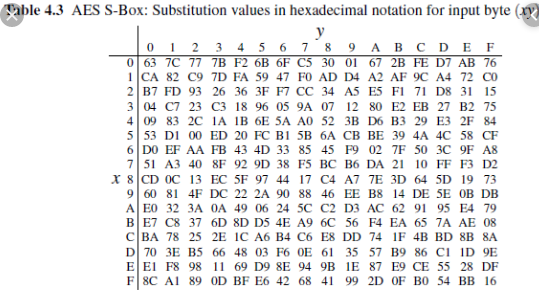
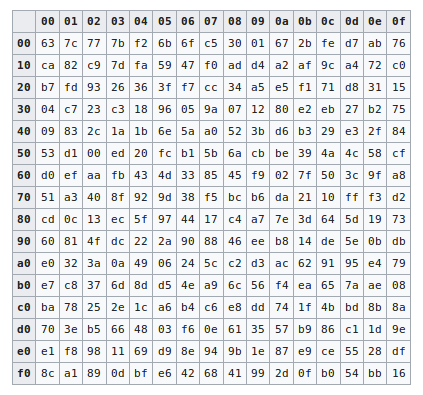
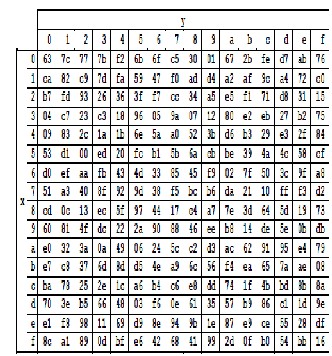
Aes S Box Table
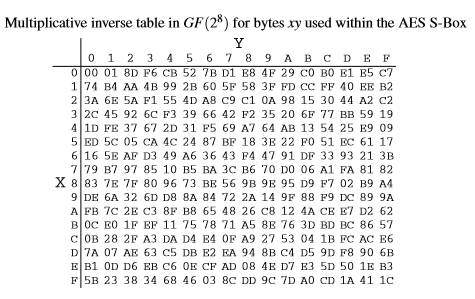
Determine The Multiplicative Inverses Of 0d16 And Chegg Com

Table 3 From Key Dependent S Box Generation In Aes Block Cipher System Semantic Scholar

Aes Advanced Encryption Standard Anu Vazhayil

Plot Of The Difference Of The S Boxes Elements Table 2 And Table 3 Download Scientific Diagram

Design And Implementation Of Encryption Unit Based On Customized Aes Algorithm

Fpga Implementation Results For Aes S Box Module Download Table
Rijndael's Sbox is a frequently used operation in AES encryption and decryption It is typically implemented as a 256byte lookup table That's fast, but means you need to enumerate a 256byte lookup table in your code I bet someone in this crowd could do it with less code, given the underlying mathematical structure.

