S Box Aes

Table 2 From Key Dependent S Box Generation In Aes Block Cipher System Semantic Scholar

Pdf An Improved Aes S Box And Its Performance Analysis Semantic Scholar
Q Tbn And9gctsubxpavkf Nfamtihh4u1aeeo0afwzvhy0ol7iptkxhwjp3lm Usqp Cau
Www Atlantis Press Com Article Pdf

Pdf Dynamic Aes 128 With Key Dependent S Box Semantic Scholar

Achieving High Performance For Advanced Encryption Standard Aes Applications
An example of a nonlinear transformation algorithm is Advanced Encryption Standard (AES) In this Rijndael algorithm, sbox is the most important part because of the encryption algorithm which means that it requires the key to be the same length as the message to be encoded.
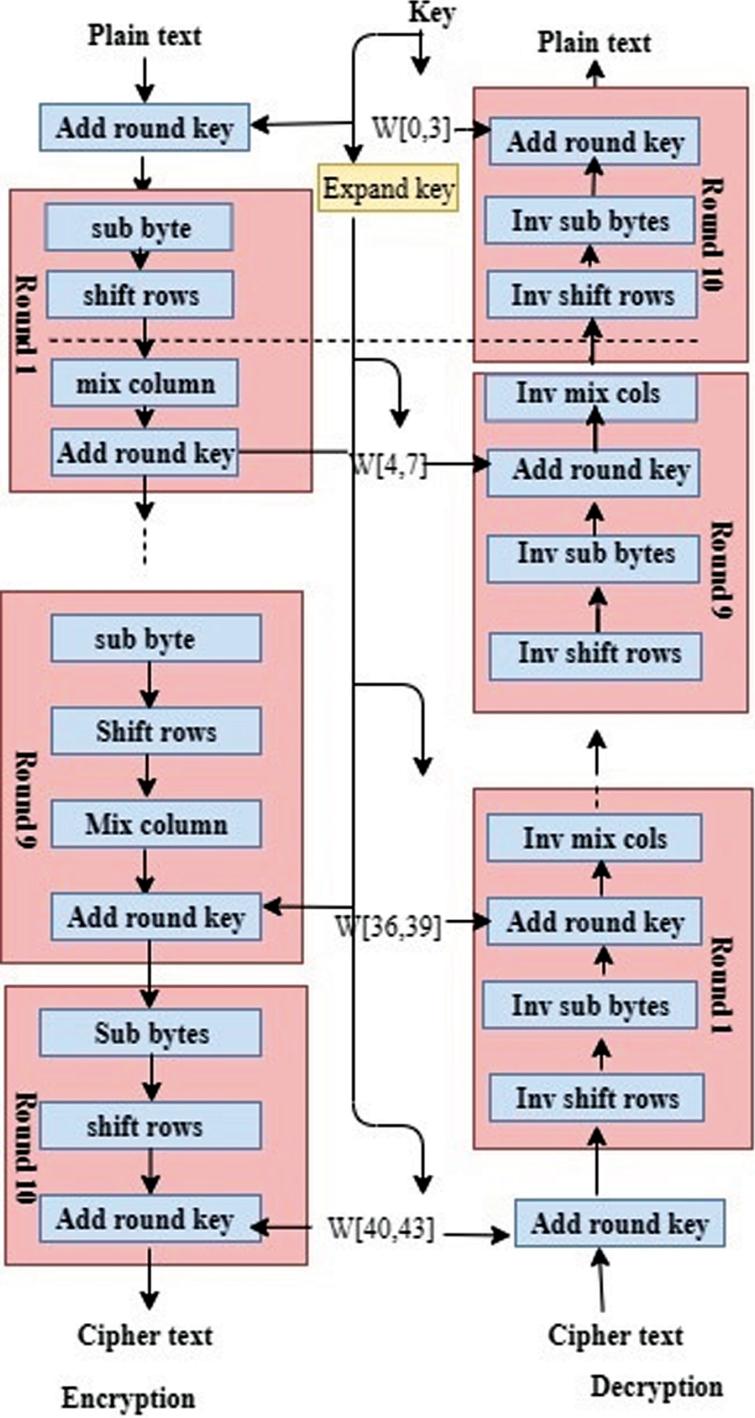
S box aes. AES Example Round 1, Substitution Bytes current State Matrix is 0 B B @ 00 3C6E 47 1F 4E 22 74 0E 08 1B 31 54 59 0B1A 1 C C A substitute each entry (byte) of current state matrix by corresponding entry in AES SBox for instance byte 6E is substituted by entry of SBox in row 6 and column E, ie, by 9F this leads to new State Matrix 0 B B. The result, when applied to the AES Sbox, is a circuit with depth 16 and only 128 gates For the inverse, it is also depth 16 and has only 127 gates There is a shared middle part, common to both the Sbox and its inverse, consisting of 63 gates. The Sbox is consistent with the one of known standards AES and GOST R We provide the findings of an avalancheeffect investigation and statistical properties of cipher texts The algorithm actually meets the avalancheeffect criterion even after the first round.
SBox is the important component of AES The eight byte input is substituted by eight byte output using SBox during SubByte transformation The proposed system compares AES encryption with two different SBoxes Sbox with 256 byte lookup table (Rijndael SBox) and AES with 16 byte SBox (Anubis SBox) 2. The Rijndael Sbox is a substitution box (lookup table) used in the Rijndael cipher, which the Advanced Encryption Standard (AES) cryptographic algorithm is based on. Abstract— To design a substitution box (SBOX) using both encryption and decryption From that, the proposed system can achieve a higher throughput and higher energy efficiency The SBOX is designed by using Advanced Encryption Standard (AES) The.
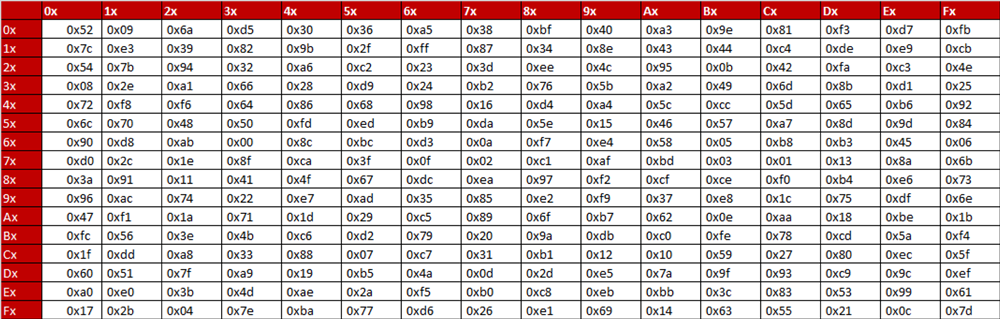
Simplified AES 16bit block 16bit key 4 x 4 Sbox Field 16 Modulus XX4 1 2 rounds SPN Musa, A, Schaefer, E, and Wedig, S 10 A Simplified AES. The AES SBox is shown in the Table below To read this Table, the byte input is broken into two 4bit halves The first half determines the row and the second half determines the column For example, the SBox transformation of 35 or 0x23 can be found in the cell at the intersection of the row labeled and the column labeled 03. In AES, the standard SBox is usually generated by using a particular irreducible polynomial {11B} in GF(2 8) as the modulus, with a particular additive constant {63}In this paper, it has been shown that, by maintaining the criteria defined by Rijndael, other moduli and constants can also be used to generate different unknown SBoxes, thus preventing linear and differential cryptanalysis.
In cryptography, an SBox (Substitutionbox) is a basic component of symmetric key algorithms which performs substitution In block ciphers, they are typically used to obscure the relationship between the key and the ciphertext Shannon's property of confusion In many cases, the SBoxes are carefully chosen to resist cryptanalysis In general, an SBox takes some number of input bits, m, and. The Advanced Encryption Standard (AES) is designed to achieve good resistance against the differential and linear cryptanalysis This includes the selection of the SBox and linear components such as the MixColumns matrix For the AES, the branch number of its MixColumns matrix is chosen as five then it ensures that any four continuous rounds of differential (linear) characteristics. The actual SBox operation is a complicated process, but just know that it’s nearly impossible to decipher with conventional computing Coupled with the rest of AES operations, it will do its job to effectively scramble and obfuscate the source data The “S” in the white box in the image above represents the complex lookup table for the S.
