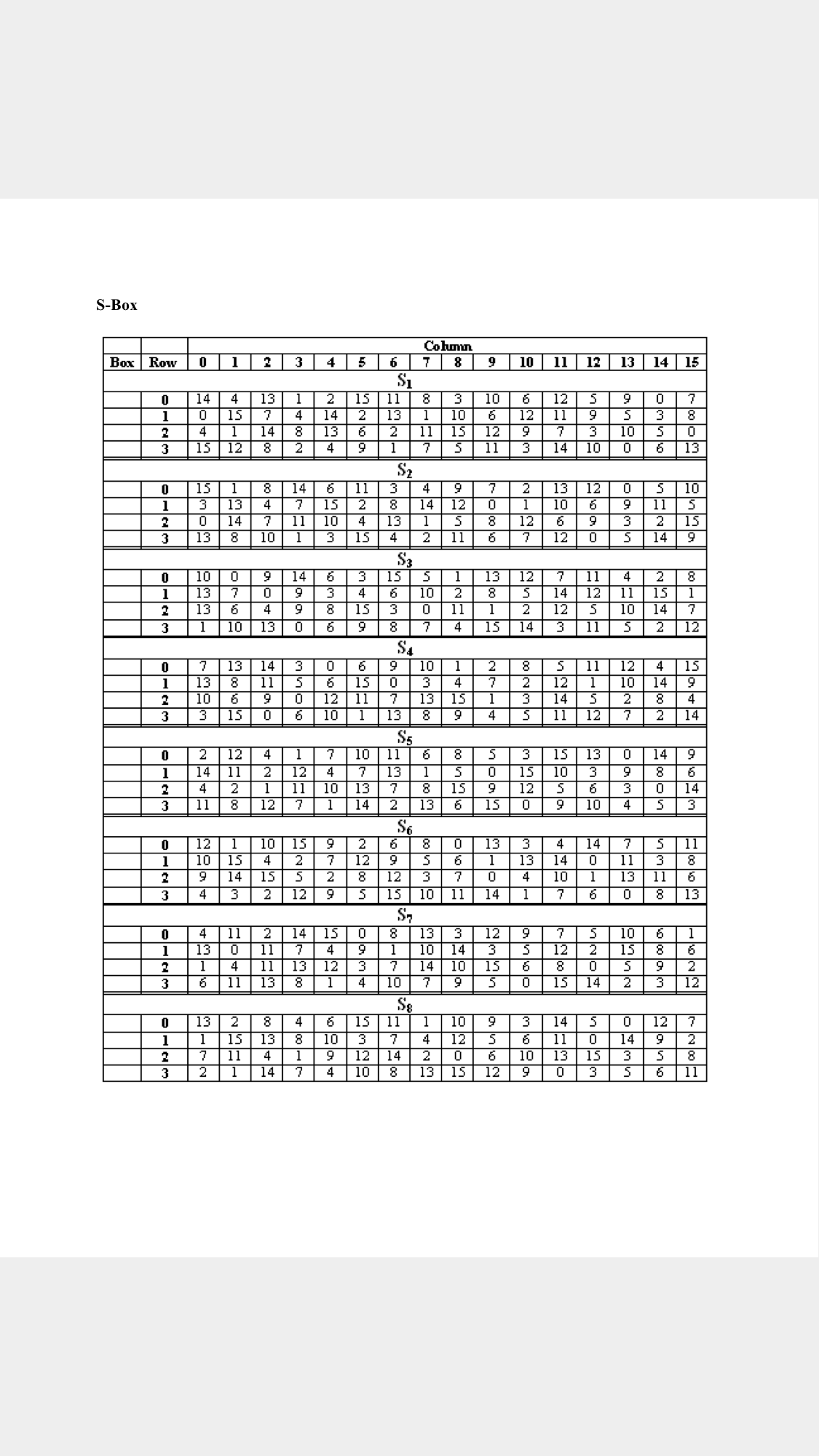
Derive The 32 Bit Output For The 48 Bit Input Usin Chegg Com

