S Box Table For Aes
Avalanche Effect Of Aes Algorithm

Fpga Implementation Results For Aes S Box Module Download Table
A Novel Byte Substitution Architecture For The Aes Cryptosystem

Plot Of The Difference Of The S Boxes Elements Table 2 And Table 3 Download Scientific Diagram
A Stick Figure Guide To The Advanced Encryption Standard Aes

Aes Advanced Encryption Standard Anu Vazhayil
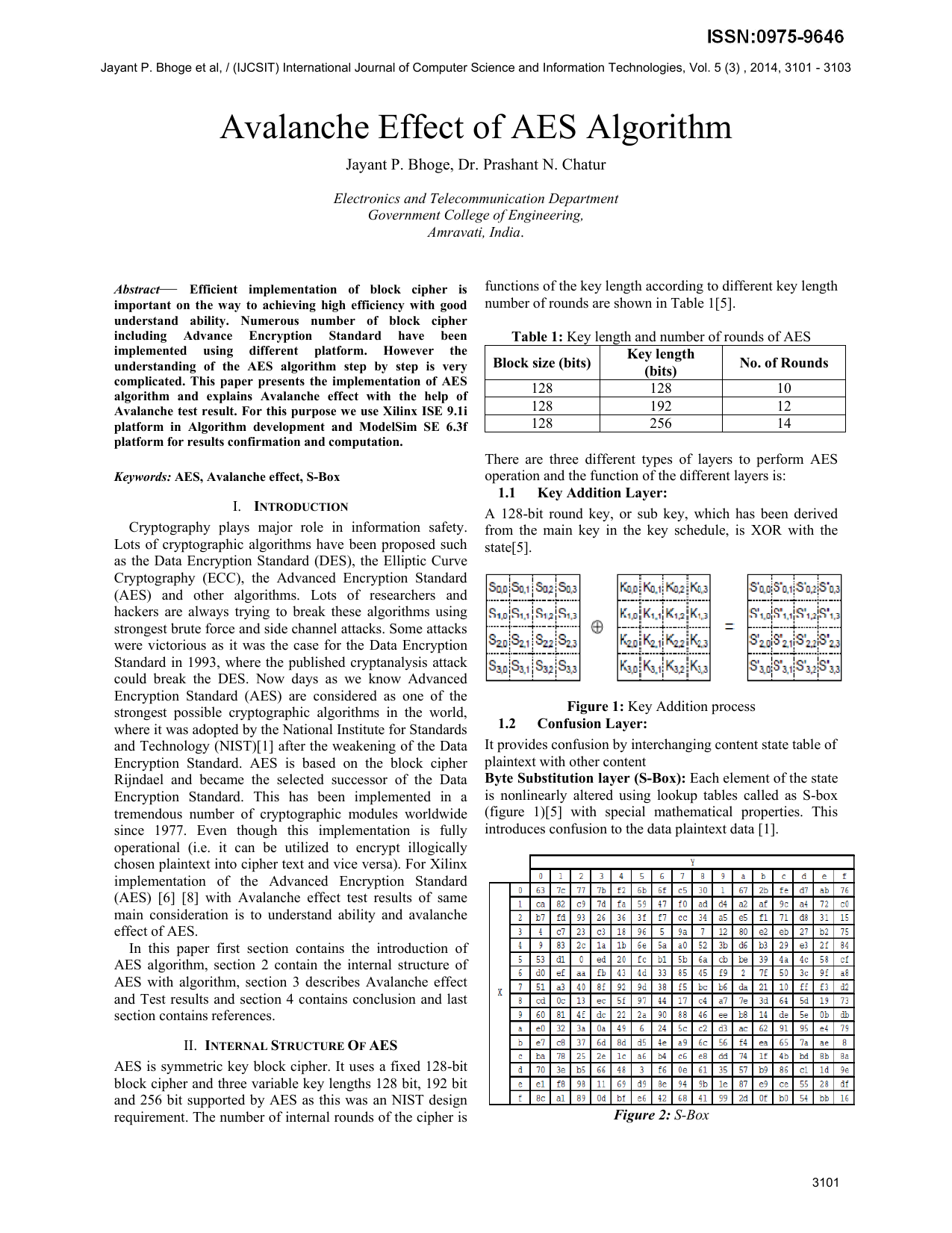
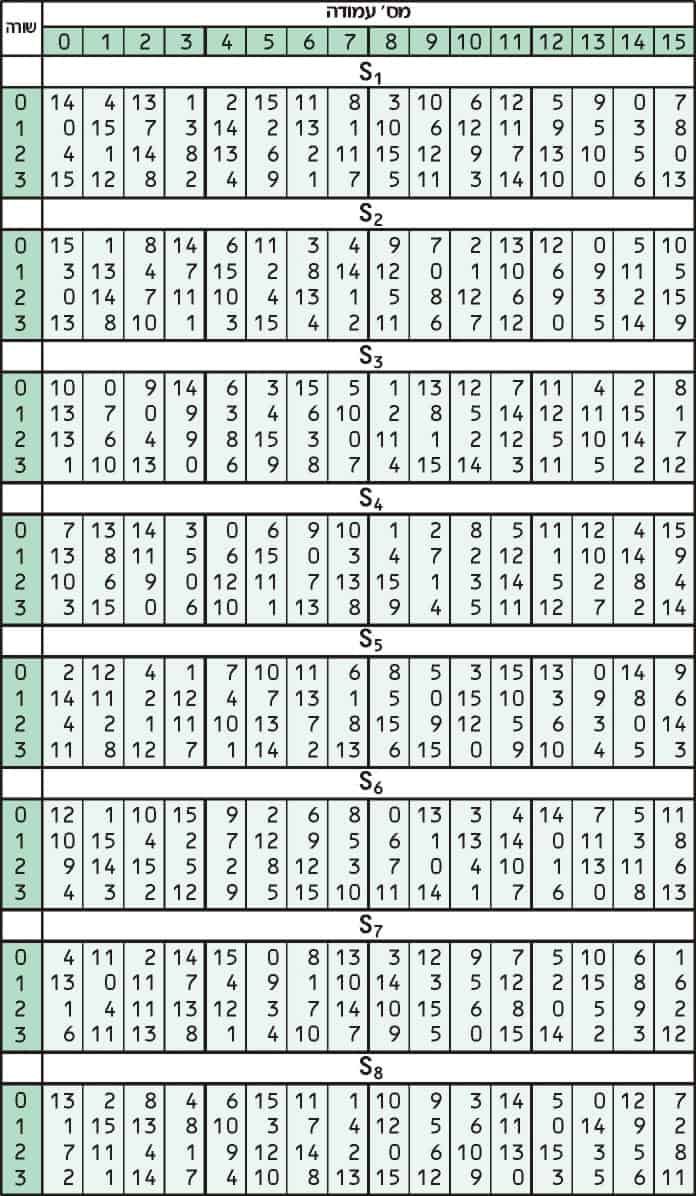
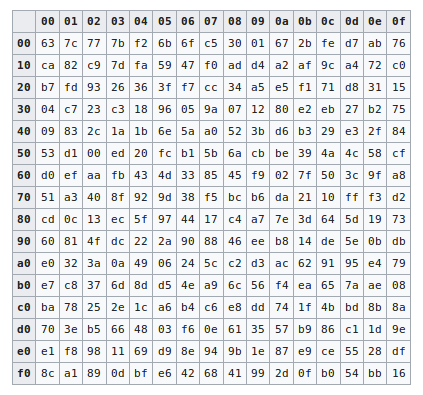
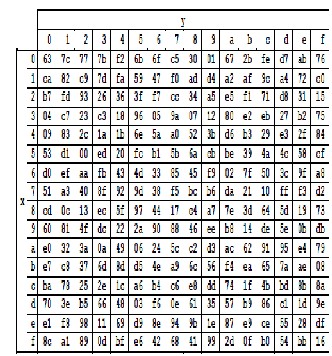
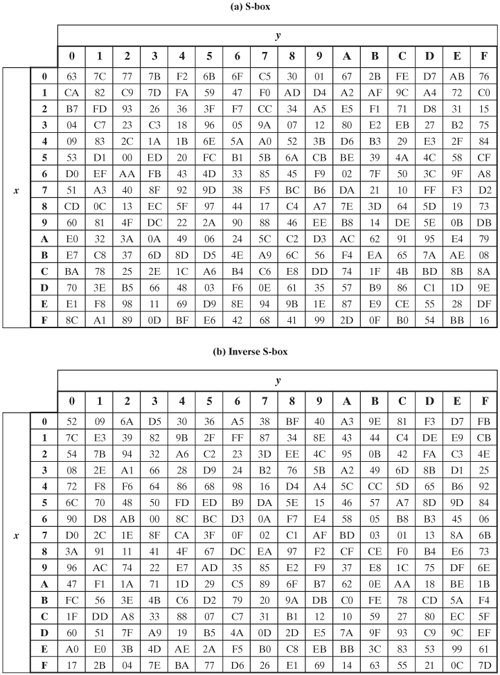
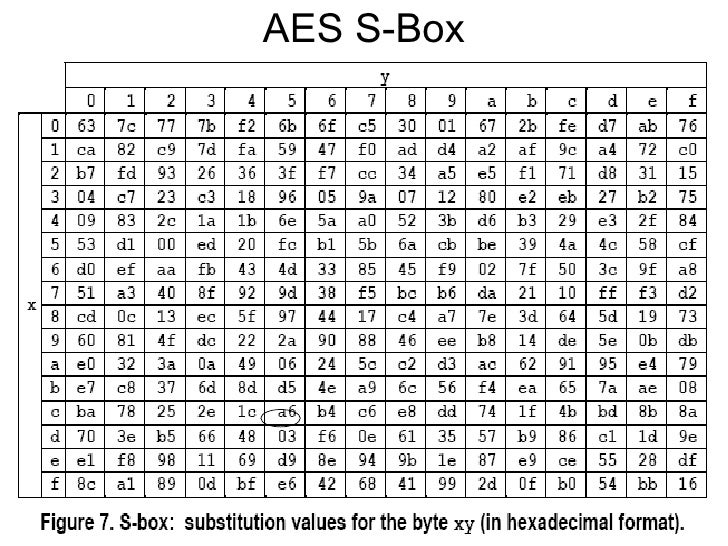
Chapter 7 The AES Algorithm Figure 71Overall structure of the AES algorithm 73 Substitute Bytes This stage (known as SubBytes) is simply a table lookup using a 16×16matrix of byte values called an sbox This matrix consists of all the possible combinations of an 8bit sequence (28= 16 × 16 = 256).