I mean, I can use a table to find the inverse, but how do I verify that it is indeed the inverse?. Rijndael's Sbox is a frequently used operation in AES encryption and decryption It is typically implemented as a 256byte lookup table That's fast, but means you need to enumerate a 256byte lookup table in your code I bet someone in this crowd could do it with less code, given the underlying mathematical structure. The AES SBox is shown in the Table below To read this Table, the byte input is broken into two 4bit halves The first half determines the row and the second half determines the column For example, the SBox transformation of 35 or 0x23 can be found in the cell at the intersection of the row labeled and the column labeled 03.
The AES SBox is shown in the Table below To read this Table, the byte input is broken into two 4bit halves The first half determines the row and the second half determines the column For example, the SBox transformation of 35 or 0x23 can be found in the cell at the intersection of the row labeled and the column labeled 03. AES Sbox AES Sbox implementation based on the approach by D Canright 1 The present design implements the Sbox of the Advanced Encryption Standard (AES) Since the overall AES structure is based on a byteoriented design, also the Sbox hast been implemented such that a single byte can be substituted. Abstract— To design a substitution box (SBOX) using both encryption and decryption From that, the proposed system can achieve a higher throughput and higher energy efficiency The SBOX is designed by using Advanced Encryption Standard (AES) The.
Sbox is a unique nonlinear operation in Rijndael, one encryption algorithm chosen as AES, and it determines the performance of AES In this paper, the weaknesses in complexity and security of AES. Suppose I have made changes in AES by removing the nonlinear Sbox and replacing it with a linear function I know that by removing the nonlinearity of the Sbox I'm making the AES vulnerable to. I mean, I can use a table to find the inverse, but how do I verify that it is indeed the inverse?.
AES can encrypt 128 bits of plaintext DES can encrypt 64 bits of plaintext AES cipher is derived from square cipher DES cipher is derived from Lucifer cipher AES was designed by Vincent Rijmen and Joan Daemen DES was designed by IBM No known cryptanalytical attacks against AES but side channel attacks against AES implementations possible. AES SBox Verification Ask Question Asked today Active today Viewed 2 times 0 $\begingroup$ How can I verify that if the SBox input is the byte 93 (expressed in hex), then the SBox output is DC?. Rijndael's Sbox is a frequently used operation in AES encryption and decryption It is typically implemented as a 256byte lookup table That's fast, but means you need to enumerate a 256byte lookup table in your code I bet someone in this crowd could do it with less code, given the underlying mathematical structure.
The Rijndael SBox was specifically designed to be resistant to linear and differential cryptanalysis This was done by minimizing the correlation between linear transformations of input/output bits, and at the same time minimizing the difference propagation probability. 1 Name of Standard Advanced Encryption Standard (AES) (FIPS PUB 197) 2 Category of Standard Computer Security Standard, Cryptography 3 Explanation The Advanced Encryption Standard (AES) specifies a FIPSapproved cryptographic algorithm that can be used to protect electronic data The AES algorithm is a. AES SBox Verification Ask Question Asked today Active today Viewed 2 times 0 $\begingroup$ How can I verify that if the SBox input is the byte 93 (expressed in hex), then the SBox output is DC?.
Sbox is a unique nonlinear operation in Rijndael, one encryption algorithm chosen as AES, and it determines the performance of AES In this paper, the weaknesses in complexity and security of AES. 1 Name of Standard Advanced Encryption Standard (AES) (FIPS PUB 197) 2 Category of Standard Computer Security Standard, Cryptography 3 Explanation The Advanced Encryption Standard (AES) specifies a FIPSapproved cryptographic algorithm that can be used to protect electronic data The AES algorithm is a. AES Example Round 1, Substitution Bytes current State Matrix is 0 B B @ 00 3C6E 47 1F 4E 22 74 0E 08 1B 31 54 59 0B1A 1 C C A substitute each entry (byte) of current state matrix by corresponding entry in AES SBox for instance byte 6E is substituted by entry of SBox in row 6 and column E, ie, by 9F this leads to new State Matrix 0 B B.