Solved 3 15 Suppose That The S Box Of Example 3 1 Is Repl Chegg Com
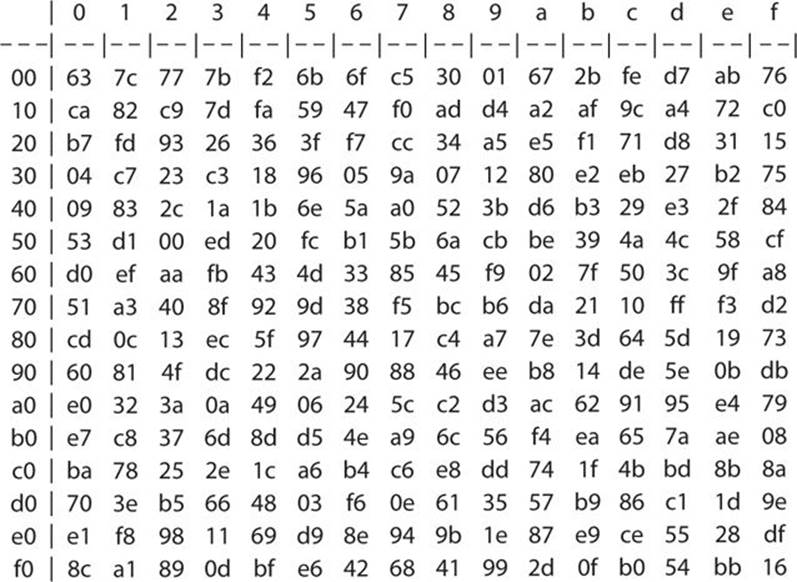
S Box Design Symmetric Ciphers And Hashes Modern Cryptography Applied Mathematics For Encryption And Informanion Security 16
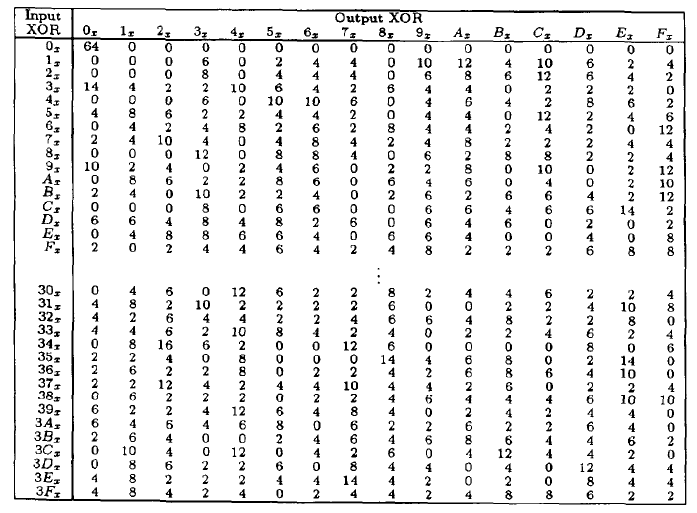
Differential Cryptanalysis On Data Encryption Standard Project 1 Security

