S Box Aes Python
Adding Aes Icm And Aes Gcm To Opencrypto Tib Av Portal

The Advanced Encryption Standard Aes Algorithm Commonlounge

Simplified Aes Example L Simplified Aes Example Le Chegg Com
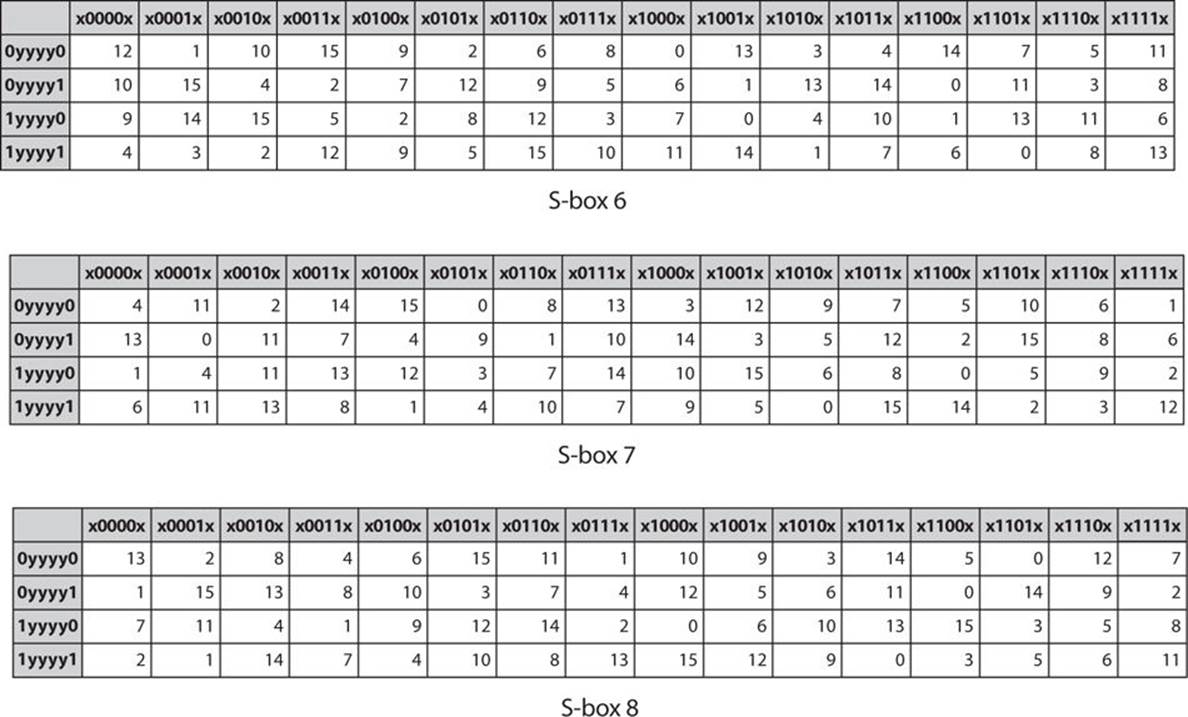
S Box Design Symmetric Ciphers And Hashes Modern Cryptography Applied Mathematics For Encryption And Informanion Security 16
Implement Cryptography Technique In Python Verilog Matlab By Formanlight
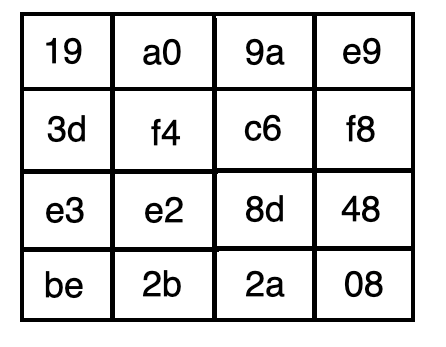
Aes Encryption 256 Bit The Encryption Standard To Rule Them By Cory Maklin Towards Data Science
If the value of s had a.
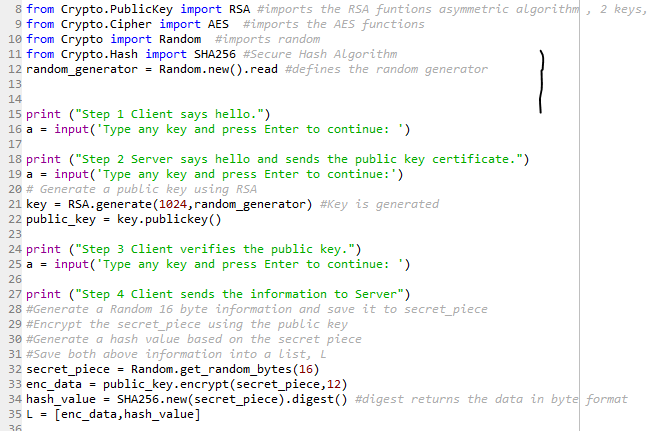
S box aes python. The number of array elements must therefore correspond to the number of distinct values that the input can take, eg if the Sbox input is 8bit, then there are 2 8 = 256 possible input values The size of the array elements themselves correspond to the number of output bits. Also, for AES encryption using pycrypto, you need to ensure that the data is a multiple of 16bytes in length Pad the buffer if it is not and include the size of the data at the beginning of the output, so the receiver can decrypt properly aes = AESnew(key, AESMODE_CBC, iv) data = 'hello world 1234' # < 16 bytes encd = aesencrypt(data) 5. Some information & examples about the SBox.
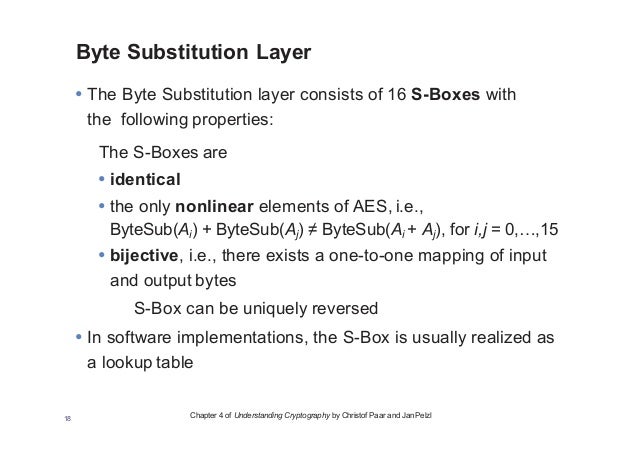
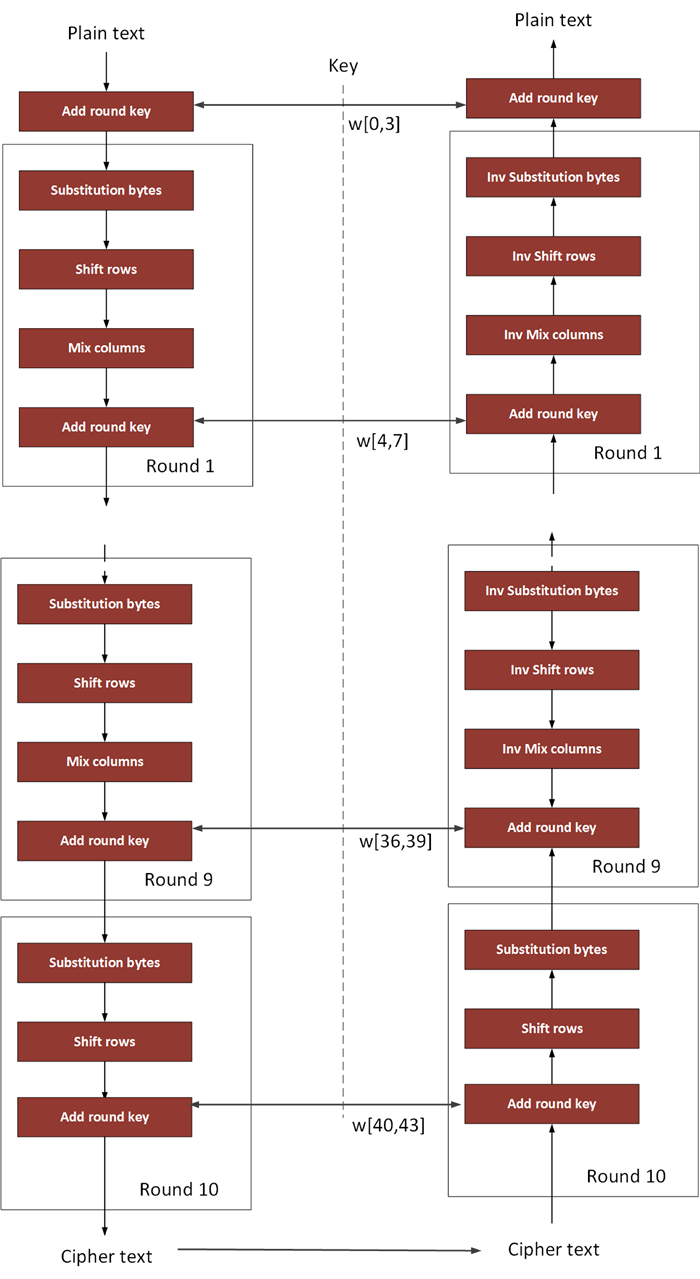
Chapter 4 of Understanding Cryptography by Christof Paar and Jan Pelzl16 Internal Structure of AES • AES is a byteoriented cipher • The state A (ie, the 128bit data path) can be arranged in a 4x4 matrix with A0,, A15 denoting the 16byte input of AES A0 A8 A12 A1 A5 A13 A6 A10 A14 A3 A11 A15 16. SubBytes – each byte in the state is replaced with a different byte according to the SBox lookup table. AES operates on a 4×4 matrix referred to as the state;.
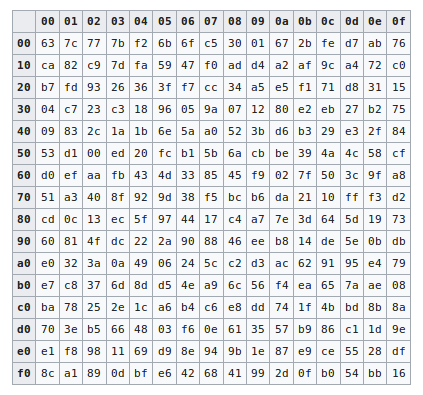
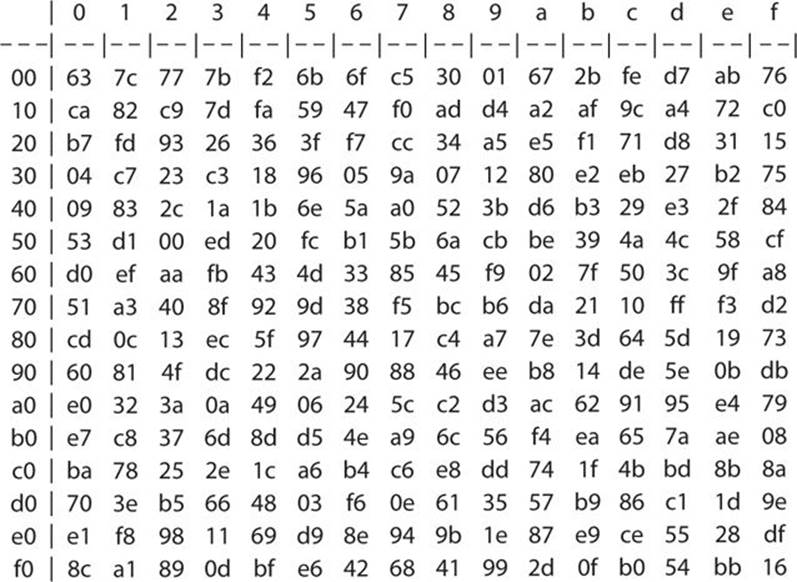
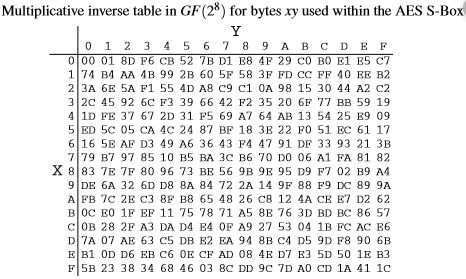
The Sbox maps an 8bit input, c, to an 8bit output, s = S(c) Both the input and output are interpreted as polynomials over GF(2) First, the input is mapped to its multiplicative inverse in GF(2 8) = GF(2)x/(x 8 x 4 x 3 x 1), Rijndael's finite field Zero, as the identity, is mapped to itself. A code in python that xor two numbers would be like this a = 1 b = 2 c = a ^ b print(c) # 3 AES uses a SBox called the Rijndael Sbox, and since AES is a symmetric encryption algorithm. In this post, we are going to find out what is AES, how its algorithm works And in the last section using python AES modules we are going to encrypt/decrypt message Background Before AES show up to the world, there was Data Encryption Standard, DES.
Advanced Encryption Standard (AES) which works on a 128 bit data encrypting it with 128, 192 or 256 bits of keys for ensuring security In this paper, we compare AES encryption with two different SBoxes Sbox with 256 byte lookup table (Rijndael SBox) and AES with 16 byte SBox (Anubis SBox). Lecture 8 AES The Advanced Encryption Standard AES in Python into the four rows of a 4 ×16 Sbox, while using the 4bit segment itself for indexing into the columns of the SBox The substitution step in DES requires bitlevel access to the block coming into a round On the other hand, all. # Python AES implementation import sys, hashlib, string, getpass from copy import copy from random import randint # The actual Rijndael specification includes variable block size, but # AES uses a fixed block size of 16 bytes (128 bits) # Additionally, AES allows for a variable key size, though this implementation # of AES uses only 256bit.