SBOX ™TWO WAYS TO INSTALL SBox ™ ‘popup’ units can be fitted either below the worksurface on a rebate, with their own custom top for a camouflaged installation, or simply dropped into a hole in the Counter, using the steel top provided Installation is either a CHAMELEON FIT or a SURFACE FIT based on the installation desired Units are supplied to 60 Countries in the following. Single pipeline AES 128 bit encryption using Sbox as Look up table aneels3/AES128. In the Substitute bytes step, we use SBOX to substitute data Simply put we can see SBOX as lookup table The way to substitute bytes for block is like this each block have 8bit data, and we can see first 4bit as row index and the last 4bit as column index, with these row, column index we can take the value from the SBOX Shift rows.
Now, the AES algorithm substitutes every byte with a code according to a preestablished table called the Rijndael Sbox It looks like this It looks like this According to the table, an element like 19 becomes d4, e9 becomes 1a, and so on. AES Most compact Sbox Canright Reduce the number of gates in Canright to 115 Boyar and Peralta Most efficient Sbox Ueno Boyar, Find and Peraltaet al Reduce the depth of Sbox to 16 gates Then to 113 CMT 1 The most compact Sbox to date 2 The most efficient Sbox to date In this paper, we propose First Imp using Tower Fields Satoh et al. Abstract A key step in the Advanced Encryption Standard (AES) algorithm is the “Sbox” Many implementations of AES have been proposed, for various goals, that effect the Sbox in various ways In particular, the most compact implementations to date of Satoh et al1 and Mentens et al2 perform the 8bit Galois field inversion of.
AES can encrypt 128 bits of plaintext DES can encrypt 64 bits of plaintext AES cipher is derived from square cipher DES cipher is derived from Lucifer cipher AES was designed by Vincent Rijmen and Joan Daemen DES was designed by IBM No known cryptanalytical attacks against AES but side channel attacks against AES implementations possible. AESTBOX Advanced Encryption Standard (AES) implementation using tboxes for faster computation Rust Implementation You find a Rust implementation in the directory with the same name in the aes_tbox subdirectory Change to the directory and run the following command to build and run AESTBOX # Build & Run cargo run. The Advanced Encryption Standard (AES) is designed to achieve good resistance against the differential and linear cryptanalysis This includes the selection of the SBox and linear components such as the MixColumns matrix For the AES, the branch number of its MixColumns matrix is chosen as five then it ensures that any four continuous rounds of differential (linear) characteristics.
This is just small explanation about the Sbox used by the AES cryptographic algorithm The Sbox is generated by determining the multiplicative inverse for a given number in Rijndael's Galois Field The multiplicative inverse is then transformed using the following affine transformation matrix 1 0 0 0 1 1 1 1 1 1 0 0 0 1 1 1. The analytical validation of the combined Sbox and InvSbox for AES is accoutrement and verified using the Spartan 6 (xc6slx2tqg144) FPGA board using Verilog HDL in Xilinx 146 tool The proposed module is initiated and implemented in the main module as combined implementation of sbox and. Advanced Encryption Standard (AES) is a block cipher system which widely used in cryptographic application Substitution box (Sbox), nonlinear substitution operation, is the main factor of the.
AESやCamelliaではそれを線形変換したものが採用されており、差分確率及び線形確率は、 26 である。 近年では、実装サイズの縮小を目的に小さいSBoxを複数組み合わせて大きなSBoxを構成する方法がとられることがある。. AES Sbox was specifically designed to be resistant to linear and differential cryptanalysis This was done by minimizing the correlation between linear transformations of input/output bits, and at the same time minimizing the difference propagation probability.