Comparing Difference Distribution Tables Cryptography Stack Exchange

Achieving High Performance For Advanced Encryption Standard Aes Applications
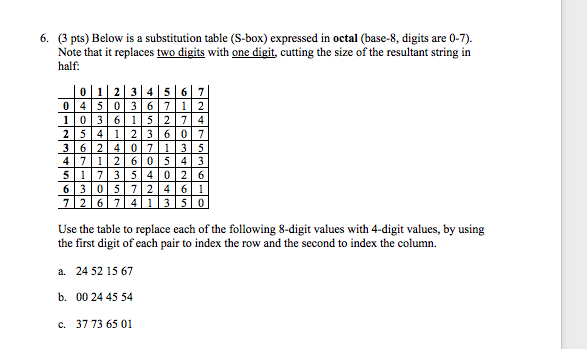
Solved 6 3 Pts Below Is A Substitution Table S Box Ex Chegg Com
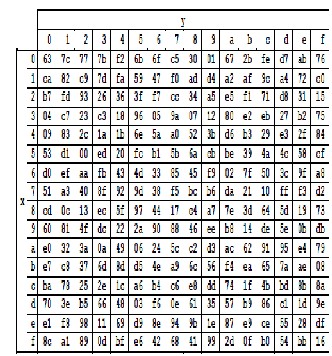
Design And Verification Of Aes Encryption With New Approach For S Box

How Are S Box Calculated In S Aes Cryptography Stack Exchange

Solved An S Box In Des Is A Table Of 4 Rows And 16 Column Chegg Com

Ppt On Des Powerpoint Slides
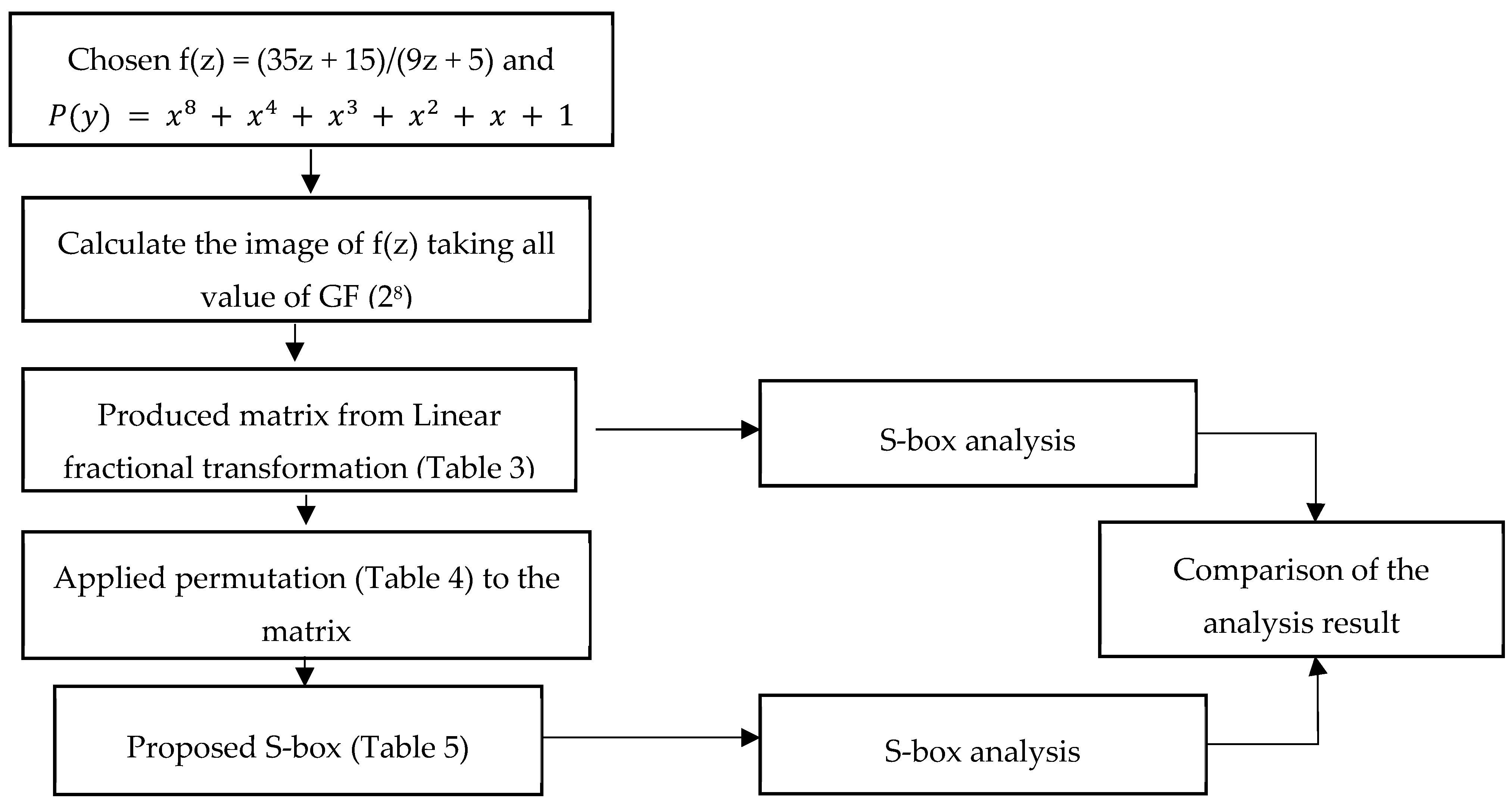
Symmetry Free Full Text S Box Construction Based On Linear Fractional Transformation And Permutation Function Html