SBoxes and Their Algebraic Representations¶ class sagecryptosboxSBox (* args, ** kwargs) ¶ Bases sagestructuresage_objectSageObject A substitution box or Sbox is one of the basic components of symmetric key cryptography. 16 bytes == 128 bits == block size;. A pure Python implementation of AES Contribute to bozhu/AESPython development by creating an account on GitHub.
Certain games and engines, such as the Rockstar Advanced Game Engine used in Grand Theft Auto IV, use AES to encrypt game assets in order to deter hacking in multiplayer Hardware x8664 and ARM processors include the AES instruction set. In this tutorial I will show you the most basic encryption/decryption program for AES (Advanced Encryption Standard) using PyCrypto and Python 3 Check out m. AddRoundKey – each byte of the round key is combined with the corresponding byte in the state using XOR;.
In cryptography, an Sbox (substitutionbox) is a basic component of symmetric key algorithms which performs substitution In block ciphers, they are typically used to obscure the relationship between the key and the ciphertext — Shannon's property of confusion In general, an Sbox takes some number of input bits, m, and transforms them into some number of output bits, n, where n is not. Sbox The 48bit output obtained by Xor step is reduced to 32 bit again Pbox Here the 32bit result obtained from Sbox is again permuted, which result in 32bit permuted output Definition of AES (Advanced Encryption Standard) Advanced Encryption Standard (AES) is also a symmetric key block cipher. Lecture 8 AES The Advanced Encryption Standard AES in Python into the four rows of a 4 ×16 Sbox, while using the 4bit segment itself for indexing into the columns of the SBox The substitution step in DES requires bitlevel access to the block coming into a round On the other hand, all.
AES Example Round 1, Substitution Bytes current State Matrix is 0 B B @ 00 3C6E 47 1F 4E 22 74 0E 08 1B 31 54 59 0B1A 1 C C A substitute each entry (byte) of current state matrix by corresponding entry in AES SBox for instance byte 6E is substituted by entry of SBox in row 6 and column E, ie, by 9F this leads to new State Matrix 0 B B. In this tutorial we will check how to encrypt and decrypt data with AES128 in ECB mode, using Python and the pycrypto library AES stands for A dvanced E ncryption S tandard and it is a cryptographic symmetric cipher algorithm that can be used to both encrypt and decrypt information 1. Simplified AES implementation in Python Posted on February 11, 12 by JHAF Simplified AES, created by Edward Schaefer and two of his students at Santa Clara University in 03, is described in the paper “A Simplified AES Algorithm and Its Linear and Differential Cryptoanalyses”, Cryptologia, Vol XXVII (2), pages.
PythonAESbase Generator for SBox, inverted SBox, lookup tables for Galois Field product, and Rcon This scripts implements a Binary Polynomial class, used to generate te neccesary tables used in the AES algorithm SBox and inverted SBox for SubBytes and InvSubBytes transformations, lookup tables for Galois Field product x2, x3, x9, x11, x13, x14 used in MixColumns and InvMixColumns, and Rcon used in KeyExpansion. You are using Python 3, not Python 2 You can't use decode() on strings in Python 3, they are already text, so bytestobytes codecs such as 'hex' can't be applied. Rijndael's Sbox is a frequently used operation in AES encryption and decryption It is typically implemented as a 256byte lookup table That's fast, but means you need to enumerate a 256byte lookup table in your code I bet someone in this crowd could do it with less code, given the underlying mathematical structure.