Aes Advanced Encryption Standard Anu Vazhayil

The Advanced Encryption Standard Aes Algorithm Commonlounge

How We Can Calculate Aes Inverse Sbox Cryptography Stack Exchange
Lirias Kuleuven Be Retrieve
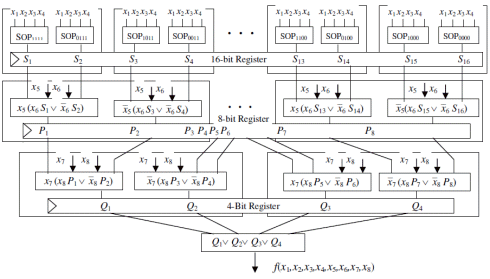
Pipeline Aes S Box Implementation Starting With Substitution Table

Inverse S Box Of Aes Algorithm Download Scientific Diagram

Advanced Encryption Standard Aes Transformation Functions

Hardware Rules And Improved S Box On Aes Scientific Net

Ppt Aes S Box How And Why Powerpoint Presentation Free To Download Id 7bc8 Odvkn

An Optimized S Box Circuit Architecture For Low Power Aes Design

Pdf An Improved Aes S Box And Its Performance Analysis Semantic Scholar

Aes S Box Input And Output Question Cryptography Stack Exchange

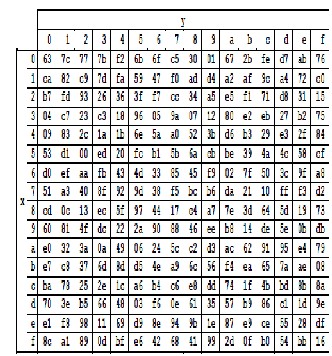
Inverse S Box Substitution Values For The Byte Xy In Hexadecimal Format Download Scientific Diagram

Symmetric Encryption And Message Confidentiality Ppt Download

Z X And S X Are The Output Of S Box Of Aes And
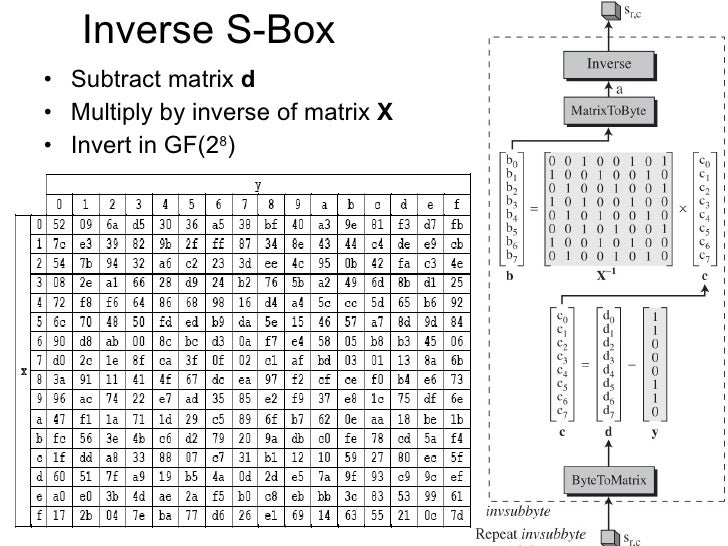
Network Security Lec4

Aes S Box Calculation Cryptography Stack Exchange
Design And Verification Of Aes Encryption With New Approach For S Box
2

Aes Advanced Encryption Standard Anu Vazhayil
Www Irjet Net Archives V2 I8 Irjet V2i811 Pdf

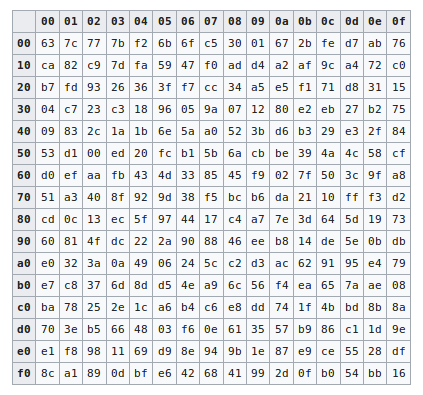
File Aes S Box Png Wikimedia Commons

Aes How To Create The S Box With Sage Cryptography Stack Exchange

New S Box Calculation For Rijndael Aes Based On An Artificial Neural Network

Aes S Box Aes S Box Hd Png Download Vhv
Www Iaeme Com Masteradmin Uploadfolder Ijecet 07 01 001 2 3 4 Ijecet 07 01 001 2 3 4 Pdf

Cryptography And Network Security Ppt Download
Http Citeseerx Ist Psu Edu Viewdoc Download Doi 10 1 1 227 7609 Rep Rep1 Type Pdf

A High Throughput Cfa Aes S Box With Error Correction Capability

Plot Of The Difference Of The S Boxes Elements Table 2 And Table 3 Download Scientific Diagram

Aria Why Have One S Box When You Can Have Two By Prof Bill Buchanan Obe Asecuritysite When Bob Met Alice Medium

Z X And S X Are The Output Of S Box Of Aes And
Number Theory And Advanced Cryptography 1 Finite Fields And Aes Ppt Video Online Download

Use Verilog To Implement The Field Multiplier For Chegg Com
Construction Of Cryptographically Secure Aes S Box Using Second Order Reversible Cellular Automata Ios Press