Table 1 From Dynamic Aes 128 With Key Dependent S Box Semantic Scholar

Secret Key Crypotography
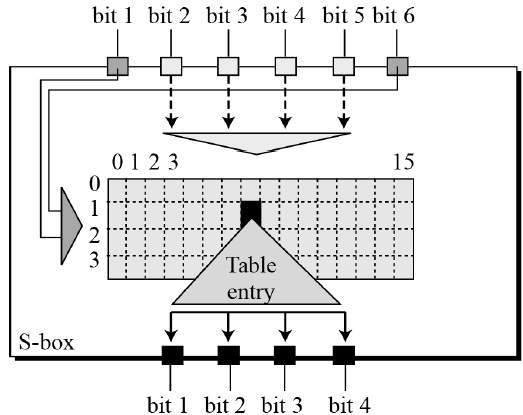
Data Encryption Standard Tutorialspoint

Modern Cryptography Des Block Cipher Programmer Sought
Q Tbn And9gcrpn6f Fj Zk O0r0bzusnq9xqfslpsyxlm9lvllraxndygwd9 Usqp Cau

Math To Replace S Boxes Good Or Bad Idea Cryptography Stack Exchange
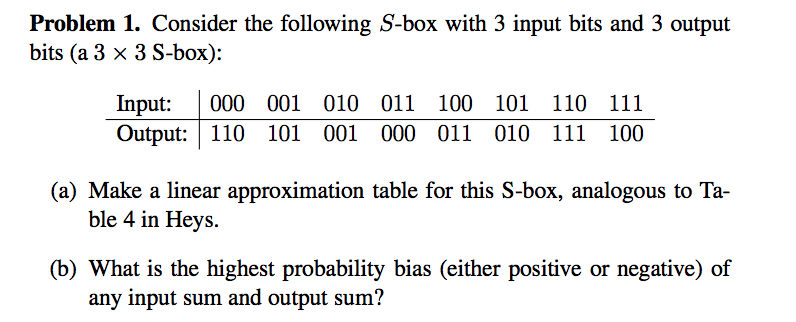
Solved Problem 1 Consider The Following S Box With 3 Inp Chegg Com

Des Encryption Youtube

Table 2 From Encryption Using Dual Key Transformation Based On Creation Of Multi S Boxes In Aes Algorithm Semantic Scholar

Table 3 From Key Dependent S Box Generation In Aes Block Cipher System Semantic Scholar

