Aes Inverse S Box
Aes Algorithm Inverse S Box Download Scientific Diagram

Research Journal Of Applied Sciences Engineering And Technology 12 1 52 62 Doi 10 Rjaset 12 2303

Table 1 From Encryption Using Dual Key Transformation Based On Creation Of Multi S Boxes In Aes Algorithm Semantic Scholar
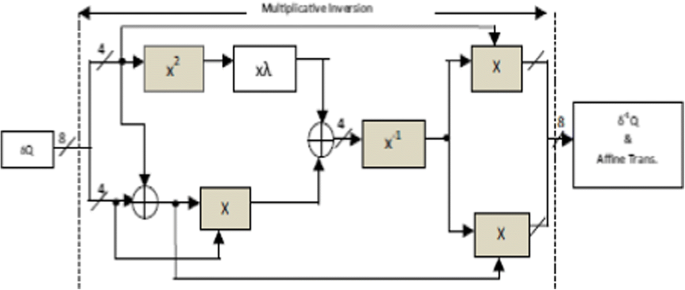
An Optimized S Box Circuit For High Speed Aes Design With Enhanced Pprm Architecture To Secure Mammographic Images Springerlink
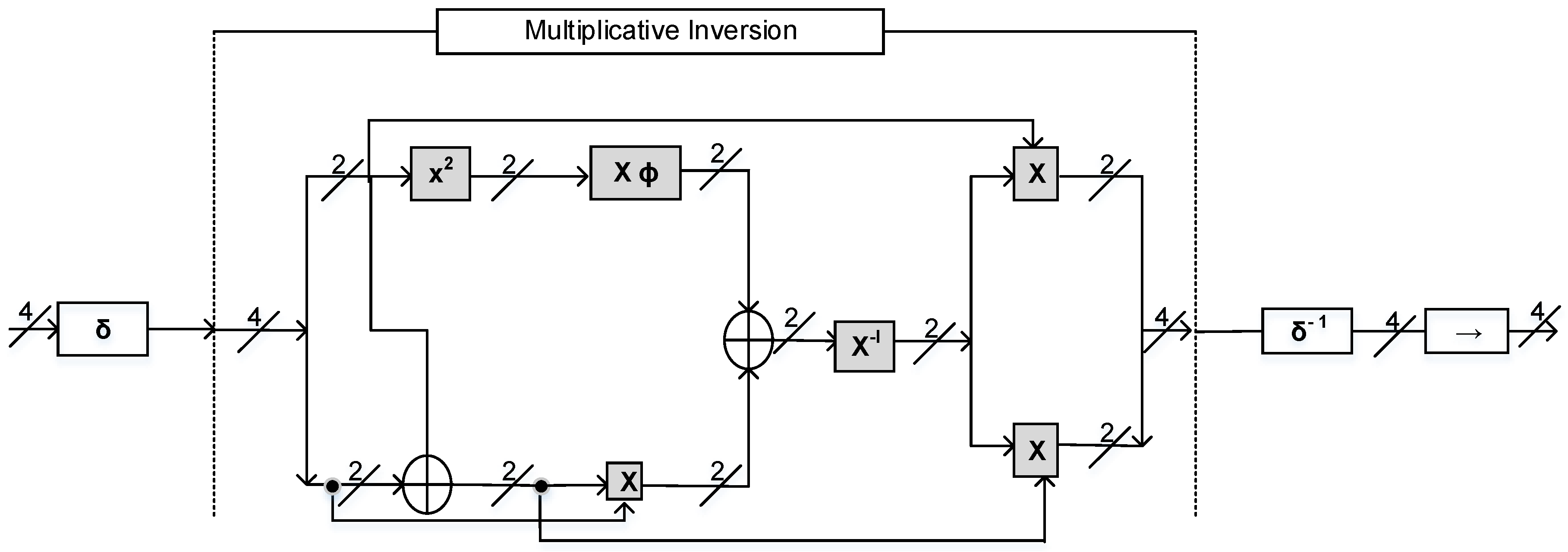
Information Free Full Text Lightweight S Box Architecture For Secure Internet Of Things Html
Q Tbn And9gcqdrzhz98dbfyic72wnjjv1mt06lryfyrhauyesgpk 31scwxyiugpircnh30ba6ldmydccxvuvsq Usqp Cau Ec
How can I verify that if the SBox input is the byte 93 (expressed in hex), then the SBox output is DC?.

