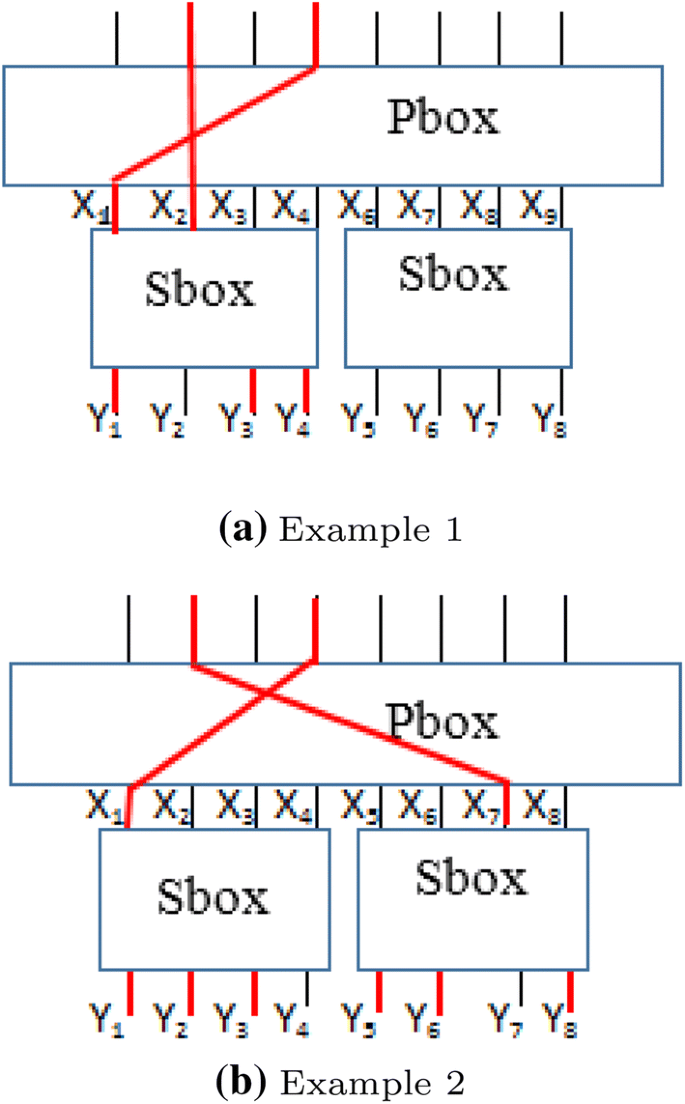
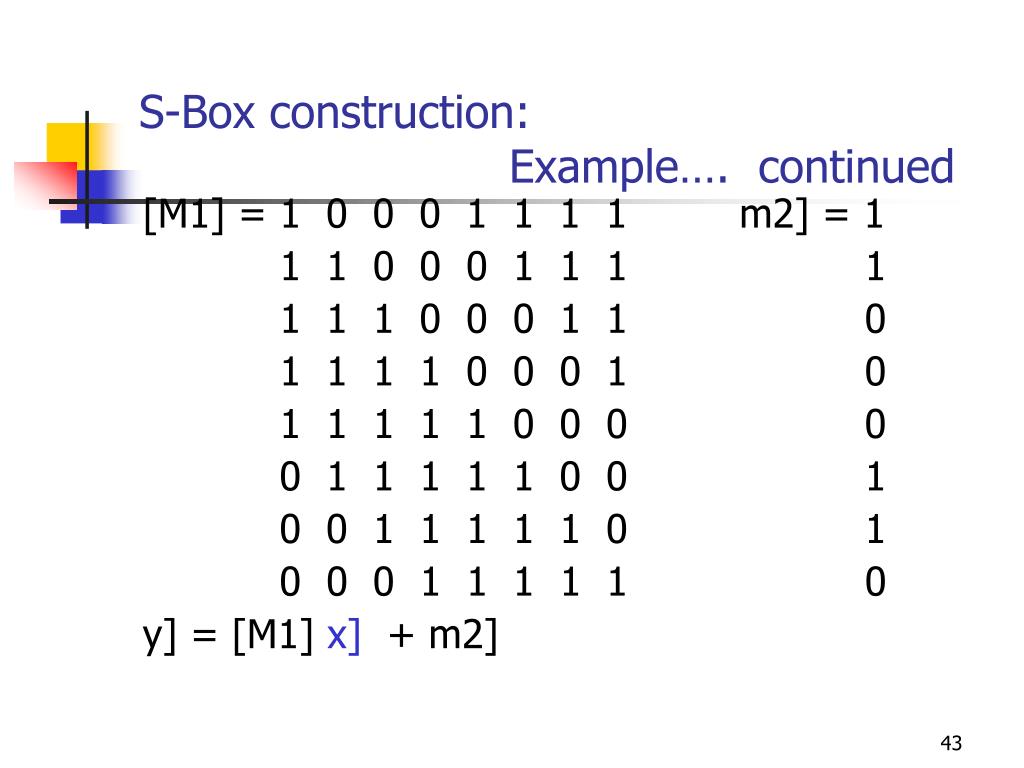
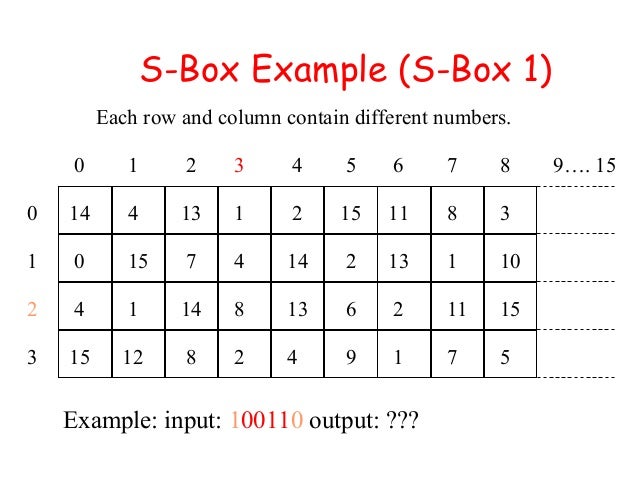
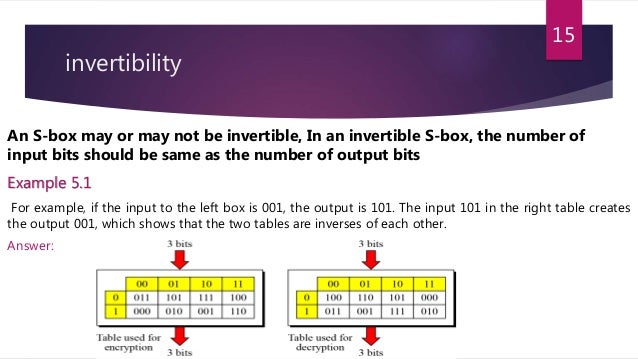
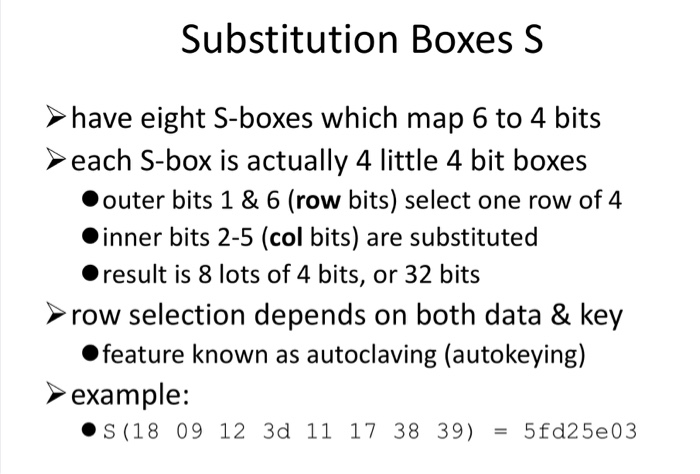
S Box Example
Towards A Real Time Image Video Cryptosystem Problems Analysis And Recommendations Springerlink
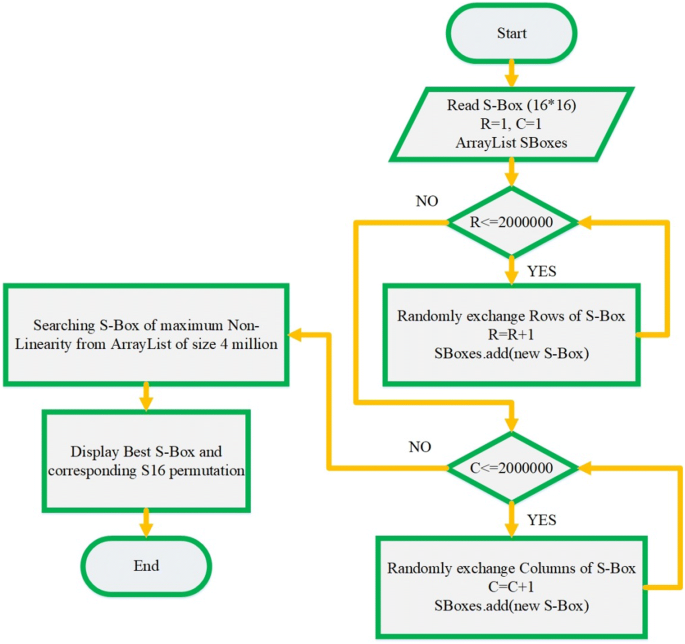
A Novel Technique To Improve Nonlinearity Of Substitution Box Without Disturbing Its Mathematical Properties Springerlink

Chapter 3 Block Ciphers And The Data Encryption Standard
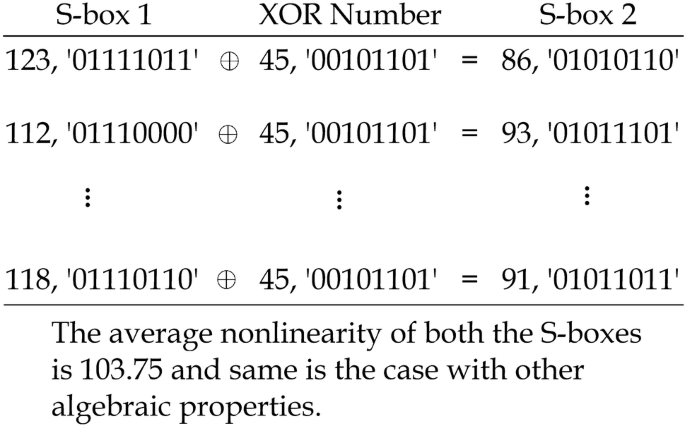
Designing Secure Substitution Boxes Based On Permutation Of Symmetric Group Springerlink
Q Tbn And9gcrpn6f Fj Zk O0r0bzusnq9xqfslpsyxlm9lvllraxndygwd9 Usqp Cau

