S Boxes In Des Map
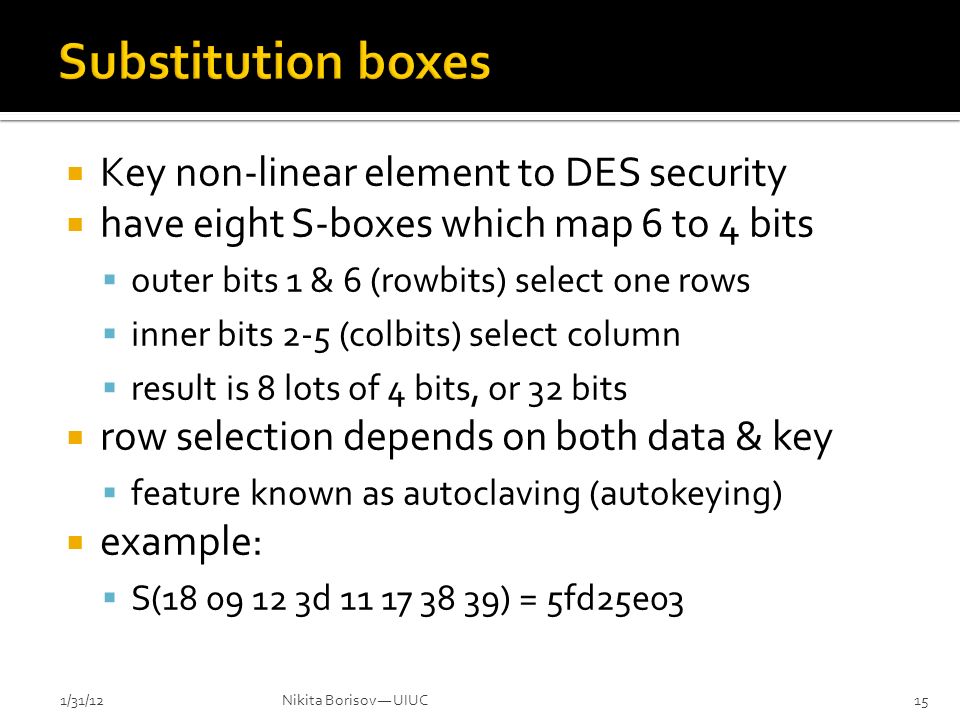
Cs461 Ece422 Spring Commercial Symmetric Systems Des Aes Modes Of Block And Stream Ciphers 21 31 12nikita Borisov Uiuc Ppt Download

Abb Locations Map

How Can Des Have 6x4 S Boxes And Still Be Reversible Theoretical Computer Science Stack Exchange

S Box Matrix With Explanation To Substitution Operation Download Scientific Diagram

Modified Data Encryption Standard Encryption Algorithm With Improved Error Performance And Enhanced Security In Wireless Fading Channels Zibideh 15 Security And Communication Networks Wiley Online Library

Exam Questions For The Course Ttm Information Security May Part 1 Pdf Free Download
The CAST Sboxes use bent functions (the most highly nonlinear Boolean functions) as their columns That is, the mapping from all the input bits to any single output bit is a bent function A paper on generating the Sboxes is Mister & Adams "Practical Sbox Design" Bent functions are combined to get additional desirable traits — a balanced Sbox (equal probability of 0 and 1 output), minimum correlation among output bits, and high overall Sbox nonlinearity.