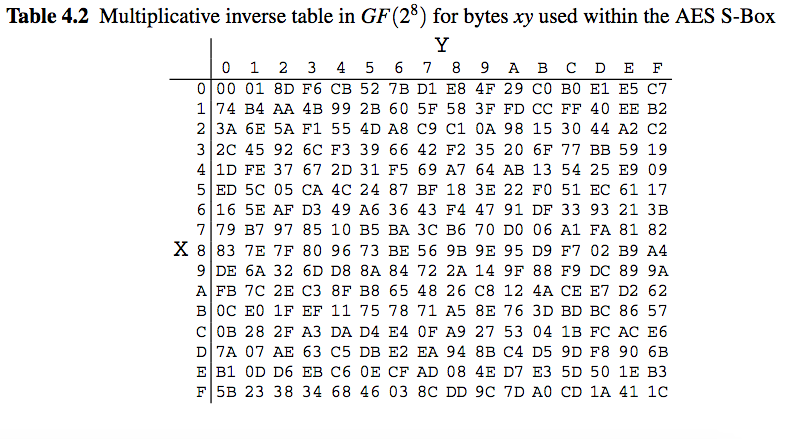
S box table for aes. Question Using The Multiplicative Inversion Table Shown Below (which Is Used As Part Of AES Sbox), (a) Find The Inverse Of Hex Entry ‘F3' From The Table (as You Know, 'F' Is For The Vertical Axis X And '3' Is For The Horizontal Axis Y) (b) For Verification, Perform A GF(23) Multiplication Of Input And Output Polynomials Using The Irreducible Polynomial Of. As Sbox in AES is in 𝐺𝐹 (28), the optimal value of nonlinearity is 1 It is observed from Table 5 that the proposed Sbox has the ability if evaluated in terms of nonlinearity analysis 33 Bit independence criterion A cryptographic design essentially carries the output bits independence criterion. Sbox,with look up table Sbox and Key expansion as modified when we change the initial key, that effectively providing a high resistance against differential cryptanalysis and especially the linear cryptanalysis The structure of the AES Sbox has been expanded and modified to be accordancewith the.
To speed up AES encryption, the SBox table is typically cache resident It contains 256 entries and each entry occupies 1 byte So the table fits into only 4 lines of cache The first two bits of the table index specify the cache line number and the remaining 6 bits specify the element within the line Types of Attacks and Attack Scenarios. 16 bytes == 128 bits == block size;. C matrix cuda aes lookup Share.
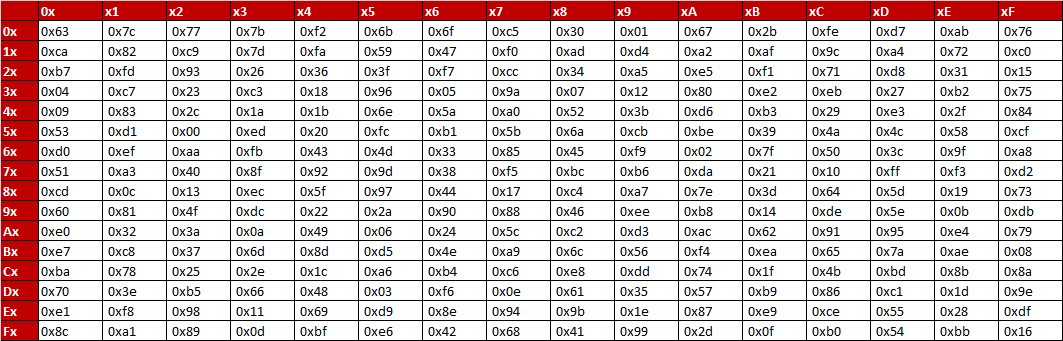
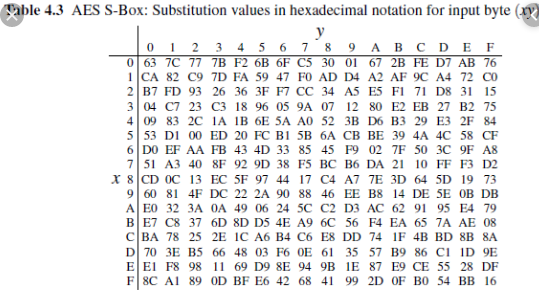
The AES SBox implements inverse multiplication in Galois Field 2 8 The AES SBox is shown in the Table below To read this Table, the byte input is broken into two 4bit halves The first half determines the row and the second half determines the column For example, the SBox transformation of 35 or 0x23 can be found in the cell at the intersection of the row labeled and the column labeled 03. Question Using The Multiplicative Inversion Table Shown Below (which Is Used As Part Of AES Sbox), (a) Find The Inverse Of Hex Entry ‘F3' From The Table (as You Know, 'F' Is For The Vertical Axis X And '3' Is For The Horizontal Axis Y) (b) For Verification, Perform A GF(23) Multiplication Of Input And Output Polynomials Using The Irreducible Polynomial Of. Sbox is used to substitute data Simply we can see Sbox as a lookup table The way to substitute bytes for block is like each block have 8bit data, and we can see first 4bit as row index and.
Eg the Blowfish and the Twofish encryption algorithms. 256 byte lookup table (Rijndael SBox) and AES with 16 byte SBox (Anubis SBox) Optimized and synthesized VHDL code is used for AES encryption Xilinx ISE 132i software is used for VHDL code implementation and Modelsim simulator is used for the simulation Keywords AES(Advanced Encryption Standard ), Rijndael, Cryptography, VHDL. All operations in a round of AES are invertible;.
Would it be wise to implement AES without lookup tables here?. Advanced Encryption Standard (AES) is a block cipher system which widely used in cryptographic application Substitution box (Sbox), nonlinear substitution operation, is the main factor of the. In general, an SBox takes some number of input bits, m, and transforms them into some number of output bits, n an m×n SBox can be implemented as a lookup table with 2 m words of n bits each Fixed tables are normally used, as in the Data Encryption Standard (DES), but in some ciphers the tables are generated dynamically from the key ;.
Sbox is the heart of every block cipher cryptosystem In AES Sbox characterizes the nonlinearity of the whole algorithm Basically, 8*8 Sbox is a function from GF(2 8) to GF(2 8), where GF(2 8) is a finite field of order 256 In other words, we can say that an 8*8 Sbox is the combination of eight different Boolean functions. ADVANCED ENCRYPTION STANDARD (AES) Federal Information Processing Standards Publications (FIPS PUBS) are issued by the National ADVANCED ENCRYPTION STANDARD (AES) Table of Contents 1 Sbox substitution values for the byte xy (in hexadecimal format). Sbox The 48bit output obtained by Xor step is reduced to 32 bit again Pbox Here the 32bit result obtained from Sbox is again permuted, which result in 32bit permuted output Definition of AES (Advanced Encryption Standard) Advanced Encryption Standard (AES) is also a symmetric key block cipher.
Rijndael's Sbox is a frequently used operation in AES encryption and decryption It is typically implemented as a 256byte lookup table That's fast, but means you need to enumerate a 256byte lookup table in your code I bet someone in this crowd could do it with less code, given the underlying mathematical structure. How can I verify that if the SBox input is the byte 93 (expressed in hex), then the SBox output is DC?. In the AES, the Sbox generate two transformations in the Galois fields GF(2) and GF(28) Sbox is a nonlinear transformation where each byte of the State is replaced by another byte using the substitution table The first transformation Sbox finds the multiplication inverse of the byte in the field GF(28) Since it is a algebraic expression, it.