The Advanced Encryption Standard Aes Algorithm Commonlounge
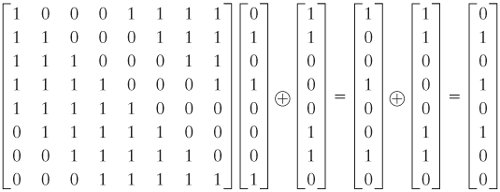
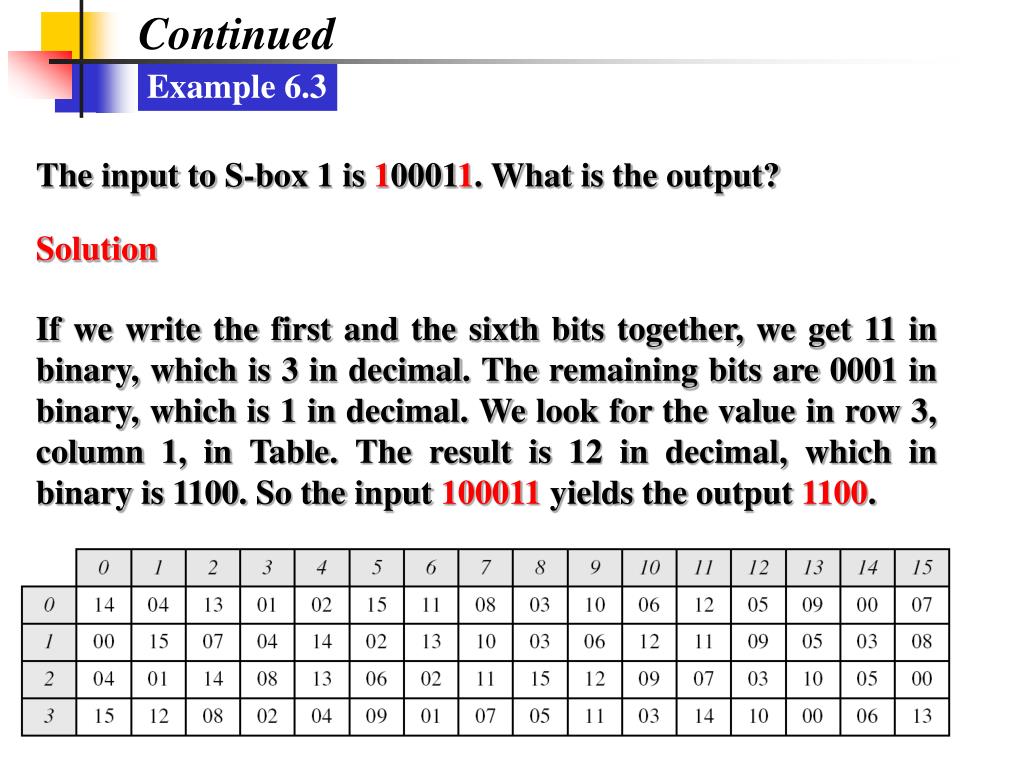
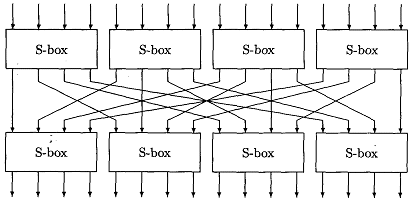
The Sbox rule is illustrated below − There are a total of eight Sbox tables The output of all eight sboxes is then combined in to 32 bit section Straight Permutation − The 32 bit output of Sboxes is then subjected to the straight permutation with rule shown in the following illustration Key Generation.