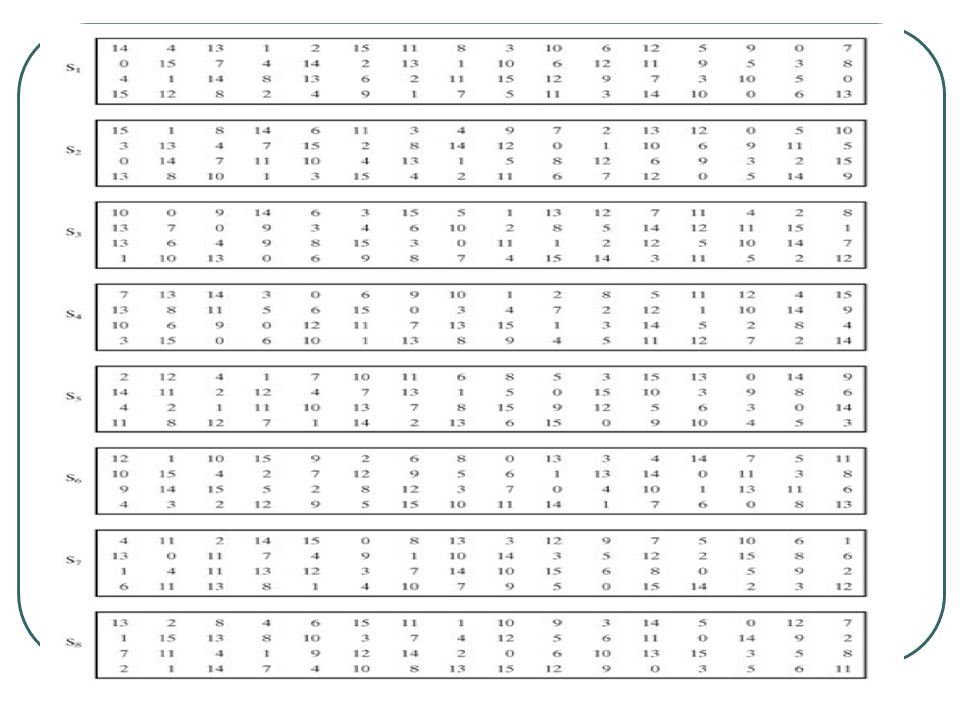
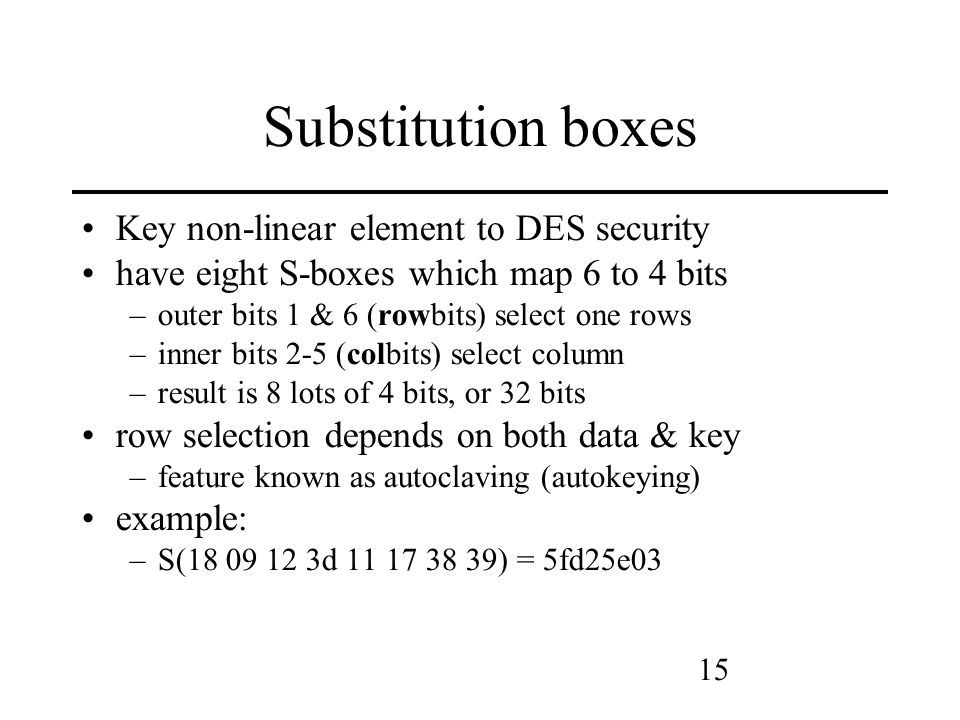
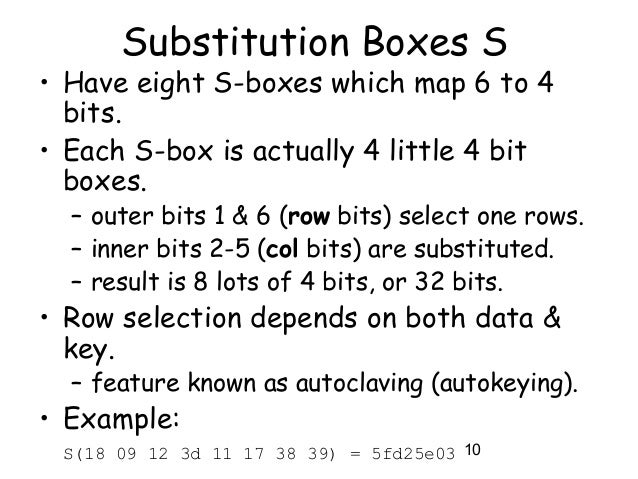
S boxes in des map. Figure 2 Sboxes Source Internet Now, to use these Sboxes, Python list can be very handy which have concept of list within list So, a Python list will have 8 element representing each of these eight Sboxes and then each of these 8 element will further have four list, one for each row and finally each row itself will be a Python list holding row values indexed between 0–15. Sboxes in DES map A) 2 to 4 bits B) 4 to 4 bits C) 6 to 4 bits D) 4 to 6 bits ANSWER C Unit 01 Q040 What is the biggest advantage of CBC mode of operation A) It can encrypt in parallel different parts of the messages B) It does not need Initialization Vector (IV). Sboxes in DES are nonlinear show that S1(X1) XOR S1(X2) is not S1(x1 XOR x2) x1= x2=.
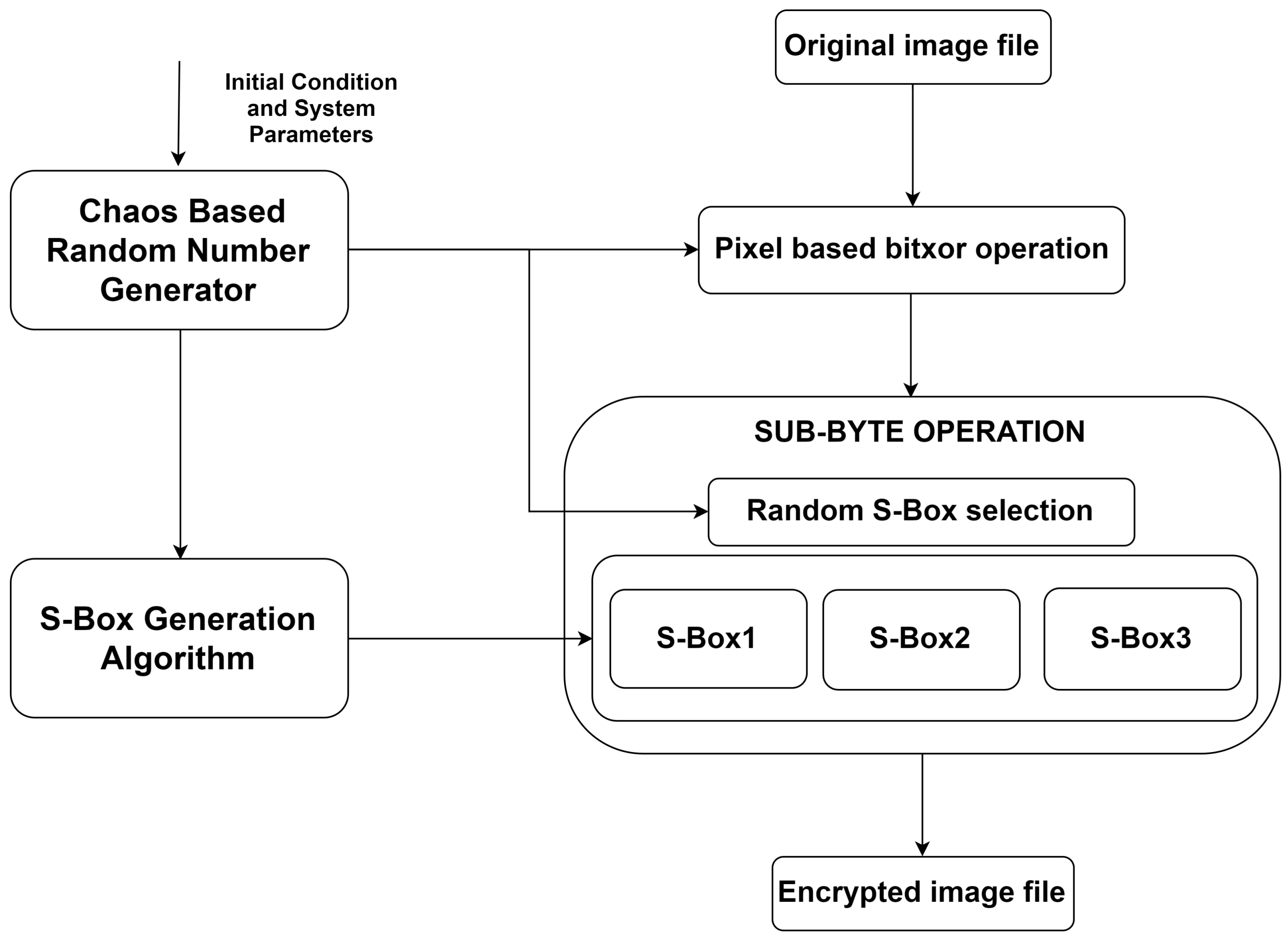
In this paper, new method for creating dynamical keydependent Sboxes based on 2D logistic map and 2D cross map is presented The results show that generated S Boxes have very low linear and differential probabilities and satisfy also the avalanche criterion and strict avalanche criterion (SAC). The 8 SBoxes of DES were the subject of intense study for many years out of a concern that a backdoor — a vulnerability known only to its designers — might have been planted in the cipher The SBox design criteria were eventually published (Don Coppersmith, 1994). All Warehouses will now be closing at 4pm CST All orders placed after will ship the following day Please call your local branch prior to pickingup your order so we can set it outside to minimize contact during this time.
The Sboxes give cryptosystems the confusion property described by Shannon and are used in conventional block ciphers such as the Data Encryption Standard (DES) and the Advanced Encryption Standard (AES) The security in these cryptographic systems depends mainly on the properties of Sboxes used. By using chaotic maps, Jakimoski and Kocarev have proposed a fourstep method to create Sboxes , which includes choosing a chaotic map, discretizing the chaotic map, key scheduling and cryptanalysis, and illustrated an Sbox which satisfies nice cryptographic properties. The S‐box is a mapping table that maps a 6‐bit input to a 4‐bit output In DES, each of the eight S‐boxes has a distinct mapping table The S‐boxes were initially designed in such a way to meet the avalanche criterion 17.
Mathematically, an n x n size of Sbox is a nonlinear mapping S {0,1}supn right arrow {0,1}supn, where {0,1}supn represents the vector spaces of n elements from GF (2), and we set n = 8 in this paper Many papers on Sboxes have been published by scholars around the world over the past decades. Keyword Dynamical SBox, Block Cipher, KeyDependence, 2D logistic map, 2D cross map, 2D cat map I Introduction The Sbox is the core component of most block ciphers, such as the Data Encryption Standard (DES), the Advanced Encryption Standard (AES) and so on. Sequential application of confusion and diffusion Typically, confusion is provided by some form of substitution ("Sboxes") So the obvious question is whether some substitutions are better than others The obvious answer is "Yes," because one possible substitution maps every value onto itself, just as though there.
The fact that the Sboxes are randomly keydependent and unknown is the main strength of the new approach, since both linear and differential cryptanalysis require known Sboxes In the paper, we briefly analyze the AES algorithm, substitution Sboxes, linear and differential cryptanalysis, and describe a randomly keydependent Sbox and. The 32 output bits of the Sboxes are then subjected to the DES Pbox Permutation The Pbox Permutation is a fixed bijective permutation that maps 32input bits to 32 output bits Lastly, the. The proposed method uses a discrete chaotic map based on the composition of permutations The obtained Sboxes have been tested on the number of criteria, such as bijection, nonlinearity, strict avalanche criterion, output bits independence criterion, equiprobable input/output XOR distribution and maximum expected linear probability.
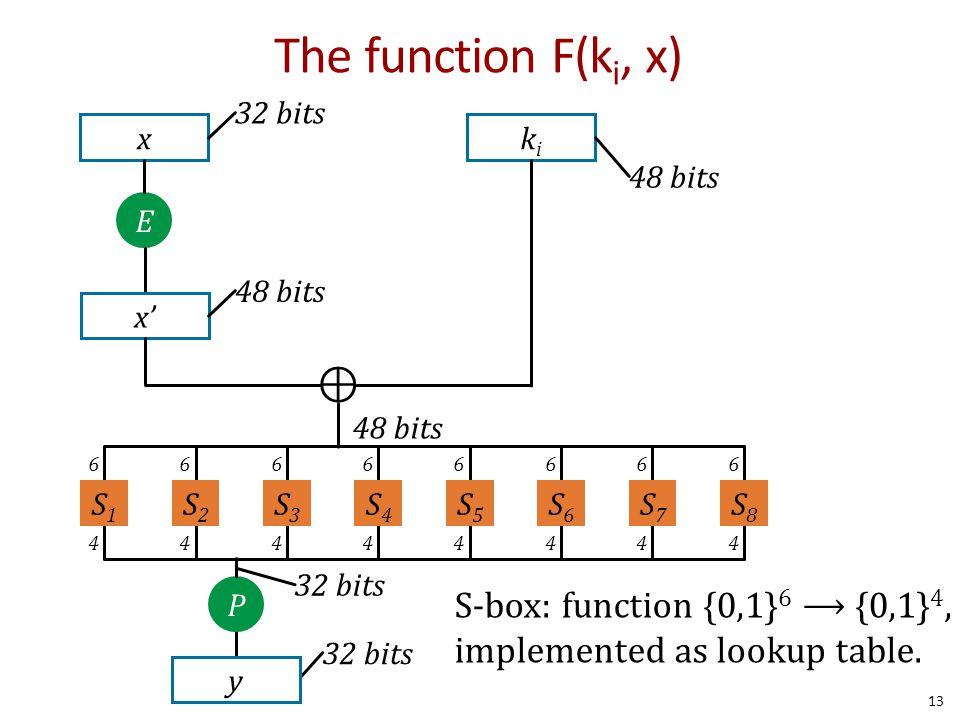
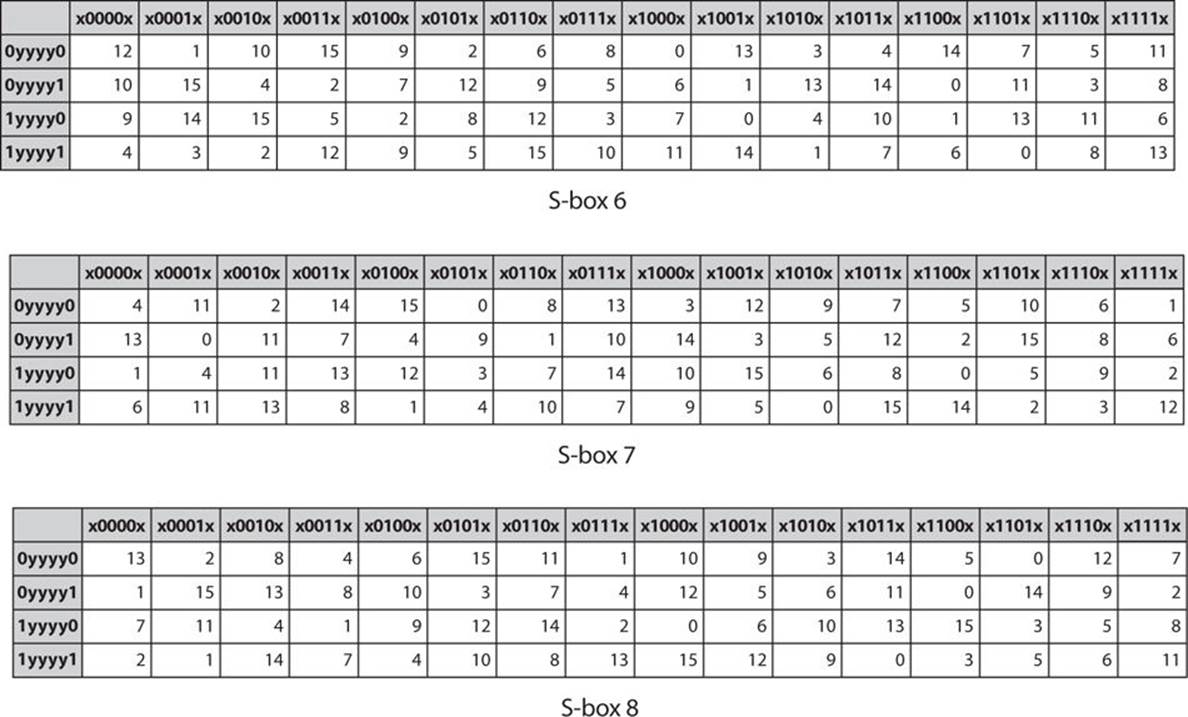
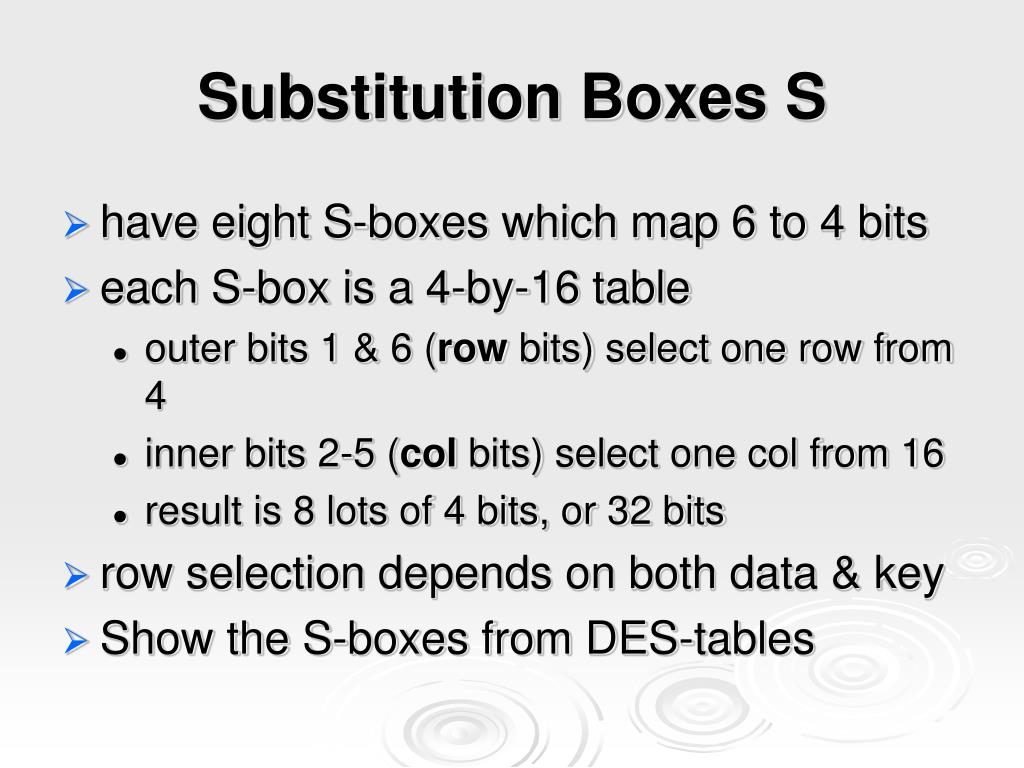
DES Sbox (Substitution Box) • 8 “substitution boxes” or Sboxes • Each Sbox maps 6 bits to 4 bits • Sbox number 1 input bits (0,5) ↓ input bits (1,2,3,4). One good example of a fixed table is the Sbox from DES (S 5), mapping 6bit input into a 4bit output Given a 6bit input, the 4bit output is found by selecting the row using the outer two bits (the first and last bits), and the column using the inner four bits. Data encryption standard (DES) has been found vulnerable against very powerful attacks and therefore, the popularity of DES has been found slightly on decline DES is a block cipher, and encrypts data in blocks of size of 64 bit each, means 64 bits of plain text goes as the input to DES, which produces 64 bits of cipher text.
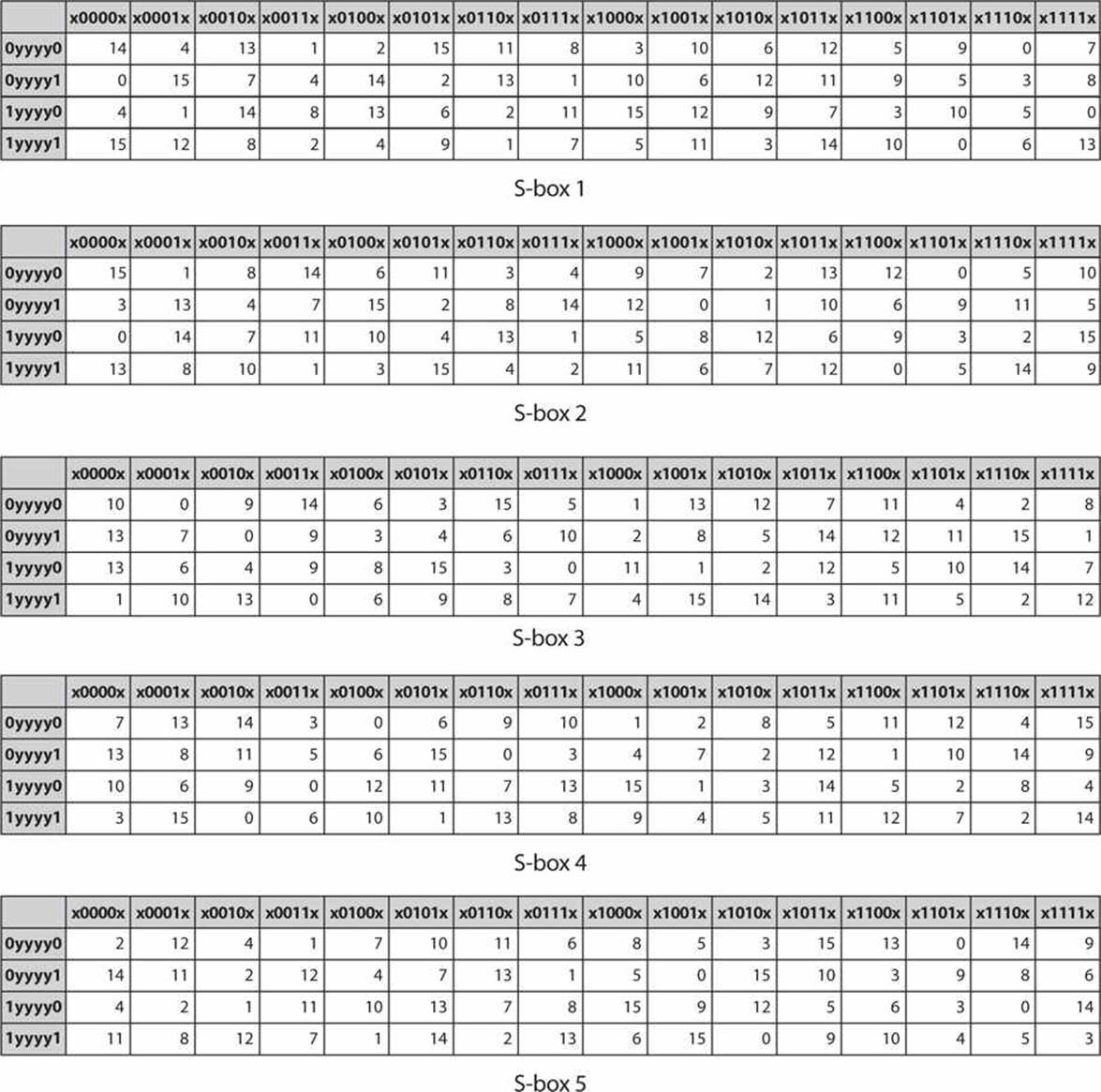
Substitution boxes (Sboxes) This table lists the eight Sboxes used in DES Each Sbox replaces a 6bit input with a 4bit output Given a 6bit input, the 4bit output is found by selecting the row using the outer two bits, and the column using the inner four bits. Figure 2 Sboxes Source Internet Now, to use these Sboxes, Python list can be very handy which have concept of list within list So, a Python list will have 8 element representing each of these eight Sboxes and then each of these 8 element will further have four list, one for each row and finally each row itself will be a Python list holding row values indexed between 0–15. Now that we’ve linked what people do to what the organization wants to accomplish by identifying what they need to produce (the Performance Chain), we can identify and coordinate all the factors that affect a change in behavior, what we call behavior influences Behavior influences comprise the farleft link in the Performance Chain, the enablers of human performance.