Aes inverse s box. The Sbox must be invertible if decryption is to be possible (IsboxSbox(a)= a) however it should not be its self inverse ie Sbox(a) 6= Isbox(a) The Inverse Shift Rows transformation, known as InvShiftRows performs these circular shifts in the opposite direction for each of the last three rows and the first row is unaltered to beginThis. Like AES encryption, Inverse SubBytes are transformed into looking up table which is called inverse Sbox and is different with that in encryption Details can be found in the chapter of AES encryption During Inverse ShiftRows, right circular shift are operated based on each row number in 2D state array. Mixing the data within each column of the State array.
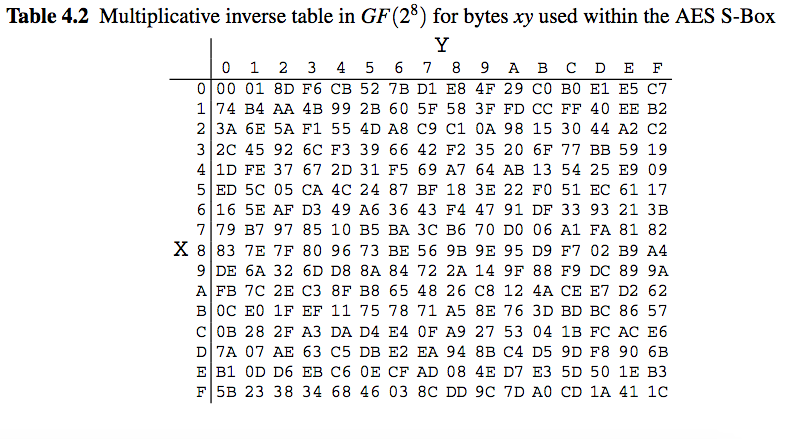
The four important operations in AES algorithm are SBox, inverse SBox, MixColumn and InverseMixColumn steps in these are computationally more involved than addroundkey and shift row operations The designs, which do not use ROMs or big lookup tables, Box and inverse S Box have been. Question Using The Multiplicative Inversion Table Shown Below (which Is Used As Part Of AES Sbox), (a) Find The Inverse Of Hex Entry ‘F3' From The Table (as You Know, 'F' Is For The Vertical Axis X And '3' Is For The Horizontal Axis Y) (b) For Verification, Perform A GF(23) Multiplication Of Input And Output Polynomials Using The Irreducible Polynomial Of. Abstract The AES combined Sbox/inverse Sbox is a single construction that is shared between the encryption and decryption data paths of the AES The currently most compact implementation of the AES combined Sbox/inverse Sbox is Canright's design, introduced back in 05 Since then, the research community has introduced several optimizations over the Sbox only, however the combined Sboxlinverse Sbox received little attention.
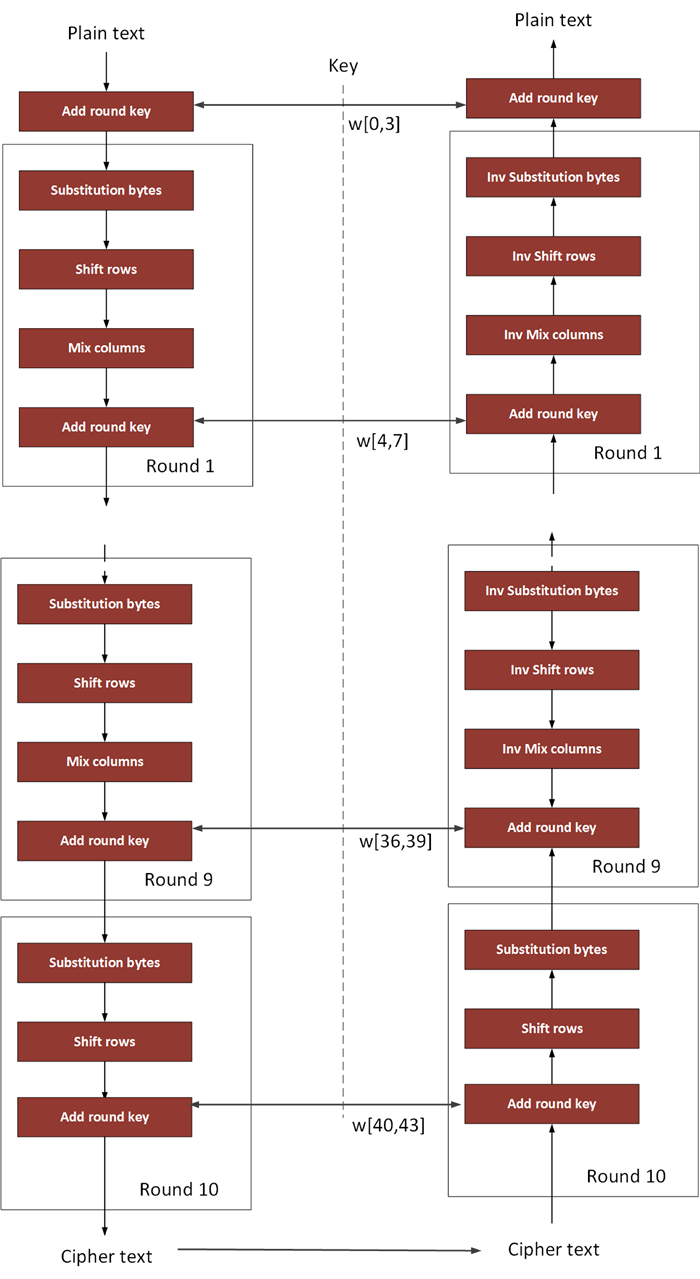
AES's single SBox Does a nonlinear substitution which is invertible For Each Byte of Input, {XY} 1Let {AB} = the multiplicative inverse of {XY} in GF(28) 2Let {XY}' = An affine transform of {AB}. Static sbox allows data analyses attack and the eventual captures of subkeys using inverse SubByte knowing inverse sbox We propose a novel yet simple design and implementation with a very low overhead cost to existing AES in order to update sbox to a dynamic sbox depending on a variable subkey at each round. For both its Cipher and Inverse Cipher, the AES algorithm uses a round function that is composed of four different byteoriented transformations byte substitution using a substitution table (Sbox), shifting rows of the State array by different offsets;.
Even though the SBox is bijective, it does not have any Þxed points, ie, there. Compact AES Sbox implementation using composite field arithmetic and Algebraic form representation, ProcIEEE 2nd Asea Symposium on Quality Electronic Design, pp 3123, 10 11 Rashmi Ramesh Rachh, PV Ananda Mohan and BS Anami, “Efficient Implementations of AES S box and Inverse S box”, Proc. Binary numbers in unshaded boxes Here is an example of the nibble substitution transformation The inverse nibble substitution function makes use of the inverse Sbox shown in Table 55b Note, for example, that the input 0 produces the output A, and the input A to the Sbox produces 0.
How can I verify that if the SBox input is the byte 93 (expressed in hex), then the SBox output is DC?. Sbox (rather than the two criteria of 2), and it turns out the best case for the merged architecture is also the best for the architecture with a separate Sbox and inverse Sbox Also, although the bit operations of Galois arithmetic correspond directly to XOR and AND (or NAND) gates, here certain combinations. The inverse Sbox is simply the Sbox run in reverse For example, the inverse Sbox of b8 16 is 9a 16 It is calculated by first calculating the inverse affine transformation of the input value, followed by the multiplicative inverse The inverse affine transformation is as follows.
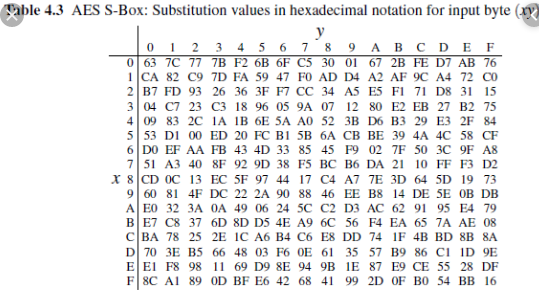
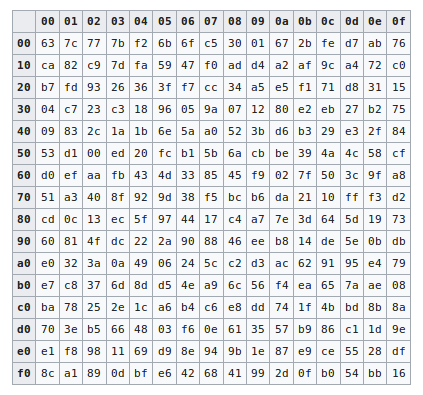
SAES SBoxes Note Hexadecimal numbers in shaded boxes;. The result is {2A}, which should appear in row {09} column {05} of the Sbox This is verified by checking Table 52a The inverse substitute byte transformation, called InvSubBytes, makes use of the inverse Sbox shown in Table 52b Note, for example, that the input {2A} produces the output {95}, and the input {95} to the Sbox produces {2A}. Static sbox allows data analyses attack and the eventual captures of subkeys using inverse SubByte knowing inverse sbox We propose a novel yet simple design and implementation with a very low overhead cost to existing AES in order to update sbox to a dynamic sbox depending on a variable subkey at each round.