S box example. That means we lay out 0x63 = 0b as 1, 1, 0, 0, 0, 1, 1, 0 This gives us the result 0, 1, 0, 0, 0, 0, 0, 1 Reading the bits from least significant to most, this gives 0x In sum, we’ve verified that the AES Sbox takes 0x11 to 0x, as stated in the table. The SBOX may also be used as a “breakout box” for any device with a 15pin DSUB connector (DA15 or DE15), including ACOM and SPE amplifiers, the FlexRadio FLEX6000™ series, and the 4O3A Antenna Genius You can connect any pin to any of the four independent RCA connectors. A "Pandora's box" is a metaphor in our modern languages, and the proverbial phrase refers to a source of endless complications or trouble arising from a single, simple miscalculation Pandora's story comes to us from ancient Greek mythology , specifically a set of epic poems by Hesiod , called the Theogony and Works and Days.
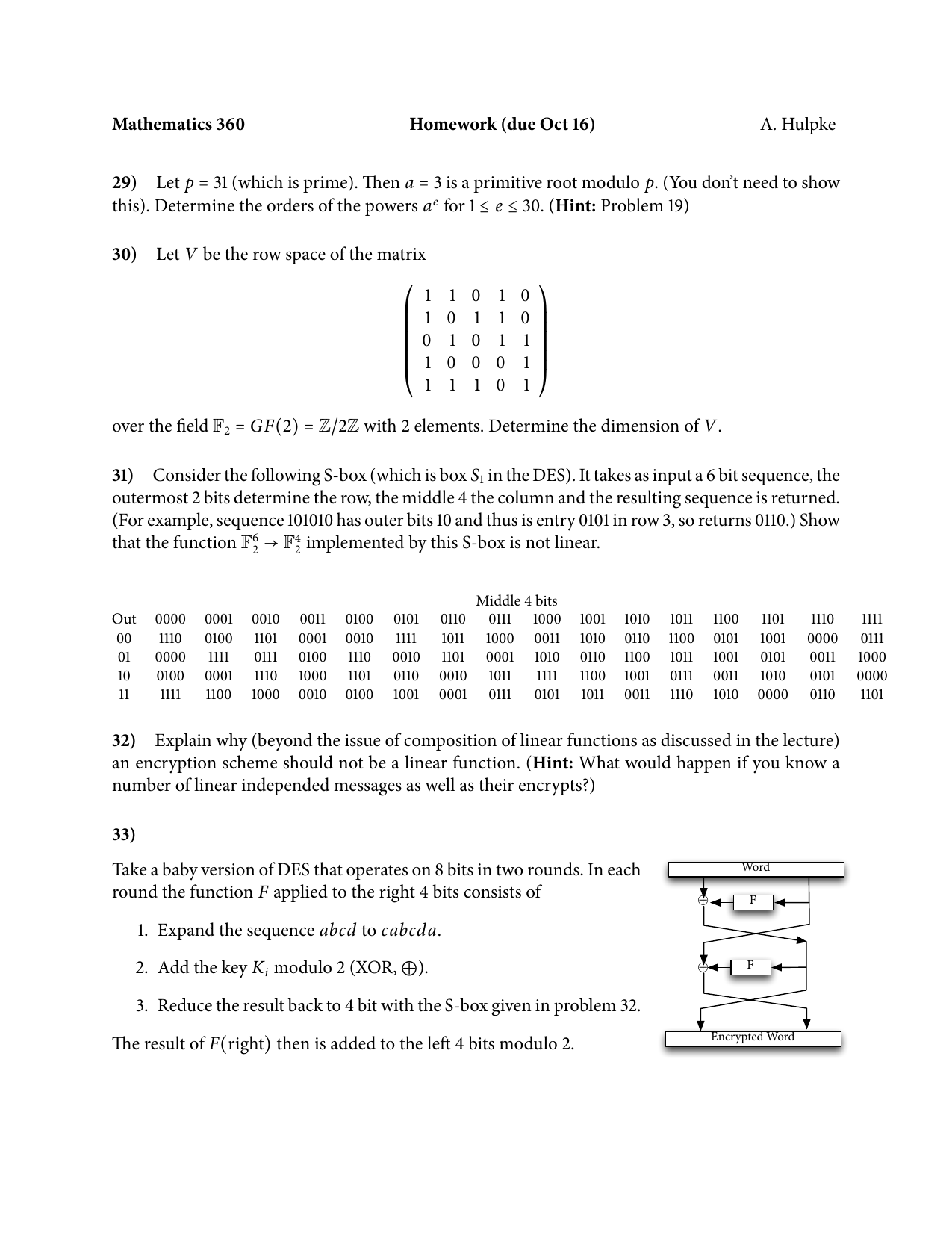
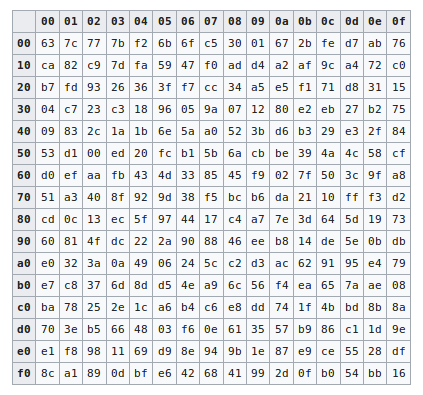
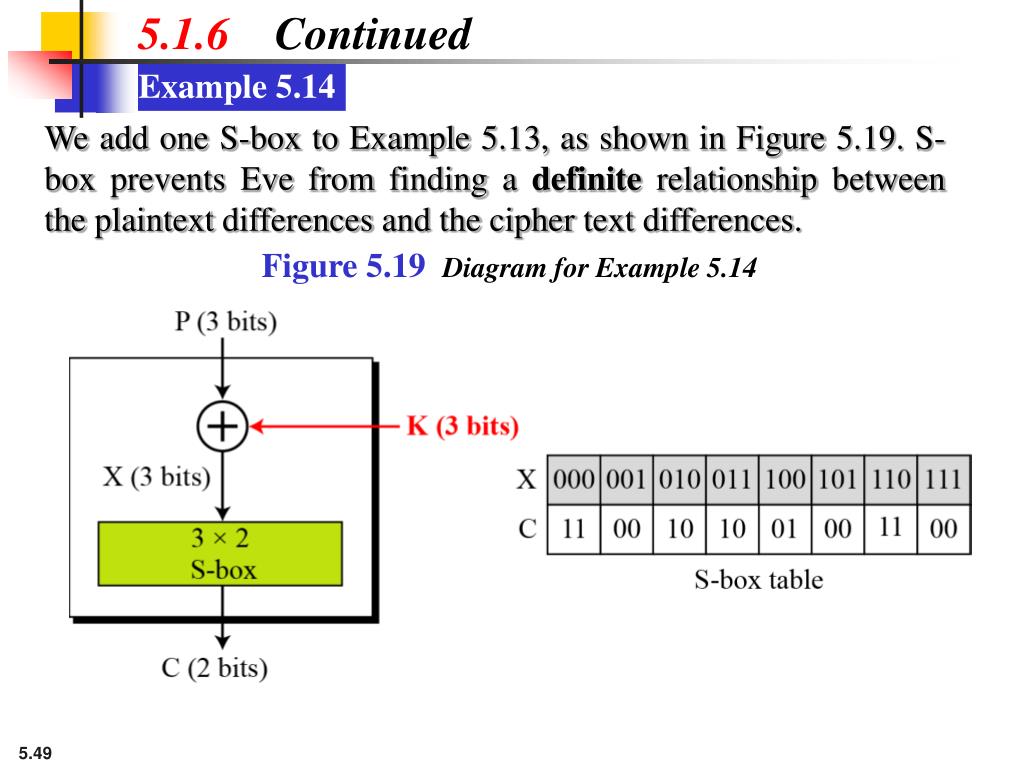
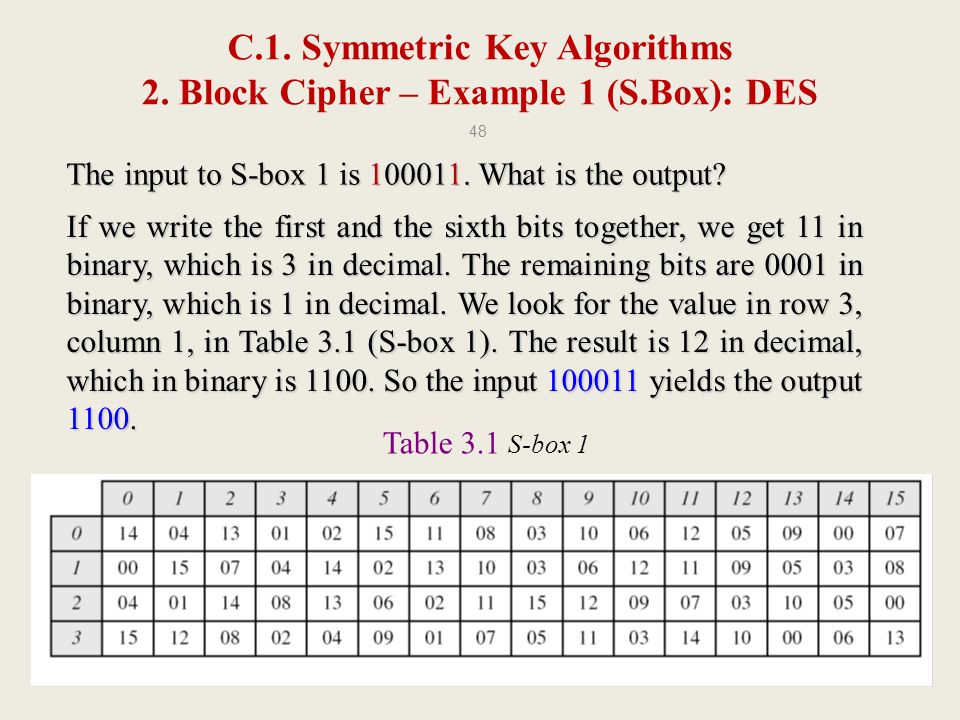
Suppose that the Sbox of Example 41 is replaced by the Sbox defined by the following substitution Tgu 0 1234 5 6 78 9 A B C D E F Tg (z) E 2 1 3 D 9 06F 4 5 A 8 C7 B Z (a) Compute the table of values ND (as defined in Definition 43) for this Sbox (b) Find a differential trail using four active Sboxes, namely, Sj, Si, S2, and Si, that has propagation ratio 27/48. Q2 Also Explain the meaning of the statement and its relevance in construction of SBox " The addition and multiplication in the equation above are being done modulo 2 (with XOR), but not in GF(16). (C) Pass left 4 bits through S0 and right four bits through S1 0 1 1 1 (D) Apply P4.
Here is an example of what my Eisenhower Box looks like for today The Difference Between Urgent and Important What is important is seldom urgent and what is urgent is seldom importantDwight Eisenhower Urgent tasks are things that you feel like you need to react to emails, phone calls, texts, news stories. The corresponding output would be "1001". Example de box 1 contentexample de box 1 contentexample dample de box 1 content example de box 1 content example de box 1 contentample de box 1 content example de box.
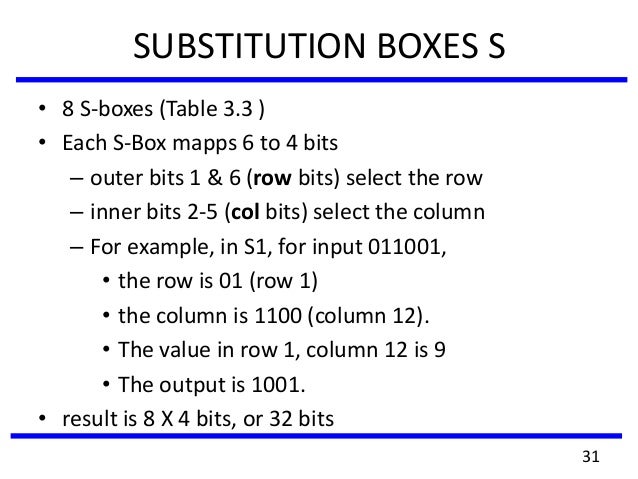
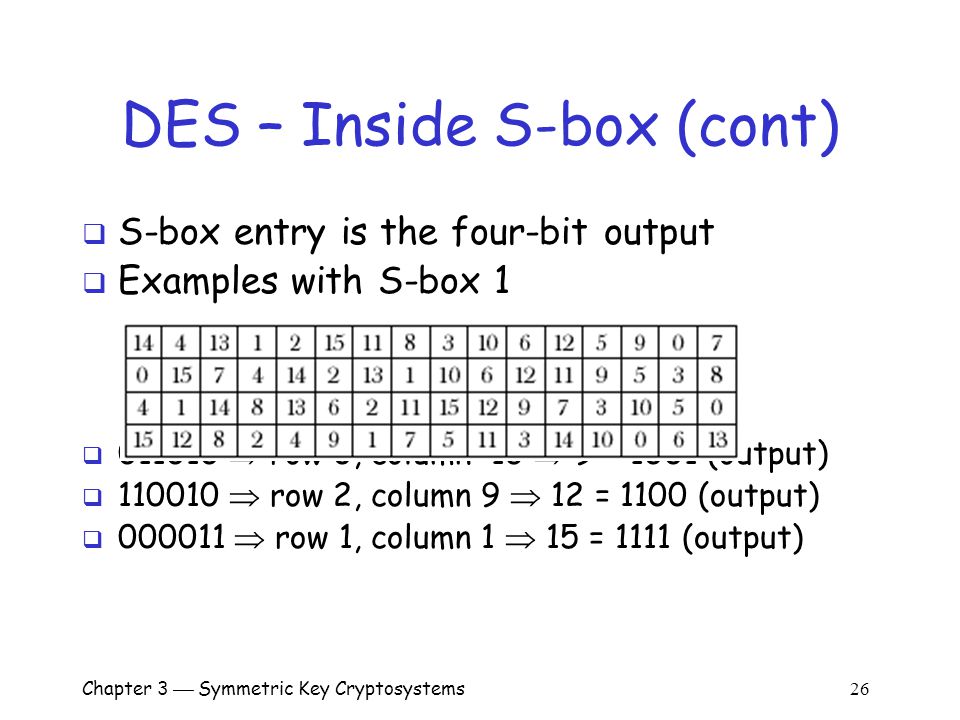
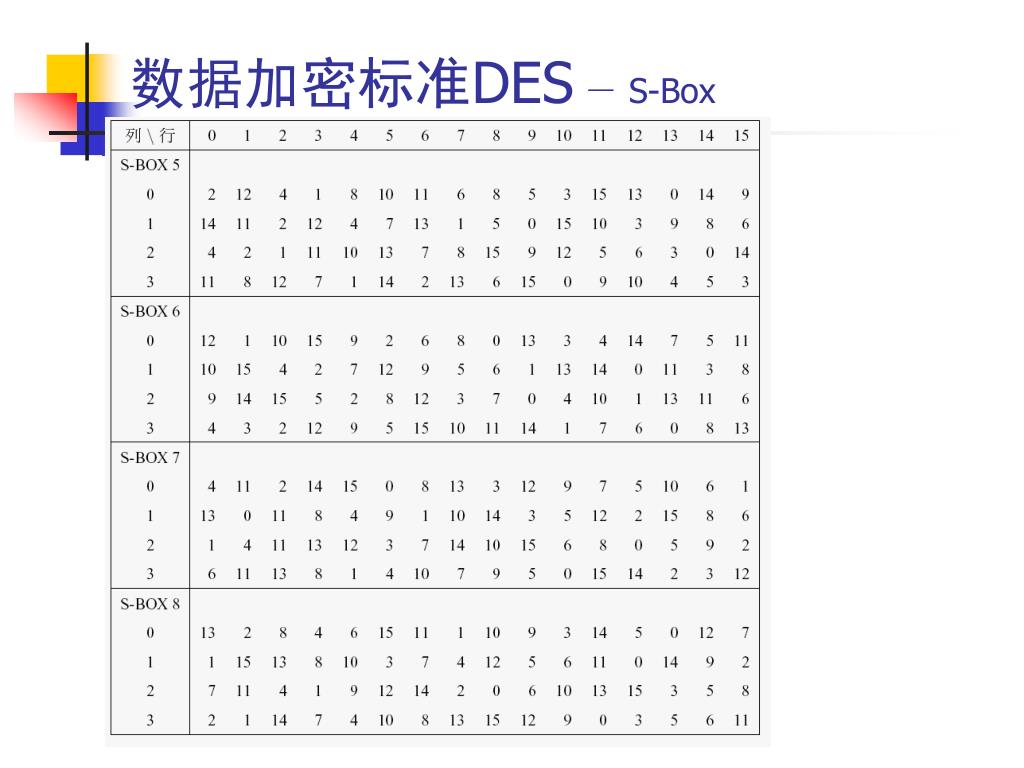
For example, against linear cryptanalysis, if an Sbox is equivalent to a linear relation such as f(x)=5x3, then if used in a Feistel round, the relationship f(y,x)=(y5x3,x) remains a linear relationship that is approximated Against differential cryptanalysis, if x' = x XOR implies f(x') =. 93 THE DES SBOXES, PBOX, AND INITIAL PERMUTATION (IP) Tables 94 to 911 specify the seven DES Sboxes, each with a 6bit input (x0, x1, Selection from Computer Security and Cryptography Book. SBox SBox SBox SBox SBox SBox SBox SBox 48bit input 32bit output Array of SBoxes Fig 67 Sboxes Sbox bit 1 bit 1 bit 2 bit 2 bit 3 bit 3 bit 4 bit 4 bit 5 bit 6 0 0123 15 1 2 3 Table entry Fig 68 Sbox rule The 48bit data from the second operation is divided into eight 6bit chunks, and each chunk is fed into a box.
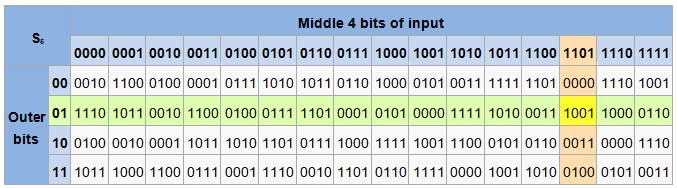
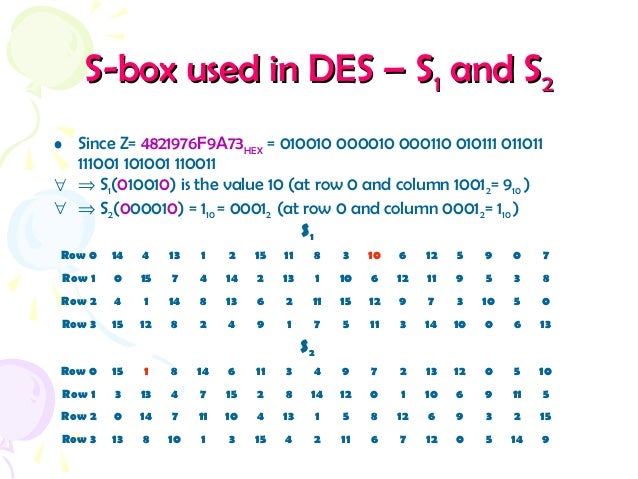
The Box component serves as a wrapper component for most of the CSS utility needs. In the example below, try changing the margin values to see how the box is pushed around due to the margin creating or removing space (if it is a negative margin) between this element and the containing element Margin collapsing A key thing to understand about margins is the concept of margin collapsing If you have two elements whose margins. One good example is this 6×4bit SBox from DES (S 5) Given a 6bit input, the 4bit output is found by selecting the row using the outer two bits (the first and last bits), and the column using the inner four bits For example, an input " 0 1101 1 " has outer bits " 01 " and inner bits "1101";.
Im getting Sbox transformation of $1010$ as $1001$ Where am i doing wrong ?. Question Suppose That The Sbox Of Example 41 Is Replaced By The Sbox Defined By The Following Substitution 8 9A B CDEF Ts (z)8 42 1 C 63D A 5 E 7 F B 90. SBox SBox SBox SBox SBox SBox SBox SBox 48bit input 32bit output Array of SBoxes Fig 67 Sboxes Sbox bit 1 bit 1 bit 2 bit 2 bit 3 bit 3 bit 4 bit 4 bit 5 bit 6 0 0123 15 1 2 3 Table entry Fig 68 Sbox rule The 48bit data from the second operation is divided into eight 6bit chunks, and each chunk is fed into a box.
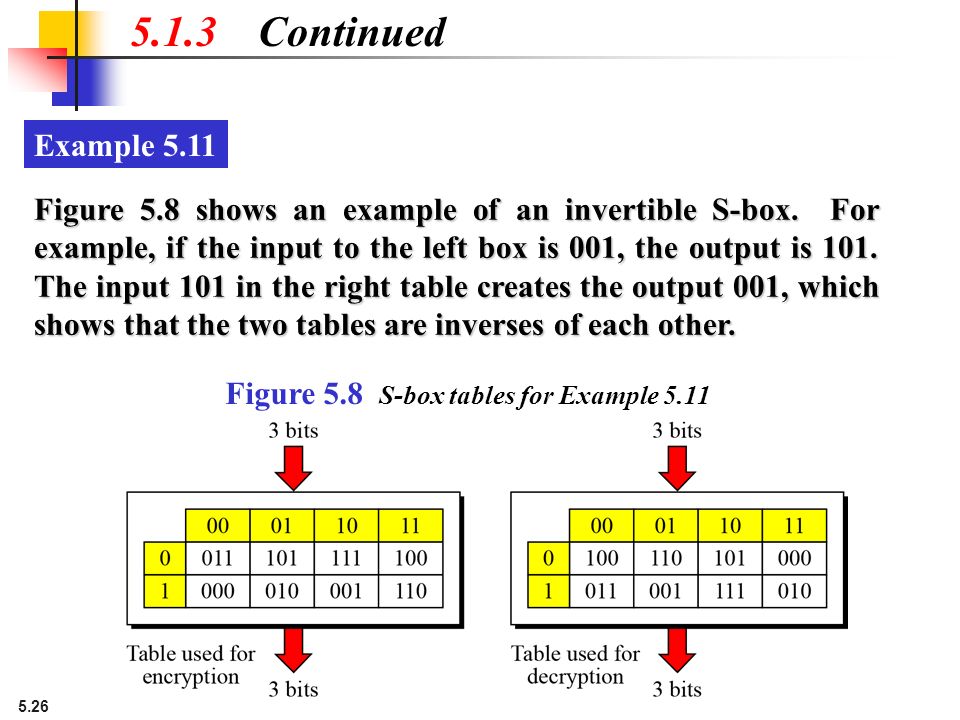
One good example of a fixed table is the Sbox from DES (S 5 ), mapping 6bit input into a 4bit output Given a 6bit input, the 4bit output is found by selecting the row using the outer two bits (the first and last bits), and the column using the inner four bits. The Sbox is generated by determining the multiplicative inverse for a given number in Rijndael's Galois Field The multiplicative inverse is then transformed using the following affine transformation matrix 1 0 0 0 1 1 1 1 1 1 0 0 0 1 1 1 1 1 1 0 0 0 1 1. The Caesar Box code is a cipher in which each letter is replaced with another letter that’s a fixed number of positions down the alphabet To decode one, start by counting the number of characters in the code Then, determine the square root of that number For example, if there are 16 characters in the code, the square root of 16 is 4.
SubstitutionBox (SBOX) is the most critical block in the Advanced Encryption Standard (AES) algorithm, consumes 75% of total power during encryption The primary idea to implement SBOX is to. Here are a couple more examples of the different shape enclosures you can build. Example 10 The facts are the same as in Example 9, except that FP is a participating FFI and provides WA with a Form W8IMY certifying that it is reporting its US accounts under chapter 4 and a withholding statement allocating 33% of the payment to a pool of US payees With respect to the US pool of payees, WA must file a Form 1042S.
Q2 Also Explain the meaning of the statement and its relevance in construction of SBox " The addition and multiplication in the equation above are being done modulo 2 (with XOR), but not in GF(16). Pandora's box is an example of a literary allusion It makes literature richer and more expressive, it allows the reader to visualize or imagine something without using many words You can just say "Open Pandora's box" which explains everything Pandora opened the box Evil came out, but also the good things came out such as hope, love. Struts 2 example A full example to create a check box via Struts 2 , and assign submitted check box value to the Action class and display it 1 Action Action class with a checkMe boolean property to hold the check box value CheckBoxActionjava.