The S boxes are kind of the smarts of, DES And then, the S box is basically a map, six bits to four bits So, the outputs of the S boxes are these four bits. All Warehouses will now be closing at 4pm CST All orders placed after will ship the following day Please call your local branch prior to pickingup your order so we can set it outside to minimize contact during this time. $\begingroup$ Also the document by D Coppersmith that says (This was the largest size that we could accommodate and still fit all of DES onto a single chip in 1974 technology) So maybe thats why they didn't make sboxes bigger, 256 bytes of sbox data might have been 'big' back then already I was going to make this a question but didn't have a good, thing, so I tacked it on as a comment.
Full Size cipher and Partial key cipher;. Data Encryption StandardDES is a feistel cipherBlock Length is 64 bitKey Length is 56 bitNo of rounds are 16Each round is applied on one Block CipherSecurity depends primarly on "sboxes"Each Sboxes maps 6 bits to 4bits Objectives Block cipher;. An Sbox is an integral component of the cryptographic systems which performs substitution Fundamentally, a bijective n × n substitutionbox is a mathematical onetoone mapping S from to, where n is its order denoting the inputs and outputs sizes.
DES Round Structure S Boxes and Key Schedule zThere are eight Sboxes in DES, each one maps 6 bits to 4 bits zHow to use the Sboxes – Sbox is 4 rows by 16 columns – Input is 6 bits The first and last bit determine the row, the middle 4 bits determine the column. An efficient software implementation of the round function of the Data Encryption Standard (DES) involves mathematical transformations performed on the DES round function and the DES round key computation function that reduce the computation required to complete a DES round on generalpurpose, embedded, and cryptographic processors These transformations shift computation associated with the. Instructor We're taking the first big stepinto the structure of modern block ciphersNow we'll talk about Sboxes and PboxesSubstitution boxes and permutation boxesare key components of modern block ciphersSboxes are nonlinear transformationsof a few input bits that provide confusionand Pboxes simply shuffle the input bits aroundto provide diffusion as we've.
Components of a Modern Block CipherP Box. Round i has input L i1,R i1 and output L i,R i;. Data Encryption Standard (DES) 1 Block Ciphers • Map nbit plaintext blocks to nbit ciphertext blocks (n = block length) Sboxes • Sboxes are the only nonlinear elements in DES design • S = matrix 4x16, values from 0 to 15 • B (6 bit long) = b1b2b3b4b5b6.
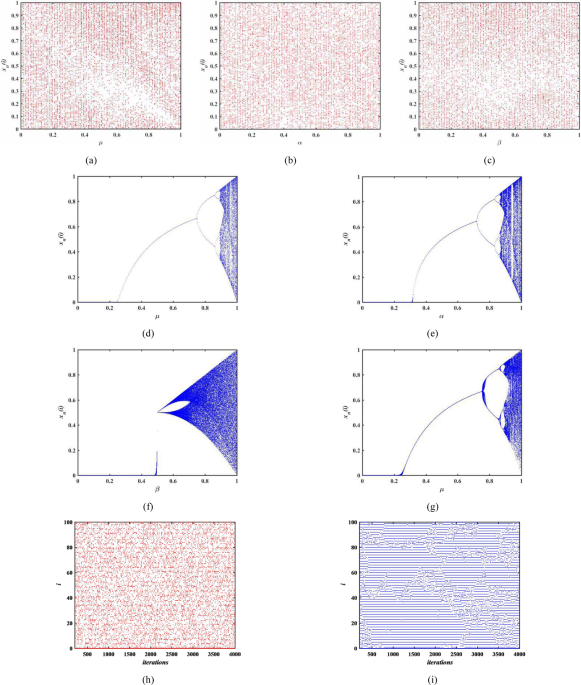
04 To construct SBoxes based on only one map, we just omit the 03 02 second step and change the first one by the arbitrarily choose 01 of the corresponding map initial condition For the next 0 results we set n=258 and N=550. And so, a dynamic Sboxes are des i gned using L atin Square doubly stochastic ma trix was proposed by W u and Noonan 3 Then, a new approach f or generating Sbox is a map,. Data encryption standard (DES) has been found vulnerable against very powerful attacks and therefore, the popularity of DES has been found slightly on decline DES is a block cipher, and encrypts data in blocks of size of 64 bit each, means 64 bits of plain text goes as the input to DES, which produces 64 bits of cipher text.
Image encryption and decryption using 3D chaotic map with AES key dependent SBoxes It contains four major parts which are Exclusive Xor forward and backward, 3D Logistic Map, 3D Chebyshev map, and 2D Arnold Cat Map, and Dynamic Sbox of AES Here, Exclusive Xor is used for image diffusing 3D. DES ENCRYPTION Plainext is broken into blocks of length 64 bitsEncryption is blockwise A message block is first gone through an initial permutation IP,then divided into two parts L 0,where L 0 is the left part of 32 bits and R 0 is the right part of the 32 bits;. L i = R i1,R i = L i1 ⊕ f(R i1,K i) and K i is the subkey for the 'i'th.
Sboxes in DES are nonlinear show that S1(X1) XOR S1(X2) is not S1(x1 XOR x2) x1= x2=. (1 point) This question concerns the DES Sboxes Please enter all answers in decimal Consider the two 6bit numbers x1 = and x2 =. In In this paper, an efficient method for designing dynamical key dependent Sboxes based on 2D logistic map and 2D cross map Sbox is a nonlinear transformation where each byte of the State is replaced by another byte using the substitution table Each individual byte of State is mapped into a new byte by using 2D cat map.
The Sboxes give cryptosystems the confusion property described by Shannon and are used in conventional block ciphers such as the Data Encryption Standard (DES) and the Advanced Encryption Standard (AES) The security in these cryptographic systems depends mainly on the properties of Sboxes used. Instructor We're taking the first big stepinto the structure of modern block ciphersNow we'll talk about Sboxes and PboxesSubstitution boxes and permutation boxesare key components of modern block ciphersSboxes are nonlinear transformationsof a few input bits that provide confusionand Pboxes simply shuffle the input bits aroundto provide diffusion as we've. The proposed methodology employs twodimensional discrete Henon map for (i) generation of dynamic and keydependent Sbox that could be integrated with symmetric algorithms like Blowfish and Data Encryption Standard (DES) and (ii) generation of onetime keys for simple substitution ciphers.
West Des Moines UMC BHA Little Pantry The Hill Baptist Church Creations Little Pantry Little Free Pantry Little Free Pantry First Presbyterian Statesboro Concordia's Blessing Box Little Food Library The Little White Chapel Pantry Blessing BoxLittle Free Pantry Mexia The Free Little Pantry Sacred Heart Church Blessing Box The. 04 To construct SBoxes based on only one map, we just omit the 03 02 second step and change the first one by the arbitrarily choose 01 of the corresponding map initial condition For the next 0 results we set n=258 and N=550.