# apply Sbox to all bytes for j in xrange (4) word j = aes_sbox word j # apply the Rcon table to the leftmost byte word 0 = word 0 ^ aes_Rcon i #### end key schedule core for z in xrange (4) for j in xrange (4) # mix in bytes from the last subkey word j ^= exkey self key_size j exkey extend (word) # Last key. Advanced Encryption Standard (AES) is a block cipher system which widely used in cryptographic application Moreover, a randomly keydependent Sbox, inverse Sbox generation algorithm and the. Abstract—The AES combined Sbox/inverse Sbox is a single construction that is shared between the encryption and decryption data paths of the AES The currently most compact implementation of the AES combined Sbox/inverse Sbox is Canright’s design, introduced back in 05 Since then, the research community has introduced.
Mixing the data within each column of the State array. The four important operations in AES algorithm are SBox, inverse SBox, MixColumn and InverseMixColumn steps in these are computationally more involved than addroundkey and shift row operations The designs, which do not use ROMs or big lookup tables, Box and inverse S Box have been. Mixing the data within each column of the State array.
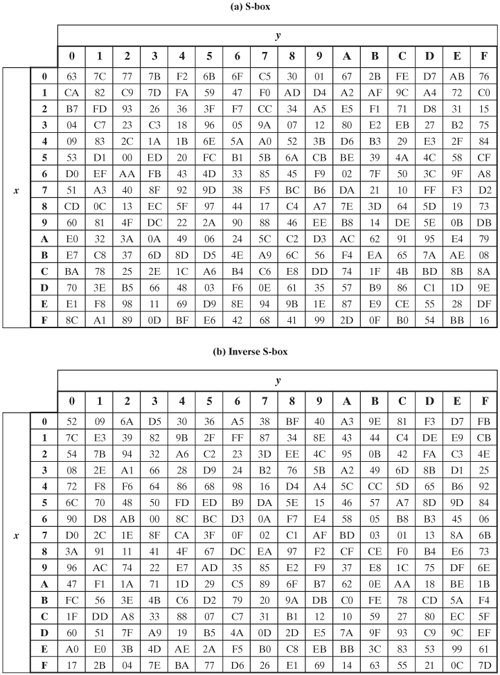
The AES SBox implements inverse multiplication in Galois Field 2 8 The AES SBox is shown in the Table below To read this Table, the byte input is broken into two 4bit halves The first half determines the row and the second half determines the column For example, the SBox transformation of 35 or 0x23 can be found in the cell at the intersection of the row labeled and the column labeled 03. I am currently working on AES i have a doubt about SBox and Inverse Sbox in the AES i want to know is we have to create a different Sbox for different key or the same S box is used for all the keys!!!. Thanks and Regards Mukesh Goyal Jul 27, 12 #2 blooz Advanced Member level 2 Joined Dec 29, 10.
Question Using The Multiplicative Inversion Table Shown Below (which Is Used As Part Of AES Sbox), (a) Find The Inverse Of Hex Entry ‘F3' From The Table (as You Know, 'F' Is For The Vertical Axis X And '3' Is For The Horizontal Axis Y) (b) For Verification, Perform A GF(23) Multiplication Of Input And Output Polynomials Using The Irreducible Polynomial Of. I am currently working on AES i have a doubt about SBox and Inverse Sbox in the AES i want to know is we have to create a different Sbox for different key or the same S box is used for all the keys!!!. Advanced Encryption Standard (AES) (FIPS PUB 197) 2 Category of Standard Computer Security Standard, Cryptography 3 Explanation The Advanced Encryption Standard (AES) specifies a FIPSapproved Inverse Sbox substitution values for the byte xy (in hexadecimal format).
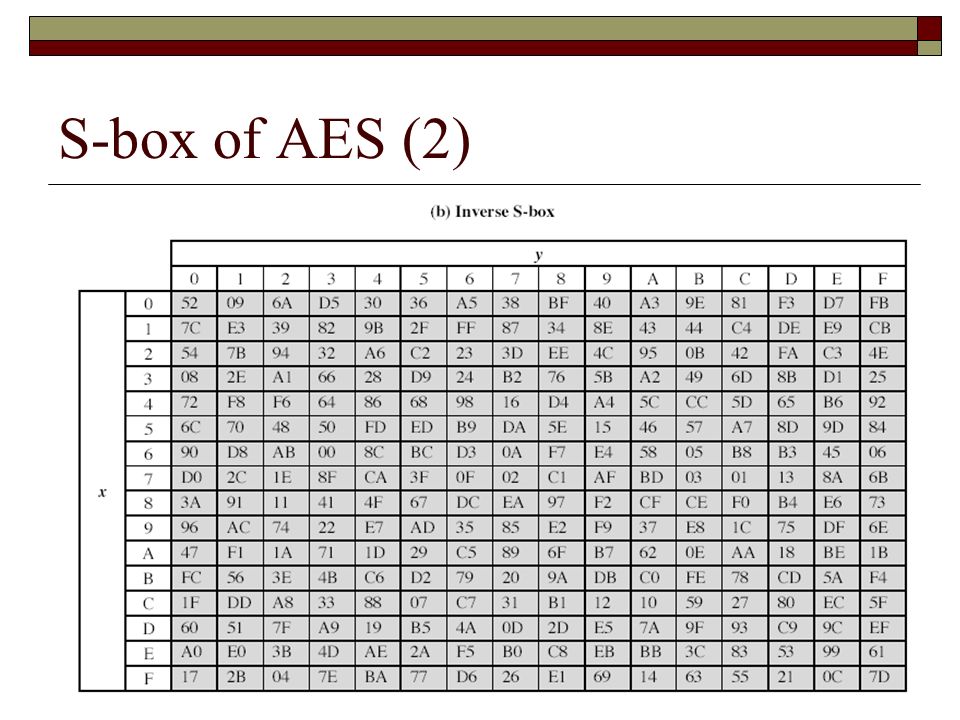
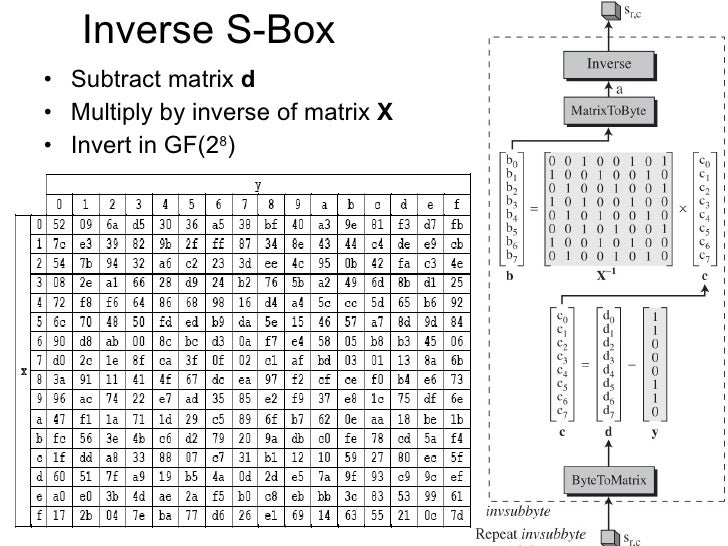
This is just small explanation about the Sbox used by the AES cryptographic algorithm The Sbox is generated by determining the multiplicative inverse for a given number in Rijndael's Galois Field The multiplicative inverse is then transformed using the following affine transformation matrix 1 0 0 0 1 1 1 1 1 1 0 0 0 1 1 1. Above shows the first and second Inverse SBox Substitution and XOR step Notice from the purple trace you can see the i2c line acking the data transfer to start the decryption The blue, wraps around the "InvSubBytesAndXOR" step and is followed by the mix columns step. The result is {2A}, which should appear in row {09} column {05} of the Sbox This is verified by checking Table 52a The inverse substitute byte transformation, called InvSubBytes, makes use of the inverse Sbox shown in Table 52b Note, for example, that the input {2A} produces the output {95}, and the input {95} to the Sbox produces {2A}.
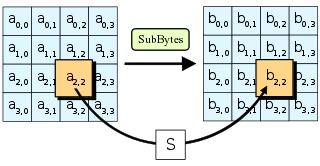
AES CIPHER The Inverse Substitute Byte Transformation Inverse substitute byte transformation, called InvSubBytes, makes use of the inverse of Sbox shown in Table 54b Note, for example, that the input {2a} produces the output {95}, and the input {95} to the Sbox produces {2a}. The block diagram of the AES algorithm is shown in Fig1 A SubBytes SubByte transformation is a highly nonlinear byte substitution where each byte inthe state array is replaced with another from a lookup table called an 561SBox This Sboxis invertible,is constructed by composing two transformations 1. IIIE1 SBOX SBox(INV SBox) used is derived from the inverse funcion over GF(28), known to have good nonlinearity properties To avoid attacks based on simple algebraic properties, the Sbox is constructed by combining the inverse function with an invertible affine transformation.