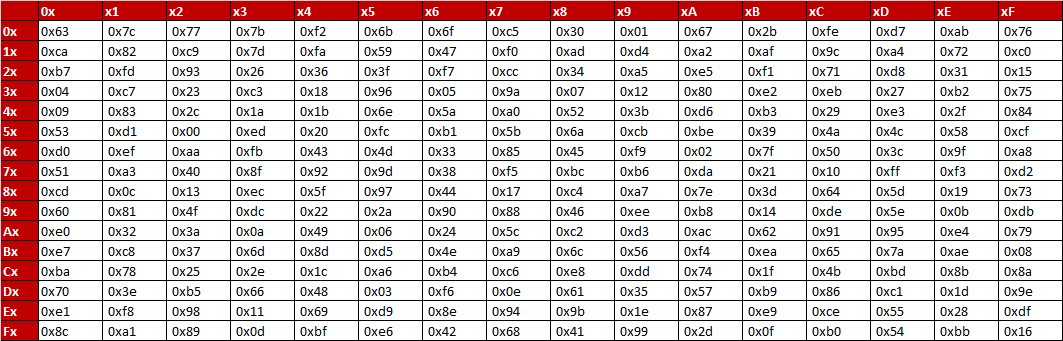
Rijndael sbox with an example in simple words Ask Question Asked 10 years ago Active 9 years, 11 months ago Viewed 3k times 2 All over google and wiki i'm not able to understand the rijndael sbox key scheduling Can anyone explain them in simple words and with an clear example????. Here the column is determined by the least significant nybble, and the row is determined by the most significant nybble For example, the value 0x9a is converted in to 0xb8 by Rijndael's Sbox The inverse Sbox is simply the Sbox run in reverse For example, the inverse Sbox of 0xdb is 0x9f The following table represents Rijndael's inverse Sbox. As in the previous example (above), we can use the SBOX or SBOXUSB to connect both an Elecraft KPA1500 Amplifier and a SteppIR antenna controller to a transceiver, with automatic frequency tracking But this example uses all four keying circuits to provide computergenerated CW and FSK keying, using two independent serial ports.
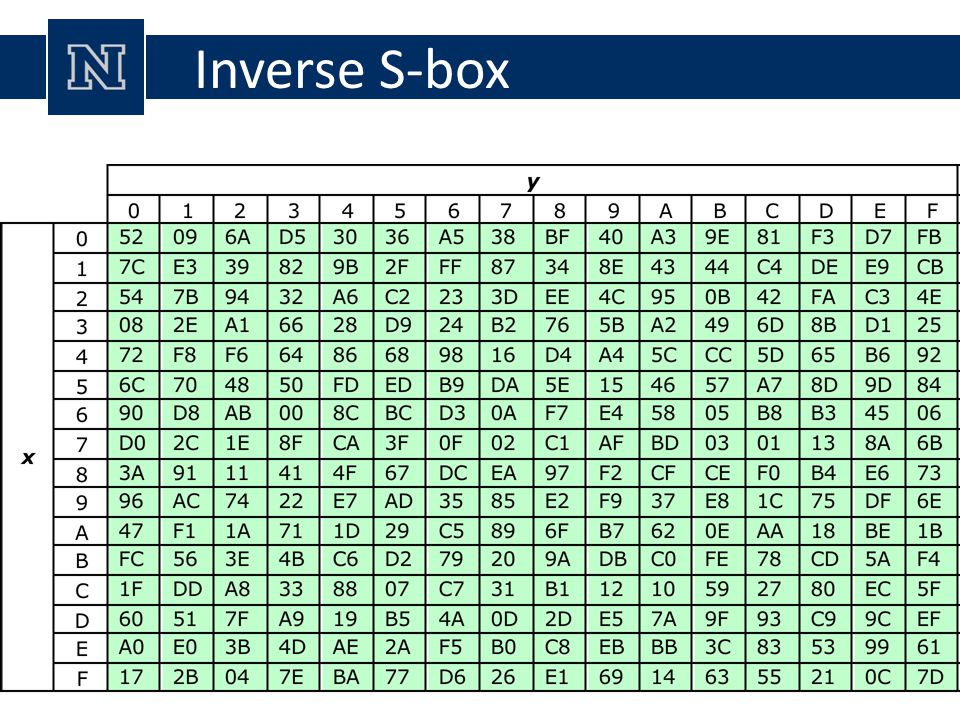
The inverse Sbox is simply the Sbox run in reverse For example, the inverse Sbox of 0xdb is 0x9f It is calculated by first calculating the inverse affine transformation of the input value, followed by the multiplicative inverse The inverse affine transformation is as follows. 93 THE DES SBOXES, PBOX, AND INITIAL PERMUTATION (IP) Tables 94 to 911 specify the seven DES Sboxes, each with a 6bit input (x0, x1, Selection from Computer Security and Cryptography Book. Skinner is considered the “father of Operant Conditioning” His experiments, conducted in what is known as “Skinner’s box,” are some of the most wellknown experiments in psychology This video will talk about Skinner’s box experiments, what influenced them, and the psychology concepts that came about from these experiments Law of.
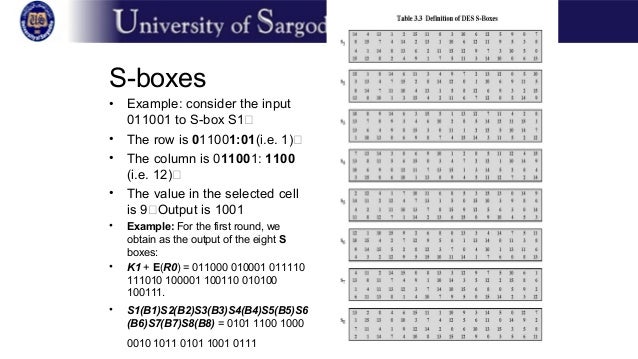
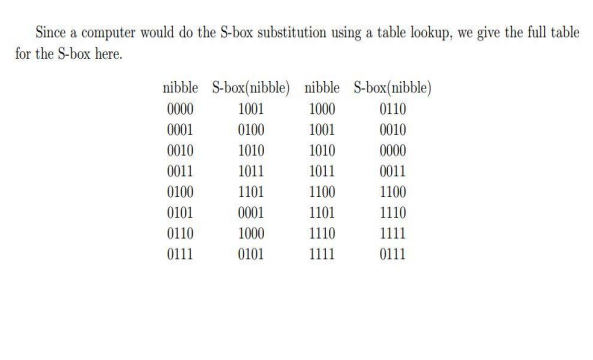
The first bit of the input is used to select the row from the Sbox, 0 for the first row and 1 for the second row The last 3 bits are used to select the column Example Let the output from the expander function be So 1101 will be the input for the S1 box and 0010 will be the input for the S2 box. Sbox Input nibble Output nibble 0000 1001 0001 0100 0010 1010 0011 1011 0100 1101 0101 0001 0110 1000 0111 0101 1000 0110 1001 0010 1010 0000 1011 0011 1100 1100 1101 1110 1110 1111 1111 0111 Construction of S box Input nibble 0101 X2 1 Construct inverse of 0101 modulo XX4 1 1011. Example (Fig 1) Hport = 3" Wport= 10" Lport = " (Fig 2) Since Hport is 3" you need to add 15"( 1/2 Of Hport) tO Lport This means that L1 L2 = 215" Always measure L1 and L2 down the center to get an accurate measurement!.
A 4bit Sbox has been defined as a box of (24 =) 16 elements varies from 0 to F in hex, arranged in a random manner as used in Data Encryption Standard or DES AT90HF71NT77NT99 Similarly for 8 bit Sbox, number of elements are 2 8 or. Get code examples like "rijndael sbox" instantly right from your google search results with the Grepper Chrome Extension. SBox Example using Java Sunday, June 09, 13 Posted by Bipin Rupadiya Write a programs to simulate encryption and decryption technique using SBox, algorithm development and Communication between client and server will be done using Java server socket programming.
Rijndael's Sbox is a frequently used operation in AES encryption and decryption It is typically implemented as a 256byte lookup table It is typically implemented as a 256byte lookup table That's fast, but means you need to enumerate a 256byte lookup table in your code. DES, for example, is a Markov cipher, because for any two 64bit input plaintexts, one can find corresponding subkeys for the first two rounds that will lead to those two input plaintexts not only being enciphered into the same 64bit output, but also going through the same Sbox entries in doing so, and furthermore, for each pair of subkeys. Betari Box Examples Using the Betari Box is all about recognizing negative cycles, and making a change within yourself to break out of them The following examples show what can happen when you are – or are not – willing to make this change Example 1 Imagine that your drive to work is very stressful.
Substitution box (Sbox) is a vital nonlinear component for the security of cryptographic schemes In this paper, a new technique which involves coset diagrams for the action of a quotient of the modular group on the projective line over the finite field is proposed for construction of an Sbox It is constructed by selecting vertices of the coset diagram in a special manner. 30 sentence examples 1 This court case could open a Pandora's box of similar claims 2 The report could open up a Pandora's box of claims from similar cases 3 Sadly, his reforms opened up a Pandora's box of domestic problems 4 The internet has. The Caesar Box code is a cipher in which each letter is replaced with another letter that’s a fixed number of positions down the alphabet To decode one, start by counting the number of characters in the code Then, determine the square root of that number For example, if there are 16 characters in the code, the square root of 16 is 4.
Im getting Sbox transformation of $1010$ as $1001$ Where am i doing wrong ?. Return True if this SBox is an involution, ie the inverse SBox is equal itself EXAMPLES sage from sagecryptosbox import SBox sage S = SBox ( x ** 254 for x in sorted ( GF ( 2 ** 8 ))) sage S is_involution () True. Rijndael sbox with an example in simple words Ask Question Asked 10 years ago Active 9 years, 11 months ago Viewed 3k times 2 All over google and wiki i'm not able to understand the rijndael sbox key scheduling Can anyone explain them in simple words and with an clear example????.
Be aware that the following example is a simplification, but it gives you a general idea of how AES works Unfortunately, there isn’t enough coffee in the world to make most people want to get through the more complicated aspects of AES Normally, the process is performed in binary and there’s a lot more maths. Cryptography and Network Security by Prof D Mukhopadhyay, Department of Computer Science and Engineering, IIT Kharagpur For more details on NPTEL visit ht. SBox SBox SBox SBox SBox SBox SBox SBox 48bit input 32bit output Array of SBoxes Fig 67 Sboxes Sbox bit 1 bit 1 bit 2 bit 2 bit 3 bit 3 bit 4 bit 4 bit 5 bit 6 0 0123 15 1 2 3 Table entry Fig 68 Sbox rule The 48bit data from the second operation is divided into eight 6bit chunks, and each chunk is fed into a box.