Function S Box S1 In The Des Algorithm Represented As A Table And Its Download Scientific Diagram
S Box Design Symmetric Ciphers And Hashes Modern Cryptography Applied Mathematics For Encryption And Informanion Security 16

What Is S Meant By S Box Row And Column In Des Cryptography Stack Exchange
Cryptography Block Ciphers Ppt Video Online Download

Des Decryption And Weaknesses Of Des S Box Properties Youtube
Http Www Cs Man Ac Uk Banach Comp Info Courseslides Wk2 1 Des Pdf
Pdf Analysis Of Development Of Dynamic S Box Generation
Computer And Network Security Rabie A Ramadan Lecture Ppt Download
A Highly Nonlinear Substitution Box S Box Design Using Action Of Modular Group On A Projective Line Over A Finite Field

Rijndael S Box Wikipedia

Cryptography And Network Security Chapter 3 Pdf Free Download

Novel Permutation Diffusion Image Encryption Algorithm With Chaotic Dynamic S Box And Dna Sequence Operation Aip Advances Vol 7 No 8
A New Image Encryption Scheme Based On Coupling Map Lattices With Mixed Multi Chaos Scientific Reports

World Wellness Map Of World Wellness Weekend

A Block Cipher With Dynamic S Boxes Based On Tent Map Request Pdf

Highly Dispersive Substitution Box S Box Design Using Chaos Bin Faheem Etri Journal Wiley Online Library
Solved Complete The Concept Map To Name Classify And Des Chegg Com