In the AES, the Sbox generate two transformations in the Galois fields GF(2) and GF(28) Sbox is a nonlinear transformation where each byte of the State is replaced by another byte using the substitution table The first transformation Sbox finds the multiplication inverse of the byte in the field GF(28) Since it is a algebraic expression, it. The only thing I recognize is the mixcolumn part constant matrix, as well as the Sbox matrix Edit Now that someone pointed it out how can a lookup implementation be actually slower?. Substitute each entry (byte) of current state matrix by corresponding entry in AES SBox for instance byte 6E is substituted by entry of SBox in row 6 and column E, ie, by 9F this leads to new State Matrix 0 B B @ 63 EB 9F A0 C0 2F 93 92 AB 30 AF C7 CB 2B 1 C C A this nonlinear layer is for resistance to di erential and linear.
Question Using The Multiplicative Inversion Table Shown Below (which Is Used As Part Of AES Sbox), (a) Find The Inverse Of Hex Entry ‘F3' From The Table (as You Know, 'F' Is For The Vertical Axis X And '3' Is For The Horizontal Axis Y) (b) For Verification, Perform A GF(23) Multiplication Of Input And Output Polynomials Using The Irreducible Polynomial Of. Sbox The 48bit output obtained by Xor step is reduced to 32 bit again Pbox Here the 32bit result obtained from Sbox is again permuted, which result in 32bit permuted output Definition of AES (Advanced Encryption Standard) Advanced Encryption Standard (AES) is also a symmetric key block cipher. I mean, I can use a table to find the inverse, but how do I verify that it is indeed the inv.
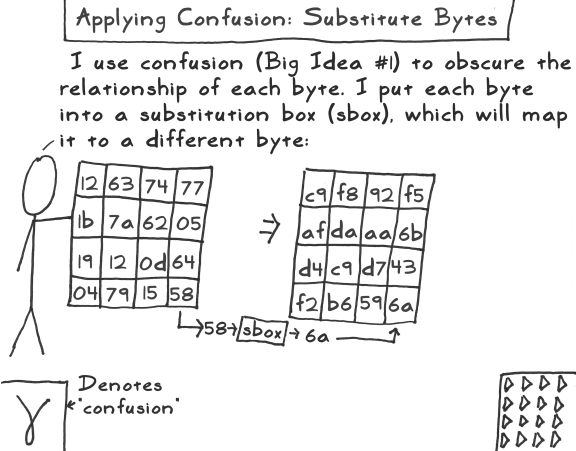
SubBytes – each byte in the state is replaced with a different byte according to the SBox lookup table. All operations in a round of AES are invertible;. The substitution table (SBox) of AdvancedEncryption Standard (AES)and its properties are key elements in cryptanalysis ciphering We aimhere to proposea straightforward method for the nonlinear transformation of AES SBoxconstruction The method reduces the steps needed to compute the multiplicativeinverse, and computes the matrices multiplication used in this transformation,without a need to use the characteristic matrix, and the result is a modernmethod constructing the SBox.
Chapter 7 The AES Algorithm Figure 71Overall structure of the AES algorithm 73 Substitute Bytes This stage (known as SubBytes) is simply a table lookup using a 16×16matrix of byte values called an sbox This matrix consists of all the possible combinations of an 8bit sequence (28= 16 × 16 = 256). 93 THE DES SBOXES, PBOX, AND INITIAL PERMUTATION (IP) Tables 94 to 911 specify the seven DES Sboxes, each with a 6bit input (x0, x1, Selection from Computer Security and Cryptography Book. Now, the AES algorithm substitutes every byte with a code according to a preestablished table called the Rijndael Sbox It looks like this It looks like this According to the table, an element like 19 becomes d4, e9 becomes 1a, and so on.
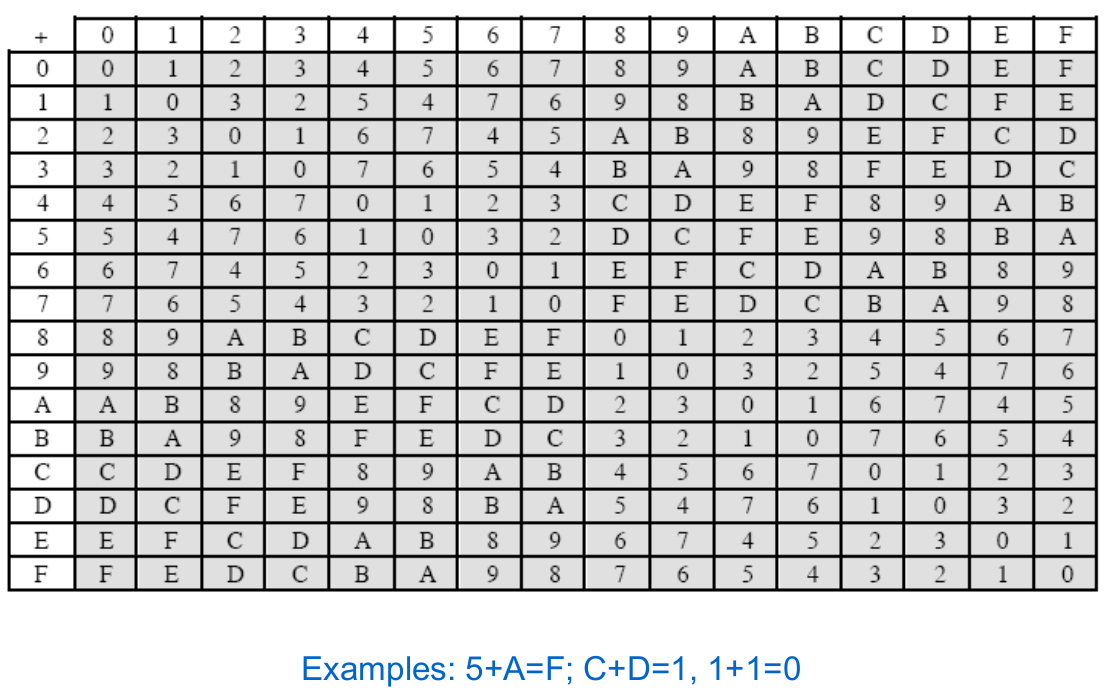
The only thing I recognize is the mixcolumn part constant matrix, as well as the Sbox matrix Edit Now that someone pointed it out how can a lookup implementation be actually slower?. AddRoundKey – each byte of the round key is combined with the corresponding byte in the state using XOR;. Sbox and pbox are the technologies that are used in cryptographic algorithms This is just small explanation about the Sbox used by the AES cryptographic algorithm The Sbox is generated by determining the multiplicative inverse for a given number in Rijndael's Galois Field The multiplicative inverse is then transformed using the following affine transformation matrix.
In memory method, ROM based LUT (Lookup table) is used to compute the Sbox that utilizes more memory, which increases area, power of AES and thus disadvantage of this is unbreakable delay and latency because of finite time of the architecture. I mean, I can use a table to find the inverse, but how do I verify that it is indeed the inv. Would it be wise to implement AES without lookup tables here?.
AES operates on a 4×4 matrix referred to as the state;. A compact AES algorithm with combinational logic based Sbox is implemented on Spartan 3 FPGA Proposed design occupies 680 slices AES ALGORITHMThe Advanced Encryption Standard is a subcategory of much larger encryption algorithm known as Rijndael. Single pipeline AES 128 bit encryption using Sbox as Look up table aneels3/AES128.
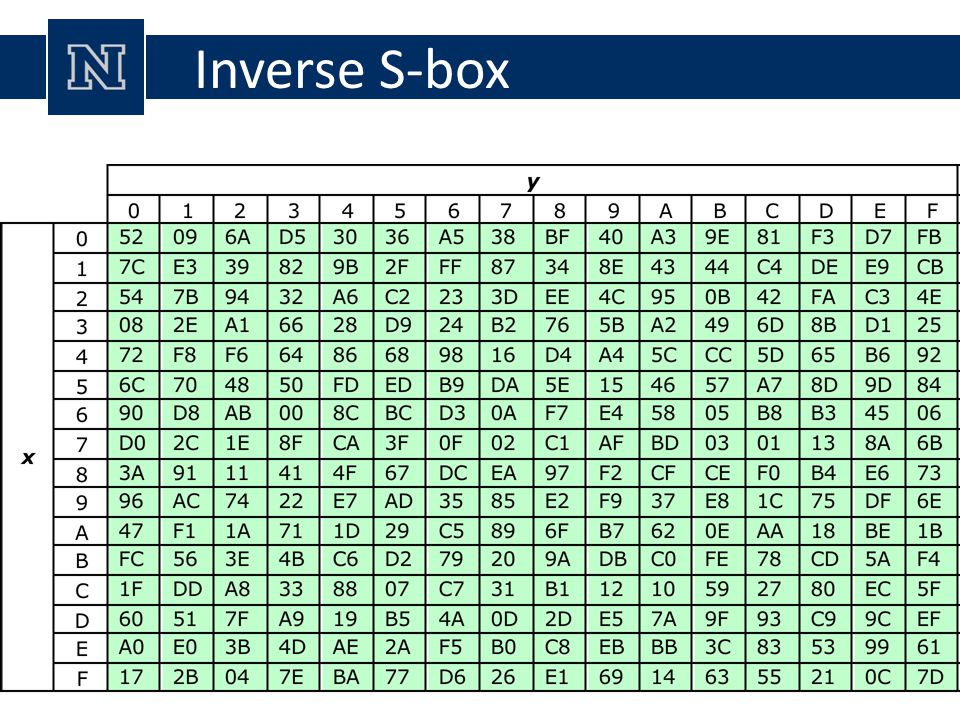