I mean, I can use a table to find the inverse, but how do I verify that it is indeed the inv. Format of AES Sbox 102 4 The Advanced Encryption Standard (AES) On a bit level Ñ and remember, the only thing that is ultimate of interest in encryption is the manipulation of bits Ñ this substitution can be described as S()=()!. Thanks and Regards Mukesh Goyal Jul 27, 12 #2 blooz Advanced Member level 2 Joined Dec 29, 10.
Inverse Sbox edit edit source The inverse Sbox is simply the Sbox run in reverse For example, the inverse Sbox of 0xdb is 0x9f It is calculated by first calculating the inverse affine transformation of the input value, followed by the multiplicative inverse The inverse affine transformation is as follows The following table represents Rijndael's inverse Sbox. For both its Cipher and Inverse Cipher, the AES algorithm uses a round function that is composed of four different byteoriented transformations byte substitution using a substitution table (Sbox), shifting rows of the State array by different offsets;. Figure 73 Substitute Bytes Stage of the AES algorithm The Inverse substitute byte transformation (known as InvSubBytes) makes use of an inverse sbox In this case what is desired is to select the value{2A} and get the value {95} Table 74 shows the two sboxes and it can be verified that this is in fact the case 62.
Advanced Encryption Standard (AES) (FIPS PUB 197) 2 Category of Standard Computer Security Standard, Cryptography 3 Explanation The Advanced Encryption Standard (AES) specifies a FIPSapproved Inverse Sbox substitution values for the byte xy (in hexadecimal format). ShiftRows – each row in the state table is shifted by a varying number of bytes Inverse operation is performed using the inverted SBox # do sbox transform on each of the values in the. How can I verify that if the SBox input is the byte 93 (expressed in hex), then the SBox output is DC?.
AES – The Advanced Encryption Standard SubBytes – each byte in the state is replaced with a different byte according to the SBox lookup table;. For both its Cipher and Inverse Cipher, the AES algorithm uses a round function that is composed of four different byteoriented transformations byte substitution using a substitution table (Sbox), shifting rows of the State array by different offsets;. Advanced Encryption Standard (AES) (FIPS PUB 197) 2 Category of Standard Computer Security Standard, Cryptography 3 Explanation The Advanced Encryption Standard (AES) specifies a FIPSapproved Inverse Sbox substitution values for the byte xy (in hexadecimal format).
Box keeps almost the same as AES inverse Sbox Comparison results suggest that the improved AES Sbox has better performance and can readily be applied to AES Keywords AES, Rijndael, ffi. Abstract The SBox and Inverse SBox in the tradition advance encryption standard is fixed and it is made by the composite field arithmatic to find the multiplicative inverse in the finite field GF (2 8)But in traditional AES the use of irreducible polynomial m(x) = x 8 x 4 x 3 x1 to find out multiplicative inverse, is known to the attacker So if we can make use of different. AES Example Round 1, Substitution Bytes current State Matrix is 0 B B @ 00 3C6E 47 1F 4E 22 74 0E 08 1B 31 54 59 0B1A 1 C C A substitute each entry (byte) of current state matrix by corresponding entry in AES SBox for instance byte 6E is substituted by entry of SBox in row 6 and column E, ie, by 9F this leads to new State Matrix 0 B B.
The value (0x) is the correct result of the inverse affine matrix The final vector of the inverse affine transform however is (0x05) The resultant 0x is then inverted, which is 0x48, the correct inverse sbox value. In the AES, the Sbox generate two transformations in the Galois fields GF(2) and GF(28) Sbox is a nonlinear transformation where each byte of the State is replaced by another byte using the substitution table The first transformation Sbox finds the multiplication inverse of the byte in the field GF(28) Since it is a algebraic. Simplified AES 16bit block 16bit key 4 x 4 Sbox Field 16 Modulus XX4 1 2 rounds SPN Musa, A, Schaefer, E, and Wedig, S 10 A Simplified AES.
I mean, I can use a table to find the inverse, but how do I verify that it is indeed the inv. The substitution table (SBox) of Advanced Encryption Standard (AES) and its properties are key elements in cryptanalysis ciphering We aim here to propose a straightforward method for the nonlinear transformation of AES SBox construction The method reduces the steps needed to compute the multiplicative inverse, and computes the matrices multiplication used in this transformation, without a. I mean, I can use a table to find the inverse, but how do I verify that it is indeed the inv.
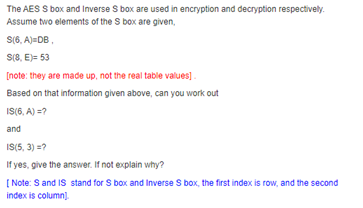
Solved The Aes S Box And Inverse S Box Are Used In Encryp Chegg Com