Partition Based Trapdoor Ciphers Intechopen

How To Teach Des Using Python The Easy Way Part 2 Round Function F By Ajit Kumar Medium

Function S Box S1 In The Des Algorithm Represented As A Table And Its Download Scientific Diagram
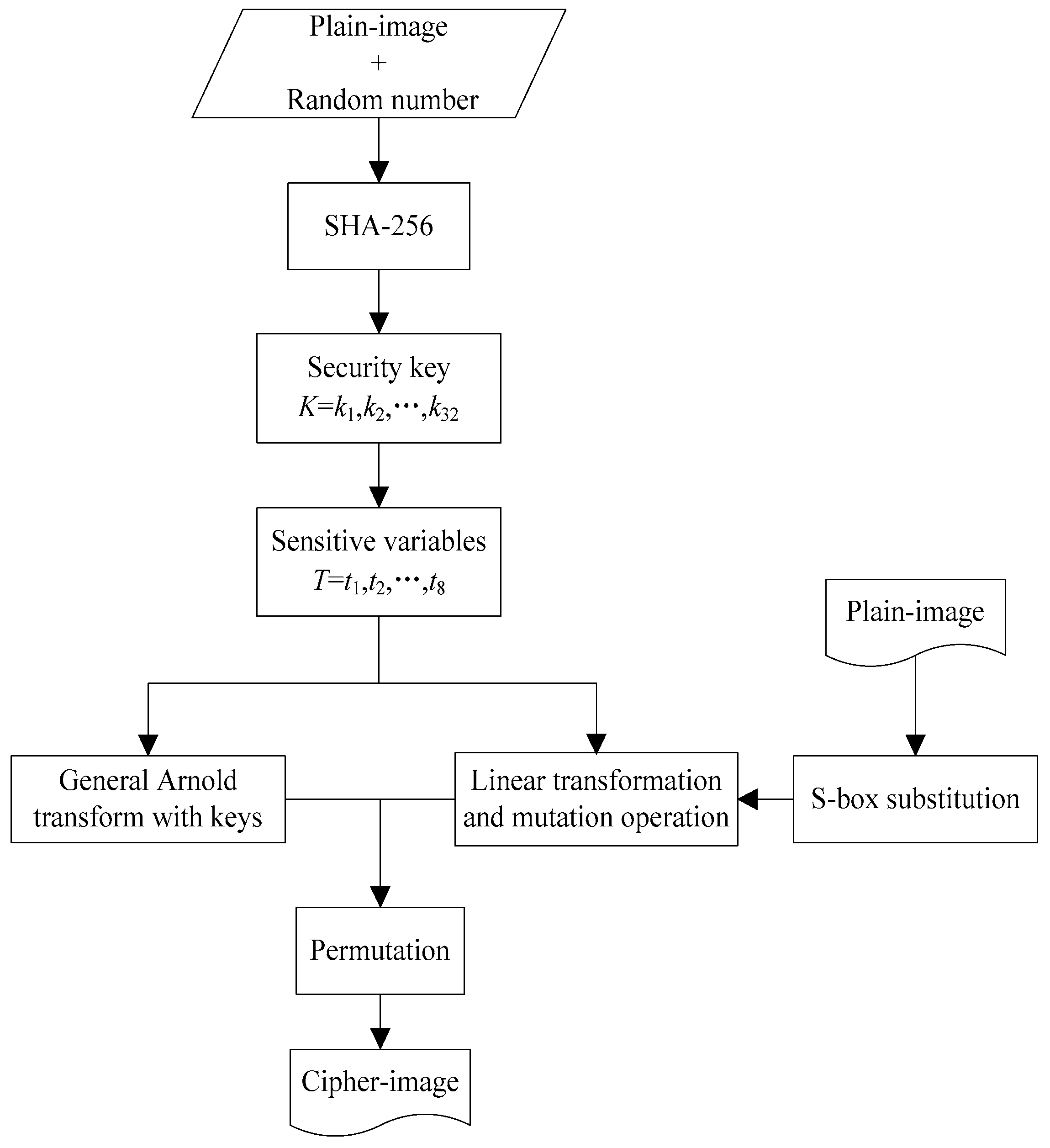
Entropy Free Full Text Quantum Image Encryption Scheme Using Arnold Transform And S Box Scrambling Html

Office Centergy One Room Ppt Download

Construction Of New S Box Using Action Of Quotient Of The Modular Group For Multimedia Security
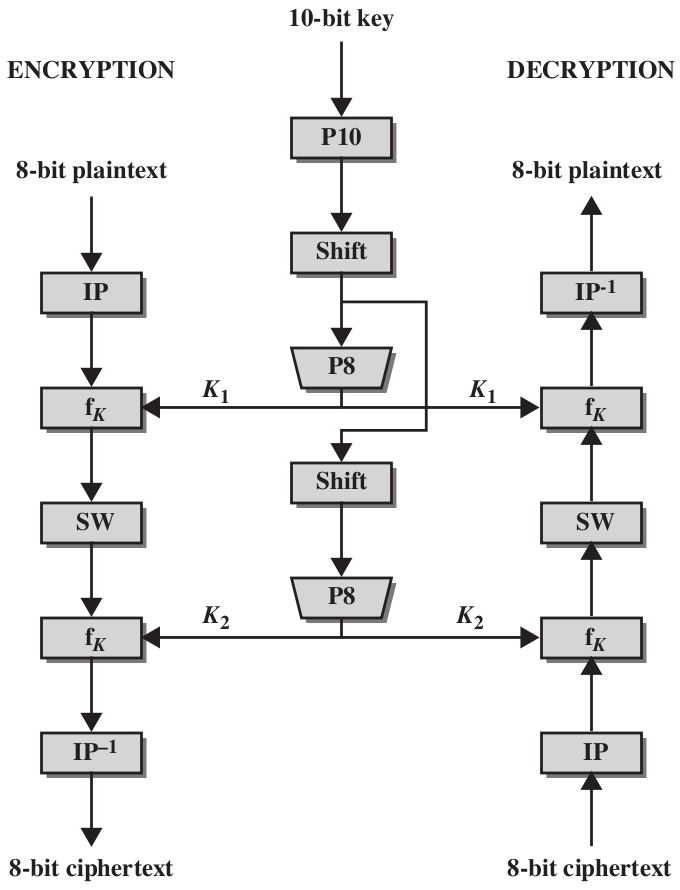
8 Data Encryption Standard

S Box Basic Question Cryptography Stack Exchange

Finding Output Given An S Box Input Of 8 Bits Cryptography Stack Exchange
Efficient Cryptosystem Approaches S Boxes And Permutation Substitution Based Encryption Springerlink

Depart Of Computer Science And Engineering Ppt Video Online Download
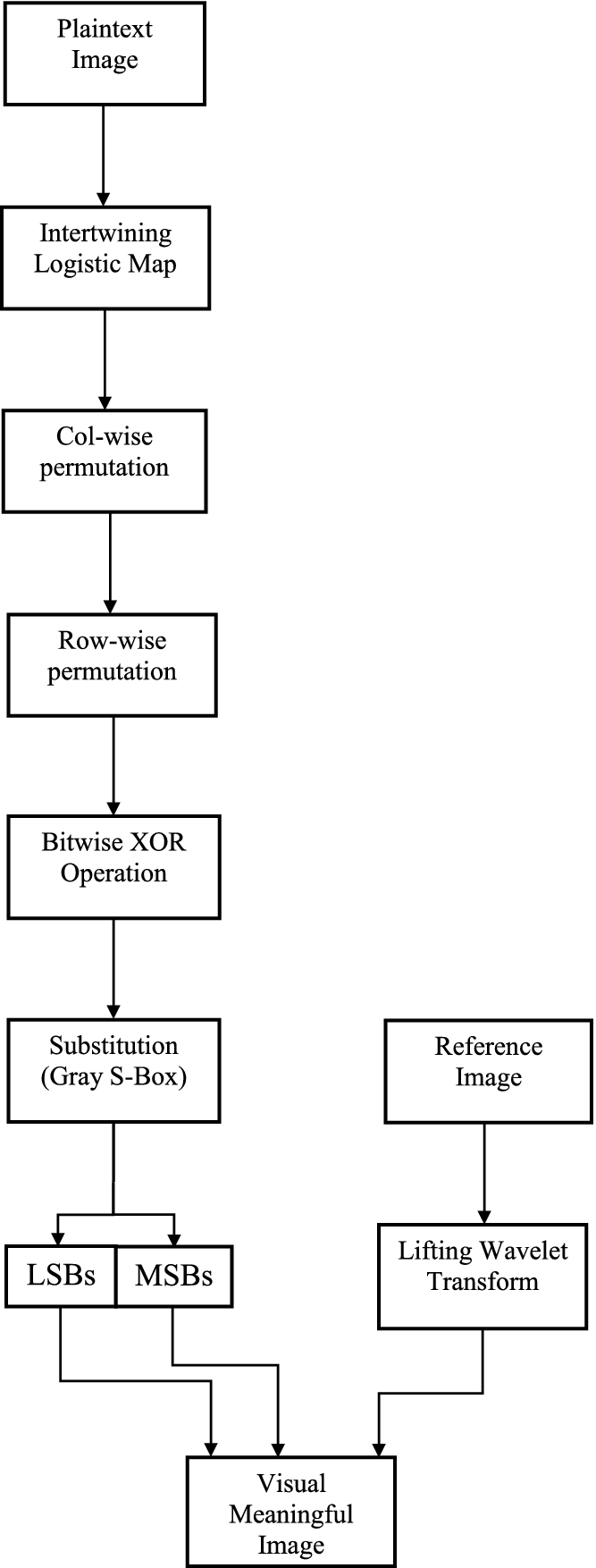
Visual Meaningful Encryption Scheme Using Intertwinning Logistic Map Springerlink