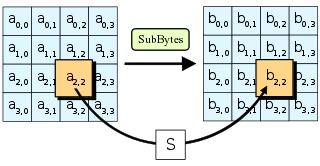
Aes s box table. Every form of 2 • S i, j will be mapped to S − Box • 2i, j and 3 • S i, j will be mapped to S − Box • 3i, j elements and change it based on their coordinate table Author name / Procedia Computer Science 00 (17) 000–000 5 Our improvement combination steps as follows. This paper is focusing on the most time consuming step of the AES algorithm This step is a NonLinear Byte Substitution that transforms some byte value into a new byte value through the use of an Sbox Substitution Table This table contains precomputed inverted values for each of the 256 8bit numbers (bytes) considered as elements of the Galois finite field GF(28). The SBox table of AES is taken as a lookup table to substitute an input byte by another, this table is constructed using a nonlinear transformation depends on the usual method taking more calculation steps to give the corresponding byte.
Culation, and so many current implementations use a table of the Sbox function output This table lookup method is fast and easy to implement But for hardware implementations of AES, there is one drawback of the table lookup approach to the Sbox function each copy of the table requires. The Rijndael Sbox is a substitution box (lookup table) used in the Rijndael cipher, which the Advanced Encryption Standard (AES) cryptographic algorithm is based on. As Sbox in AES is in 𝐺𝐹 (28), the optimal value of nonlinearity is 1 It is observed from Table 5 that the proposed Sbox has the ability if evaluated in terms of nonlinearity analysis 33 Bit independence criterion A cryptographic design essentially carries the output bits independence criterion.
Single pipeline AES 128 bit encryption using Sbox as Look up table aneels3/AES128. Sbox and pbox are the technologies that are used in cryptographic algorithms This is just small explanation about the Sbox used by the AES cryptographic algorithm The Sbox is generated by determining the multiplicative inverse for a given n. So, we have 16 SBoxes that each operate on one byte Each SBox operates in parallel, and each is identical We’ll skip the mathematical details, but the SBox substitution table is precomputed using Galois Field arithmetic Because the table is fixed by the AES standard, we can efficiently perform substitutions without the complex.
Let S be an NxM Sbox Let δ be the largest value in the differential distribution table of the Sbox (not taking into account first row and column) Then δ {α β} α α β = ⊕ ⊕ = ∈ ≠ ∈ max max# ( ) ( ) 2, 0, 2 x S x S x VN VM (16) Let S be an NxM Sbox Let λ be the largest value in the linear distribution table of the Sbox. Advanced Encryption Standard (AES) block cipher system is widely used in cryptographic applications A nonlinear substitution operation is the main factor of the AES cipher system strength The purpose of the proposed approach is to generate the random Sboxes changing for every change of the secret key. The 16 input bytes are substituted by looking up a fixed table (Sbox) given in design The result is in a matrix of four rows and four columns.