Table 2 From An Algorithm For Key Dependent S Box Generation In Block Cipher System Semantic Scholar
Q Tbn And9gcqrh7bkhwqfe1vo8kb7lnm7 Of7ykgp 5lpezn Fcanao6qwuorhytiwp9c3duvultcmcmmsu5jzg Usqp Cau Ec

Advanced Encryption Standard Aes Transformation Functions

Cryptography And Network Security Ppt Video Online Download
Sandilands Info Sgordon Teaching Css322y06s2 Protected Css322y06s2l05 Advanced Encryption Standard Pdf

How We Can Calculate Aes Inverse Sbox Cryptography Stack Exchange

Pdf The Memory Less Method Of Generating Multiplicative Inverse Values For S Box In Aes Algorithm
Http Www Cs Man Ac Uk Banach Comp Info Courseslides Wk2 3 Aes Pdf

The Advanced Encryption Standard Aes Algorithm Commonlounge

Aes S Box Input And Output Question Cryptography Stack Exchange
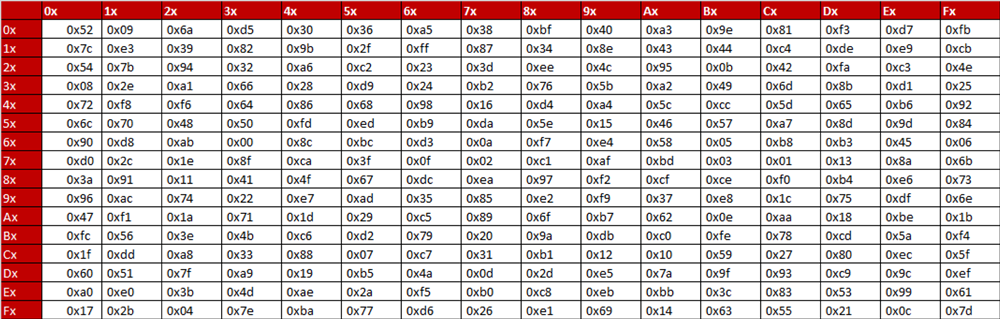
Aes Encryption

Ch05 Testbank Crypto6e

Secret Key Crypotography
Determine The Multiplicative Inverses Of 0d16 And Chegg Com
Http Www Ijicic Org Ijicic Pdf
Advanced Encryption Standard Wikipedia

The Advanced Encryption Standard Aes Algorithm Commonlounge

Aes Inverse S Box Rijndael Inverse S Box 16 Download Scientific Diagram

High Speed Area Efficient Implementation Of Aes Algorithm On Reconfigurable Platform Intechopen
2

Aes Algorithm Inverse S Box Download Scientific Diagram
Number Theory And Advanced Cryptography 1 Finite Fields And Aes Ppt Video Online Download

Aria Why Have One S Box When You Can Have Two By Prof Bill Buchanan Obe Asecuritysite When Bob Met Alice Medium

What S Happens If We Use The Weakest S Box For Aes Cryptography Stack Exchange
Solved C Points 6 Using Table 4 2 Of Gf 2 Determine Chegg Com

The Inverse Affine Transformation Of Aes Sbox Uses Different Additive Constant Cryptography Stack Exchange
Www Irjet Net Archives V2 I8 Irjet V2i811 Pdf