About Gost S Cipher Grasshopper Its Sbox And Lost Seeds Virgil Security Inc Blog Sudo Null It News
An Example Of The Aes S Box 4 3 Shift Rows Download Scientific Diagram
Mathematics 360 Homework Due Oct 16 A Hulpke
Section 5 2 The Aes Cipher Cryptography And Network Security 4th Edition

Solved Explain How To Use This S Box And Then Provide An Chegg Com

9 3 The Des S Boxes P Box And Initial Permutation Ip Computer Security And Cryptography Book

Cs480 Cryptography And Information Security Ppt Download

Introduction To Modern Symmetric Key Ciphers Pdf Free Download

A Genetic Algorithm For Constructing Bijective Substitution Boxes With High Nonlinearity Sciencedirect

Tight Bounds Of Differentially And Linearly Active S Boxes And Division Property Of Lilliput
Chapter 3 Block Ciphers And The Data Encryption Standard
Trible Data Encryption Standard 3des
Hardware Realization Of A Secure And Enhanced S Box Based Speech Encryption Engine Springerlink
Sect Ctf 17 Bad Aes
Ppt Class Assignment Powerpoint Presentation Free Download Id

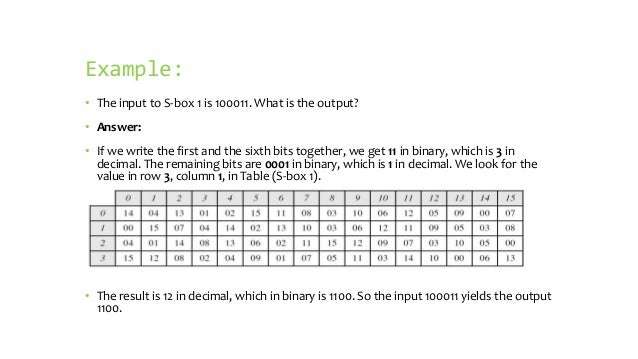
Finding Output Given An S Box Input Of 8 Bits Cryptography Stack Exchange

What Is Data Encryption Standard Des Definition Working Advantages And Disadvantages Binary Terms
Lecture 23 Symmetric Encryption Ppt Download
Cs6701 Cryptography And Network Security
Ppt There Is No Security On This Earth There Is Only Opportunity General Douglas Macarthur Powerpoint Presentation Id

Example Using A Selection Box In A Table

S Box Youtube

How To Compute Bit Independent Criteria On A 4 Bit S Box Cryptography Stack Exchange
Chapter 3 Symmetric Key Cryptosystems 1 Overview Modern Symmetric Key Cryptosystems O Data Encryption Standard Des Adopted In 1976 Block Size Ppt Download

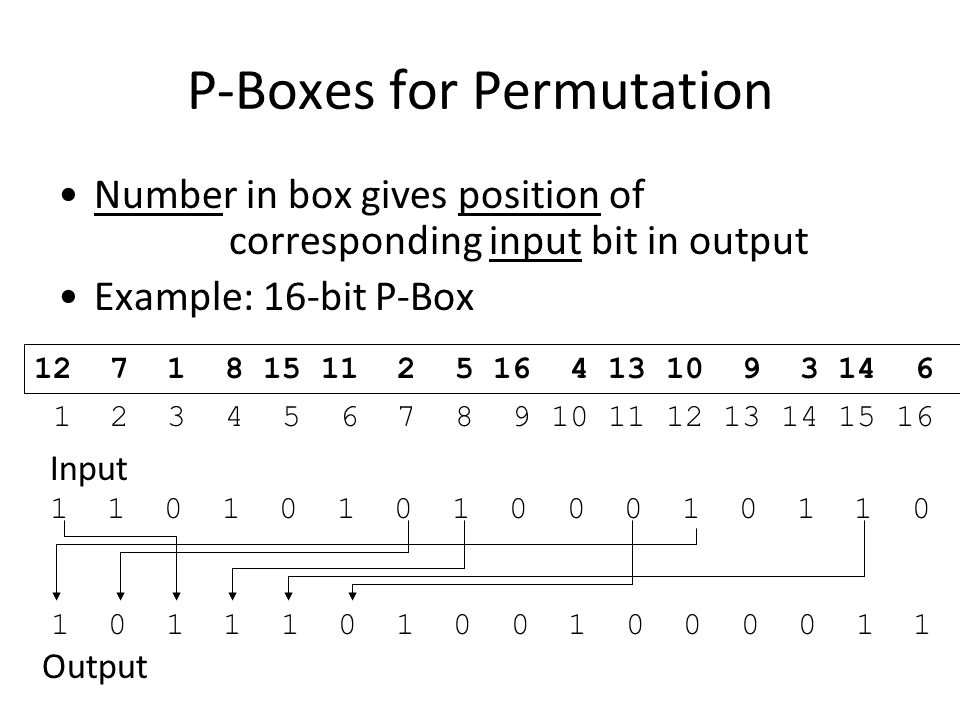
Permutation Box
Class3
Ppt Introduction To Modern Symmetric Key Ciphers Powerpoint Presentation Id