The SBox table of AES is taken as a lookup table to substitute an input byte by another, this table is constructed using a nonlinear transformation depends on the usual method taking more calculation steps to give the corresponding byte. Would it be wise to implement AES without lookup tables here?. Sbox is used to substitute data Simply we can see Sbox as a lookup table The way to substitute bytes for block is like each block have 8bit data, and we can see first 4bit as row index and.
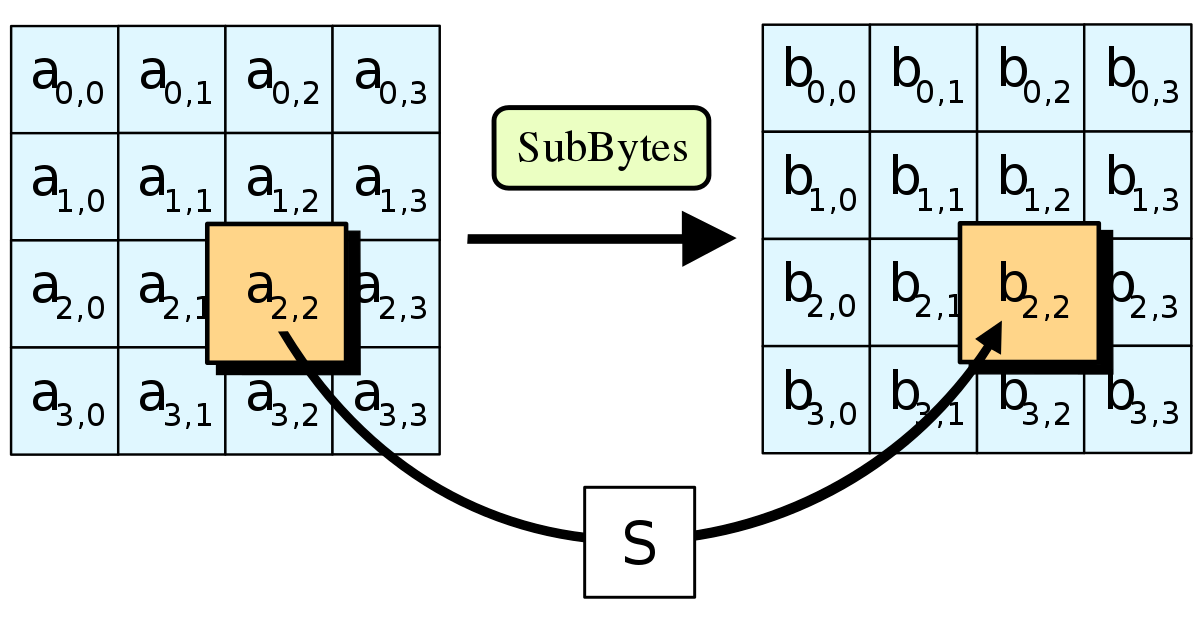
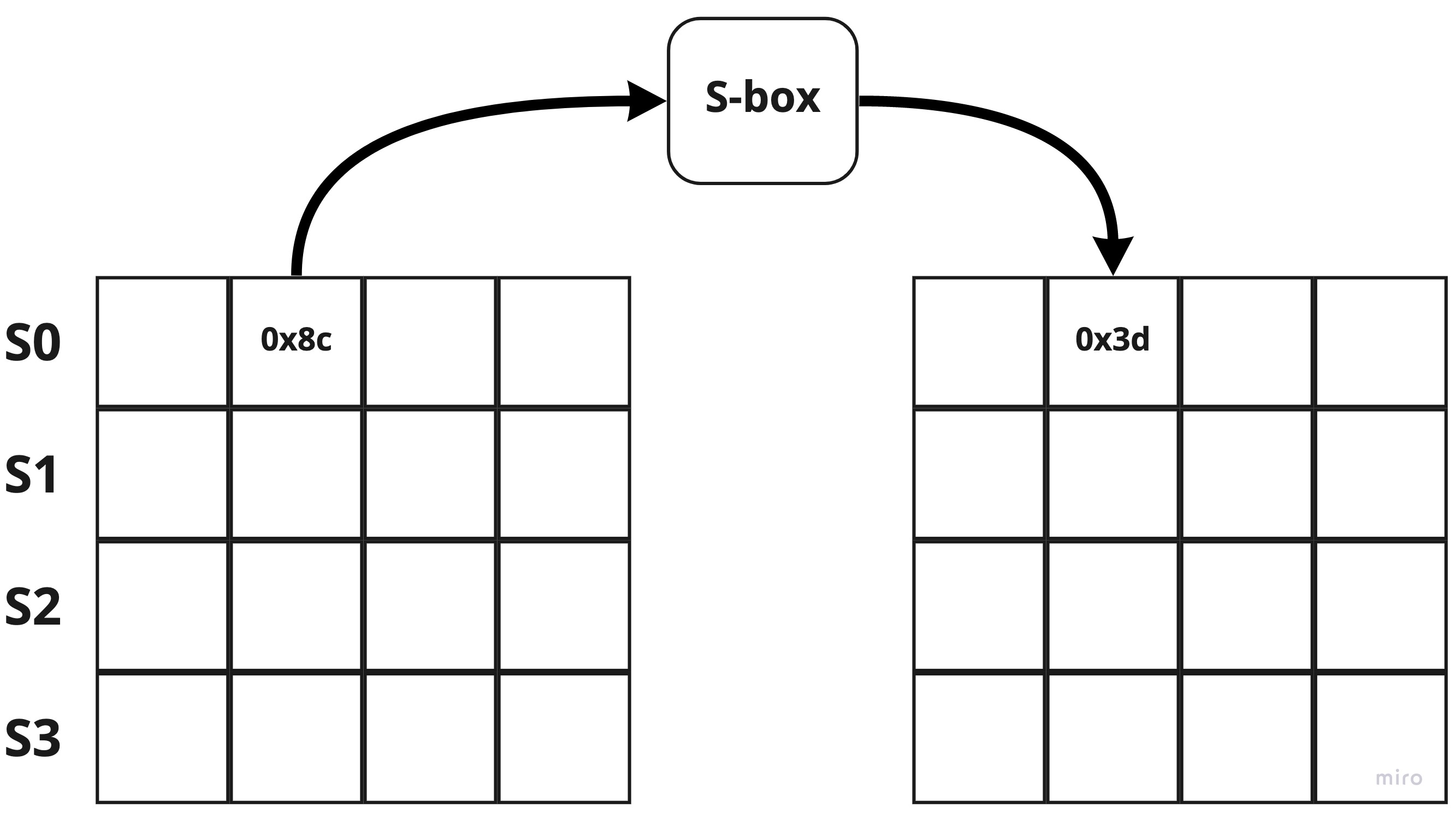
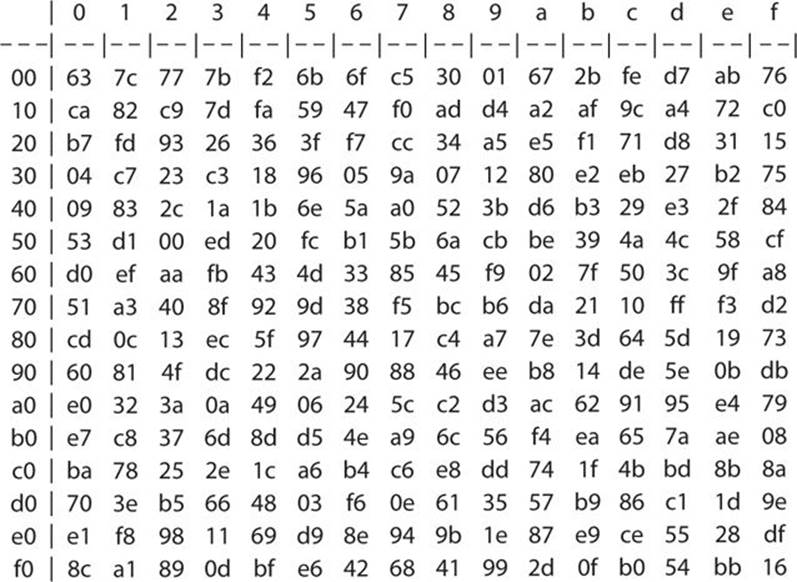
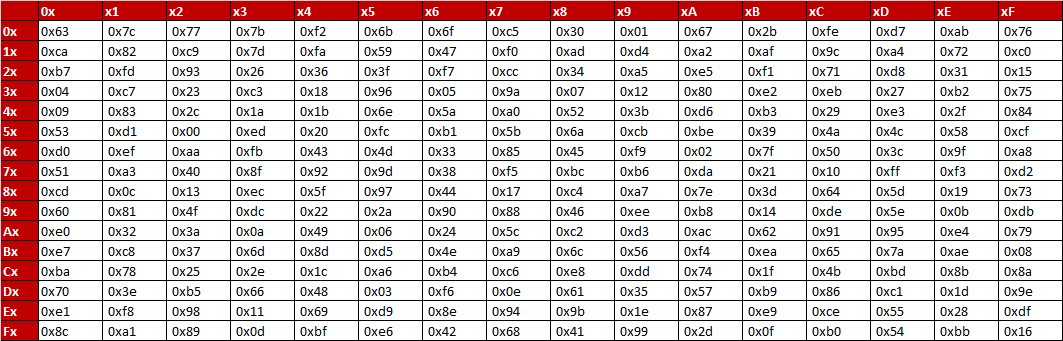
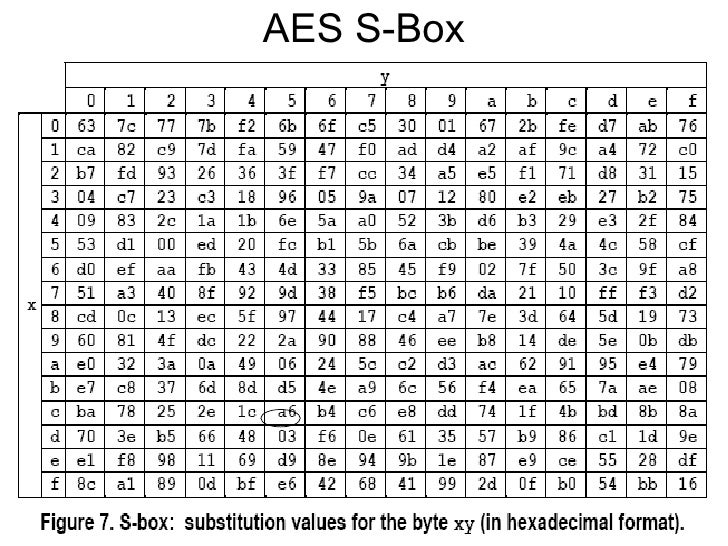
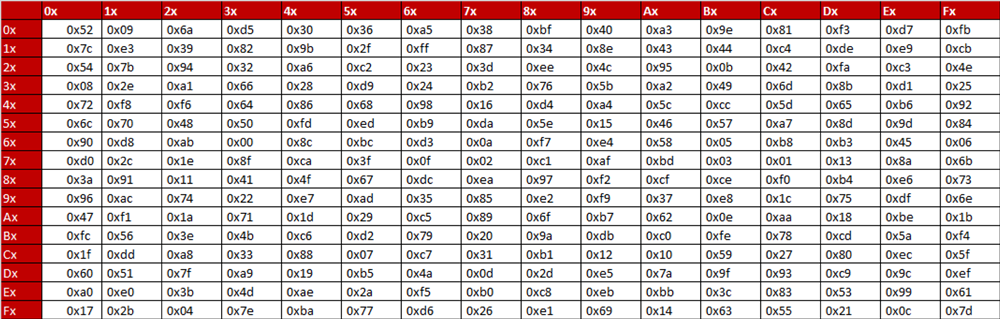
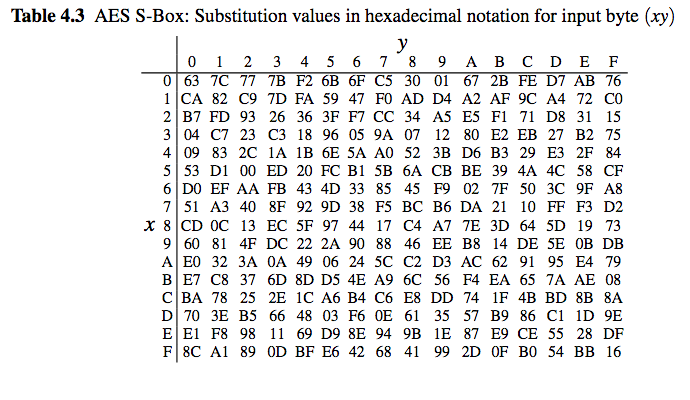
In memory method, ROM based LUT (Lookup table) is used to compute the Sbox that utilizes more memory, which increases area, power of AES and thus disadvantage of this is unbreakable delay and latency because of finite time of the architecture. The 16 input bytes are substituted by looking up a fixed table (Sbox) given in design The result is in a matrix of four rows and four columns. AES defines a 16 * 16 matrix of byte values, called an Sbox (Table 52a), that contains a permutation of all possible 256 8bit values Each individual byte of State is mapped into a new byte in the following way The leftmost 4 bits of the byte are used as a row value and the rightmost 4 bits are used as a column value.
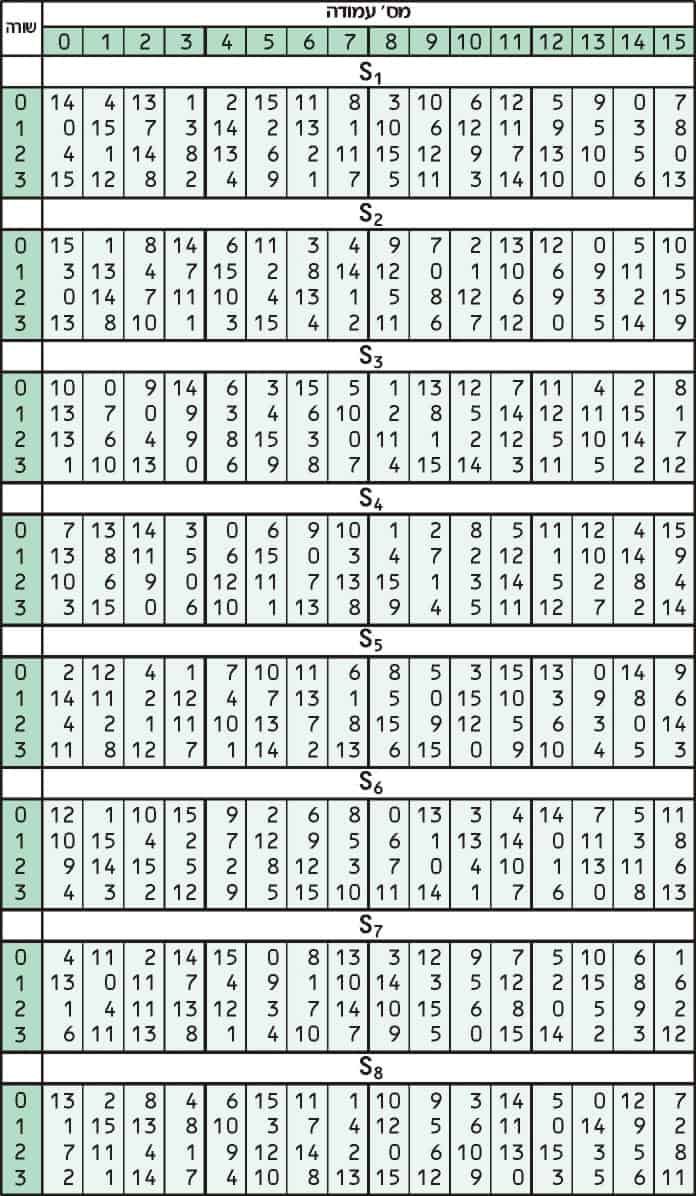
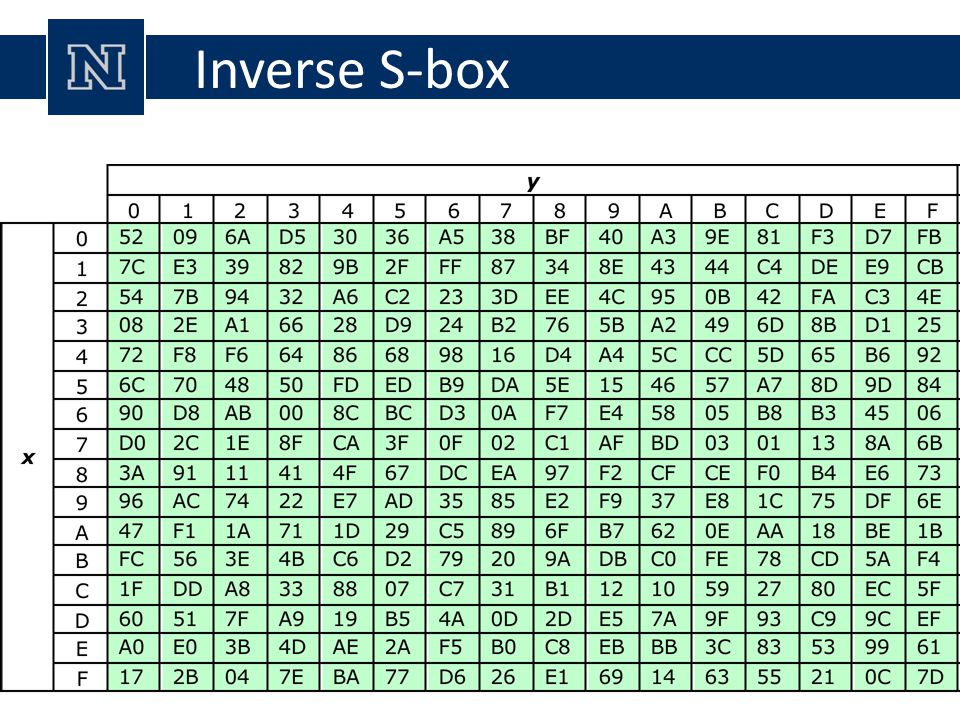
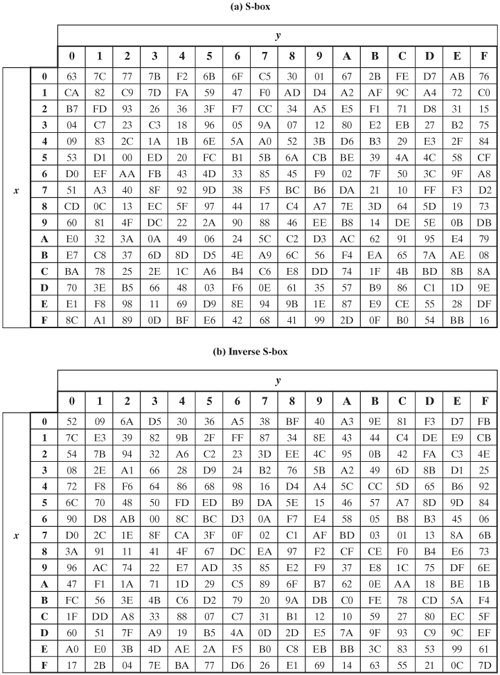
Table 74 shows the two sboxes and it can be verified that this is in fact the case 62 Chapter 7 The AES Algorithm The sbox is designed to be resistant to known cryptanalytic attacks. ADVANCED ENCRYPTION STANDARD (AES) Federal Information Processing Standards Publications (FIPS PUBS) are issued by the National ADVANCED ENCRYPTION STANDARD (AES) Table of Contents 1 Sbox substitution values for the byte xy (in hexadecimal format). The inverse Sbox is simply the Sbox run in reverse For example, the inverse Sbox of 0xdb is 0x9f It is calculated by first calculating the inverse affine transformation of the input value, followed by the multiplicative inverse The inverse affine transformation is as follows The following table represents Rijndael's inverse Sbox.
Advanced Encryption Standard (AES) which works on a 128 bit data encrypting it with 128, 192 or 256 bits of keys for ensuring security In this paper, we compare AES encryption with two different SBoxes Sbox with 256 byte lookup table (Rijndael SBox) and AES with 16 byte SBox (Anubis SBox). Advanced Encryption Standard (AES) block cipher system is widely used in cryptographic applications A nonlinear substitution operation is the main factor of the AES cipher system strength The purpose of the proposed approach is to generate the random Sboxes changing for every change of the secret key. Substitute each entry (byte) of current state matrix by corresponding entry in AES SBox for instance byte 6E is substituted by entry of SBox in row 6 and column E, ie, by 9F this leads to new State Matrix 0 B B @ 63 EB 9F A0 C0 2F 93 92 AB 30 AF C7 CB 2B 1 C C A this nonlinear layer is for resistance to di erential and linear.