In this tutorial I will show you the most basic encryption/decryption program for AES (Advanced Encryption Standard) using PyCrypto and Python 3 Check out m. And then multiply by a matrix and add a vector to get a new vector The AES designers chose this matrix and vector for this step Same as the polynomials, all the math is mod 2 so you will only end up with 0's and 1's Now you have the AES forward SBox To get the reverse SBox you need to do the steps in reverse. Browse other questions tagged encryption aes sboxes or ask your own question The Overflow Blog Level Up Mastering statistics with Python – part 2.
RELATED How to Download Files in Python Let's start off by installing cryptography pip3 install cryptography Open up a new Python file and let's get started from cryptographyfernet import Fernet Generating the Key Fernet is an implementation of symmetric authenticated cryptography, let's start by generating that key and write it to a file. In this post, we are going to find out what is AES, how its algorithm works And in the last section using python AES modules we are going to encrypt/decrypt message Background Before AES show up to the world, there was Data Encryption Standard, DES. AES¶ AES (Advanced Encryption Standard) is a symmetric block cipher standardized by NISTIt has a fixed data block size of 16 bytes Its keys can be 128, 192, or 256 bits long AES is very fast and secure, and it is the de facto standard for symmetric encryption.
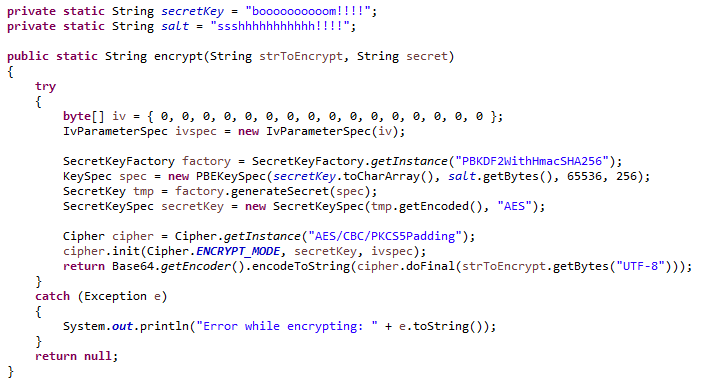
In the following python 3 program, we use pycrypto classes for AES 256 encryption and decryption The program asks the user for a password (passphrase) for encrypting the data This passphrase is converted to a hash value before using it as the key for encryption. The given message is encrypted with AES128 using the AES key and IV from step 2), in CBC mode and PKCS#7 padding In the following python 3 program, we use pycrypto classes for AES 256 encryption and decryption The program asks the user for a password (passphrase) for encrypting the data. T = AES sub_word (t) expanded extend ( xor (t, expanded (iself nk) * 4(iself nk 1) * 4)) return expanded def add_round_key (self, rkey) for i, b in enumerate (rkey) self state i ^= b def sub_bytes (self) for i, b in enumerate (self state) self state i = AES Sbox b def inv_sub_bytes (self) for i, b in enumerate (self state) self state i = AES Sbox_inv b def shift_rows (self).
Advanced Encryption Standard (AES) block cipher system is widely used in crypto graphic applications A nonlinear substitution operation is the main factor of the AES cipher sys tem strength. Browse other questions tagged encryption aes sboxes or ask your own question The Overflow Blog Level Up Mastering statistics with Python – part 2. AES uses a SBox called the Rijndael Sbox, and since AES is a symmetric encryption algorithm there is also a Reverse Rijndael SBox for decryption Finally we are good to go Now that we have basic.
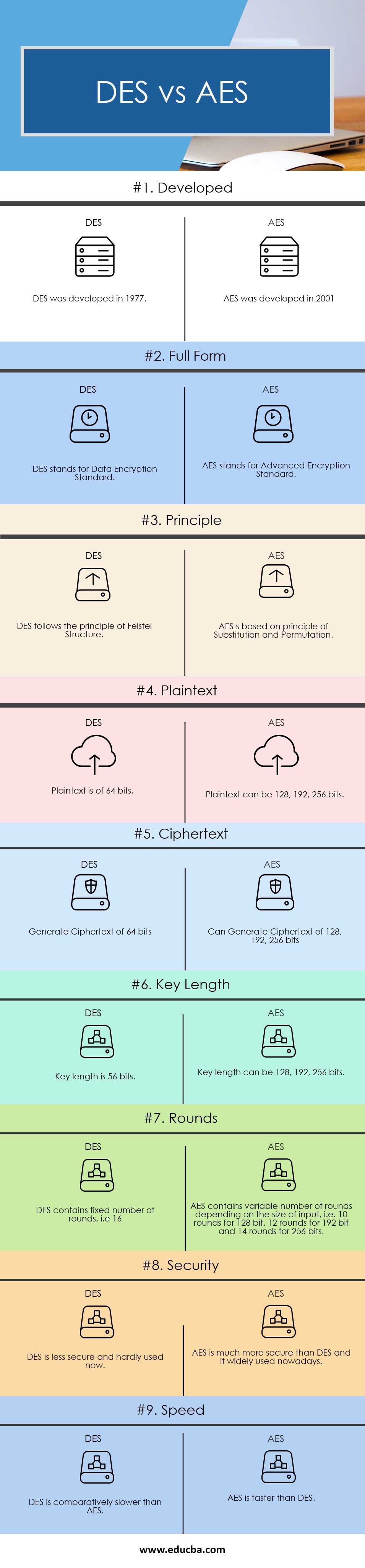