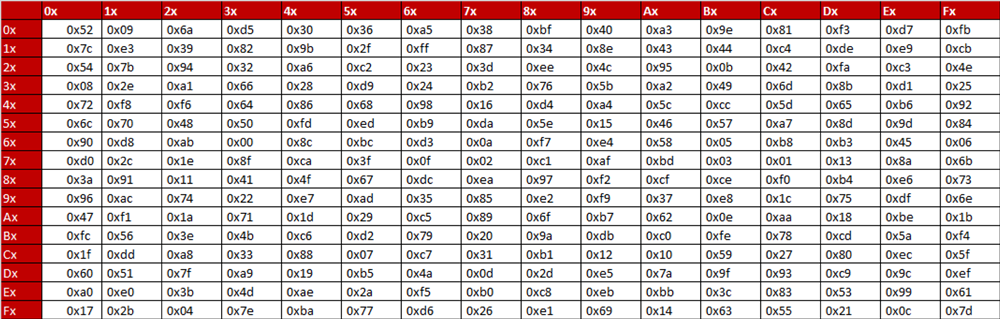
Single pipeline AES 128 bit encryption using Sbox as Look up table aneels3/AES128. To speed up AES encryption, the SBox table is typically cache resident It contains 256 entries and each entry occupies 1 byte So the table fits into only 4 lines of cache The first two bits of the table index specify the cache line number and the remaining 6 bits specify the element within the line. The inverse Sbox is simply the Sbox run in reverse For example, the inverse Sbox of 0xdb is 0x9f It is calculated by first calculating the inverse affine transformation of the input value, followed by the multiplicative inverse The inverse affine transformation is as follows The following table represents Rijndael's inverse Sbox.
AddRoundKey – each byte of the round key is combined with the corresponding byte in the state using XOR;. How can I verify that if the SBox input is the byte 93 (expressed in hex), then the SBox output is DC?. SubBytes – each byte in the state is replaced with a different byte according to the SBox lookup table.
AES operates on a 4×4 matrix referred to as the state;. I mean, I can use a table to find the inverse, but how do I verify that it is indeed the inv. Advanced Encryption Standard (AES) is a block cipher system which widely used in cryptographic application Substitution box (Sbox), nonlinear substitution operation, is the main factor of the.
How can I verify that if the SBox input is the byte 93 (expressed in hex), then the SBox output is DC?. Advanced Encryption Standard (AES) block cipher system is widely used in cryptographic applications A nonlinear substitution operation is the main factor of the AES cipher system strength The purpose of the proposed approach is to generate the random Sboxes changing for every change of the secret key. But for hardware implementations of AES, there is one drawback of the table lookup approach to the Sbox function each copy of the table requires 256 bytes of storage, along with the circuitry to address the table and fetch the results Each of the 16 bytes in a block can go through the Sbox function independently, and so could be processed in parallel for the byte substitution step.
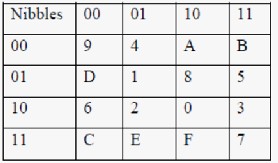
Now we construct an SBox object for the 4bit small scale AES SBox (cf sagecryptomqsr ) sage sr = mqSR(1,1,1,4, allow_zero_inversions=True) sage S = SBox( srsub_byte(e) for e in list(srk)) sage S (6, 5, 2, 9, 4, 7, 3, 12, 14, 15, 10, 0, 8, 1, 13, 11) AUTHORS. The substitution table (SBox) of AdvancedEncryption Standard (AES)and its properties are key elements in cryptanalysis ciphering We aimhere to proposea straightforward method for the nonlinear transformation of AES SBoxconstruction The method reduces the steps needed to compute the multiplicativeinverse, and computes the matrices multiplication used in this transformation,without a need to use the characteristic matrix, and the result is a modernmethod constructing the SBox. C matrix cuda aes lookup Share.
SBox The substitution step in DES requires bitlevel access to the block coming into a round On the other hand, all operations in AES are purely bytelevel, which makes for convenient and fast software implementation of AES About the security of AES, considering how many years have passed since the cipher was introduced in 01, all of the. Substitution tables for Sbox and InvSbox It can be implemented by using memory method and memoryless method In memory method, ROM based LUT (Lookup table) is used to compute the Sbox that utilizes more memory, which increases area, power of AES and thus. The Rijndael Sbox is a substitution box ( lookup table) used in the Rijndael cipher, which the Advanced Encryption Standard (AES) cryptographic algorithm is based on.
The AES is the primary instrument used for collecting export trade data, which are used by the Census Bureau for statistical purposes The AES record provides the means for collecting data on US exports Public Law of the Foreign Trade Relations Act of 03 authorizes th is collection Title 13, USC,. This paper is focusing on the most time consuming step of the AES algorithm This step is a NonLinear Byte Substitution that transforms some byte value into a new byte value through the use of an Sbox Substitution Table This table contains precomputed inverted values for each of the 256 8bit numbers (bytes) considered as elements of the Galois finite field GF(28). The construction of AES’s SBox is detailed in many places and much better than I could do What’s important here is that an Sbox is a lookup table which transforms each byte into a matching one The process is fully reversible with an Inverse SBox (used for decryption), such that SISb = ISSb = b Here is the resulting state after going through the SubBytes operation.