Table 2 From Key Dependent S Box Generation In Aes Block Cipher System Semantic Scholar
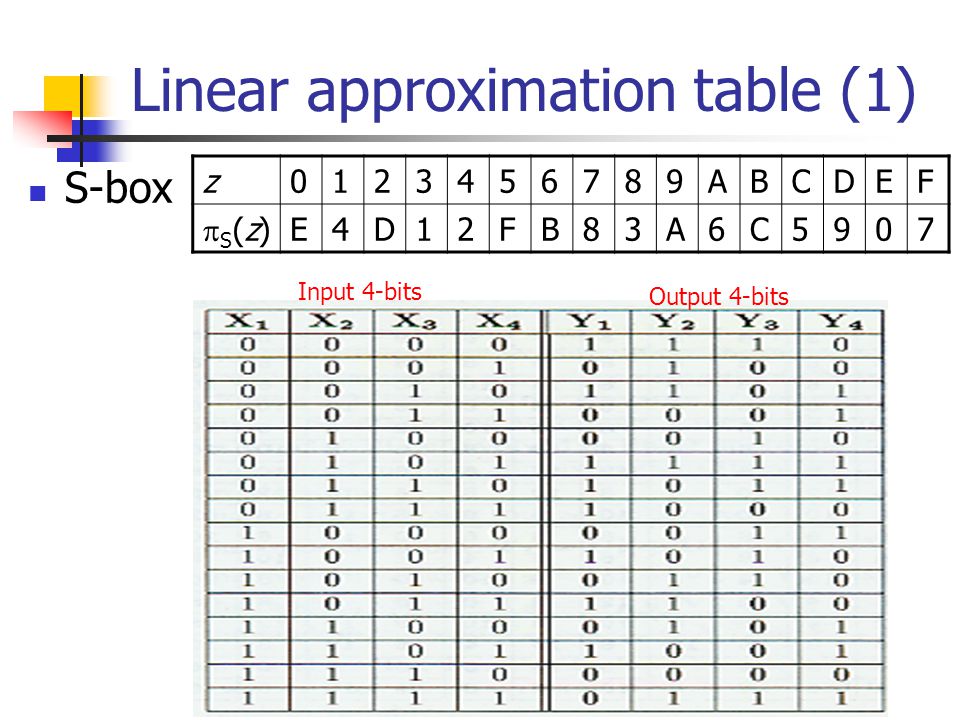
Cryptanalysis On Substitution Permutation Networks Jen Chang Liu 05 Ref Cryptography Theory And Practice D R Stinson Ppt Download

Cryptography Data Encryption Standard Des

The Advanced Encryption Standard Aes Algorithm Commonlounge
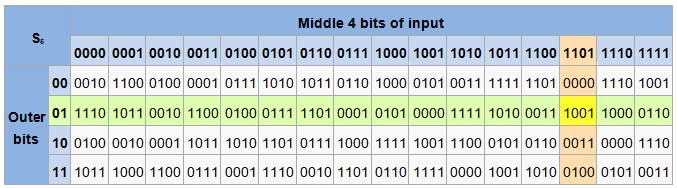
Introduction To Data Encryption Morf Coding And Engineering