Construction Of New S Box Using Action Of Quotient Of The Modular Group For Multimedia Security

Des Supplementary Material Wikipedia
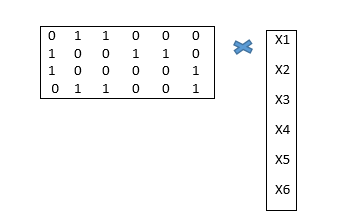
Data Encryption Standard
S Box Design Symmetric Ciphers And Hashes Modern Cryptography Applied Mathematics For Encryption And Informanion Security 16

Solved Date Show That X 3 Mod I Have No Solution X 12 Chegg Com

An Algorithm For The Construction Of Substitution Box For Block Ciphers Based On Projective General Linear Group Aip Advances Vol 7 No 3

Des Substitution Boxes Youtube

Des And Feistel Cipher Cryptography Stack Exchange

Generation Of Dynamical S Boxes For Block Ciphers Via Extended Logistic Map
Ppt Modern Block Ciphers Powerpoint Presentation Free Download Id

Generation Of Dynamical S Boxes For Block Ciphers Via Extended Logistic Map

S Box Youtube

Generation Of Dynamical S Boxes For Block Ciphers Via Extended Logistic Map
8 Data Encryption Standard
Applied Sciences Free Full Text S Box Based Image Encryption Application Using A Chaotic System Without Equilibrium Html

Shambhu Upadhyaya Computer Science Eng University At Buffalo Ppt Download

Spn Method An S Box Substitutes A Small Block Of Bits The Input Of The Download Scientific Diagram
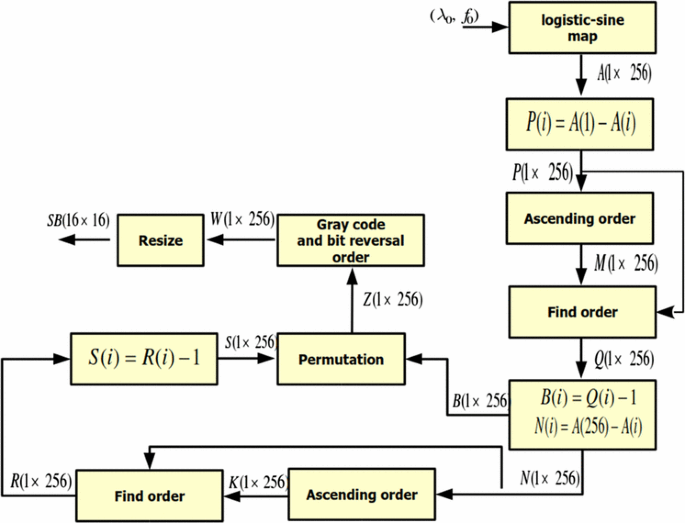
Efficient Cryptosystem Approaches S Boxes And Permutation Substitution Based Encryption Springerlink
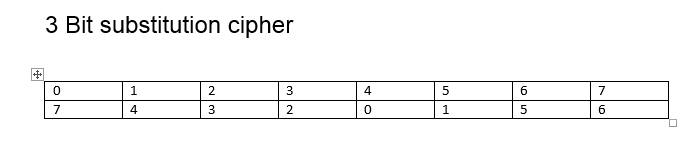
Data Encryption Standard
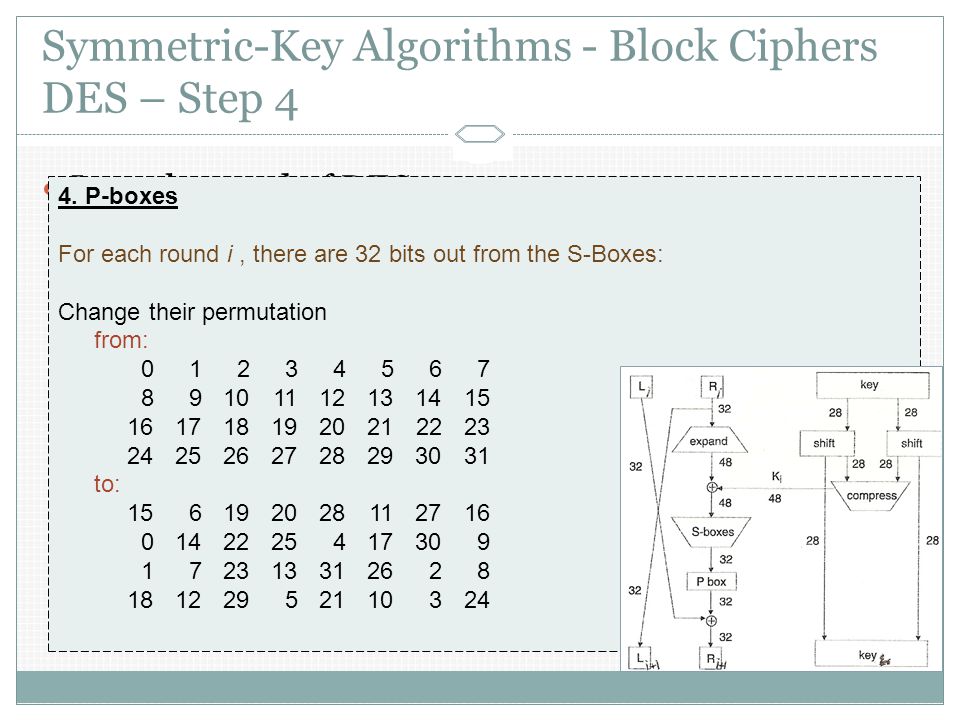
Cs 4 Sd Section By Dr Daniyal Alghazzawi 3 Information Security Ppt Download
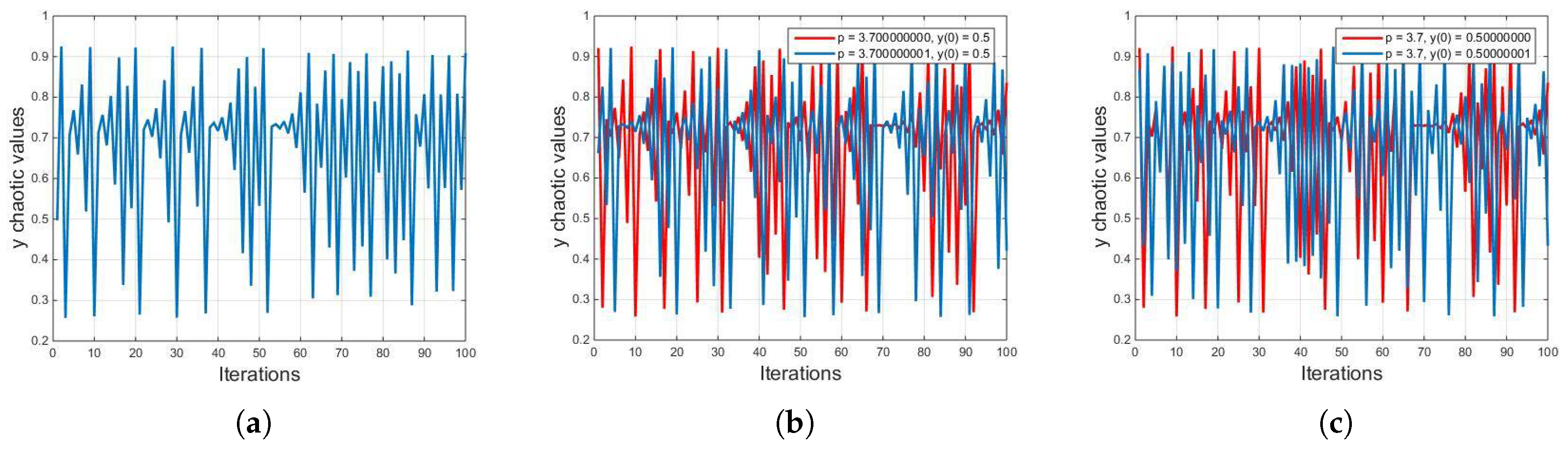
Symmetry Free Full Text Construction Of S Box Based On Chaotic Map And Algebraic Structures Html
1 Symmetric Cryptography Cs461 Ece422 Fall Outline Overview Of Cryptosystem Design Commercial Symmetric Systems Des Aes Modes Of Block And Stream Ppt Download
Data Encryption Standard

Generation Of Dynamical S Boxes For Block Ciphers Via Extended Logistic Map

Function S Box S1 In The Des Algorithm Represented As A Table And Its Download Scientific Diagram
Http Www Cs Man Ac Uk Banach Comp Info Courseslides Wk2 1 Des Pdf