Ch05 Testbank Crypto6e
Solved C Points 6 Using Table 4 2 Of Gf 2 Determine Chegg Com

Aes Smaller Than S Box Springerprofessional De

An Algorithm For The Construction Of Substitution Box For Block Ciphers Based On Projective General Linear Group Aip Advances Vol 7 No 3

Pdf An Improved Aes S Box And Its Performance Analysis Semantic Scholar

Advanced Encryption Standard Aes With Dynamic Substitution Box
Implementation Of Simplified Aes Algorithm For Wireless Sensor Nodes On Fpga
Http Www Ijera Com Papers Vol3 Issue1 Iw Pdf

Design And Implementation Of Encryption Unit Based On Customized Aes Algorithm
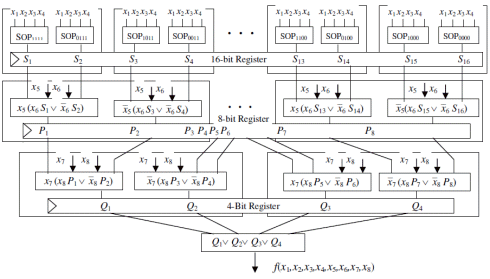
Pipeline Aes S Box Implementation Starting With Substitution Table

Aes Algorithm Flowchart 2 1 Byte Substitution Using S Box Table S Box Download Scientific Diagram

What Is Aes Encryption And How Does It Work Cybernews
2
Q Tbn And9gcspmz4pvvldpmuymanx3og7knpoleyoqjbf050lmlijs2yhcok3 Usqp Cau

New S Box Calculation For Rijndael Aes Based On An Artificial Neural Network
A Novel Byte Substitution Architecture For The Aes Cryptosystem
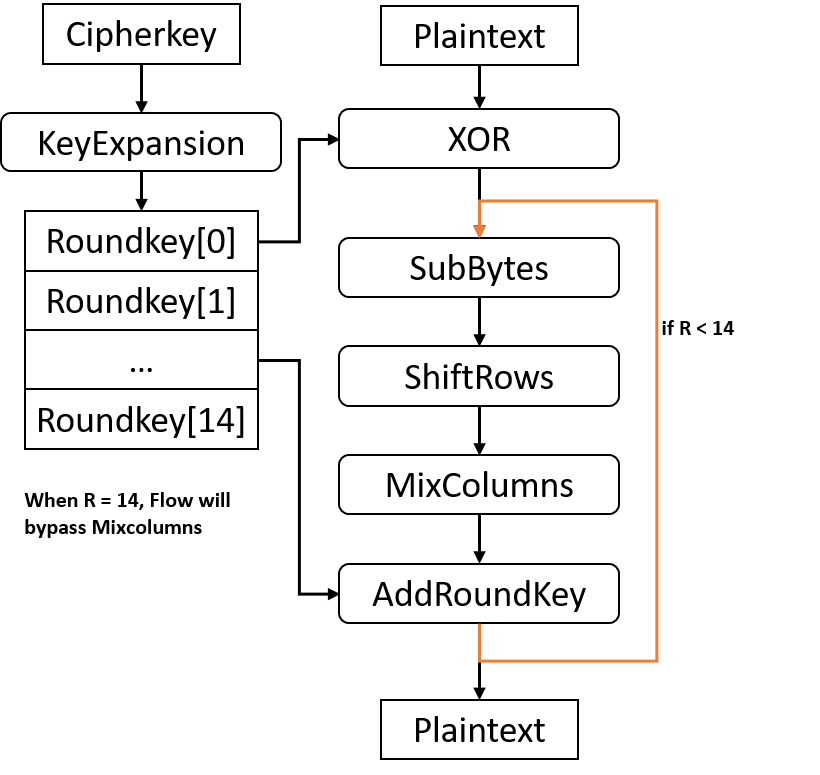
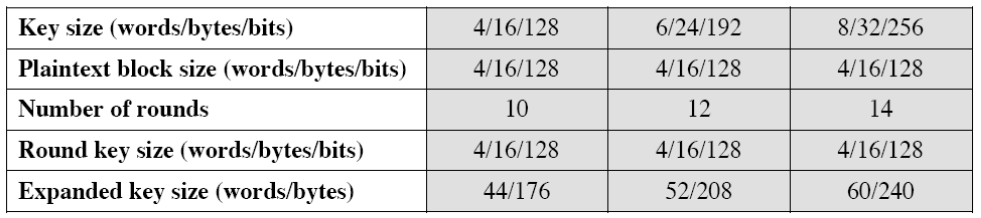
Es 128 192 256 Algorithm Processes Plain Data Blocks Of 128 Bits And Generates Cipher Data Blocks Of 128 Bits Using Cipher Keys Of 128 192 256 Bits