Q2 Also Explain the meaning of the statement and its relevance in construction of SBox " The addition and multiplication in the equation above are being done modulo 2 (with XOR), but not in GF(16) encryption aes sboxes. C matrix cuda aes lookup Share. The conversion is done 1byte at a time based on a conversion table called Sbox which has 256 values Below illustrates to perform sboxs01 well Unlike DES, we can see that all bytes have been converted at this point This post doesn’t cover AES’s SBox as it is mentioned in many places and much better than I could do ShiftRows.
To speed up AES encryption, the SBox table is typically cache resident It contains 256 entries and each entry occupies 1 byte So the table fits into only 4 lines of cache The first two bits of the table index specify the cache line number and the remaining 6 bits specify the element within the line. If implemented as a lookuptable, it's basically just an array with the "lookup" just being indexing into the array The number of array elements must therefore correspond to the number of distinct values that the input can take, eg if the Sbox input is 8bit, then there are 28= 256 possible input values. AES defines a 16 * 16 matrix of byte values, called an Sbox (Table 52a), that contains a permutation of all possible 256 8bit values Each individual byte of State is mapped into a new byte in the following way The leftmost 4 bits of the byte are used as a row value and the rightmost 4 bits are used as a column value.
Values called an sbox This matrix consists of all the possible combinations of an 8bit sequence (28 = 16 × 16 = 256) However, the sbox is not just a random permutation of these values and there is a well defined method for creating the sbox tables The designers of Rijndael showed how this was done unlike the sboxes in DES for which. The AES SBox is shown in the Table below To read this Table, the byte input is broken into two 4bit halves The first half determines the row and the second half determines the column For example, the SBox transformation of 35 or 0x23 can be found in the cell at the intersection of the row labeled and the column labeled 03. Substitute each entry (byte) of current state matrix by corresponding entry in AES SBox for instance byte 6E is substituted by entry of SBox in row 6 and column E, ie, by 9F this leads to new State Matrix 0 B B @ 63 EB 9F A0 C0 2F 93 92 AB 30 AF C7 CB 2B 1 C C A this nonlinear layer is for resistance to di erential and linear.
C matrix cuda aes lookup Share. It is based on five lookup tables, which are generated from Sbox (the substitution table in AES) The obvious advantages are reducing the codesize, improving the implementation efficiency, and helping new learners to understand the AES encryption algorithm and GF (28) multiplication which are necessary to correctly implement AES. To speed up AES encryption, the SBox table is typically cache resident It contains 256 entries and each entry occupies 1 byte So the table fits into only 4 lines of cache The first two bits of the table index specify the cache line number and the remaining 6 bits specify the element within the line.
The computation results are shown in Table 1 It is obvious that AES Sbox’s iterative periods involve 87, 81, 59, 27 and 2 These ve periods satisfy 87 81 59. To speed up AES encryption, the SBox table is typically cache resident It contains 256 entries and each entry occupies 1 byte So the table fits into only 4 lines of cache The first two bits of the table index specify the cache line number and the remaining 6 bits specify the element within the line. Sbox is used to substitute data Simply we can see Sbox as a lookup table The way to substitute bytes for block is like each block have 8bit data, and we can see first 4bit as row index and.