The Aes Rijndael S Box
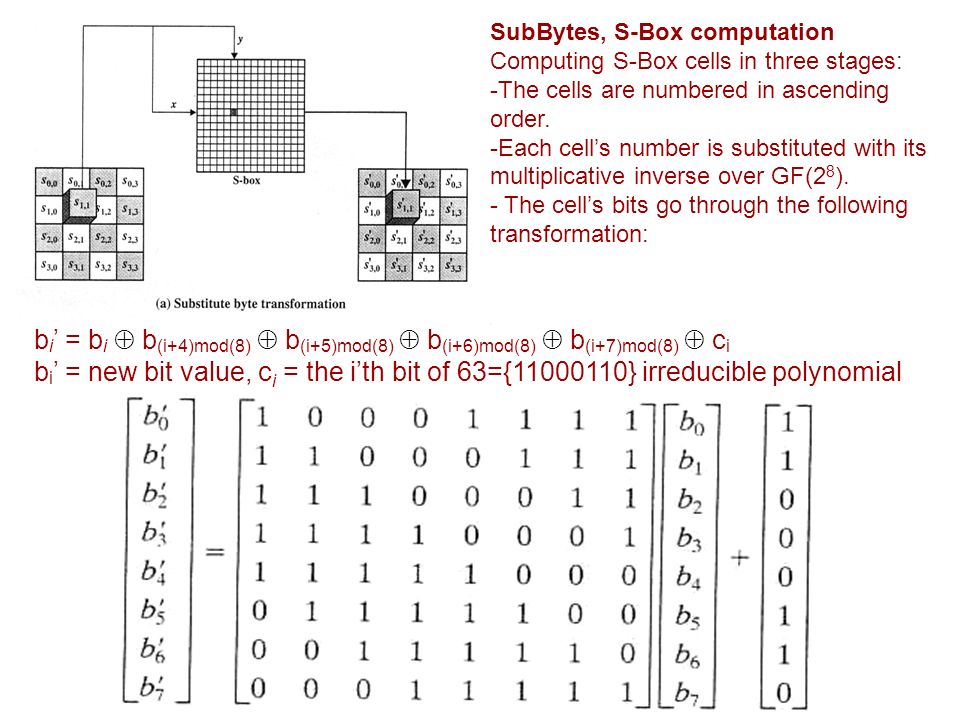
Cryptography And Network Security Ppt Video Online Download
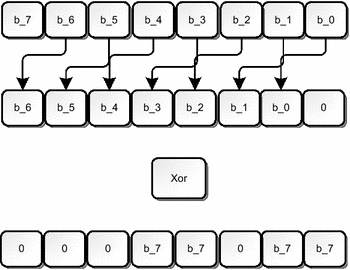
An Algorithm To Generating Inverse S Box For Rijndael Encryption Standard Springerlink

New S Box Calculation For Rijndael Aes Based On An Artificial Neural Network
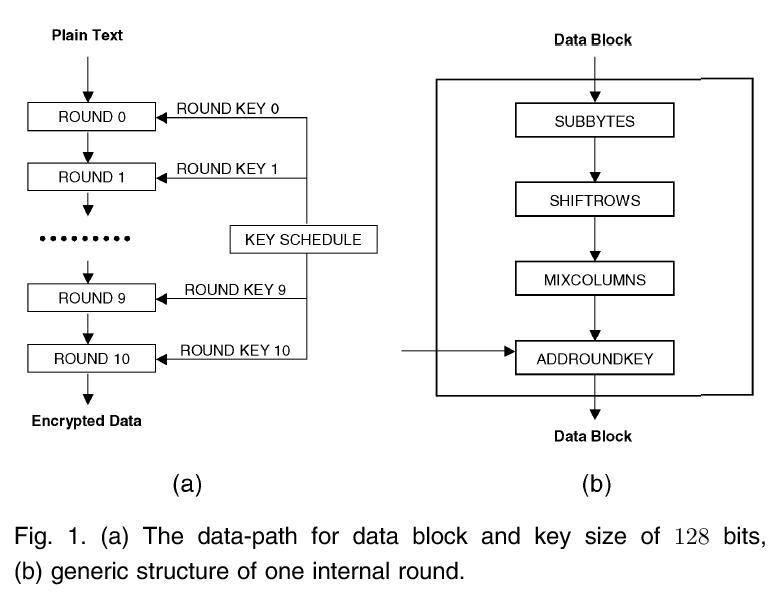
Locating Faults In An Implementation Of Aes
Ieeexplore Ieee Org Iel7 Pdf

Aes Advanced Encryption Standard Anu Vazhayil

Advanced Encryption Standard Aes Transformation Functions

How Is The Matrix Created Using Isomorphic Transform Fucntion And Isomorphic Inverse Transform Function Stack Overflow
Q Tbn And9gcqpjqtbzw9obw6g33qmkd0ub6ugtsa6mkxmxxa5ujwocvqlvitpk13 Ljujvmndiyo8xxv0bhxrtw Usqp Cau Ec

How Are The Aes Inverse S Boxes Calculated Cryptography Stack Exchange

The Advanced Encryption Standard Aes Algorithm Commonlounge
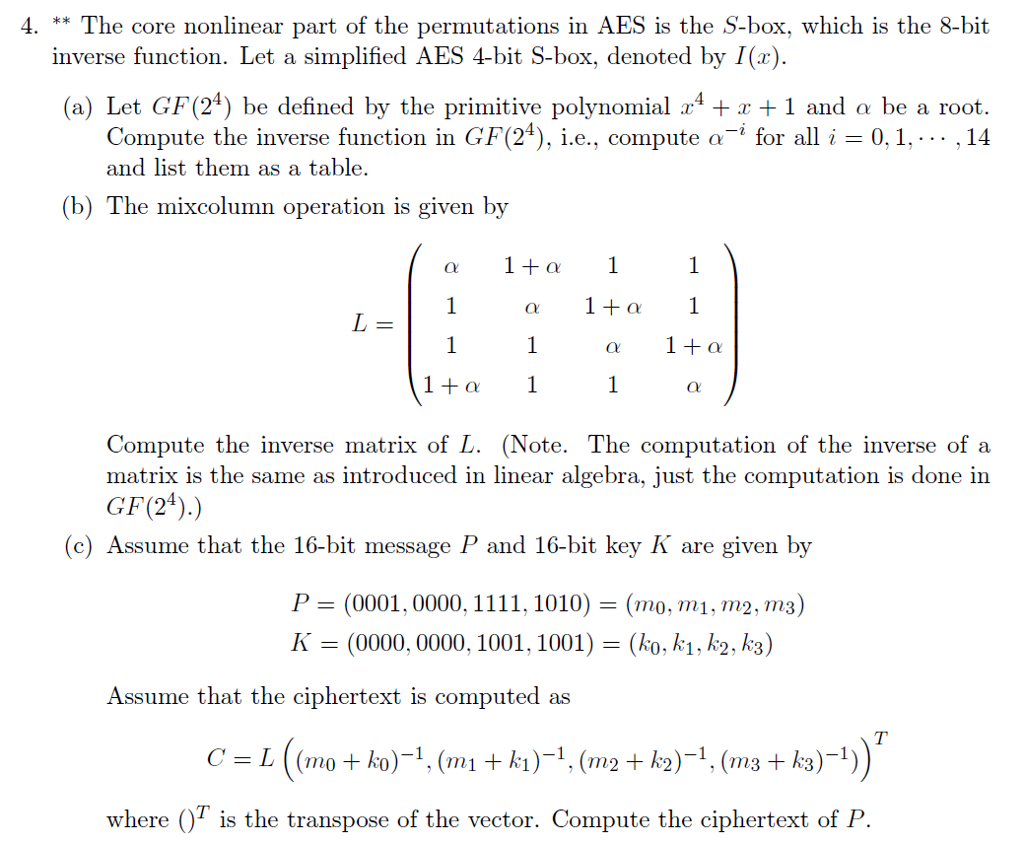
4 The Core Nonlinear Part Of The Permutations Chegg Com