Dmr Based Technique For Fault Tolerant Aes S Box Architecture Deepai

Explaon Like I M Five The Rijndael S Box Crypto

Aes Inverse S Box 23 Download Scientific Diagram

Aes Cipher And Xts Non Cosmic Concentration Gradient
An Example Of The Aes S Box 4 3 Shift Rows Download Scientific Diagram
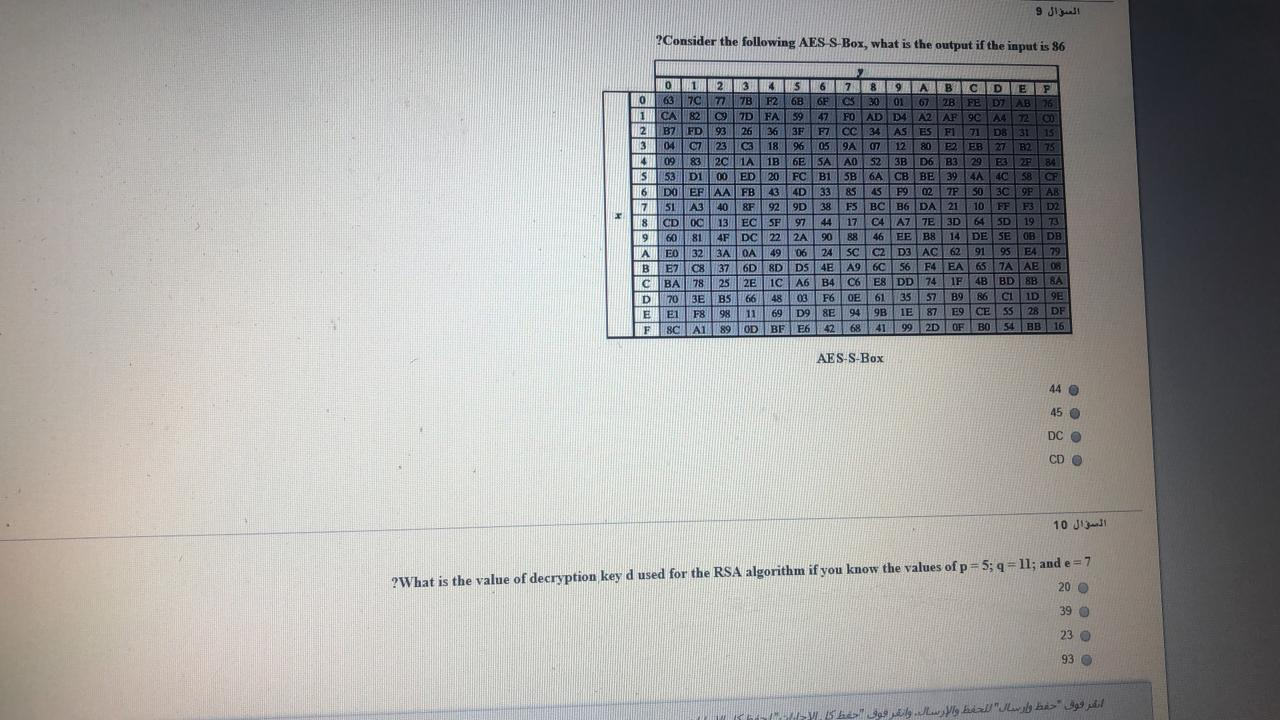
Solved السؤال 9 Consider The Following Aes S Box What Chegg Com
Http Www Ijera Com Papers Vol3 Issue1 Iw Pdf

The Advanced Encryption Standard Aes Algorithm Commonlounge
Ieeexplore Ieee Org Iel5 Pdf
Quantum Circuit Implementations Of Aes With Fewer Qubits Springerlink
2
Www Alliedjournals Com Download Data Ijems V2is Pdf

Advanced Encryption Standard Aes Transformation Functions

Consider The Following Aes S Box Used In The Bytes Chegg Com
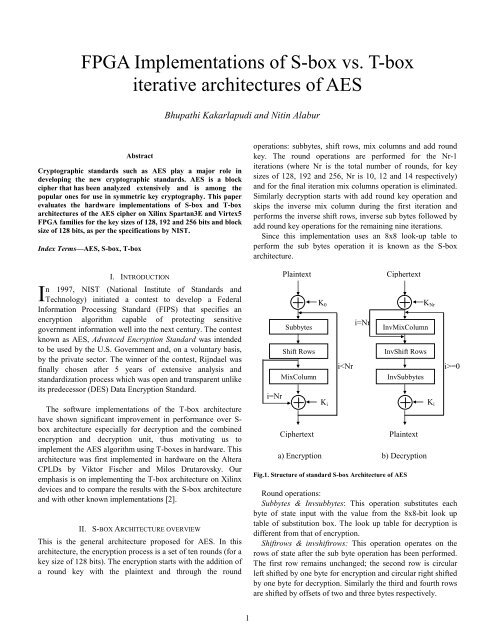
Aes T Box Report
Dl Acm Org Doi Pdf 10 1145
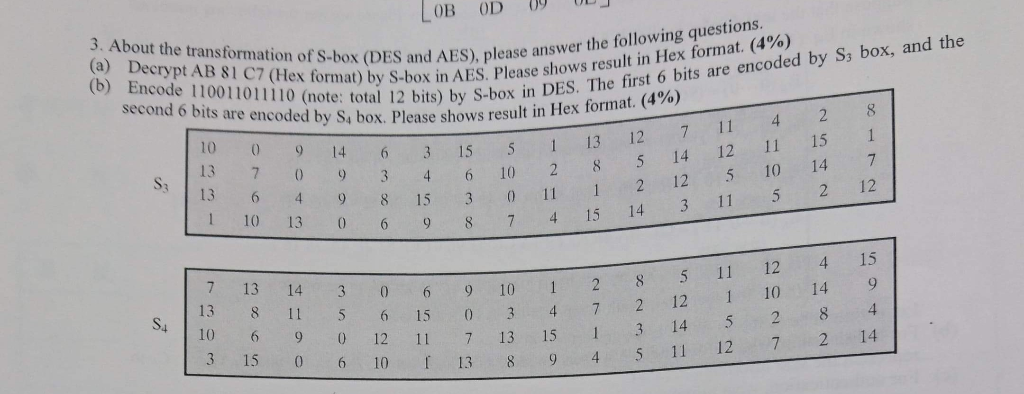
Solved 3 About The Transformation Of S Box Des And Aes Chegg Com