The Advanced Encryption Standard Aes Algorithm Commonlounge

Ece 5760

Ppt On Des Powerpoint Slides

New S Box Calculation For Rijndael Aes Based On An Artificial Neural Network

S Box Substitution Box Youtube

Data Encryption Standard Des Ppt Video Online Download

Cryptography Data Encryption Standard Des

Finding Output Given An S Box Input Of 8 Bits Cryptography Stack Exchange
Http Cse Iitkgp Ac In Debdeep Courses Iitkgp Crypto Slides Lc Pdf
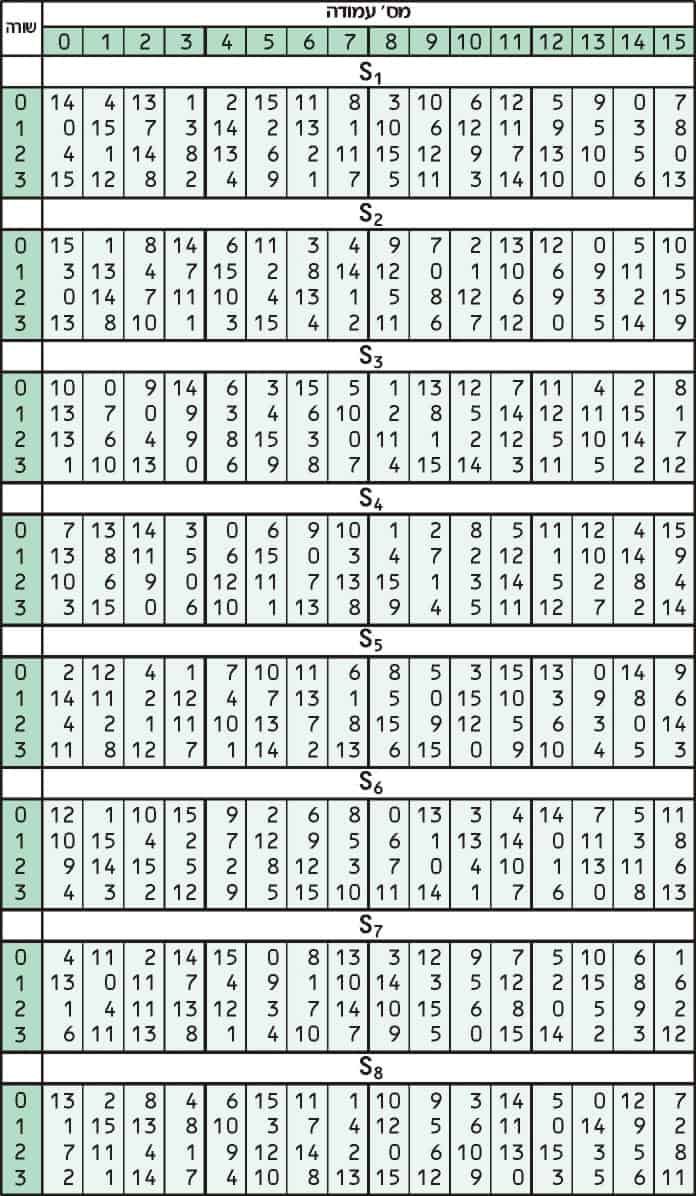
What Is 3des Encryption And How Does Des Work Comparitech

Correlation Function Of The Normalized S Box Table 2 Download Scientific Diagram
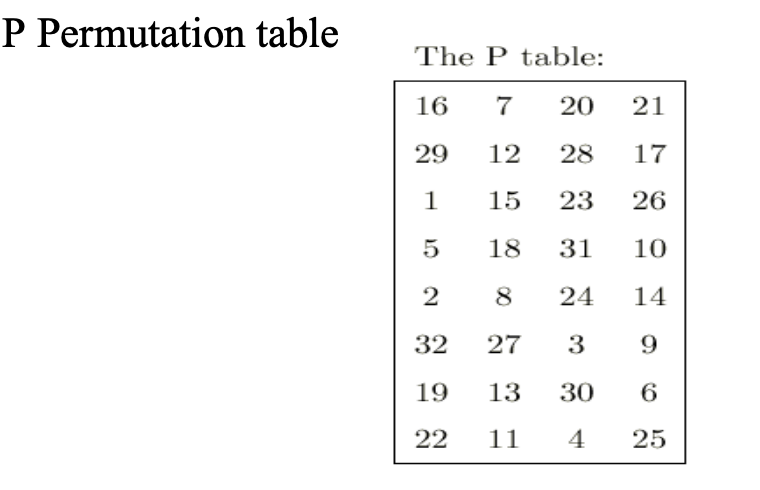
Referring To The Lecture Notes On Des There Are One Expansion Permutation Table1 Eight Substitution S Boxes And One Permutation P Box Table 2 Course Hero
1

Multiplicative Inverse Cryptography Stack Exchange
Q Tbn And9gcsvskl Ol5 Wgf3aikvgc Tqbnnivsvud4qug7wmizavovnhful Usqp Cau