Browse other questions tagged encryption aes sboxes or ask your own question The Overflow Blog Level Up Mastering statistics with Python – part 2. AES Example Round 1, Substitution Bytes current State Matrix is 0 B B @ 00 3C6E 47 1F 4E 22 74 0E 08 1B 31 54 59 0B1A 1 C C A substitute each entry (byte) of current state matrix by corresponding entry in AES SBox for instance byte 6E is substituted by entry of SBox in row 6 and column E, ie, by 9F this leads to new State Matrix 0 B B. AES can encrypt 128 bits of plaintext DES can encrypt 64 bits of plaintext AES cipher is derived from square cipher DES cipher is derived from Lucifer cipher AES was designed by Vincent Rijmen and Joan Daemen DES was designed by IBM No known cryptanalytical attacks against AES but side channel attacks against AES implementations possible.
The Rijndael SBox Given the prominence of AES, the Rijndael Sbox is a good candidate for analysis In fact, this is probably the most important portion of this chapter Before we delve deeply into the Sboxes for Rijndael, let’s look at some of the mathematics behind the Sbox design The actual Rijndael Sbox is shown in Figure 86. “SBox” Implementation of AES is NOT side channel resistant 3 strategy to obtain the AES key in a less restrictive attack scenario Section 5 summarizes related work and Section 6 concludes the paper 2 Background We first review the basics of AES and cache Various cachebased attacks and scenarios are summarized. Sbox and pbox are the technologies that are used in cryptographic algorithms This is just small explanation about the Sbox used by the AES cryptographic algorithm The Sbox is generated by determining the multiplicative inverse for a given n.
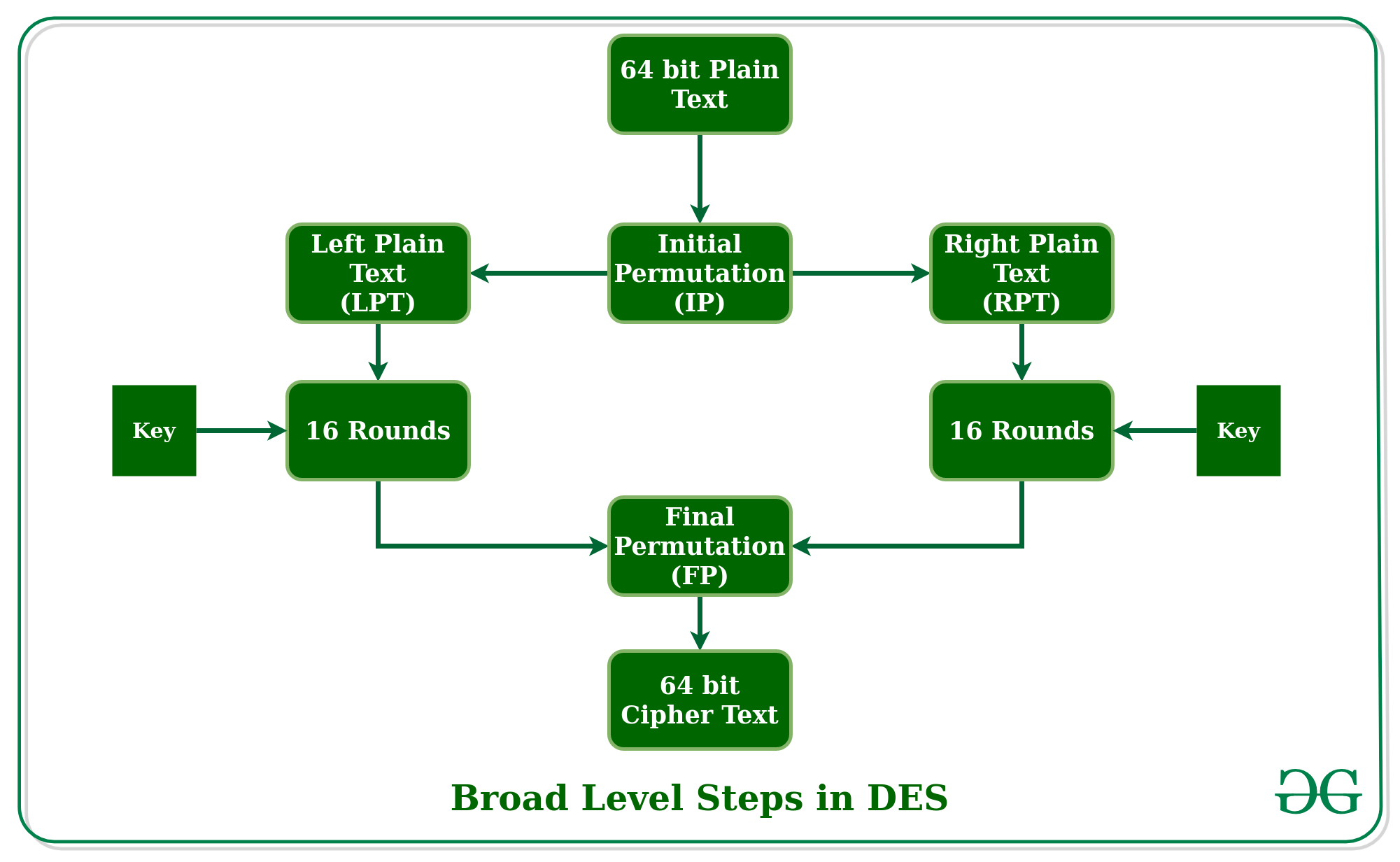
AES¶ AES (Advanced Encryption Standard) is a symmetric block cipher standardized by NISTIt has a fixed data block size of 16 bytes Its keys can be 128, 192, or 256 bits long AES is very fast and secure, and it is the de facto standard for symmetric encryption. All operations in a round of AES are invertible;. For decryption, we use the same algorithm, and we reverse the order of the 16 round keys Next, to better understand what is DES, let us learn the various modes of operation for DES DES Modes of Operation Data encryption experts using DES have five different modes of operation to choose from.
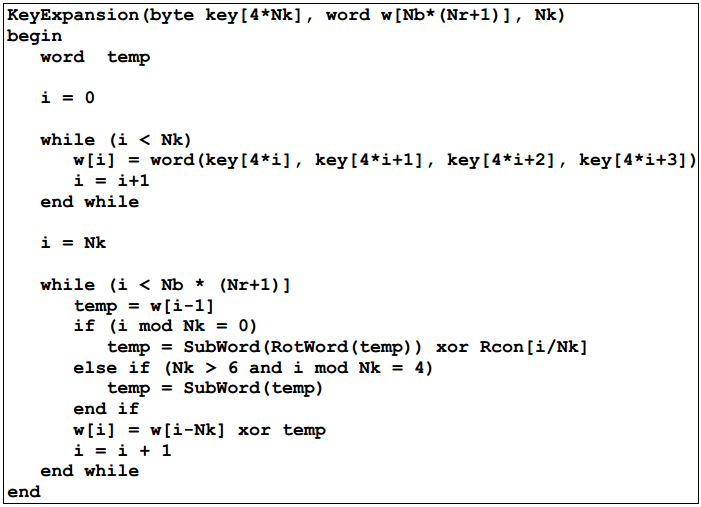
Also, for AES encryption using pycrypto, you need to ensure that the data is a multiple of 16bytes in length Pad the buffer if it is not and include the size of the data at the beginning of the output, so the receiver can decrypt properly aes = AESnew(key, AESMODE_CBC, iv) data = 'hello world 1234' # < 16 bytes encd = aesencrypt(data) 5. AES key expansion consists of several primitive operations Rotate – takes a 4byte word and rotates everything one byte to the left, eg rotate(1,2,3,4) → 2, 3, 4, 1 SubBytes – each byte of a word is substituted with the value in the SBox whose index is the value of the original byte. This article describes the Sbox used by the Rijndael (aka AES) cryptographic algorithm where x0, , x7 is the multiplicative inverse as a vector The matrix multiplication can be calculated by the following algorithm Store the multiplicative inverse of the input number in two 8bit unsigned temporary variables s and x Rotate the value s one bit to the left;.
XFire uses AES128, AES192 and AES 256 to encrypt usernames and passwords;.