Pdf An Improved Aes S Box And Its Performance Analysis Semantic Scholar
A Novel Byte Substitution Architecture For The Aes Cryptosystem
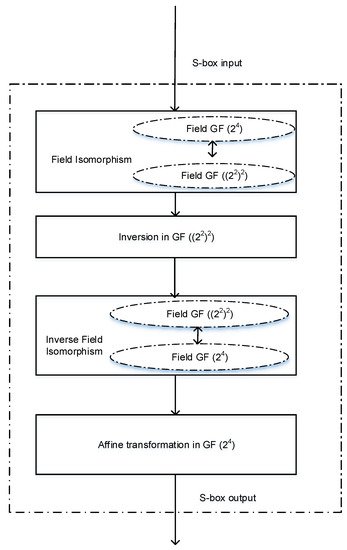
Information Free Full Text Lightweight S Box Architecture For Secure Internet Of Things Html

The Strongest Encryption Algorithm Matlab And Verilog Realization Of Aes Encryption Algorithm Programmer Sought
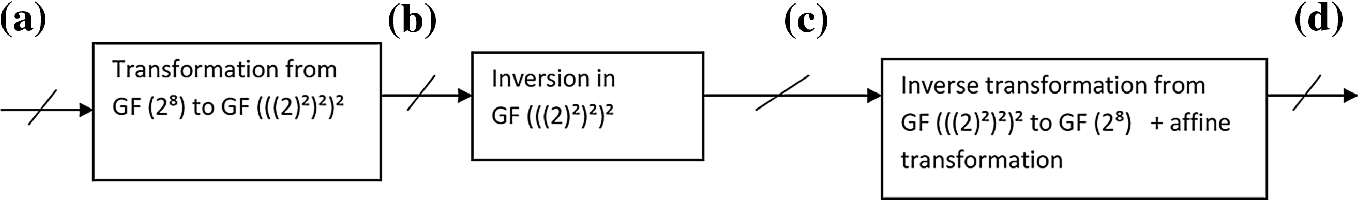
Compact And Secure S Box Implementations Of Aes A Review Springerlink
Http Www Jcreview Com Fulltext 197 Pdf

Fpga Implementation Of Subbyte Inverse Subbyte For Aes Algorithm
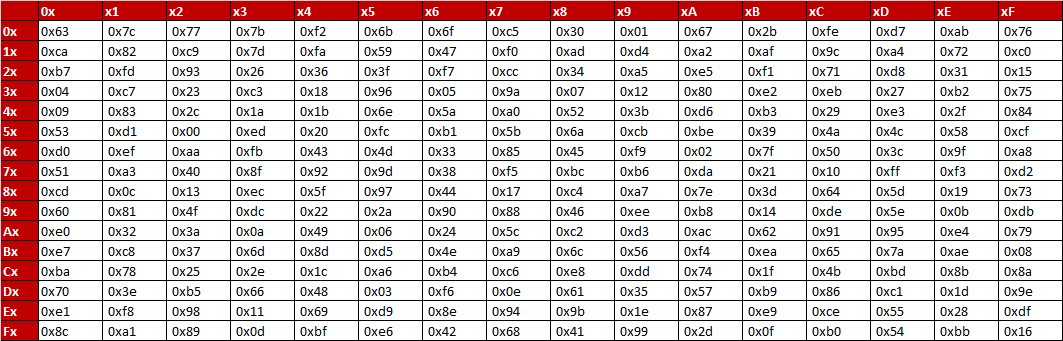
Aes Encryption
Http Eprint Iacr Org 11 332 Pdf
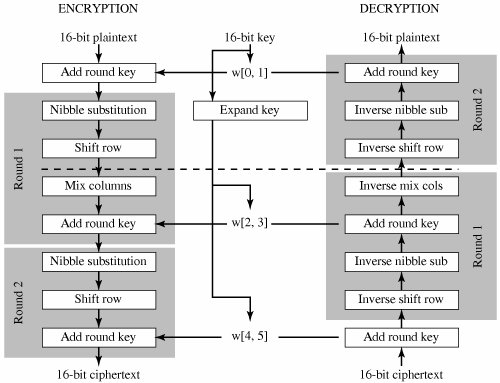
Appendix 5b Simplified Aes Cryptography And Network Security 4th Edition
Sect Ctf 17 Bad Aes

Making Aes Stronger Aes With Key Dependent S Box Semantic Scholar

Inverse S Box Substitution Values For The Byte Xy In Hexadecimal Format Download Scientific Diagram

How Are S Box Calculated In S Aes Cryptography Stack Exchange

The Advanced Encryption Standard Aes Algorithm Commonlounge
Http Www Iaeme Com Masteradmin Uploadfolder Ijecet 07 01 001 Ijecet 07 01 001 Pdf
Www Alliedjournals Com Download Data Ijems V2is Pdf

The Advanced Encryption Standard Aes Algorithm Commonlounge

Rijndael S Box Wikipedia

A Very Compact Aes Spiht Selective Encryption Computer Architecture Design With Improved S Box
Aes Encryption

Z X And S X Are The Output Of S Box Of Aes And

New S Box Calculation For Rijndael Aes Based On An Artificial Neural Network

Achieving High Performance For Advanced Encryption Standard Aes Applications

Inverse S Box Of Aes Algorithm Download Scientific Diagram
Network Security Lec4

How We Can Calculate Aes Inverse Sbox Cryptography Stack Exchange

High Speed Area Efficient Implementation Of Aes Algorithm On Reconfigurable Platform Intechopen