Single pipeline AES 128 bit encryption using Sbox as Look up table aneels3/AES128. Would it be wise to implement AES without lookup tables here?. THE LOW POWER SBOX DESIGN The Sbox implementation is the complicated process in the AES architecture The Sbox can be designed on the ROM where the Sbox values are stored This is known as LookUp Table (LUT) sbox It means that the operation based on LUT needs a memory (256x8 bit=1024 bit).
Substitute each entry (byte) of current state matrix by corresponding entry in AES SBox for instance byte 6E is substituted by entry of SBox in row 6 and column E, ie, by 9F this leads to new State Matrix 0 B B @ 63 EB 9F A0 C0 2F 93 92 AB 30 AF C7 CB 2B 1 C C A this nonlinear layer is for resistance to di erential and linear. AES Sbox AES Sbox implementation based on the approach by D Canright The present design implements the Sbox of the Advanced Encryption Standard (AES) Since the overall AES structure is based on a byteoriented design, also the Sbox hast been implemented such that a single byte can be substituted. The LookUp Table based SBox of conventional AES occupies large storage space, reduced throughput and consumes more power This article presents the design of an SBox based on Reversible Cellular Automata function that reduces the implementation cost.
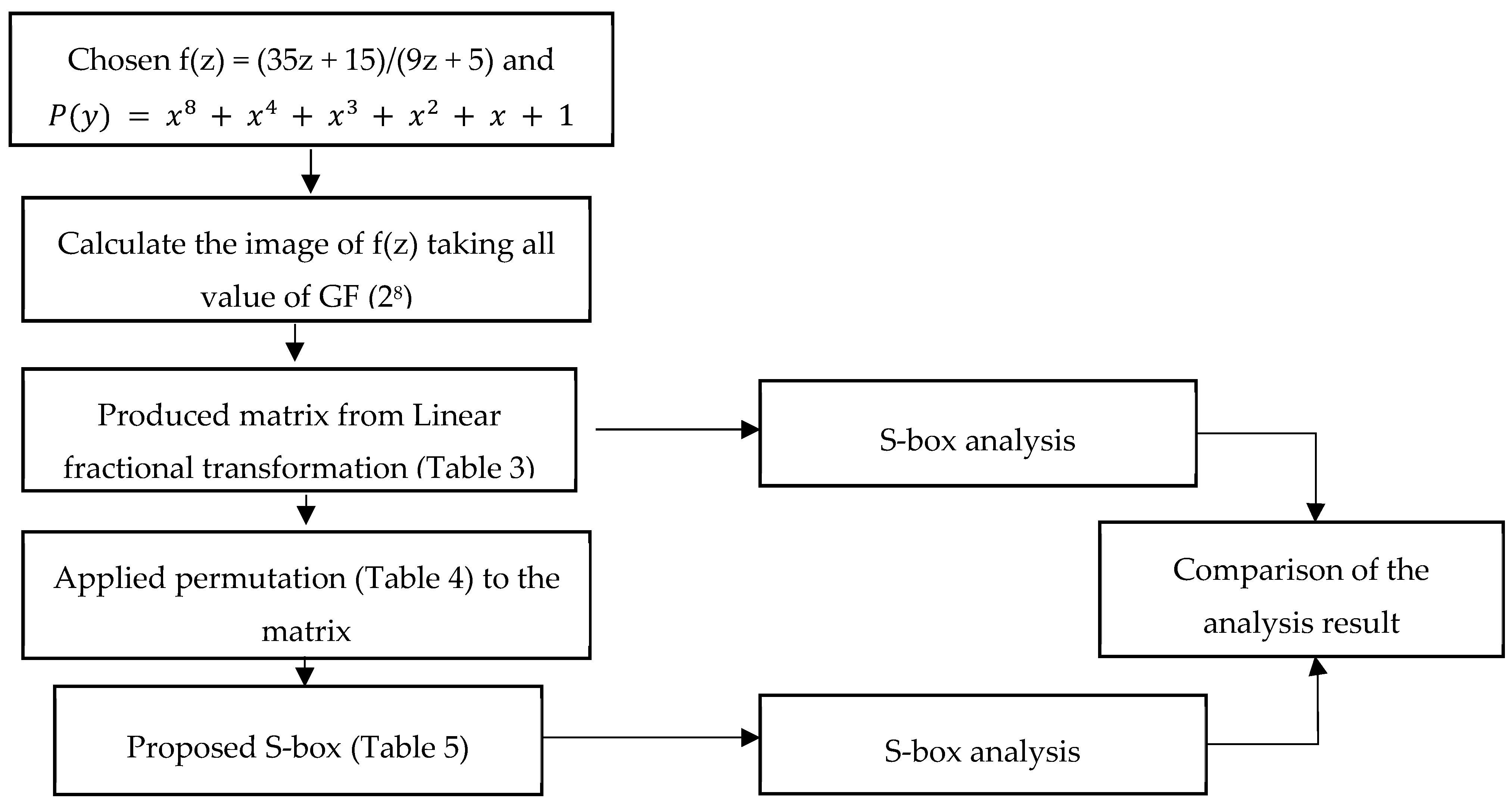
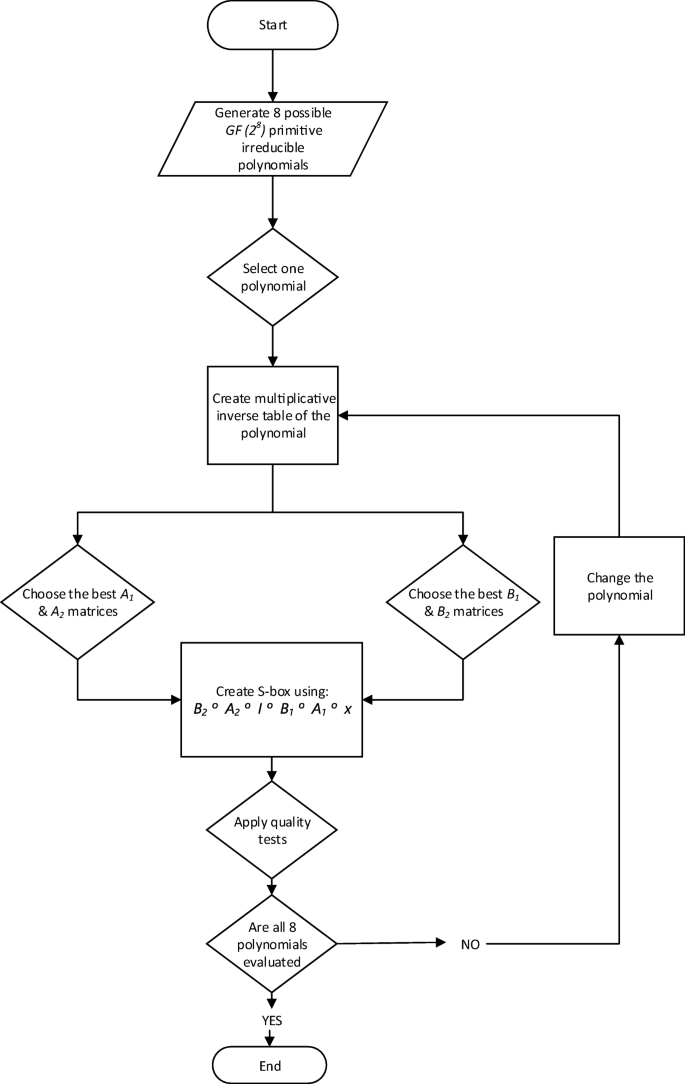
The only thing I recognize is the mixcolumn part constant matrix, as well as the Sbox matrix Edit Now that someone pointed it out how can a lookup implementation be actually slower?. Advanced Encryption Standard (AES) is a block cipher system which widely used in cryptographic application Substitution box (Sbox), nonlinear substitution operation, is the main factor of the. The substitution table (SBox) of Advanced Encryption Standard (AES) and its properties are key elements in cryptanalysis ciphering We aim here to propose a straightforward method for the nonlinear transformation of AES SBox construction The method reduces the steps needed to compute the multiplicative inverse, and computes the matrices multiplication used in this transformation, without a.
To speed up AES encryption, the SBox table is typically cache resident It contains 256 entries and each entry occupies 1 byte So the table fits into only 4 lines of cache The first two bits of the table index specify the cache line number and the remaining 6 bits specify the element within the line Types of Attacks and Attack Scenarios. To speed up AES encryption, the SBox table is typically cache resident It contains 256 entries and each entry occupies 1 byte So the table fits into only 4 lines of cache The first two bits of the table index specify the cache line number and the remaining 6 bits specify the element within the line. The only thing I recognize is the mixcolumn part constant matrix, as well as the Sbox matrix Edit Now that someone pointed it out how can a lookup implementation be actually slower?.
Sect Ctf 17 Bad Aes
Http Www Ijera Com Papers Vol3 Issue1 Iw Pdf
Www Irjet Net Archives V2 I8 Irjet V2i811 Pdf
Avalanche Effect Of Aes Algorithm