Pdf An Improved Aes S Box Based On Fibonacci Numbers And Prime Factor Semantic Scholar

Ch05 Testbank Crypto6e

How Are The Aes Inverse S Boxes Calculated Cryptography Stack Exchange
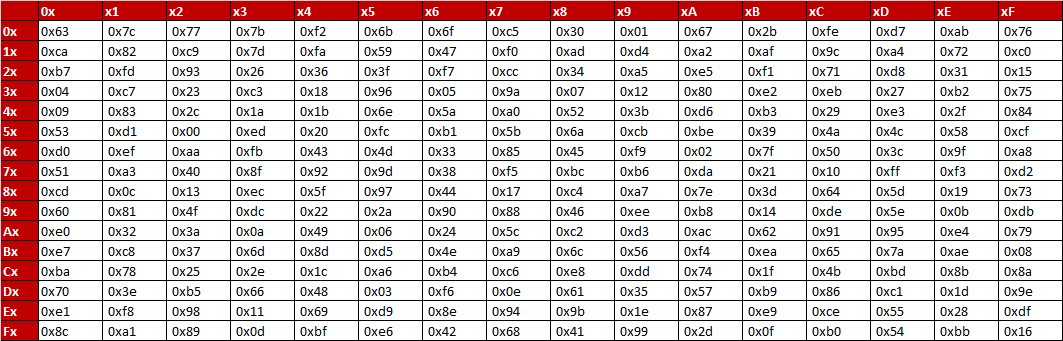
Aes Encryption

Table 2 From Encryption Using Dual Key Transformation Based On Creation Of Multi S Boxes In Aes Algorithm Semantic Scholar

Z X And S X Are The Output Of S Box Of Aes And
3

Aes Cryptocore Digilent Projects

New S Box Calculation For Rijndael Aes Based On An Artificial Neural Network

Implementation And Design Of Aes S Box On Fpga Pdf Free Download
Www Esat Kuleuven Be Cosic Publications Article 2575 Pdf
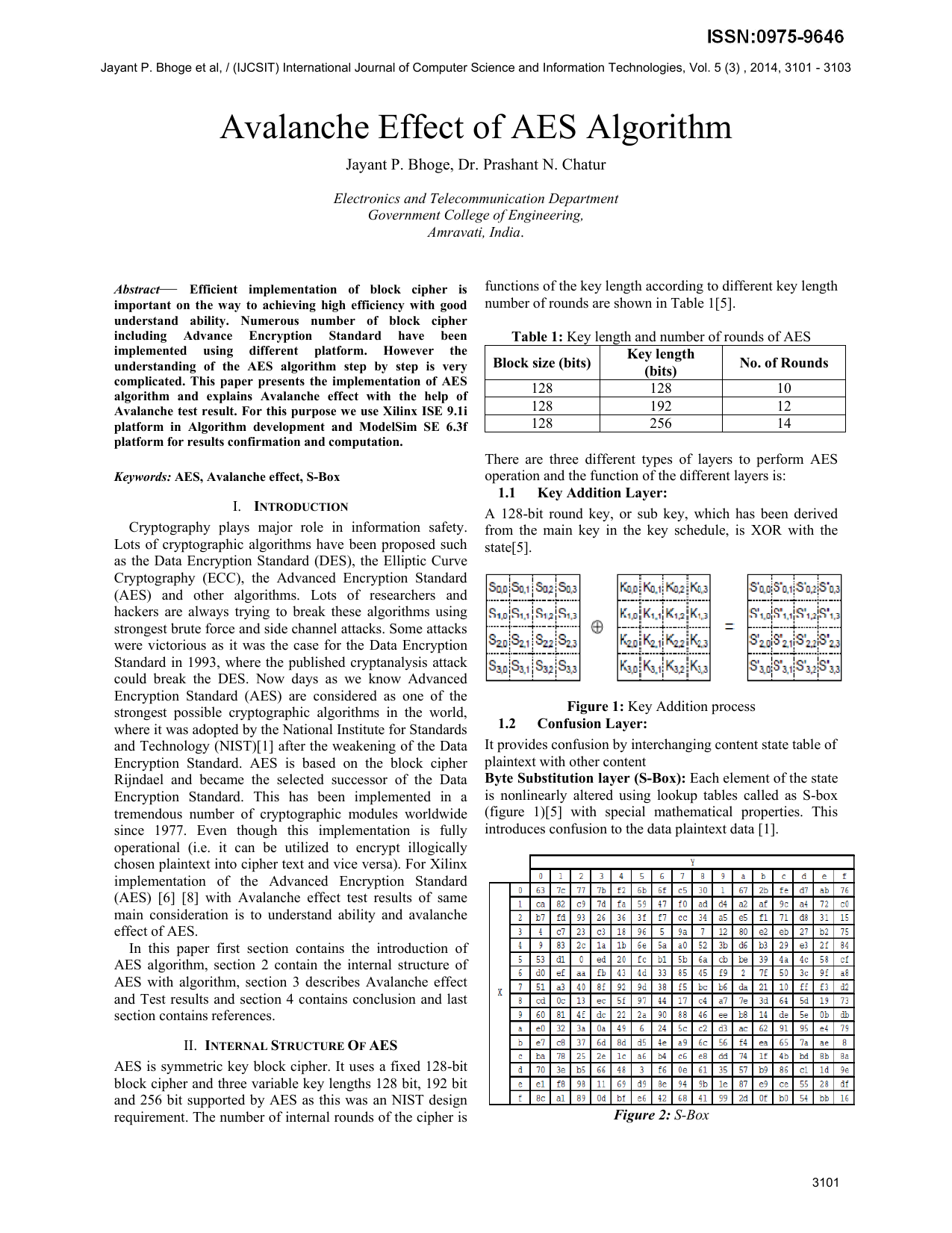
Avalanche Effect Of Aes Algorithm
3 The Core Nonlinear Part Of The Permutations In Aes Is The S Box Which Is The 8 Bit Inverse Function Let A Simplified Aes 4 Bit S Box Course Hero