The Advanced Encryption Standard Aes Algorithm Commonlounge

Z X And S X Are The Output Of S Box Of Aes And

Explaon Like I M Five The Rijndael S Box Crypto
2

Inverse S Box Substitution Values For The Byte Xy In Hexadecimal Format Download Scientific Diagram
Q Tbn And9gctlnljm65h2hel8t5uvk9uut3lz7kvbjtq0nyrjfoocjjv Kiqd9wohbavjspdbmeaovjyb Am3fq Usqp Cau Ec

Figure 3 From Novel Architecture For Inverse Mix Columns For Aes Using Ancient Vedic Mathematics On Fpga Semantic Scholar

New S Box Calculation For Rijndael Aes Based On An Artificial Neural Network

Aes Inverse S Box 23 Download Scientific Diagram
Section 5 2 The Aes Cipher Cryptography And Network Security 4th Edition

Advanced Encryption Standard Aes Transformation Functions

New S Box Calculation For Rijndael Aes Based On An Artificial Neural Network
A Novel Byte Substitution Architecture For The Aes Cryptosystem

A Very Compact Aes Spiht Selective Encryption Computer Architecture Design With Improved S Box
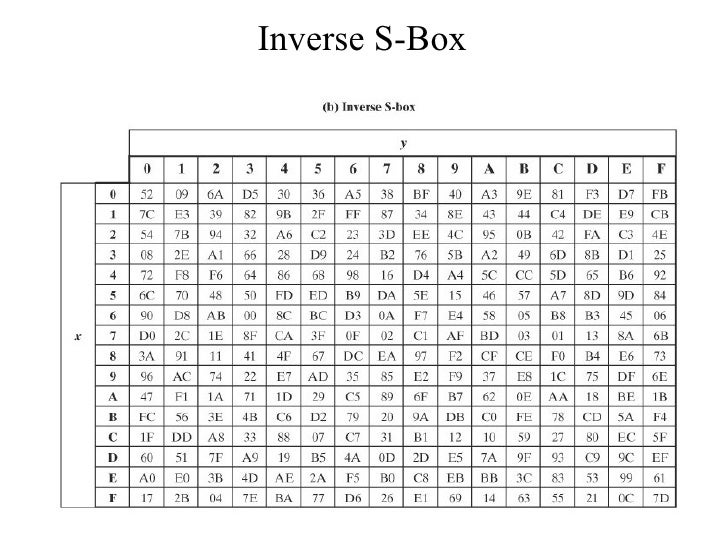
Unit V Network Management And Security

Table 5 From Dynamic Aes 128 With Key Dependent S Box Semantic Scholar

Table 3 From Encryption Using Dual Key Transformation Based On Creation Of Multi S Boxes In Aes Algorithm Semantic Scholar
Http Euler Ecs Umass Edu Ece597 Pdf Crypto Part4 Aes Pdf

Woa1 Technologies For Modifying A First Cryptographic Cipher With Operations Of A Second Cryptographic Cipher Google Patents

Image Encryption Using Aes Key Expansion
Iopscience Iop Org Article 10 10 1757 9x 978 1 0142 Pdf
Http Www Ijera Com Papers Vol3 Issue1 Iw Pdf
Dl Acm Org Doi Pdf 10 1145

New S Box Calculation For Rijndael Aes Based On An Artificial Neural Network
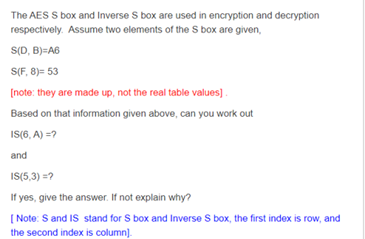
Solved The Aes S Box And Inverse S Box Are Used In Encryp Chegg Com

The Inverse Affine Transformation Of Aes Sbox Uses Different Additive Constant Cryptography Stack Exchange
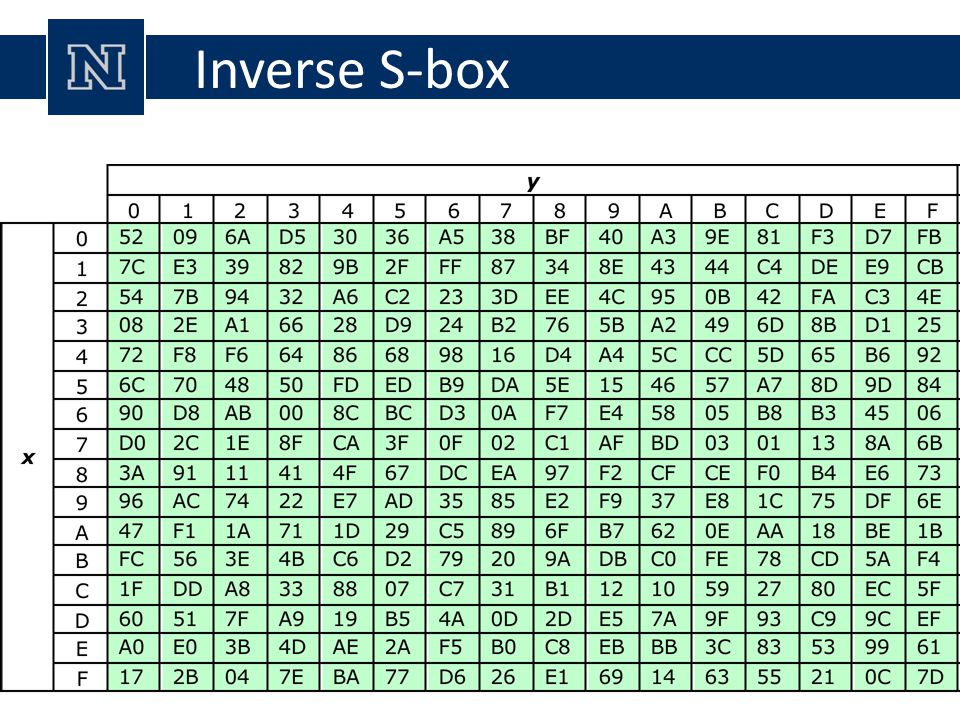
Lecture 23 Symmetric Encryption Ppt Download

The Inverse Affine Transformation Of Aes Sbox Uses Different Additive Constant Cryptography Stack Exchange

Ece 5760