3d Determine The Aes S Box Substitution Value For Which Is In Hex Youtube
Advanced Encryption Standard Wikipedia

Ece 5760
Lirias Kuleuven Be Retrieve

Secret Key Crypotography
Http Www Ijera Com Papers Vol3 Issue1 Iw Pdf
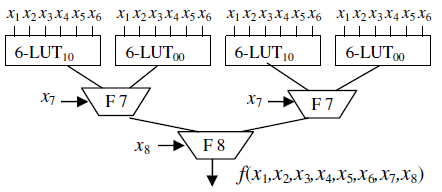
Pipeline Aes S Box Implementation Starting With Substitution Table
Advanced Encryption Standard Wikipedia

New S Box Calculation For Rijndael Aes Based On An Artificial Neural Network
Ieeexplore Ieee Org Iel7 Pdf

Aes Smaller Than S Box Springerprofessional De

Aes S Box Rijndael S Box 16 Download Scientific Diagram

Table 1 From Dynamic Aes 128 With Key Dependent S Box Semantic Scholar

Inverse S Box Substitution Values For The Byte Xy In Hexadecimal Format Download Scientific Diagram

The Advanced Encryption Standard Aes Algorithm Commonlounge

Advanced Encryption Standard Aes Transformation Functions
Ryo Nakao

Aes Advanced Encryption Standard Anu Vazhayil

New S Box Calculation For Rijndael Aes Based On An Artificial Neural Network

How Are S Box Calculated In S Aes Cryptography Stack Exchange

Table 43 Aes S Box Substitution Values In Hexadecimal Notation For Input Byte Course Hero
Aip Scitation Org Doi Pdf 10 1063 1
What Is 3des Encryption And How Does Des Work Comparitech

Advanced Encryption Standard Aes Transformation Functions
S Box Design Symmetric Ciphers And Hashes Modern Cryptography Applied Mathematics For Encryption And Informanion Security 16
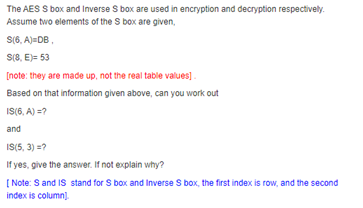
Solved The Aes S Box And Inverse S Box Are Used In Encryp Chegg Com
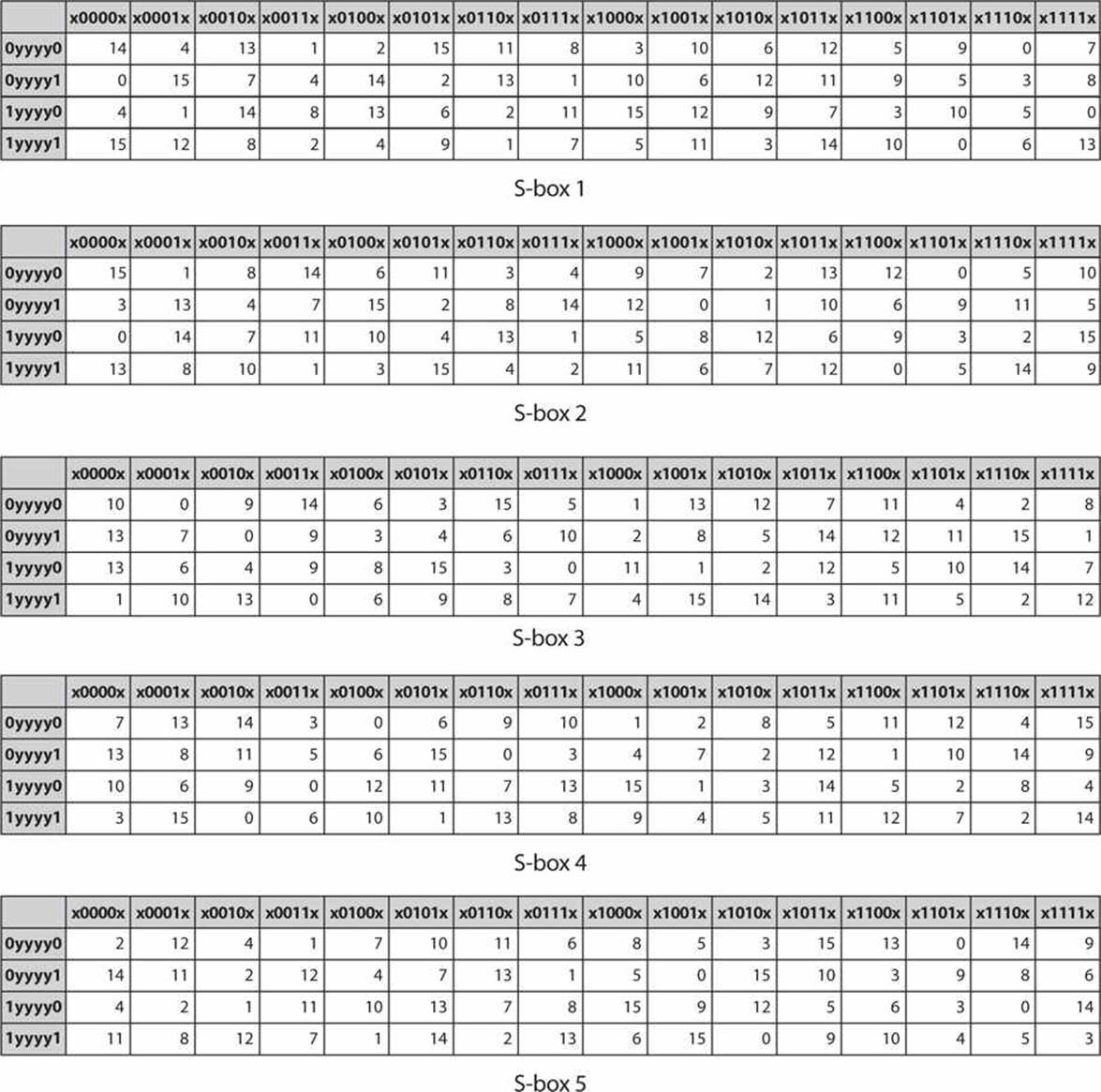
S Box Design Symmetric Ciphers And Hashes Modern Cryptography Applied Mathematics For Encryption And Informanion Security 16

The Advanced Encryption Standard Aes Algorithm Commonlounge
Q Tbn And9gcrlke38hvryx7soy4gg1km9wvfkr 87ye10q0icolw3fqxoz6 Usqp Cau
Http Citeseerx Ist Psu Edu Viewdoc Download Doi 10 1 1 227 7609 Rep Rep1 Type Pdf
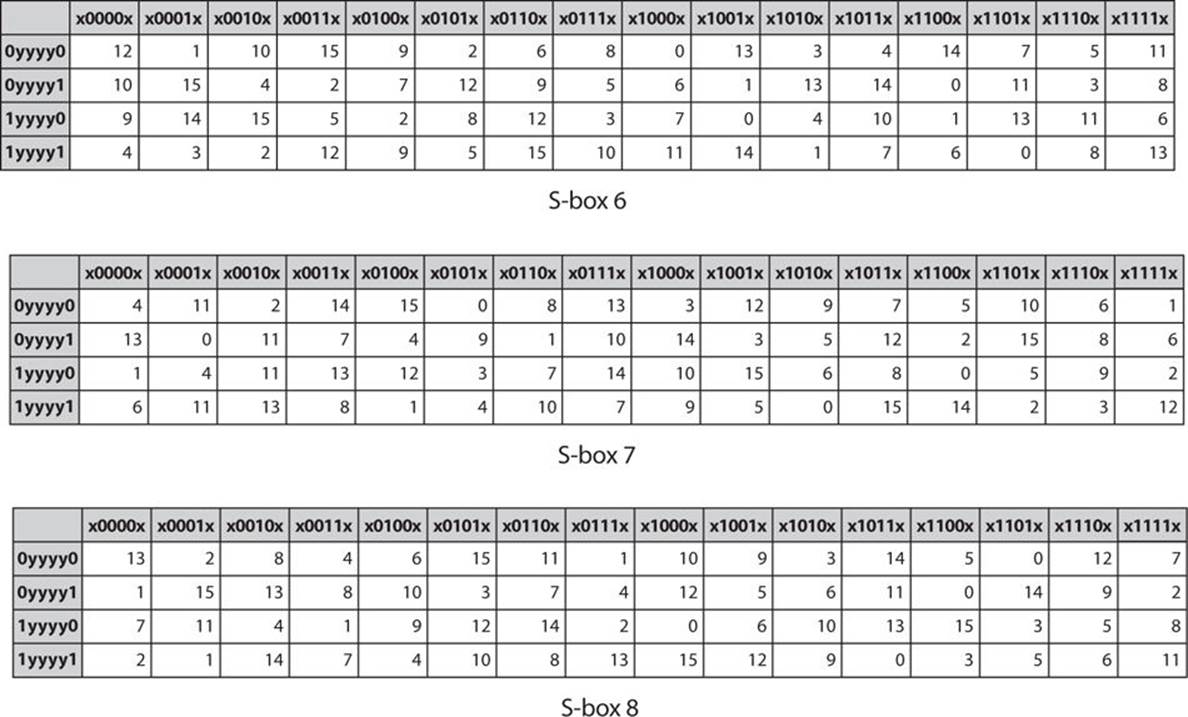
S Box Design Symmetric Ciphers And Hashes Modern Cryptography Applied Mathematics For Encryption And Informanion Security 16
Q Tbn And9gcq Raxfwj2ura1kadboki 0ic9uqbm48wdz6h9hhbtj3p64kk Usqp Cau
Www Tandfonline Com Doi Pdf 10 1080 16