Ece 5760
Q Tbn And9gcspmz4pvvldpmuymanx3og7knpoleyoqjbf050lmlijs2yhcok3 Usqp Cau
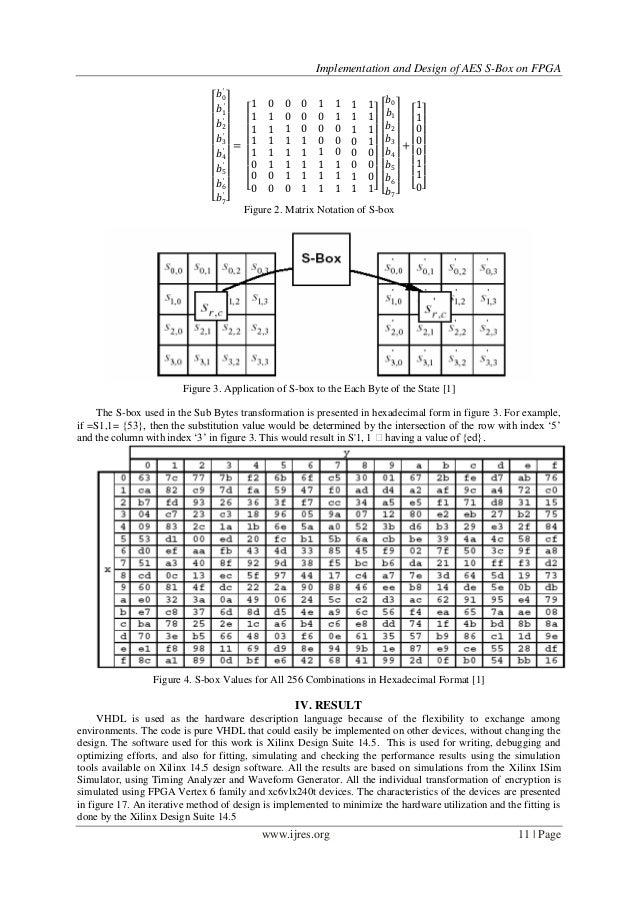
Implementation And Design Of Aes S Box On Fpga

The Rijndael S Box Youtube
Http Eprint Iacr Org 11 332 Pdf

Aria Why Have One S Box When You Can Have Two By Prof Bill Buchanan Obe Asecuritysite When Bob Met Alice Medium
A Stick Figure Guide To The Advanced Encryption Standard Aes

Secure Framework Enhancing Aes Algorithm In Cloud Computing
Section 5 2 The Aes Cipher Cryptography And Network Security 4th Edition

Quantum Circuit Implementations Of Aes With Fewer Qubits Springerlink
Http Ijarse Com Images Fullpdf J1014ijarse Pdf

New S Box Calculation For Rijndael Aes Based On An Artificial Neural Network
Http Www Redalyc Org Pdf 5122 Pdf

Pdf On The Algebraic Expression Of The Aes S Box Like S Boxes Osman Karaahmetoglu And Bora Aslan Academia Edu
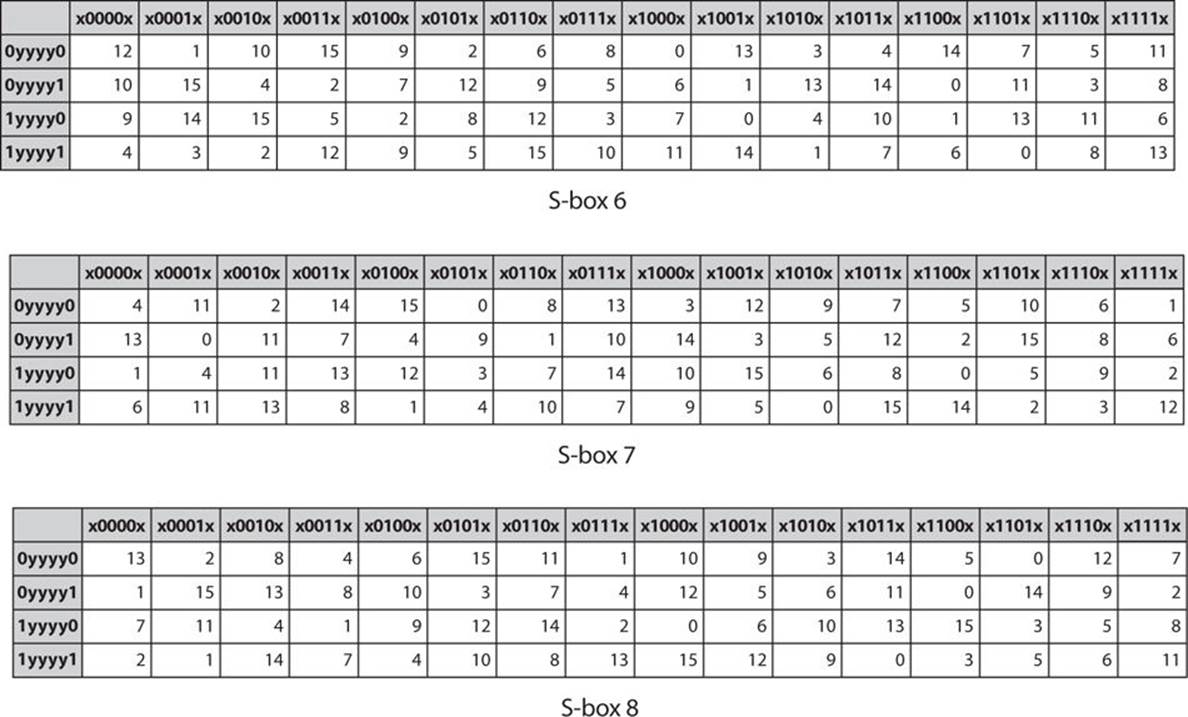
S Box Design Symmetric Ciphers And Hashes Modern Cryptography Applied Mathematics For Encryption And Informanion Security 16