Top Pdf Decryption Algorithm 1library

Crypto On X86 And Arm Optimization Of Encryption Algorithms Using X86 And Arm Assembly

4 The Advanced Encryption Standard Aes
Sect Ctf 17 Bad Aes
S Box Design Symmetric Ciphers And Hashes Modern Cryptography Applied Mathematics For Encryption And Informanion Security 16

Explaon Like I M Five The Rijndael S Box Crypto

Python Aes Encryption Decryption Using Pycrypto Tutorial Youtube

Cosic Cryptography Blog Cosic Page 2
4 The Advanced Encryption Standard Aes
Data Encryption Standard Des Set 1 Geeksforgeeks

Aes Key Generation In Python Rmraport

The Aes Rijndael S Box
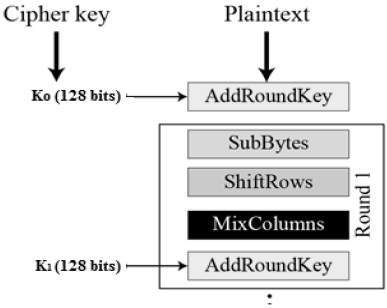
Advanced Encryption Standard Tutorialspoint

Simplified Aes Implementation In Python Joao H De A Franco

Very Basic Intro To The Aes 256 Cipher Qvault

Trouble Implementing Aes Key Expansion Stack Overflow

Aes Encryption Principle And Aoe Engineering Practice Develop Paper
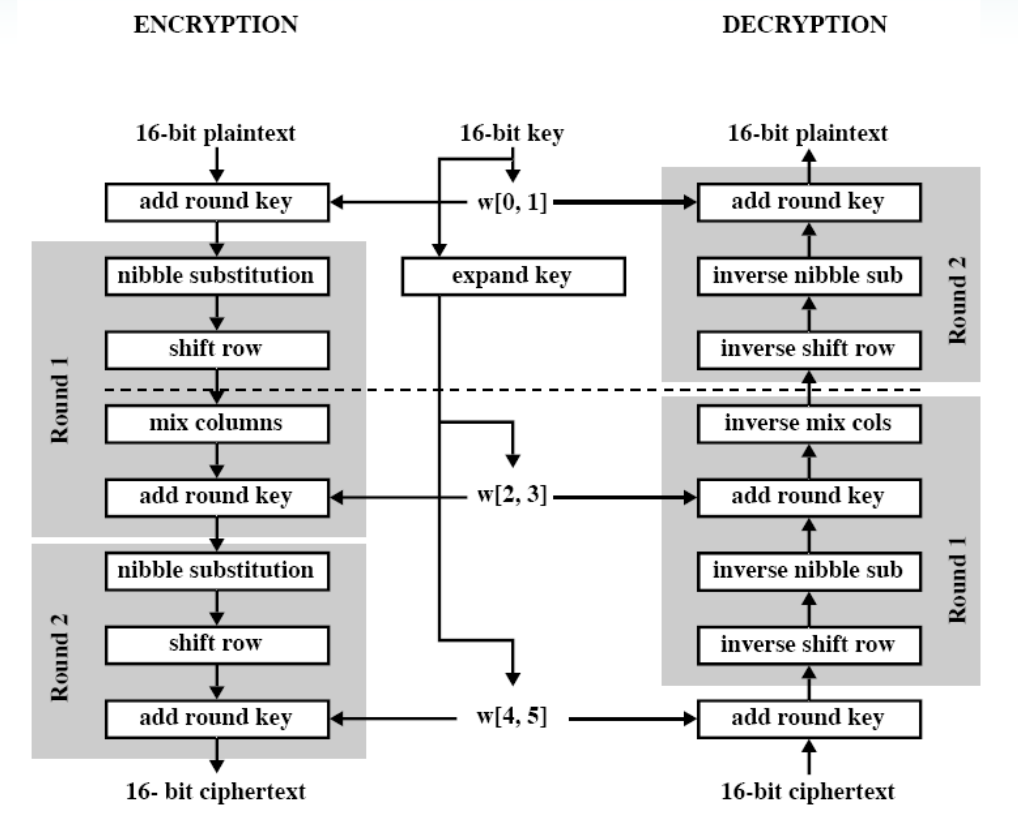
9 Advanced Encryption Standard

Hidden In Plaintext An Obfuscation Based Countermeasure Against Fpga Bitstream Tampering Attacks
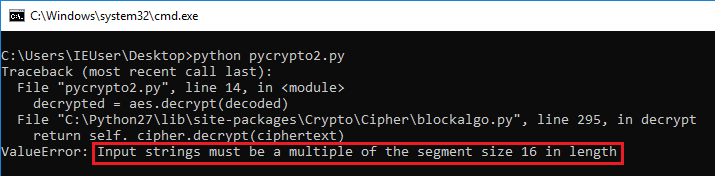
Aes Cfb128 Pycrypto Vs Go

Aes Encryption Principle And Aoe Engineering Practice Develop Paper

Calculate The Output Of The S Box In Aes Manually Programmer Sought

How We Can Calculate Aes Inverse Sbox Cryptography Stack Exchange
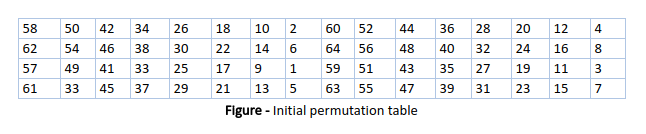
Data Encryption Standard Des Set 1 Geeksforgeeks

Cache Attacks On The Arm Trustzone Implementations Of Aes 256 And Aes 256 Gcm Via Gpu Based Analysis Springerlink

Recovering The Aes Key On A Cortex M3 Processor With Emusca Using Unicorn Engine And Daredevil By Jevinskie Adafruit Industries Makers Hackers Artists Designers And Engineers

List Of 0 Cryptography Resources
C Implementation Of Aes Encryption Algorithms

S Box Implementation Of Aes Is Not Side Channel Resistant Springerlink
Python Generate An Aes Key Peatix

Linux Security 15

How We Can Calculate Aes Inverse Sbox Cryptography Stack Exchange

The Advanced Encryption Standard Aes Algorithm Commonlounge
9 Advanced Encryption Standard

Part 3 Topic 2 Recovering Aes Key From A Single Bit Of Data Chipwhisperer 5 4 0 Documentation

Lecture 8 Aes Purdue University
Aes Ccm Attack Chipwhisperer Wiki

What Is Aes Encryption And How Does It Work Cybernews

Crypto On X86 And Arm Optimization Of Encryption Algorithms Using X86 And Arm Assembly Page 2