Building Aes 128 From The Ground Up With Python By Henrique Marcomini Wavy Product Engineering Medium

Pdf An Improved Aes S Box And Its Performance Analysis Semantic Scholar
Http Www Um Es Docencia Jsimon Congresocripto Absautores Presentaciones Stoianov Pdf
3
9 Advanced Encryption Standard
Design And Verification Of Aes Encryption With New Approach For S Box
Dl Acm Org Doi Pdf 10 1145
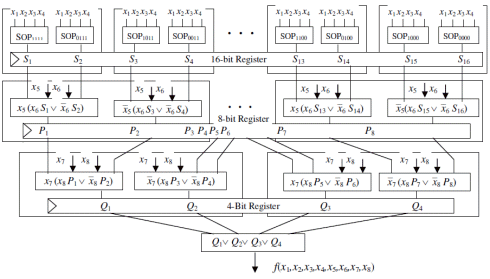
Pipeline Aes S Box Implementation Starting With Substitution Table

Construction Of New S Box Using Action Of Quotient Of The Modular Group For Multimedia Security

Table 2 From Key Dependent S Box Generation In Aes Block Cipher System Semantic Scholar

The Aes Rijndael S Box
Q Tbn And9gcrmq1uror0bzpl6mnp52butzzlkreaovkmephwit8vsl474qera Usqp Cau
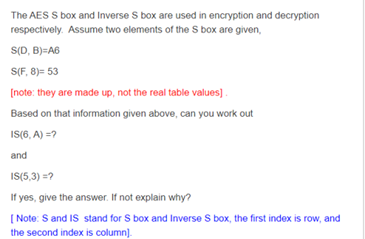
Solved The Aes S Box And Inverse S Box Are Used In Encryp Chegg Com

Ece 5760

Fpga Implementation Results For Aes Box Download Table

Achieving High Performance For Advanced Encryption Standard Aes Applications

The Advanced Encryption Standard Aes Algorithm Commonlounge
2
Aes Encryption
Lecture 23 Symmetric Encryption Ppt Download
Www Mdpi Com 1099 4300 21 3 245 Pdf

Ch05 Testbank Crypto6e
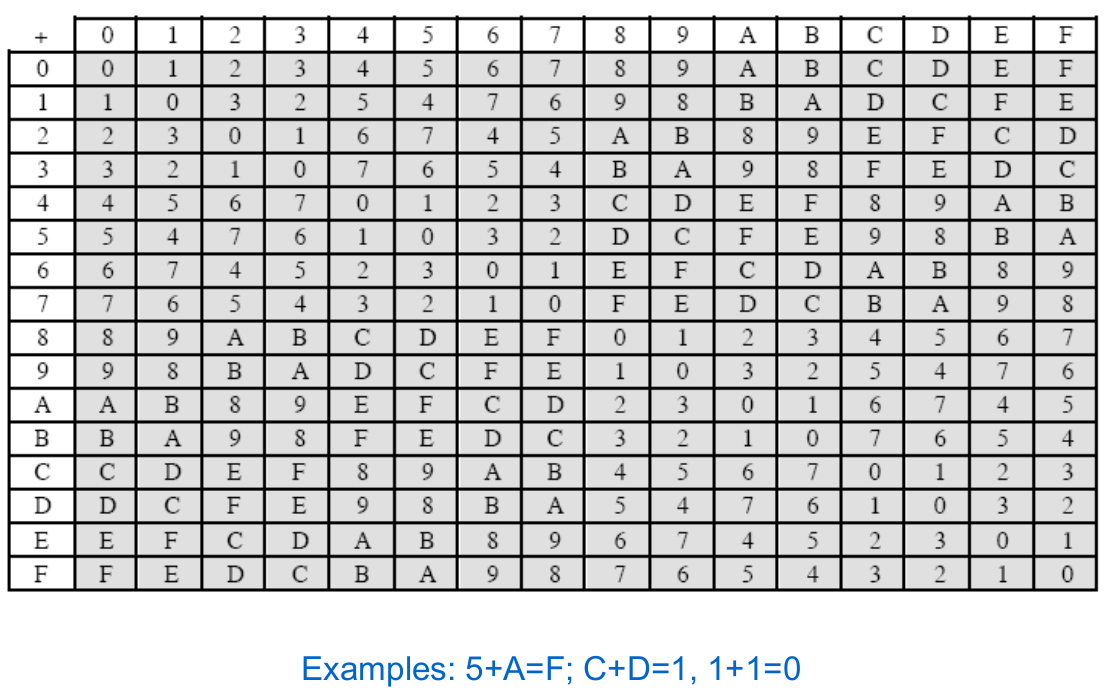
Solved Using The Table Determine The Multiplicative Inve Chegg Com
Ieeexplore Ieee Org Iel5 Pdf

Finding Output Given An S Box Input Of 8 Bits Cryptography Stack Exchange

Aes

Pdf An Improved Aes S Box And Its Performance Analysis Semantic Scholar
Implementation Of Simplified Aes Algorithm For Wireless Sensor Nodes On Fpga

New S Box Calculation For Rijndael Aes Based On An Artificial Neural Network
Network Security Lec4

Aes Algorithm Flowchart 2 1 Byte Substitution Using S Box Table S Box Download Scientific Diagram

Rijndael S Box Wikipedia

Table 2 From Encryption Using Dual Key Transformation Based On Creation Of Multi S Boxes In Aes Algorithm Semantic Scholar
Symmetry Free Full Text S Box Construction Based On Linear Fractional Transformation And Permutation Function Html
A Highly Nonlinear S Box Based On A Fractional Linear Transformation Springerplus Full Text
Www Osti Gov Servlets Purl
Eprint Iacr Org 17 1161 Pdf
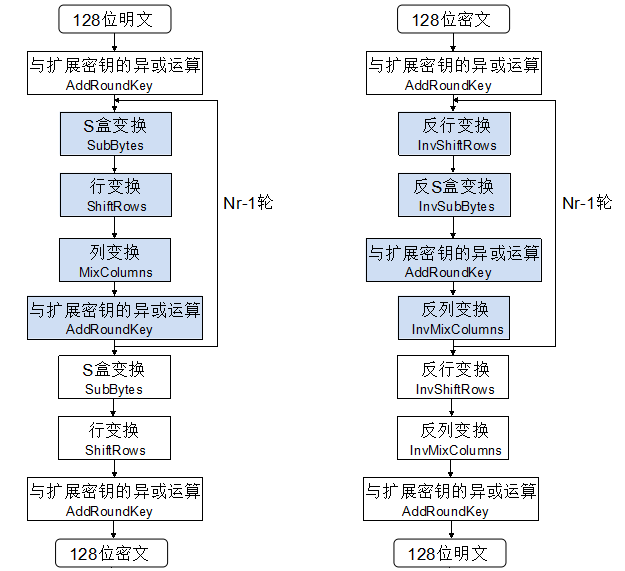
Section 5 2 The Aes Cipher Cryptography And Network Security 4th Edition
C Implementation Of Aes Encryption Algorithms
A New Construction Of Confusion Component Of Block Ciphers Springerlink