Achieving High Performance For Advanced Encryption Standard Aes Applications

New S Box Calculation For Rijndael Aes Based On An Artificial Neural Network
Www Mdpi Com 1099 4300 21 3 245 Pdf
Eprint Iacr Org 17 1161 Pdf
Http Www Um Es Docencia Jsimon Congresocripto Absautores Presentaciones Stoianov Pdf
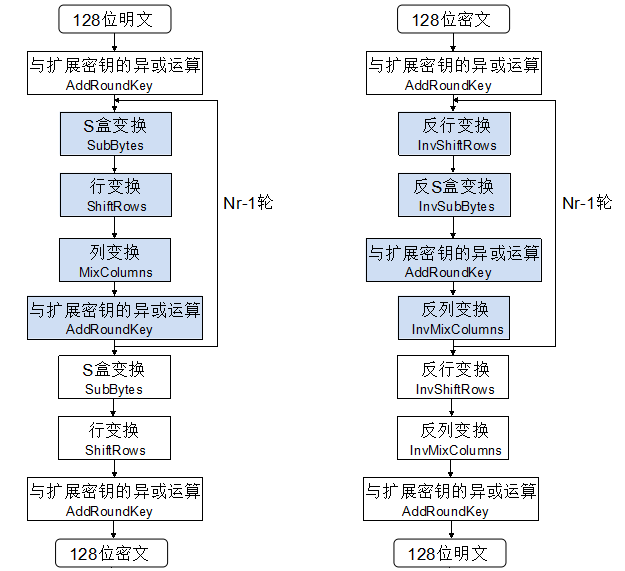
C Implementation Of Aes Encryption Algorithms
Dl Acm Org Doi Pdf 10 1145

Ece 5760
Eprint Iacr Org 18 1002 Pdf
Lecture 23 Symmetric Encryption Ppt Download
Ieeexplore Ieee Org Iel7 Pdf
Q Tbn And9gcq Raxfwj2ura1kadboki 0ic9uqbm48wdz6h9hhbtj3p64kk Usqp Cau
What Is 3des Encryption And How Does Des Work Comparitech

Table 1 From Dynamic Aes 128 With Key Dependent S Box Semantic Scholar

Secret Key Crypotography
Www2 Rivier Edu Journal Roaj Fall 10 J455 Selent Aes Pdf
Http Cse Iitkgp Ac In Debdeep Courses Iitkgp Crypto Slides Dc Pdf
9 Advanced Encryption Standard

Aes
Www Osti Gov Servlets Purl
Sect Ctf 17 Bad Aes
Design And Verification Of Aes Encryption With New Approach For S Box
1

Advanced Encryption Standard Aes Transformation Functions
Lirias Kuleuven Be Retrieve
Aes Encryption

S Box Substitution Box Youtube
9 Advanced Encryption Standard
Http Www Iaeme Com Masteradmin Uploadfolder Ijecet 07 01 001 Ijecet 07 01 001 Pdf

Finding Output Given An S Box Input Of 8 Bits Cryptography Stack Exchange

Aes Advanced Encryption Standard Anu Vazhayil

Aes S Box Performance And Comparison With Previous Work Download Table

Use Verilog To Implement The Field Multiplier For Chegg Com
Aes Encryption
Q Tbn And9gcrmq1uror0bzpl6mnp52butzzlkreaovkmephwit8vsl474qera Usqp Cau
Determine The Multiplicative Inverses Of 0d16 And Chegg Com
Section 5 2 The Aes Cipher Cryptography And Network Security 4th Edition

S Box Implementation Of Aes Is Not Side Channel Resistant Springerlink
Advanced Encryption Standard Wikipedia

Construction Of S8 Liu J S Boxes And Their Applications Sciencedirect
Arxiv Org Pdf 1908

New S Box Calculation For Rijndael Aes Based On An Artificial Neural Network

The Aes Rijndael S Box

Table 3 From Key Dependent S Box Generation In Aes Block Cipher System Semantic Scholar

Table 2 From An Algorithm For Key Dependent S Box Generation In Block Cipher System Semantic Scholar

Rijndael S Box Wikipedia
S Box Design Symmetric Ciphers And Hashes Modern Cryptography Applied Mathematics For Encryption And Informanion Security 16
Citeseerx Ist Psu Edu Viewdoc Download Doi 10 1 1 9 8099 Rep Rep1 Type Pdf