Generation Of Dynamical S Boxes For Block Ciphers Via Extended Logistic Map

A New Classification Of 4 Bit Optimal S Boxes And Its Application To Present Rectangle And Spongent Springerlink
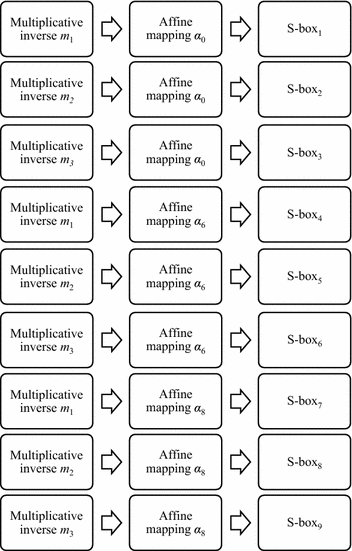
The Replacement Of Irreducible Polynomial And Affine Mapping For The Construction Of A Strong S Box Springerlink
Des Lecture

Highly Dispersive Substitution Box S Box Design Using Chaos Bin Faheem Etri Journal Wiley Online Library
Eprint Iacr Org 19 092 Pdf

Generation Of Dynamical S Boxes For Block Ciphers Via Extended Logistic Map
Q Tbn And9gcsn3qjcuyvzonhtmizy52avrzil4p7epgmihz3p6s Hwoeuufi Usqp Cau

Spn Method An S Box Substitutes A Small Block Of Bits The Input Of The Download Scientific Diagram

Function S Box S1 In The Des Algorithm Represented As A Table And Its Download Scientific Diagram
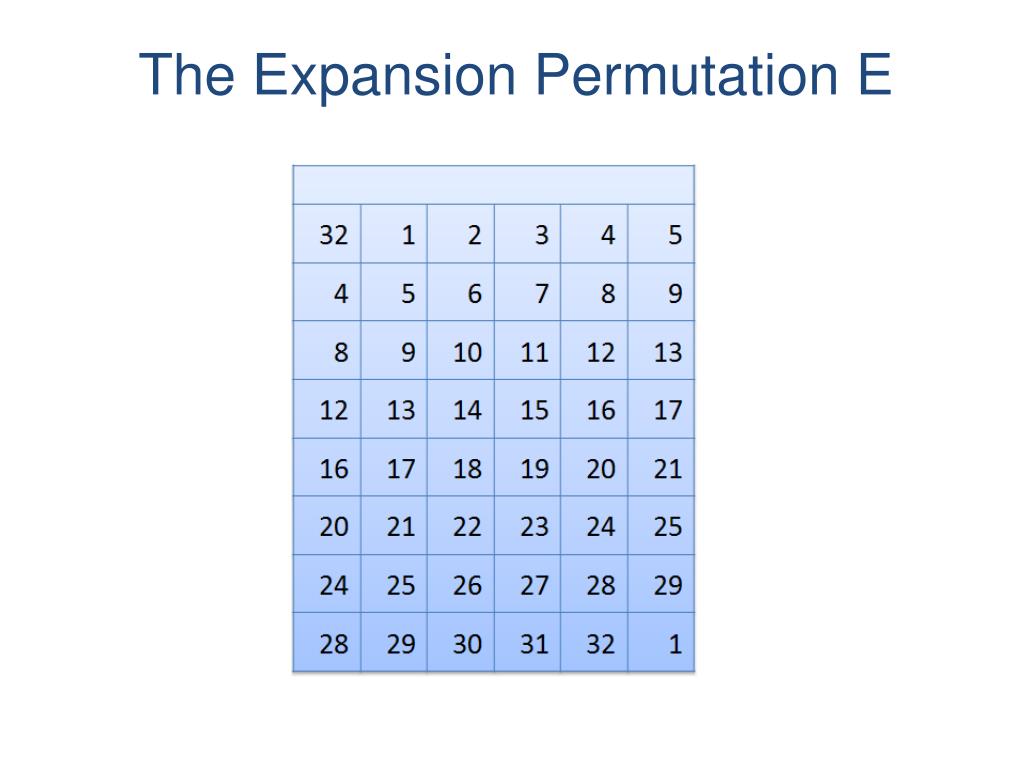
Ppt Modern Block Ciphers Powerpoint Presentation Free Download Id

S Box Basic Question Cryptography Stack Exchange
Securewww Esat Kuleuven Be Cosic Publications Article 2726 Pdf

Generation Of Dynamical S Boxes For Block Ciphers Via Extended Logistic Map
Eprint Iacr Org 680 Pdf
Www Lri Fr Fmartignon Documenti Systemesecurite 4 Des Pdf
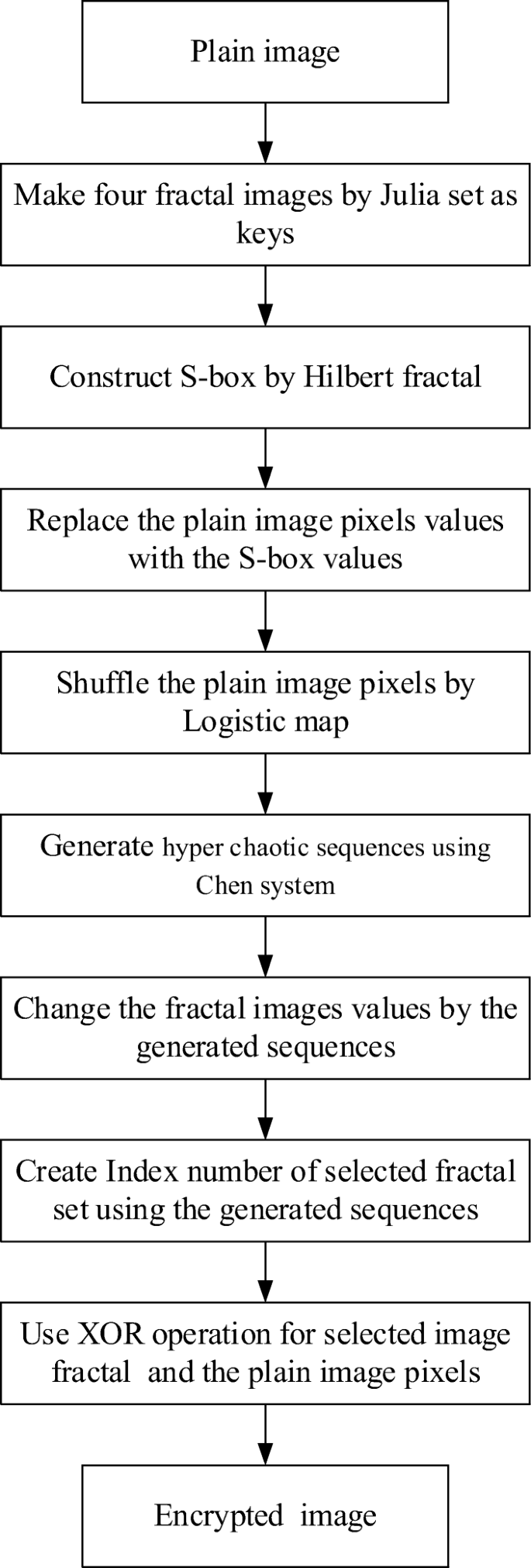
A Novel Color Image Encryption Algorithm Based On Substitution Box And Hyper Chaotic System With Fractal Keys Springerlink
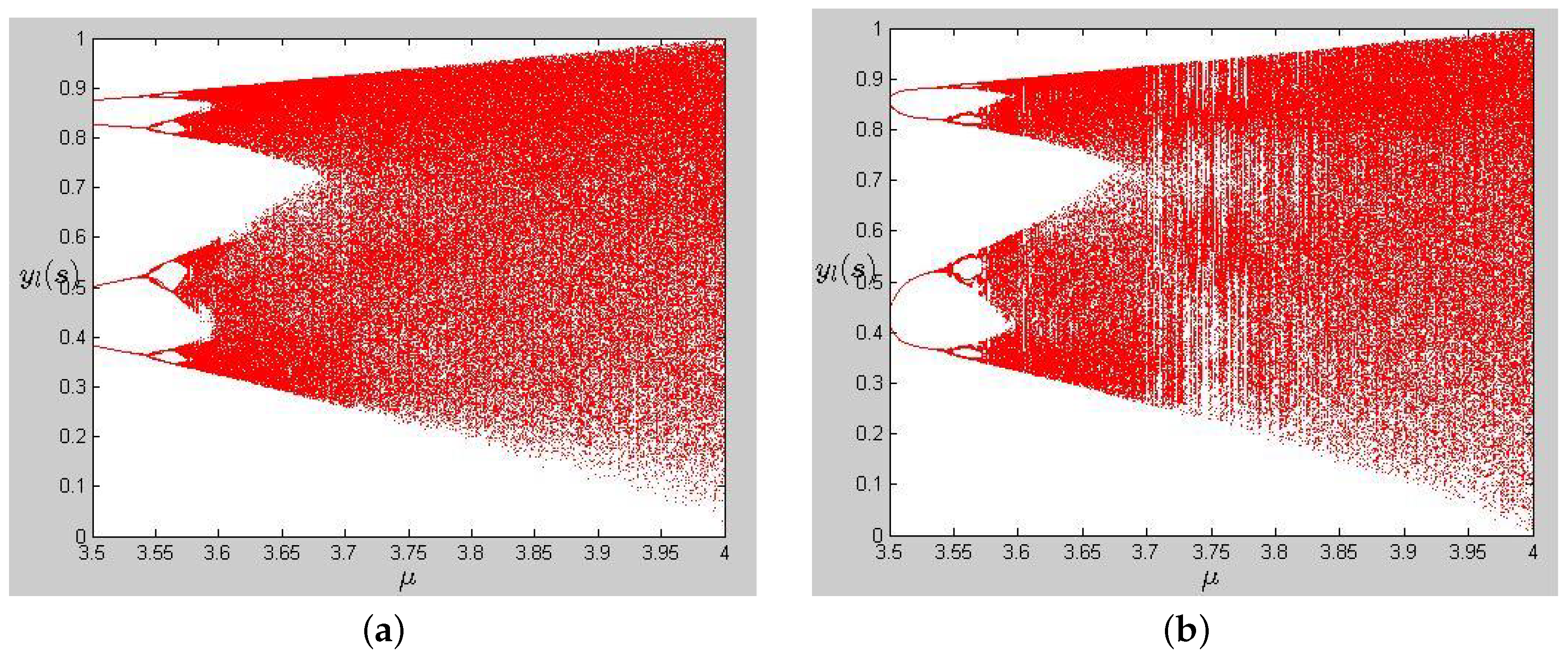
Applied Sciences Free Full Text A Novel Method For Constructing The S Box Based On Spatiotemporal Chaotic Dynamics Html