Please Implement Aes Encryption From Scratch Witho Chegg Com

Aes Implementations Wikipedia
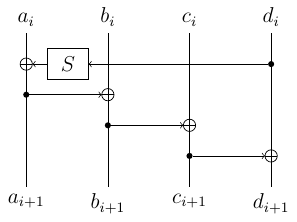
Tokyo Westerns Mma Ctf 16 Backdoored Crypto System Reverse Crypto 400 More Smoked Leet Chicken
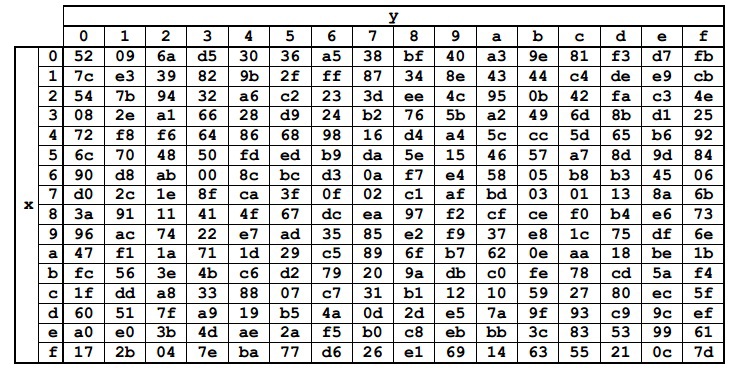
Aes 128 Details And Implementation In Python Sudo Null It News
How To Use Redis With Python Real Python
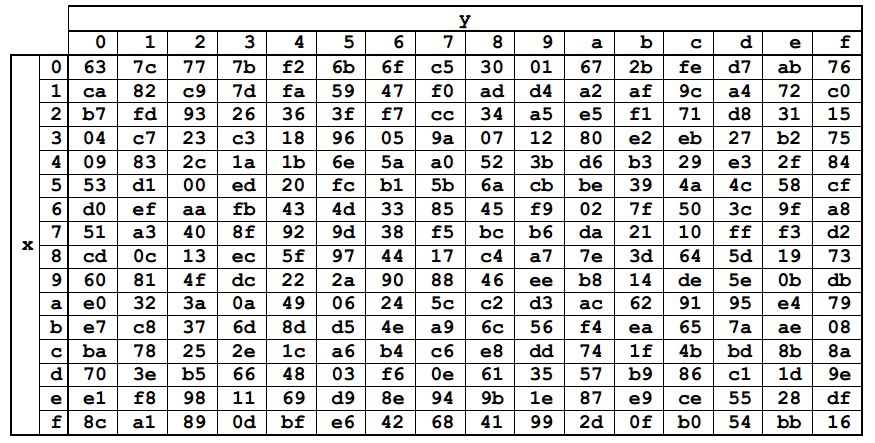
Aes 128 Details And Implementation In Python Sudo Null It News
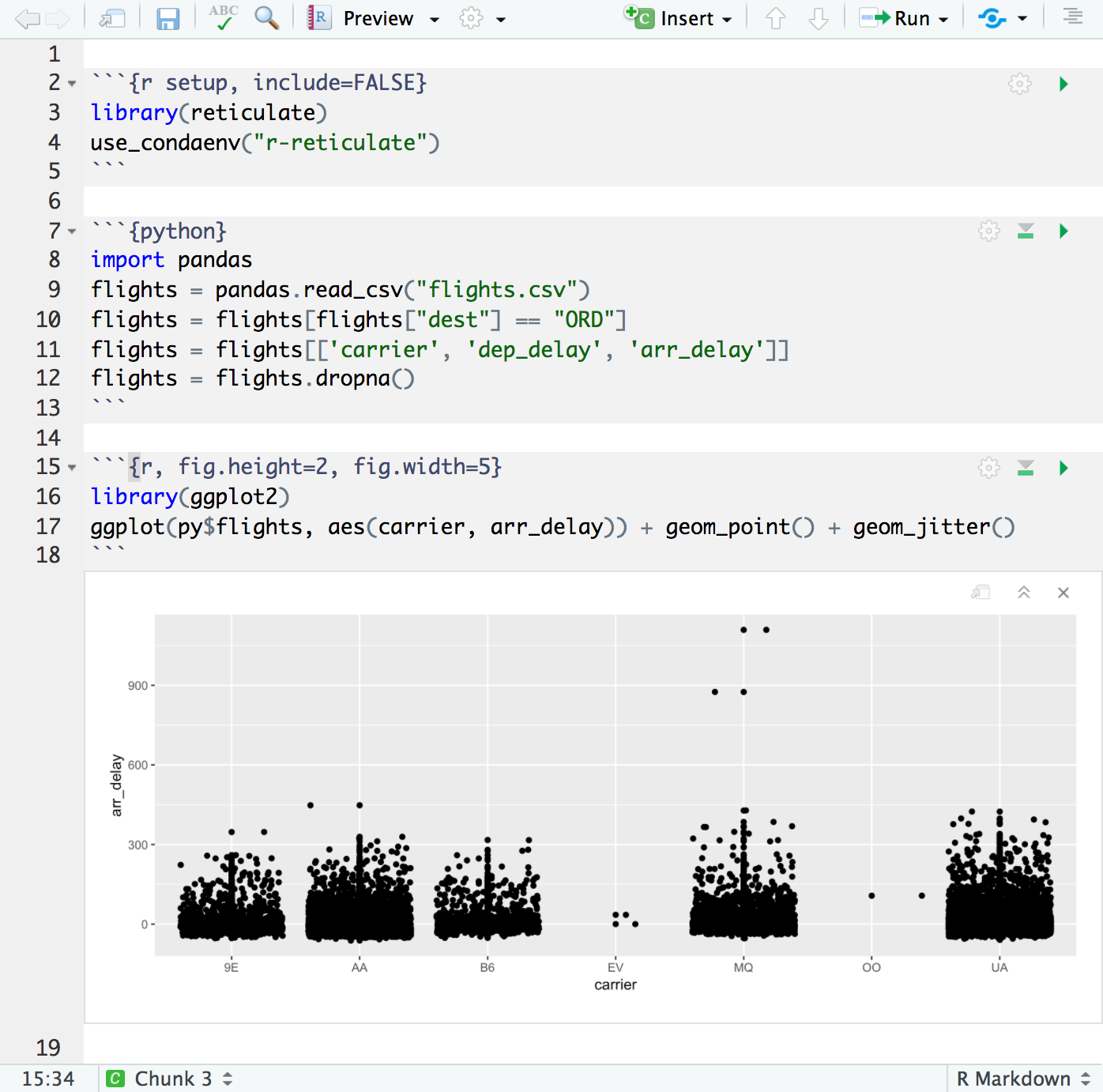
Rstudio 1 2 Preview Reticulated Python Rstudio Blog

Pdf An Aes Based Encryption Algorithm With Shuffling

Brandon Sterne Aes Tutorial Python Implementation

128 Bit Aes Rijndael Block Cipher Behind The Sciences

Explaon Like I M Five The Rijndael S Box Crypto

Rijndael S Box Wikipedia

Very Basic Intro To The Aes 256 Cipher Qvault

Building Aes 128 From The Ground Up With Python By Henrique Marcomini Wavy Product Engineering Medium

V4 Tutorial B6 Breaking Aes Manual Cpa Attack Chipwhisperer Wiki

Building Aes 128 From The Ground Up With Python By Henrique Marcomini Wavy Product Engineering Medium

Python Language Please I Need Help Generating 10 R Chegg Com
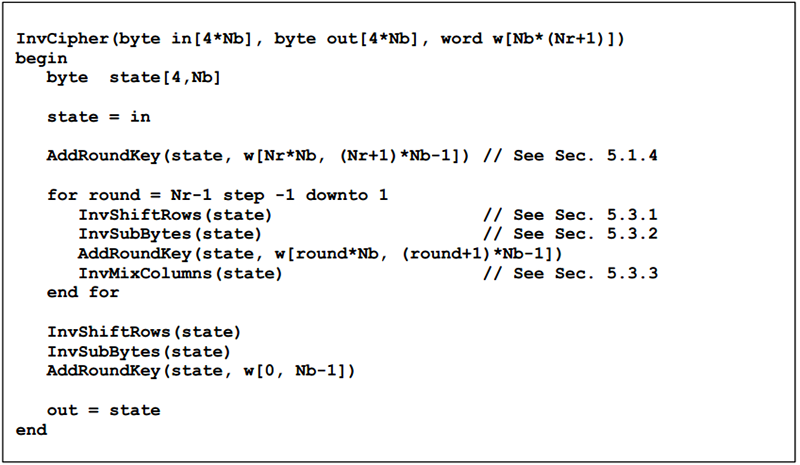
C Implementation Of Aes Encryption Algorithms
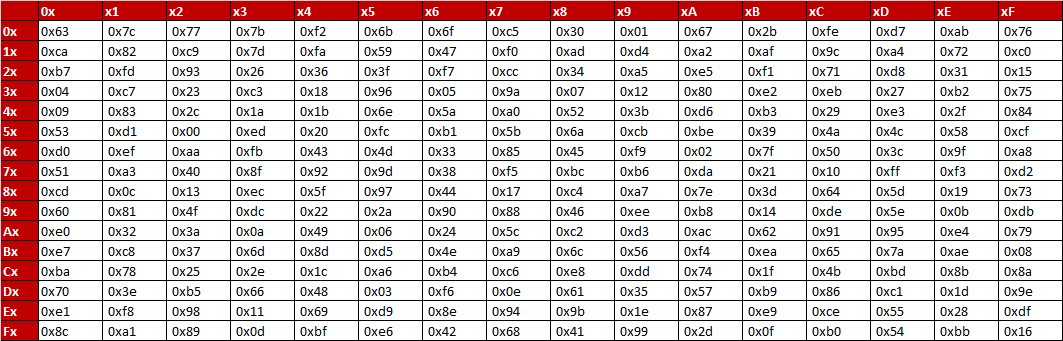
Aes Encryption

S Box And P Box
Differential Fault Analysis On White Box Aes Implementations

The Aes Block Cipher Block Ciphers Coursera
A Practical Guide For Cracking Aes 128 Encrypted Firmware Updates Hypoxic