The Advanced Encryption Standard Aes Algorithm Commonlounge

Secret Key Crypotography
Network Security Lec4

Inverse S Box Substitution Values For The Byte Xy In Hexadecimal Format Download Scientific Diagram
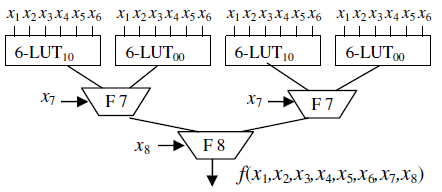
Pipeline Aes S Box Implementation Starting With Substitution Table
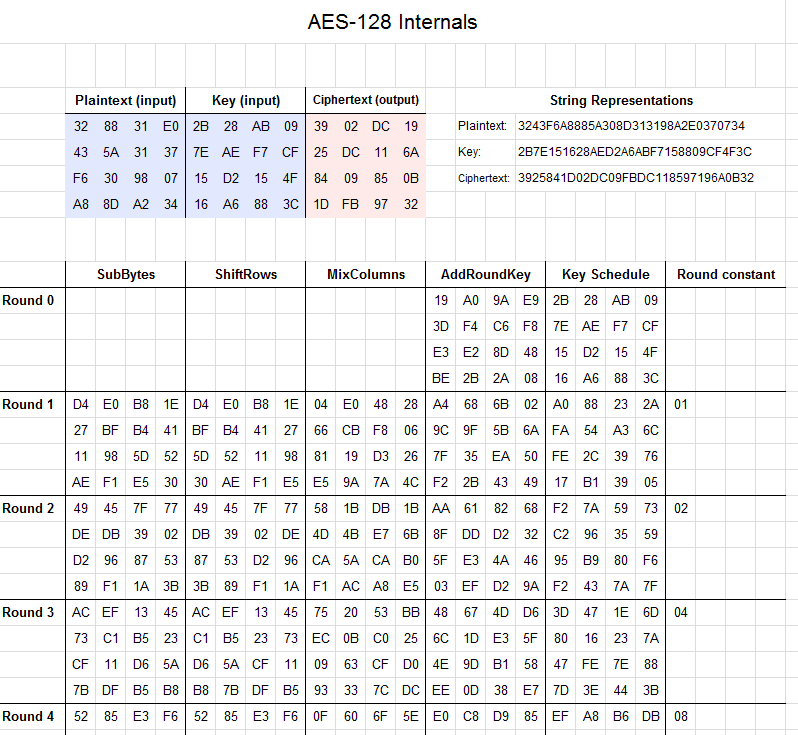
Aes Cipher Internals In Excel
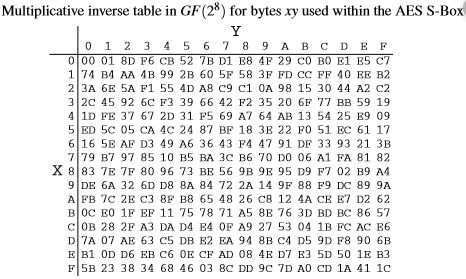
Determine The Multiplicative Inverses Of 0d16 And Chegg Com
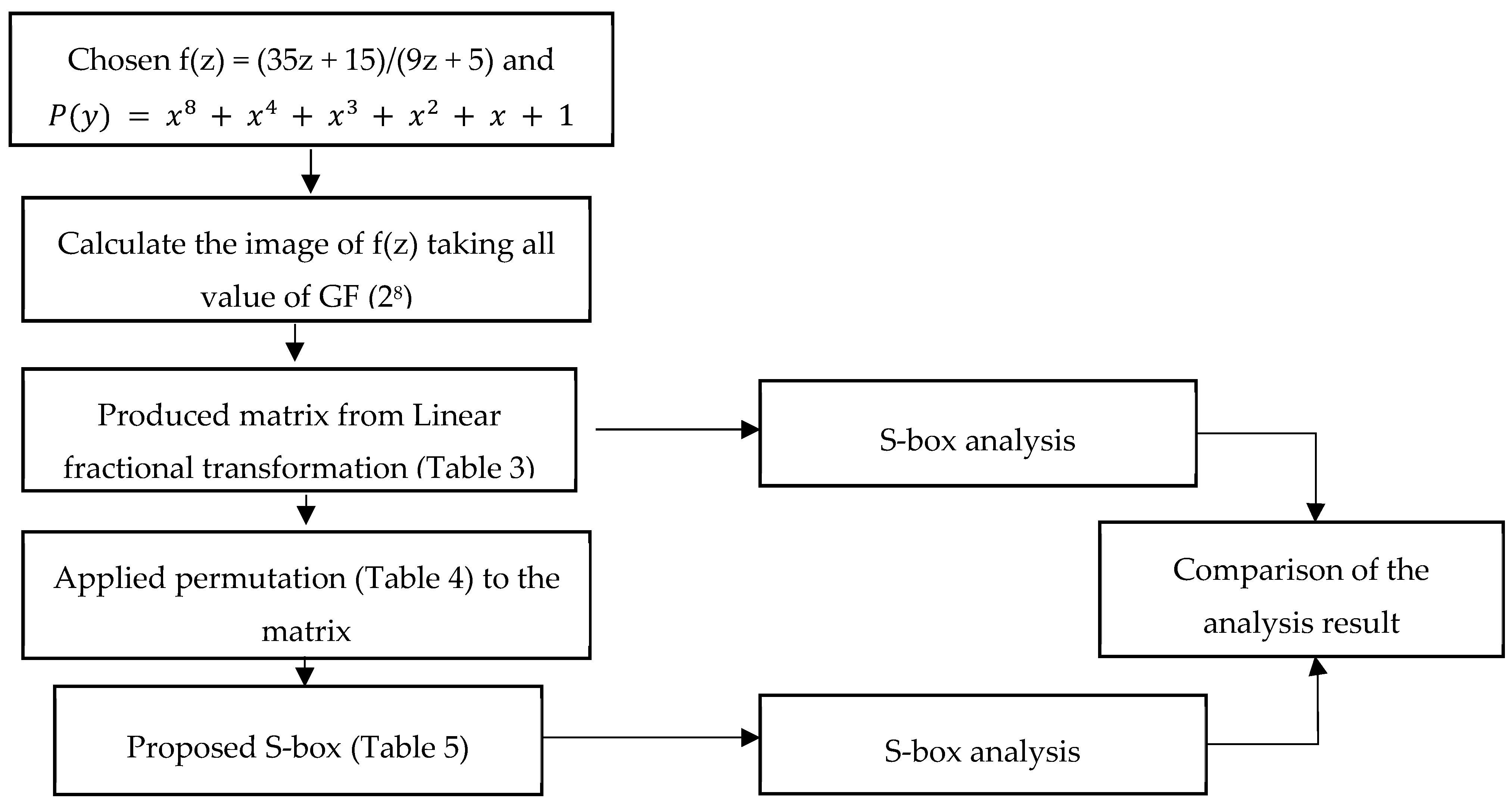
Symmetry Free Full Text S Box Construction Based On Linear Fractional Transformation And Permutation Function Html
Ieeexplore Ieee Org Iel5 Pdf

How Are S Box Calculated In S Aes Cryptography Stack Exchange
Www Irjet Net Archives V2 I8 Irjet V2i811 Pdf

Advanced Encryption Standard Aes Transformation Functions

The Advanced Encryption Standard Aes Algorithm Commonlounge

Table 1 From Enhancement Of Advanced Encryption Standard Aes Cryptographic Strength Via Generation Of Cipher Key Dependent S Box Semantic Scholar

Table 2 From Encryption Using Dual Key Transformation Based On Creation Of Multi S Boxes In Aes Algorithm Semantic Scholar
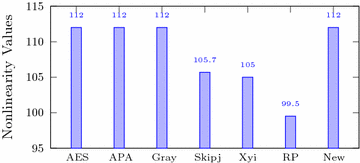
A Highly Nonlinear S Box Based On A Fractional Linear Transformation Springerplus Full Text

Aes S Box Rijndael S Box 16 Download Scientific Diagram

The Advanced Encryption Standard Aes Algorithm Commonlounge
Http Www Cs Man Ac Uk Banach Comp Info Courseslides Wk2 3 Aes Pdf