Ppt Chapter 2 Conventional Single Key Cryptography Ece 6612 Powerpoint Presentation Id

Partition Based Trapdoor Ciphers Intechopen

The Data Encryption Standard Block Ciphers Coursera

Pdf Analysis Of Development Of Dynamic S Box Generation
Http Www Uobabylon Edu Iq Eprints Publication 2 6033 Pdf

9 3 The Des S Boxes P Box And Initial Permutation Ip Computer Security And Cryptography Book
Q Tbn And9gcq8ba71mfxmxdnrevhcr0yylwgydur4unvcfsy6l Lto35m0n3p Usqp Cau

Ppt Infromation Security Powerpoint Presentation Free Download Id
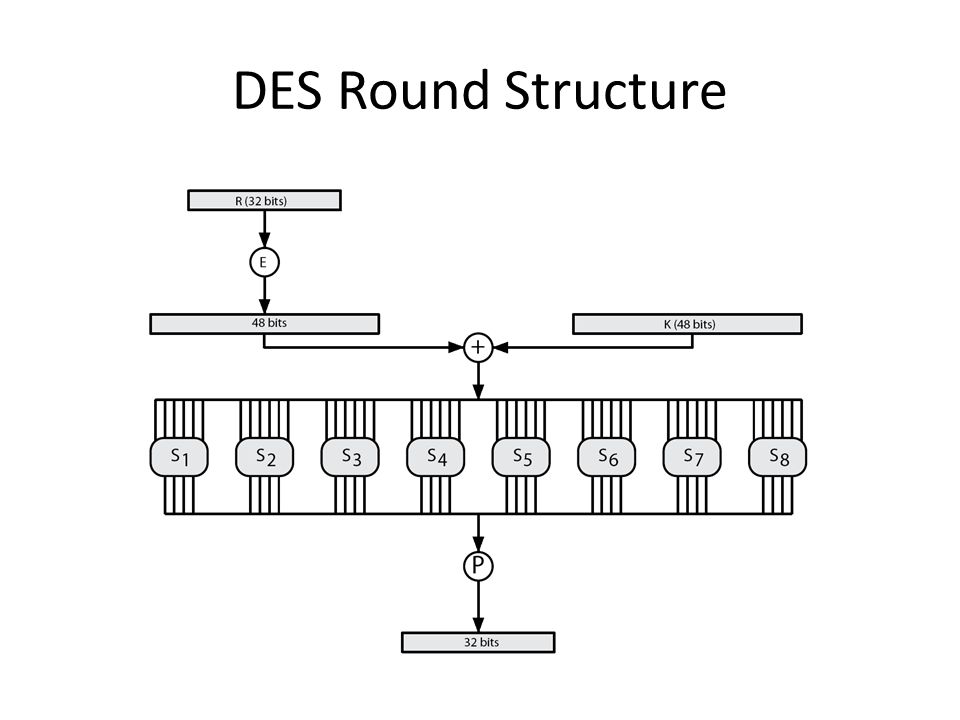
Cryptography And Network Security Chapter 3 Chapter 3 Block Ciphers And The Data Encryption Standard All The Afternoon Mungo Had Been Working On Stern S Ppt Download

A Simple Yet Efficient S Box Method Based On Chaotic Sine Map Sciencedirect
A Highly Nonlinear S Box Based On A Fractional Linear Transformation Springerplus Full Text

Generation Of Dynamical S Boxes For Block Ciphers Via Extended Logistic Map
Q Tbn And9gct0abdt09pq1t3tk4maupgmxojjcotjx41l5h7t410 Usqp Cau
Www Mdpi Com 1099 4300 21 3 245 Pdf
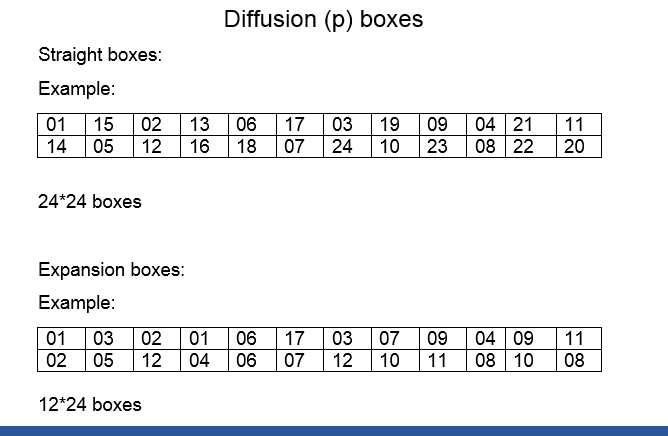
Data Encryption Standard
Q Tbn And9gcqapowi2tt9xae7n8ibd3tbzbujci5pfuypknu9 Xztuxe9cuie Usqp Cau

Cs 4 Sd Section By Dr Daniyal Alghazzawi 3 Information Security Ppt Download
A Highly Nonlinear S Box Based On A Fractional Linear Transformation Springerplus Full Text
Www Tandfonline Com Doi Pdf 10 1080 18
Http Www Uobabylon Edu Iq Eprints Publication 2 6033 Pdf
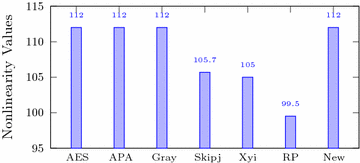
8 Data Encryption Standard

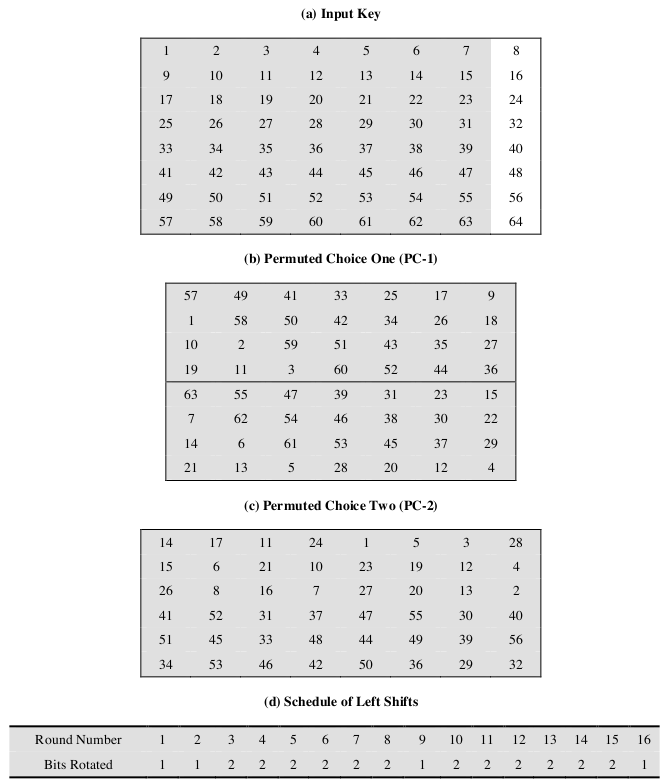
9 3 The Des S Boxes P Box And Initial Permutation Ip Computer Security And Cryptography Book
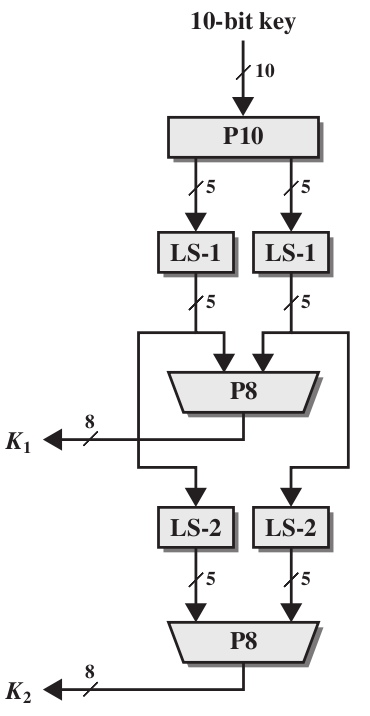
8 Data Encryption Standard

Permutation Box Wikipedia

Pdf Study Of S Box Properties In Block Cipher