S Box Substitution Box Youtube
Plos One A Novel Byte Substitution Architecture For The Aes Cryptosystem
Symmetry Free Full Text S Box Construction Based On Linear Fractional Transformation And Permutation Function Html
Http Www Ijera Com Papers Vol3 Issue1 Iw Pdf

Table 2 From An Algorithm For Key Dependent S Box Generation In Block Cipher System Semantic Scholar

Block Cipher Programmer Sought
Eprint Iacr Org 18 1002 Pdf
Aes Encryption
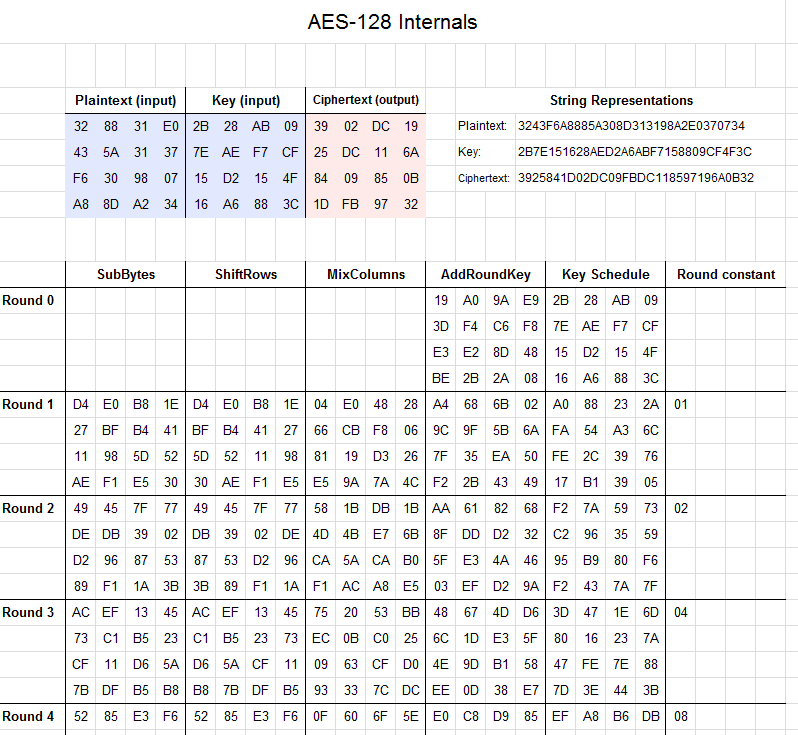
Aes Cipher Internals In Excel
Solved C Points 6 Using Table 4 2 Of Gf 2 Determine Chegg Com
Http Cse Iitkgp Ac In Debdeep Courses Iitkgp Crypto Slides Dc Pdf

Construction Of S8 Liu J S Boxes And Their Applications Sciencedirect

The Advanced Encryption Standard Aes Algorithm Commonlounge
Http Www Cs Man Ac Uk Banach Comp Info Courseslides Wk2 3 Aes Pdf
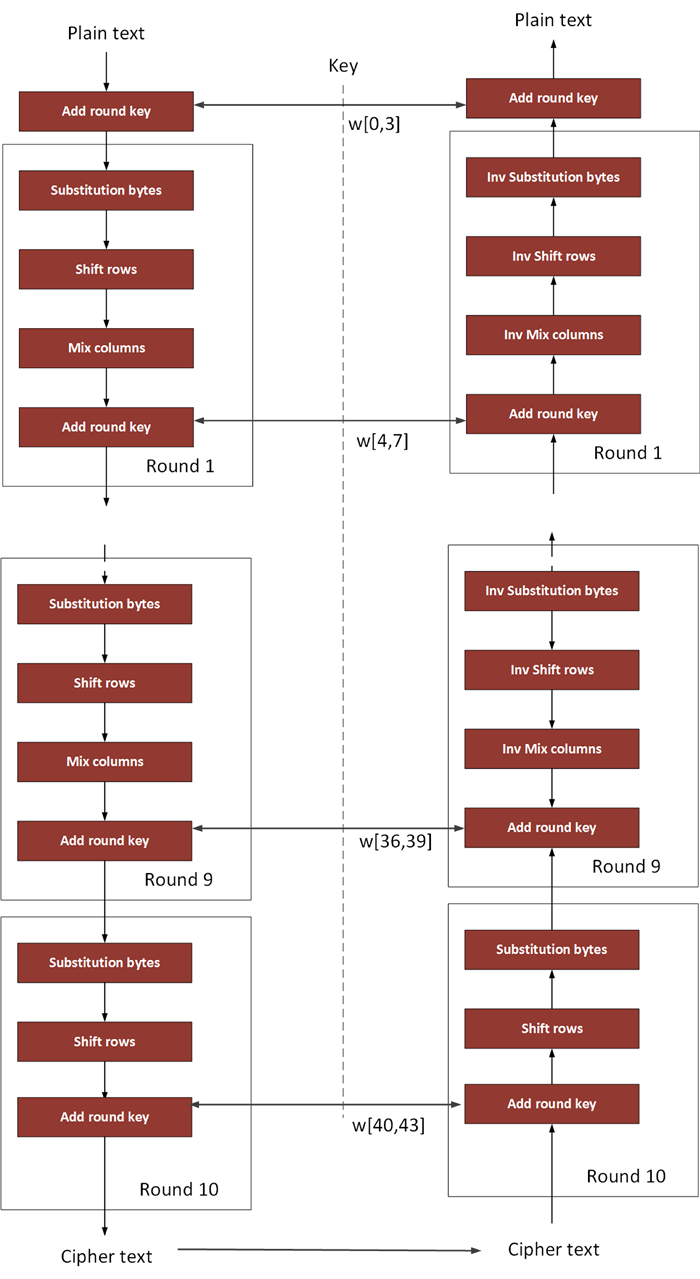
Aes Encryption

An Algorithm For The Construction Of Substitution Box For Block Ciphers Based On Projective General Linear Group Aip Advances Vol 7 No 3

Aes S Box Performance And Comparison With Previous Work Download Table

Advanced Encryption Standard Aes With Dynamic Substitution Box
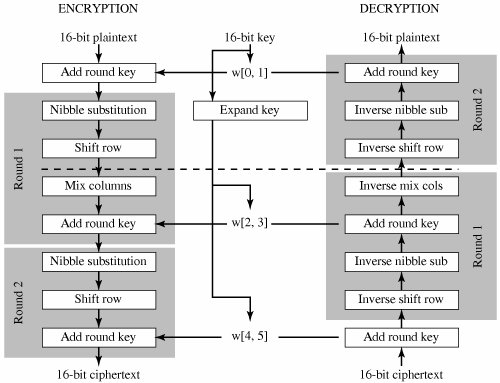
Appendix 5b Simplified Aes Cryptography And Network Security 4th Edition

New S Box Calculation For Rijndael Aes Based On An Artificial Neural Network

Cryptography And Network Security Ppt Download