Pdf Image Cryptographic Application Design Using Advanced Encryption Standard Aes Method
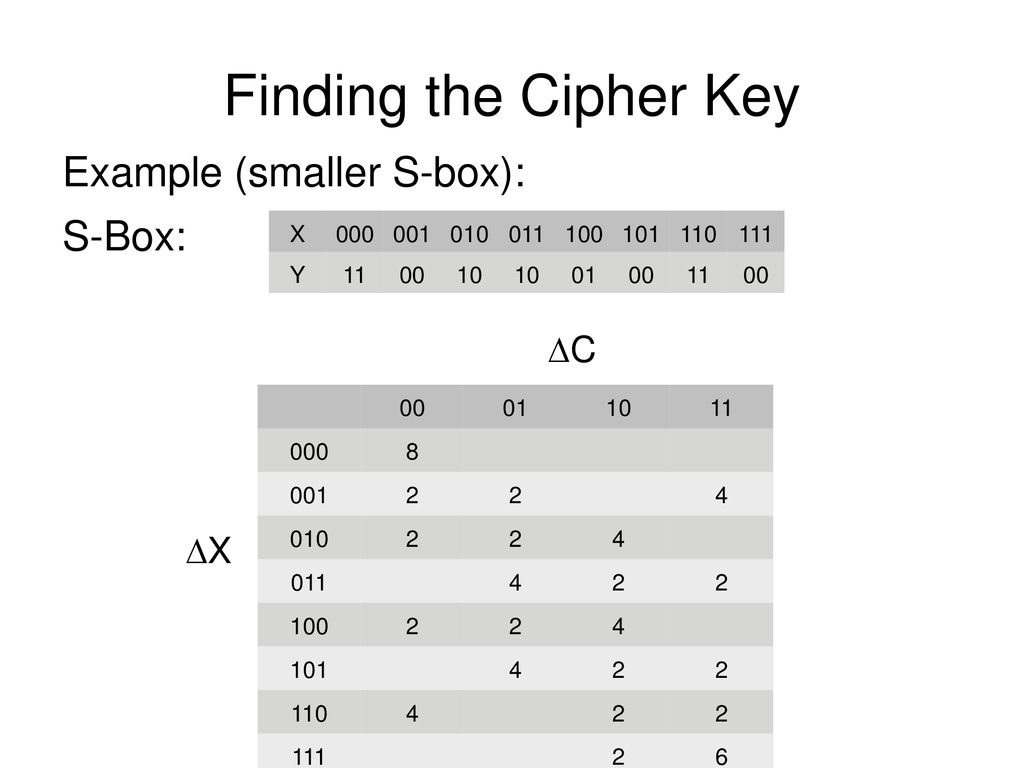
Differential Cryptanalysis Ppt Download
S Box Design Symmetric Ciphers And Hashes Modern Cryptography Applied Mathematics For Encryption And Informanion Security 16

A Detailed Description Of Des And 3des Algorithms Data Encryption Standard And Triple Des Commonlounge
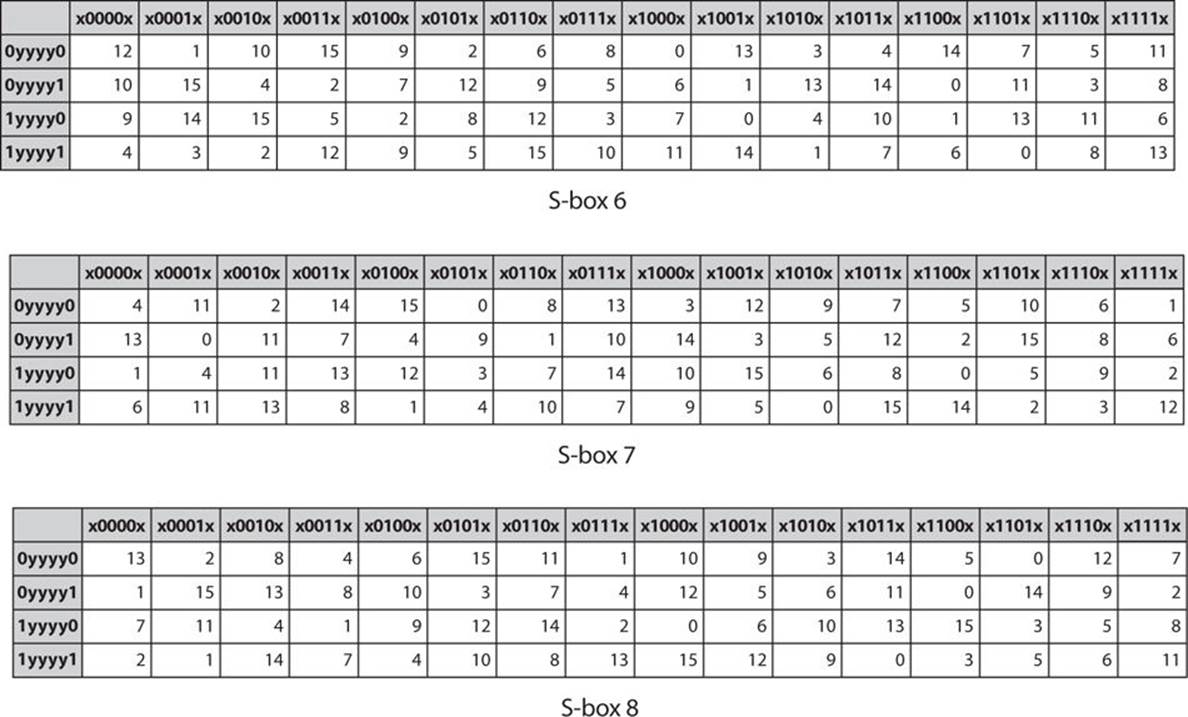
Csci 5857 Encoding And Encryption Ppt Video Online Download

An Example Of The Aes S Box 4 3 Shift Rows Download Scientific Diagram
Javascript Des Example

File Edgeworth Box Example Svg Wikipedia

Symmetric Encryption And Message Confidentiality Ppt Download

Rijndael S Box Wikipedia

Solved 3 15 Suppose That The S Box Of Example 3 1 Is Repl Chegg Com

What Is Data Encryption Standard Des Definition Working Advantages And Disadvantages Binary Terms
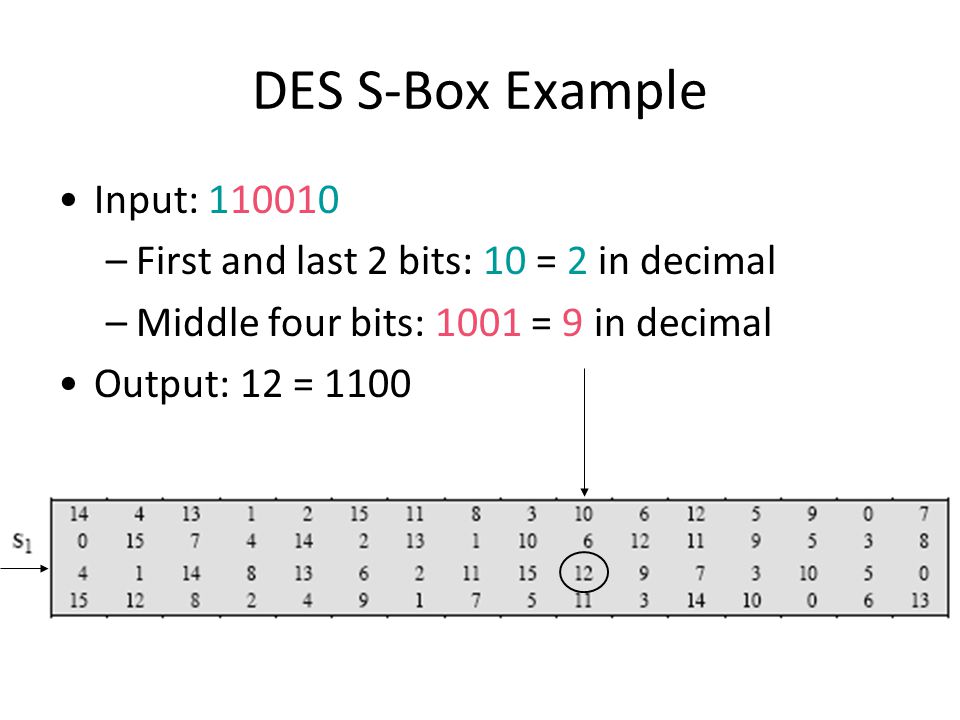
The Digital Encryption Standard Csci 5857 Encoding And Encryption Ppt Download
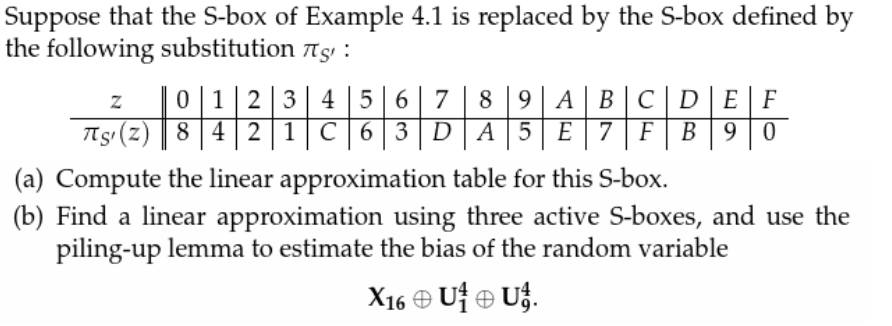
Solved Suppose S Box Example 41 Replaced S Box Defined Following Substitution 8 9a B Cde F Ts Z 8 Q

Advanced Encryption Standard Aes Transformation Functions

How Are The Aes Inverse S Boxes Calculated Cryptography Stack Exchange
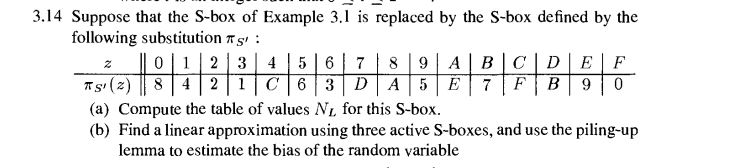
Solved 3 14 Suppose That The S Box Of Example 3 I Is Repl Chegg Com
Ppt Computer Security Set Of Slides 3 Powerpoint Presentation Free Download Id
Q Tbn And9gctsubxpavkf Nfamtihh4u1aeeo0afwzvhy0ol7iptkxhwjp3lm Usqp Cau