Hpac Sbox A Novel Implementation Of Predictive Learning Classifier And Adaptive Chaotic S Box For Counterfeiting Sidechannel Attacks In An Iot Networks Sciencedirect

Output Problem In The Implementation Of Aes Sbox With Secret Sharing Concept Stack Overflow

Stm32 Implement Aes 128 Bit Encryption Algorithm Standard Implementation Transfer Programmer Sought
Des Vs Aes Top 9 Amazing Differences You Should Learn
Aes Cfb128 Pycrypto Vs Go

A Practical Guide For Cracking Aes 128 Encrypted Firmware Updates Hypoxic

Chapter 36 Aes Encryption And Decryption On The Gpu Nvidia Developer
Aes Encryption
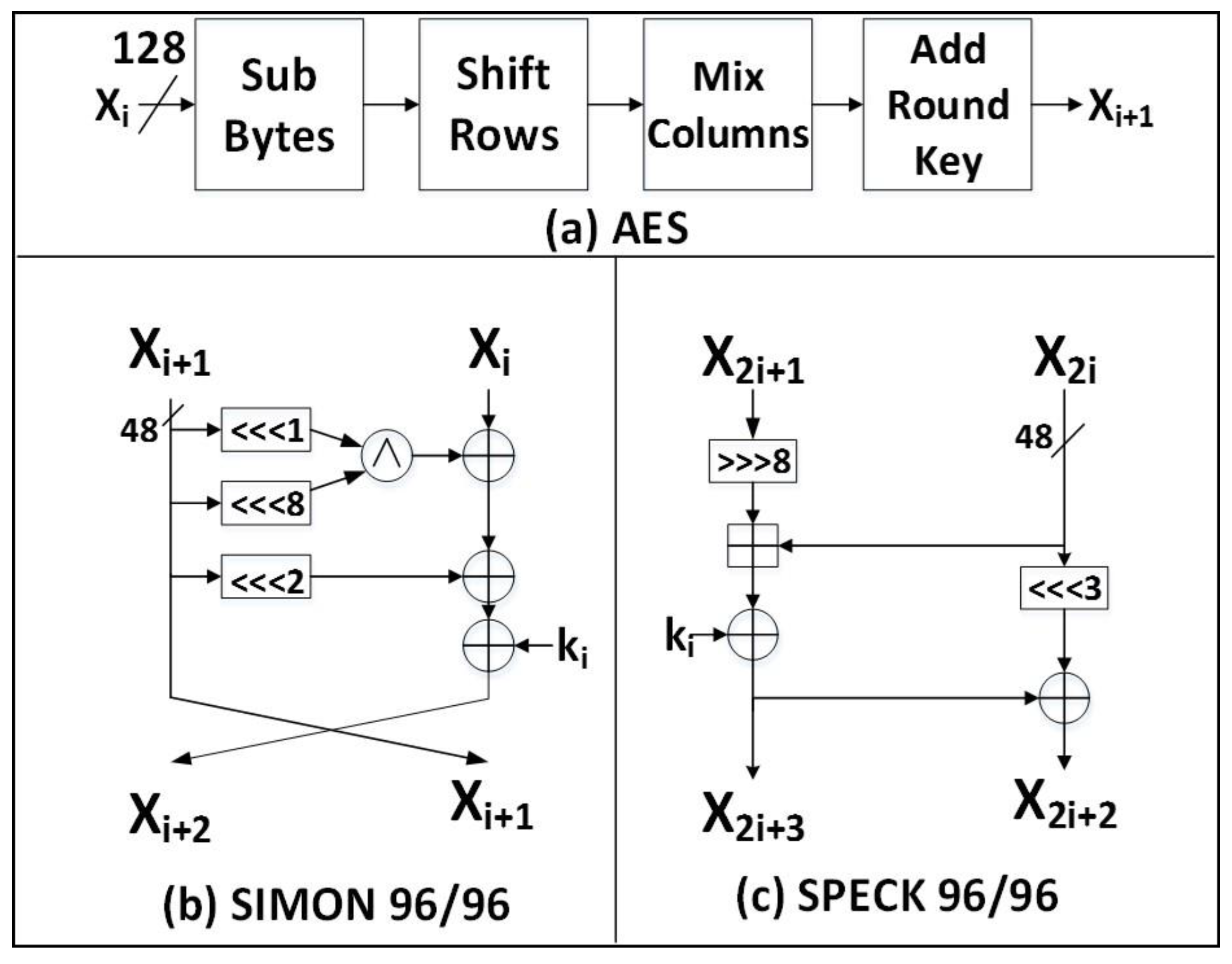
Computers Free Full Text Comparing The Cost Of Protecting Selected Lightweight Block Ciphers Against Differential Power Analysis In Low Cost Fpgas Html

Pdf Python Based Fpga Implementation Of Aes Using Migen For Internet Of Things Security
Github Pcaro90 Python Aes Base Generator For S Box Inverted S Box Lookup Tables For Galois Field Product And Rcon

Aes S Box Affine Mapping How To Do It Cryptography Stack Exchange
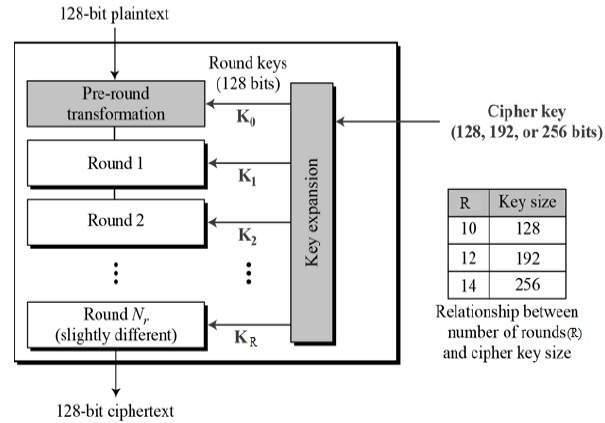
Advanced Encryption Standard Tutorialspoint
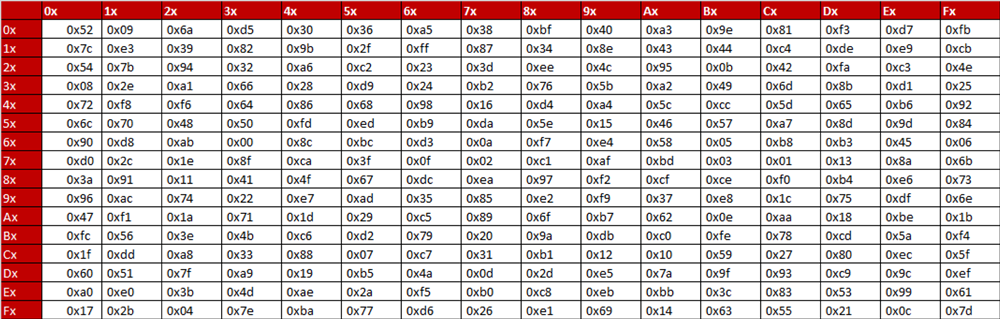
Aes Encryption