How Are The Aes Inverse S Boxes Calculated Cryptography Stack Exchange

Block Cipher Programmer Sought
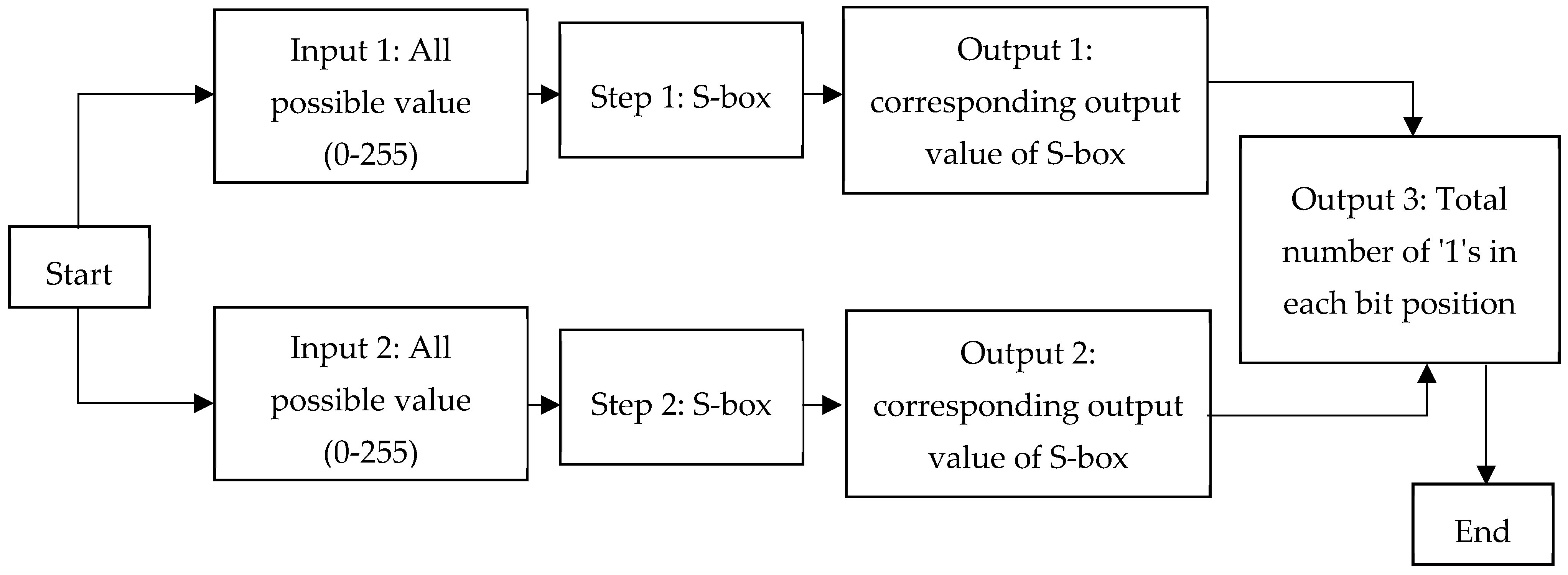
Symmetry Free Full Text S Box Construction Based On Linear Fractional Transformation And Permutation Function Html
Http Www Ijera Com Papers Vol3 Issue1 Iw Pdf
Http Citeseerx Ist Psu Edu Viewdoc Download Doi 10 1 1 227 7609 Rep Rep1 Type Pdf
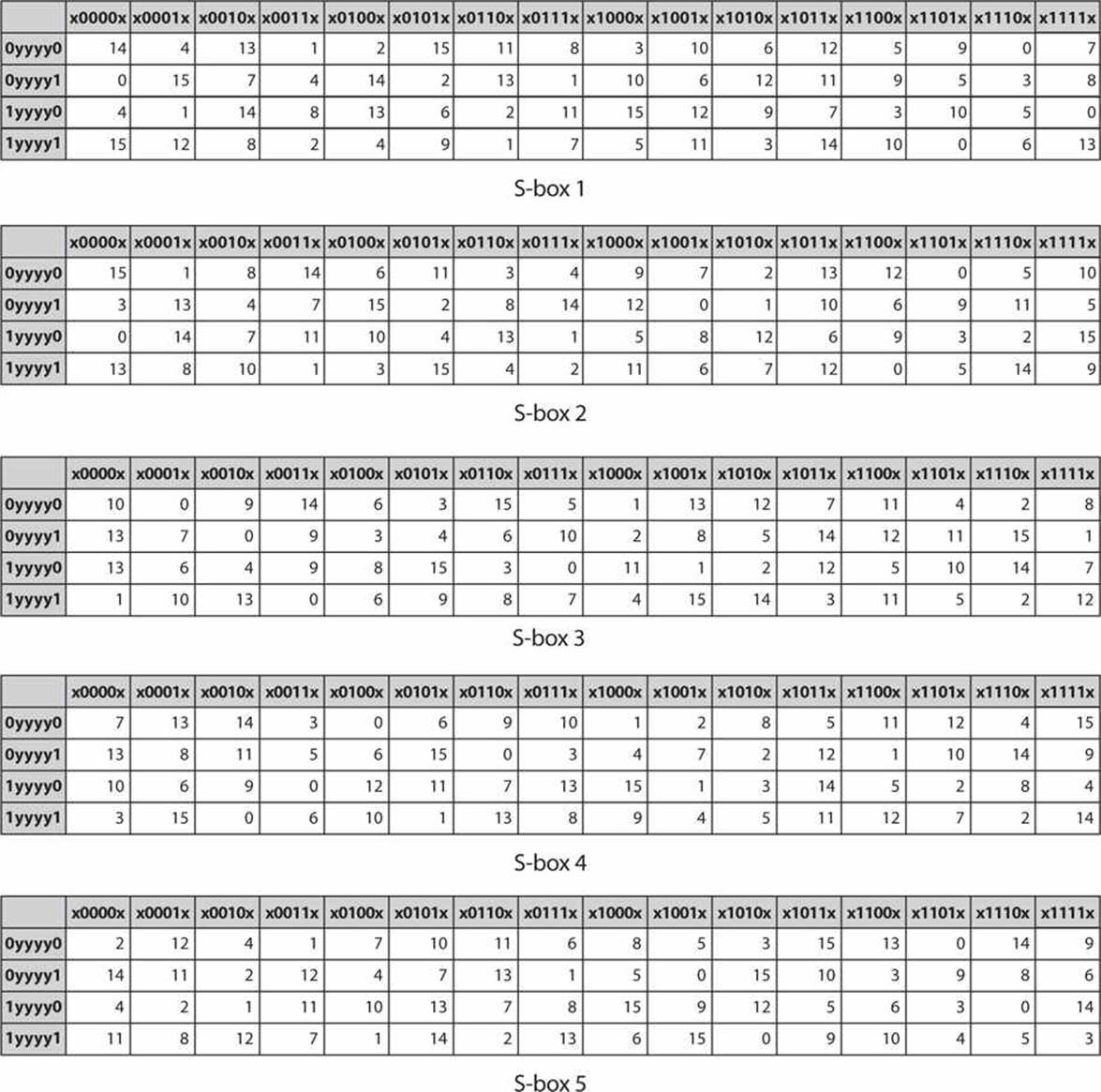
S Box Design Symmetric Ciphers And Hashes Modern Cryptography Applied Mathematics For Encryption And Informanion Security 16

3d Determine The Aes S Box Substitution Value For Which Is In Hex Youtube

Cryptography And Network Security Ppt Download

Achieving High Performance For Advanced Encryption Standard Aes Applications
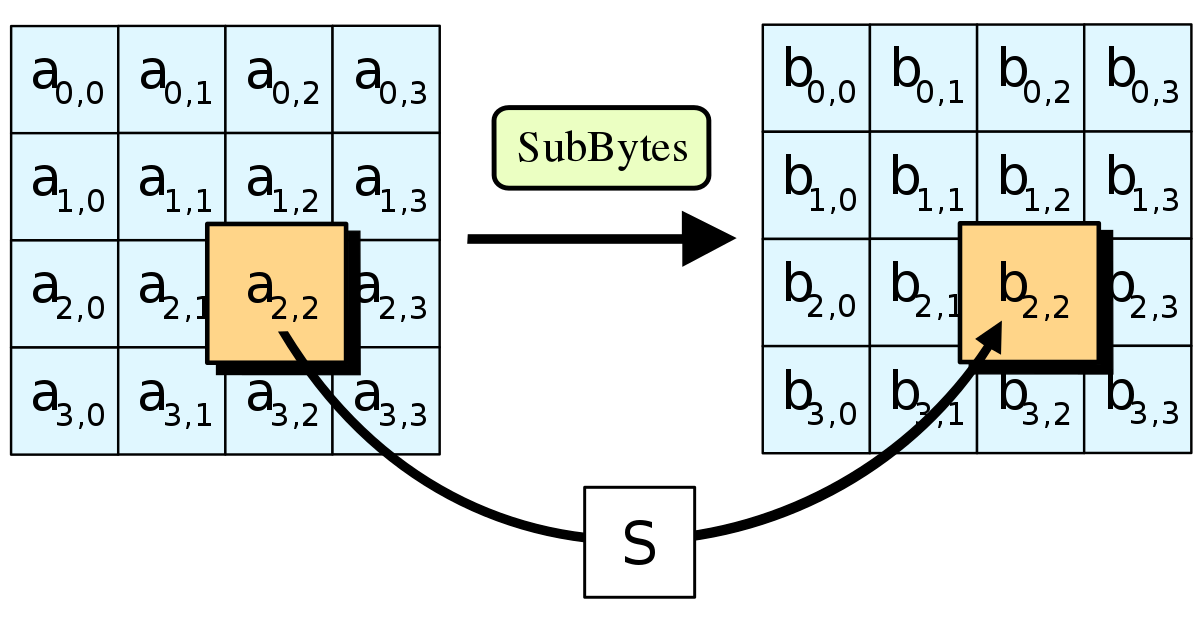
Advanced Encryption Standard Wikipedia

New S Box Calculation For Rijndael Aes Based On An Artificial Neural Network

Ece 5760

Table 2 From Key Dependent S Box Generation In Aes Block Cipher System Semantic Scholar
Http Www Ijera Com Papers Vol3 Issue1 Iw Pdf