Lecture 4 Data Encryption Standard Des Dr Nermin Hamza Ppt Video Online Download

Struts 2 S Combobox Combo Box Example Mkyong Com

Explaon Like I M Five The Rijndael S Box Crypto
3

Advanced Encryption Standard Aes Transformation Functions

Figure 3 From Aes T Box Tampering Attack Semantic Scholar

Achieving High Performance For Advanced Encryption Standard Aes Applications

Des Algorithm Teacher

The Amazing King Differential Cryptanalysis Tutorial

Aes
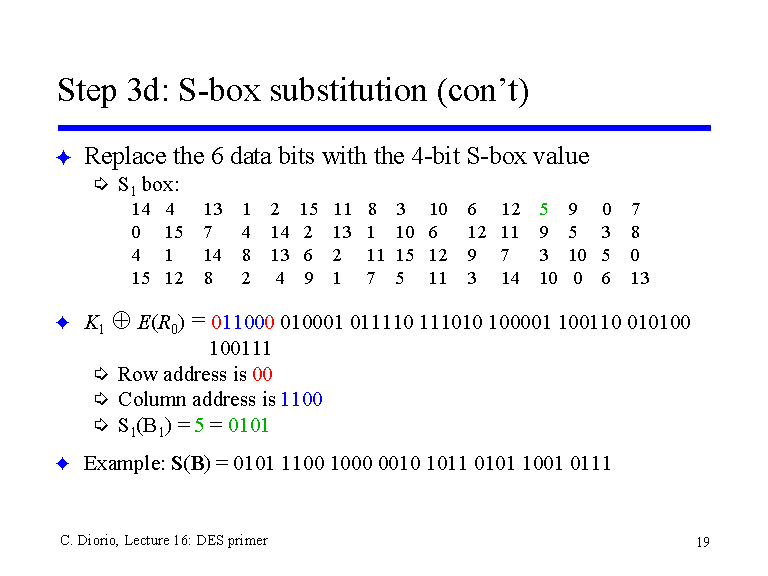
Step 3d S Box Substitution Con T
Simplified Aes Example L Simplified Aes Example Le Chegg Com

9 3 The Des S Boxes P Box And Initial Permutation Ip Computer Security And Cryptography Book
Www Mdpi Com 1099 4300 21 3 245 Pdf
Introduction To Data Encryption Morf Coding And Engineering
Ppt Network Security Powerpoint Presentation Free Download Id

When The Nsa Made Crypto Better In 13 Edward Snowden Outlined How By Prof Bill Buchanan Obe Asecuritysite When Bob Met Alice Medium

Table 3 From A New Algorithm To Construct Secure Keys For Aes Semantic Scholar
Aes Encryption
Solved Contents 1 Fietsel Structure And S Box Review Q Chegg Com

A New S Box Structure To Increase Complexity Of Algebraic Expression For Block Cipher Cryptosystems Semantic Scholar
Solved Q1 Apply One Time Pad Algorithm To Encrypt The Pl Chegg Com

3 30 Pts Use The Spn Substitution Permutation Chegg Com

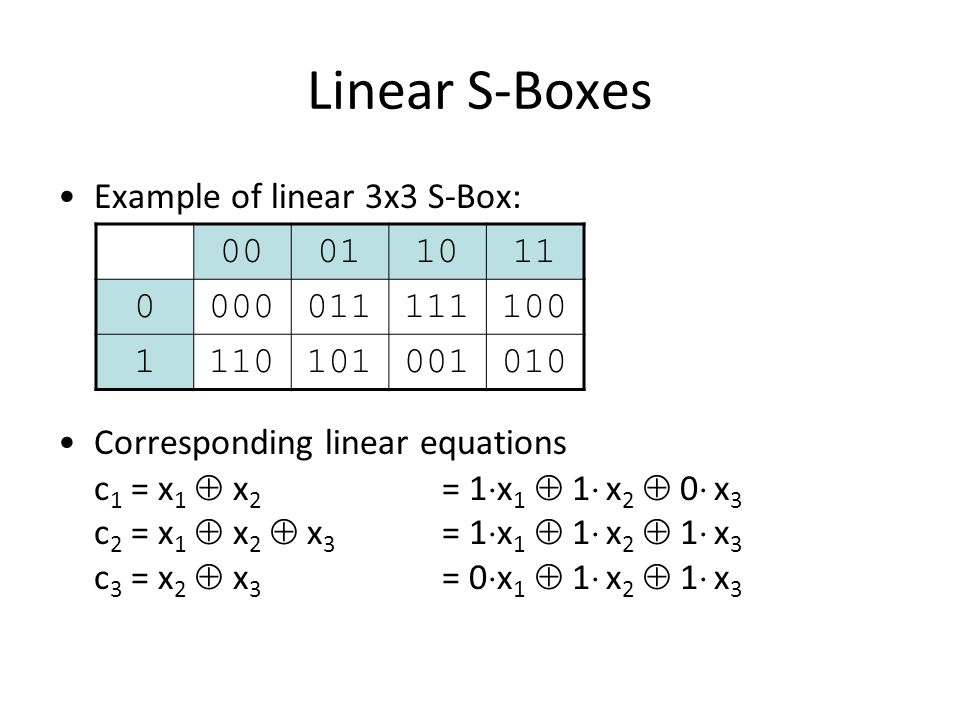
S Box And It S Linearity Cryptography Stack Exchange

Permutation Box Wikiwand

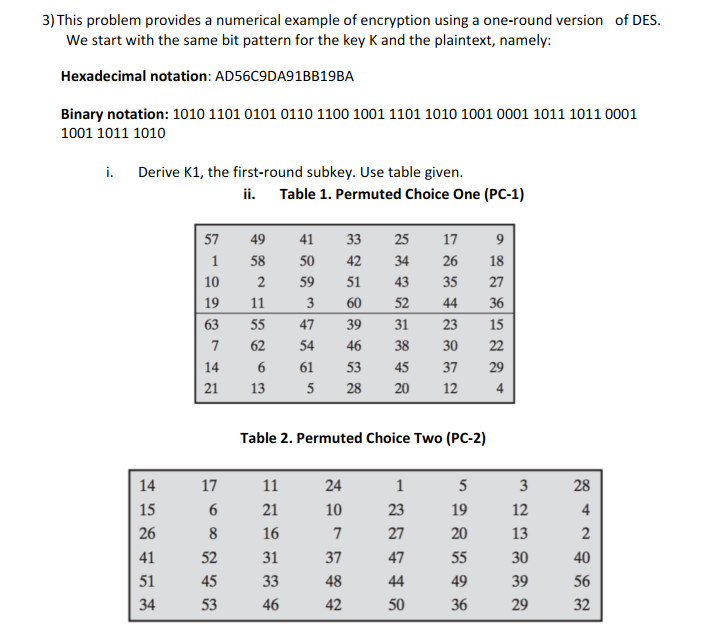
Solved 4 11 This Problem Provides A Numerical Example Of Chegg Com
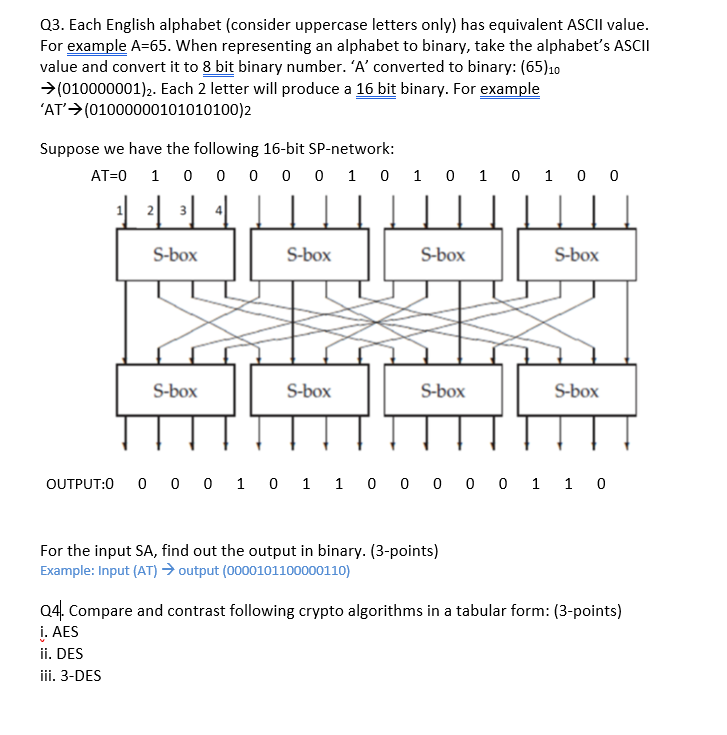
Introduction To Modern Symmetric Key Ciphers Ppt Video Online Download
Block Ciphers

In This Example The Article Is Available In Three Sizes S M L And Download Scientific Diagram
Modern Block Cipher Modern Symmetric Key Cipher
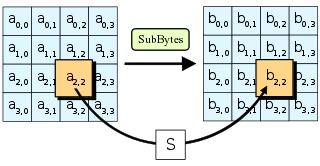
Advanced Encryption Standard Wikipedia

Substitution Permutation Networks Pseudorandom Function Youtube

What Is S Meant By S Box Row And Column In Des Cryptography Stack Exchange
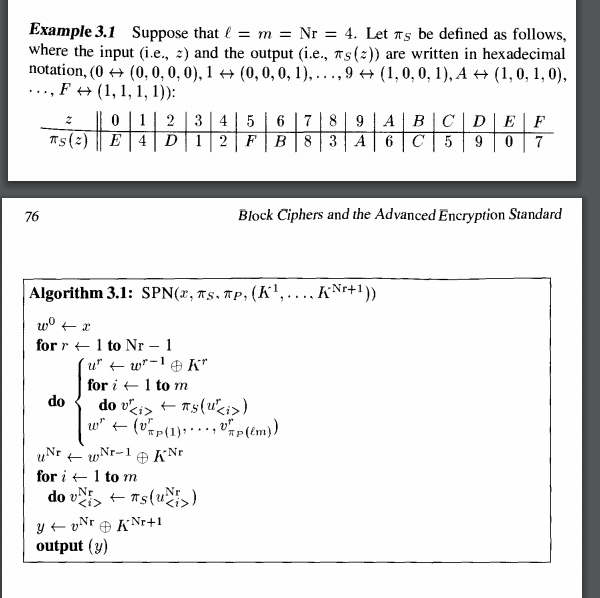
Solved 3 15 Suppose That The S Box Of Example 3 1 Is Repl Chegg Com

Example Using A Selection Box In A Table

Table 1 From Reverse Engineering The S Box Of Streebog Kuznyechik And Stribobr1 Semantic Scholar

Random Facts About Arc4random During The First Week Of Labs At By Kavan Brandon Medium