Table 3 From Key Dependent S Box Generation In Aes Block Cipher System Semantic Scholar

Aes Smaller Than S Box Springerprofessional De
Www Osti Gov Servlets Purl

Sm4 Block Cipher Chinese Standard For Wapi Crypto On X86 And Arm
Q Tbn And9gcqehpldz7psfjrs7pmbsxxysg 64ocgk26e2p94atioxorqy6m8 Usqp Cau
Aip Scitation Org Doi Pdf 10 1063 1
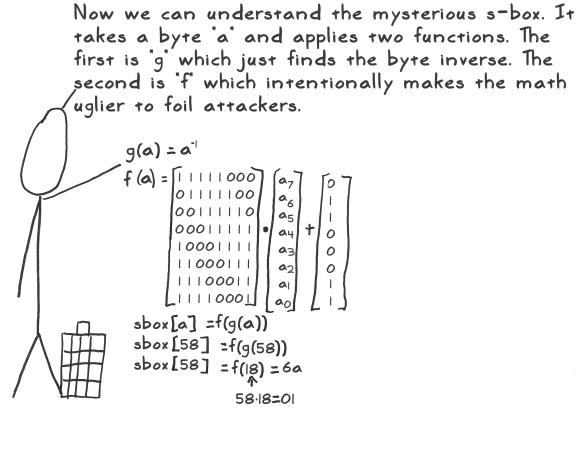
Sect Ctf 17 Bad Aes

Rijndael S Box Wikipedia
Aes Encryption

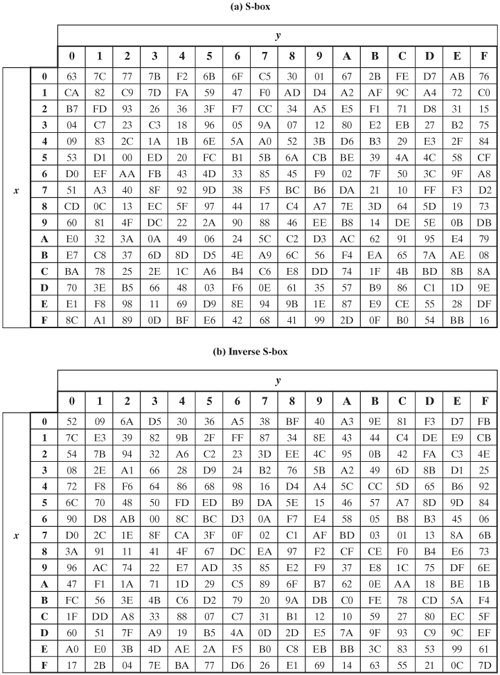
The Aes Rijndael S Box

How Are S Box Calculated In S Aes Cryptography Stack Exchange
2 S Box Of Aes Algorithm Download Scientific Diagram

Advanced Encryption Standard Aes Implementaion Using Java
Tches Iacr Org Index Php Tches Article Download 4 5

Linux Security June 15
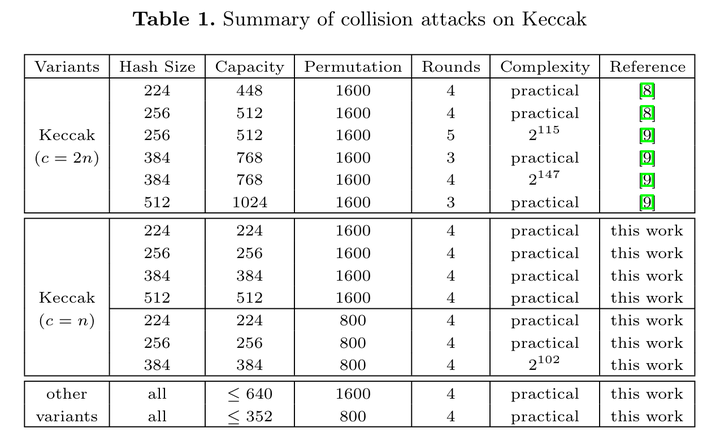
Security Of Aes With A Secret S Box Stefan Kolbl

How We Can Calculate Aes Inverse Sbox Cryptography Stack Exchange

Pdf Implementation And Design Of Aes S Box On Fpga Ijres Journal Academia Edu