How Are S Box Calculated In S Aes Cryptography Stack Exchange
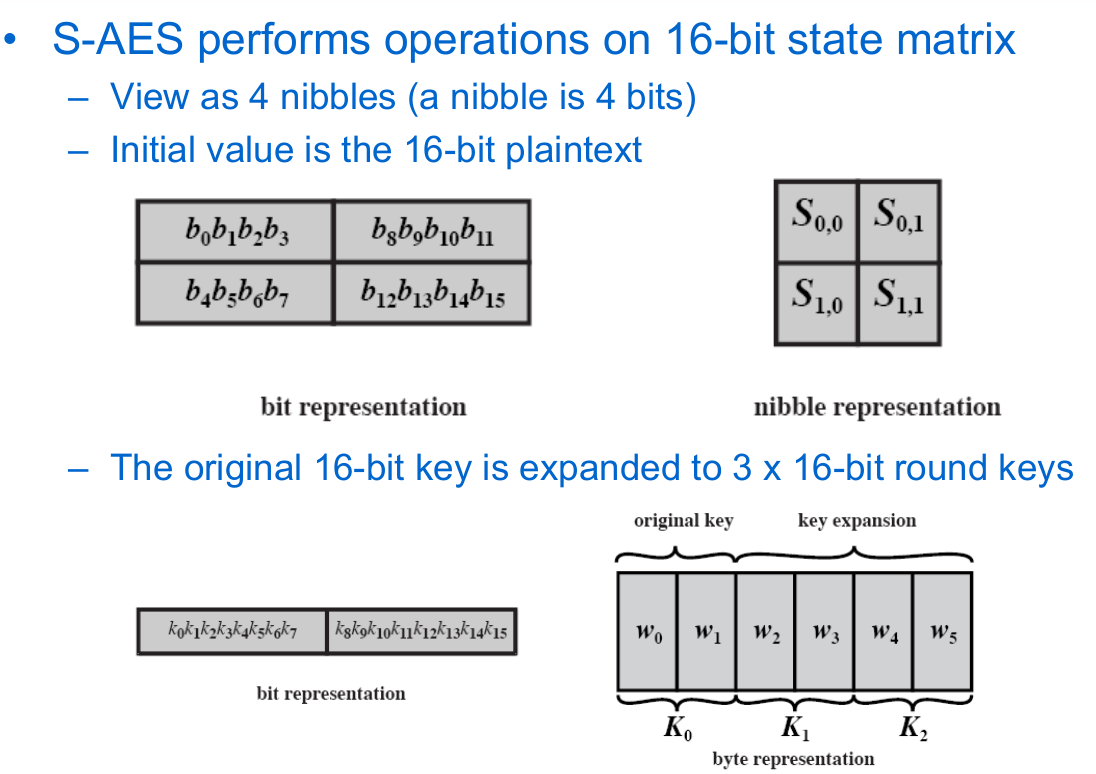
9 Advanced Encryption Standard

Cloud Security Using Aes Algorithm With Dynamic S Box Youtube
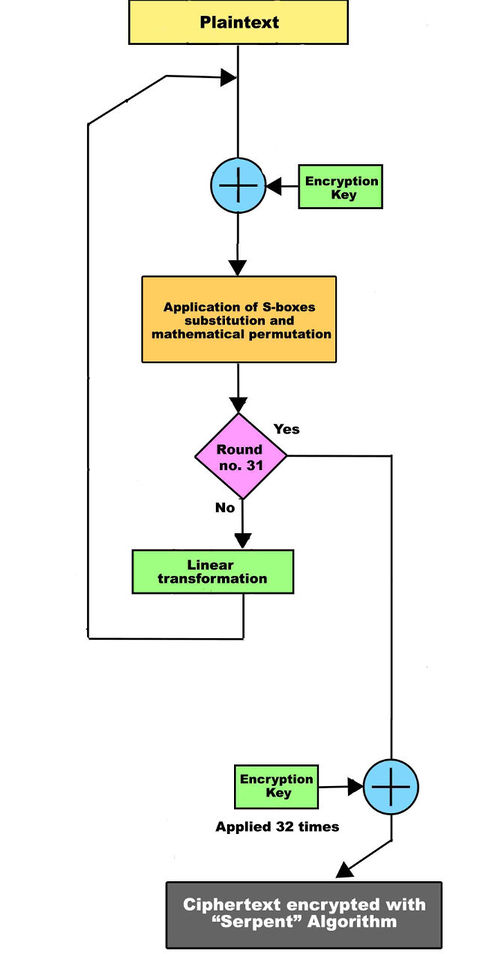
Encrypting Everything Gender And Tech Resources

Crypto Squarectf 18 C4 Leaky Power Teamrocketist Portuguese Ctf Team

Building Aes 128 From The Ground Up With Python By Henrique Marcomini Wavy Product Engineering Medium
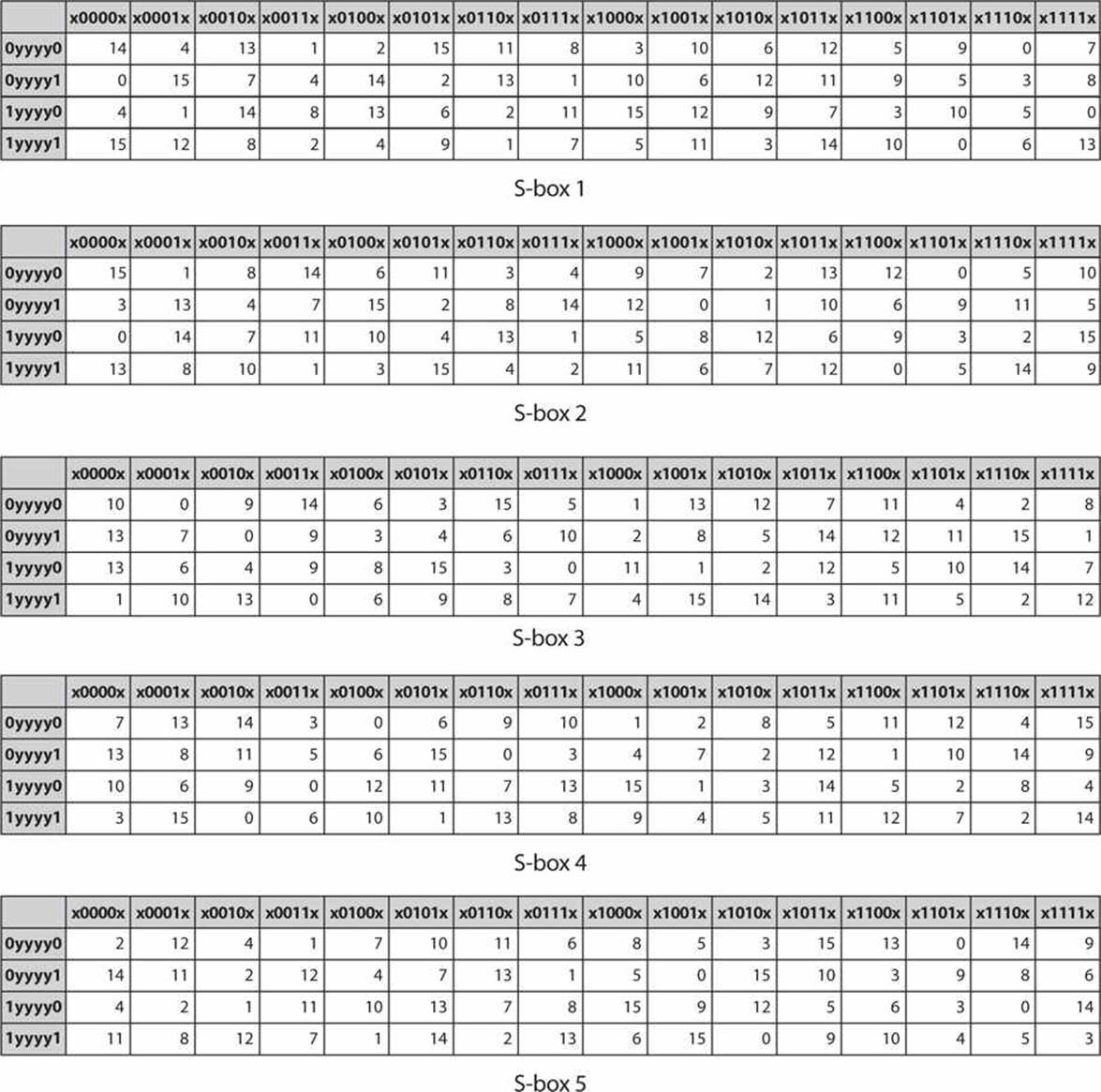
S Box Design Symmetric Ciphers And Hashes Modern Cryptography Applied Mathematics For Encryption And Informanion Security 16