Des Data Encryption Standard A Symmetric Key Block Cipher By Umesha Ellewala Medium

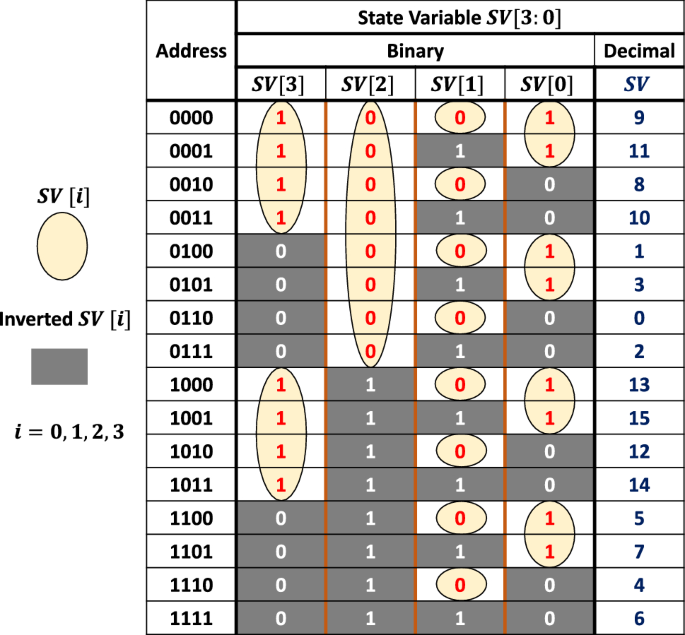
An Illustrative Example Of The Proposed S Box Architecture Download Scientific Diagram
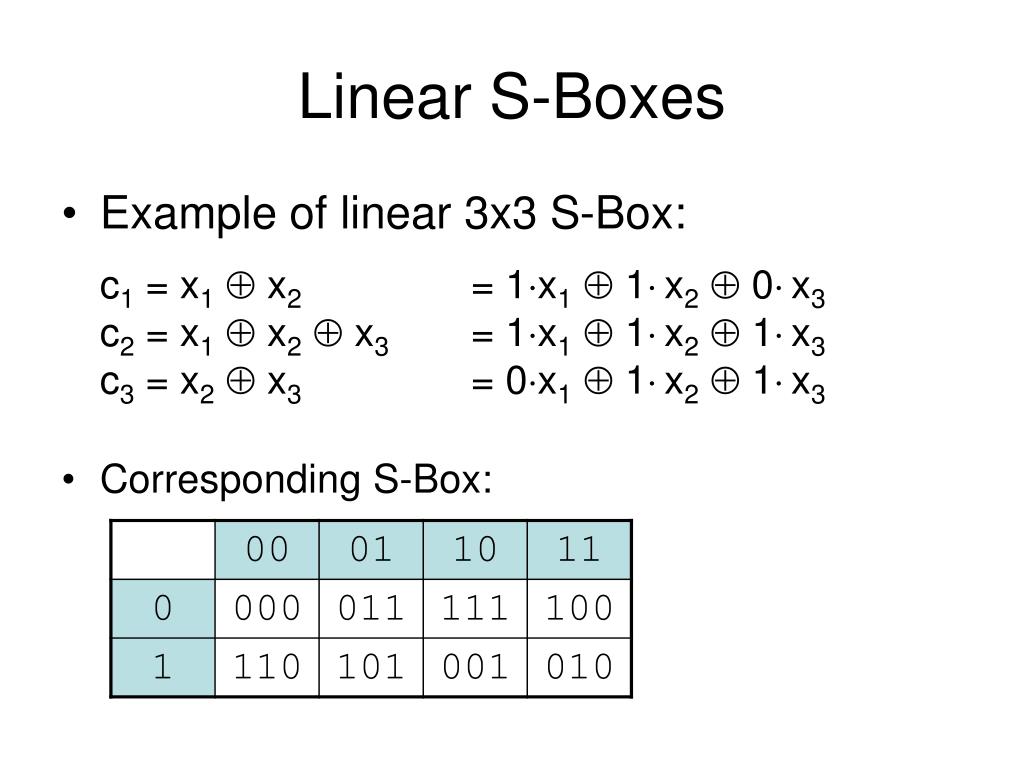
Ppt Digital Encryption Standard Powerpoint Presentation Free Download Id
Substitution Boxes S Have Eight S Boxes Which Map Chegg Com
Cpit 425 Chapter Three Symmetric Key Cryptography Ppt Download
Sp Networks

Advanced Encryption Standard Aes Transformation Functions
Des Analysis And Attacks Csci 5857 Encoding And Encryption Ppt Download
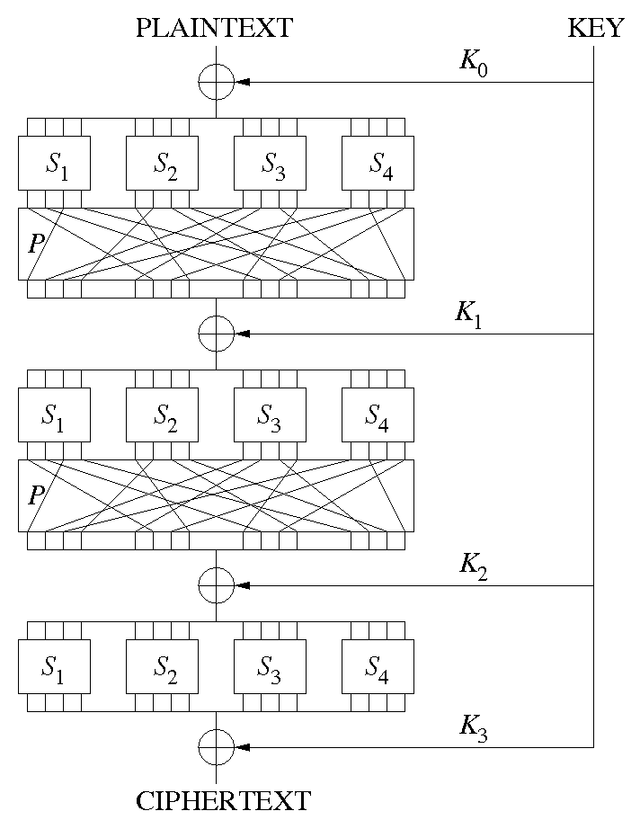
Substitution Permutation Network Wikiwand

Example 3 Ten Cards Numbered 1 To 10 Are Placed In A Box

Pdf The Whirlpool Hashing Function
Q Tbn And9gcsvskl Ol5 Wgf3aikvgc Tqbnnivsvud4qug7wmizavovnhful Usqp Cau
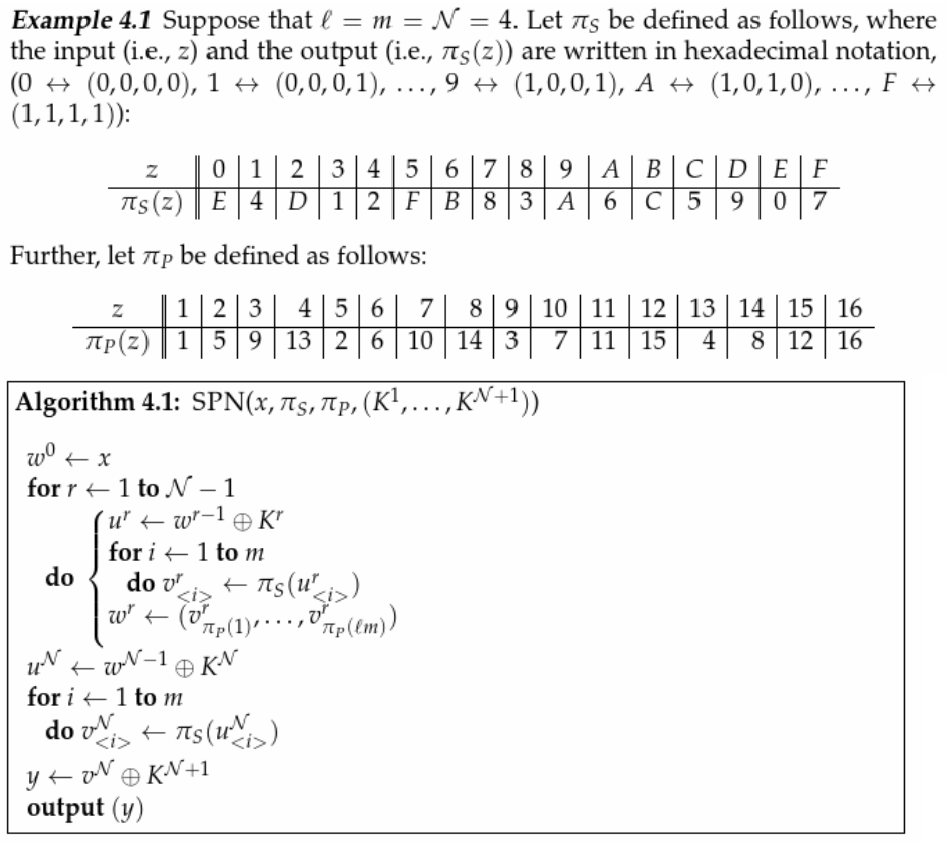
Solved Suppose That The S Box Of Example 4 1 Is Replaced Chegg Com
Example For Completing Label And Transmittal Form Library Media
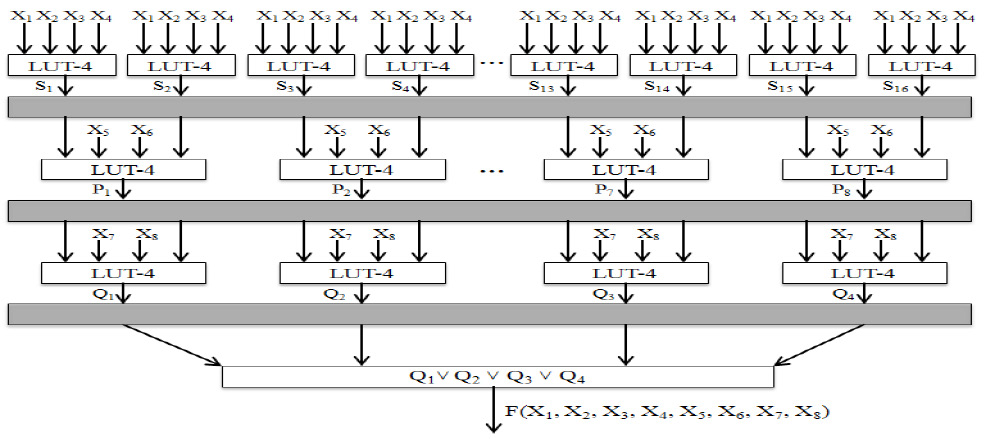
Performance Assessment Of An Efficient Search And Realization Technique Of The S Box In The Aes Cryptosystem Figure 8



